- Как интегрировать Linux-машину в среду домена Windows AD (Active Directory)
- Шаг 1. Установка пакетов и подготовка
- Шаг 2. Настройка DNS
- Шаг 3. Обнаружение домена, присоединение к нему и проверка результата.
- Шаг 4. Последние настройки и авторизация.
- LDAP on Cumulus Linux Using Server 2008 Active Directory
- Prerequisites
- Active Directory Setup
- Goals
- Configure Cumulus Linux
- Automate It with Ansible
Как интегрировать Linux-машину в среду домена Windows AD (Active Directory)
В этой статье будет описан процесс добавления Linux-машины (Ubuntu 20.04) в домен Windows AD.
Шаг 1. Установка пакетов и подготовка
После этого установите требуемые пакеты.
sudo apt -y install realmd sssd sssd-tools libnss-sss libpam-sss adcli samba-common-bin oddjob oddjob-mkhomedir packagekit
Далее мы настроим все инструменты. Вам требуется знать:
Шаг 2. Настройка DNS
Откройте конфигурационный файл netplan:
Если вы видите там «dhcp4: true», то есть ваш DHCP-сервер настроен корректно, переходите к следующему шагу. Если вы настраиваете параметры сетевого подключения вручную, ознакомьтесь с примером настройки:
network:ethernets:enp0s3:addresses:- 192.168.0.15/24gateway4: 192.168.0.10nameservers:addresses: [192.168.0.1, 192.168.0.2]search:- office.localoptional: trueversion: 2
- addresses — это IP, назначаемый сетевой карте;
- gateway4 — IP роутера;
- nameservers — DNS-сервера;
- search — целевой домен.
Шаг 3. Обнаружение домена, присоединение к нему и проверка результата.
В первую очередь требуется обнаружить домен:
Вы увидите что-то подобное. Это означает, что настройки сети верны и машина получила ответ от домена. Если нет, вам необходимо проверить настройки сети, домен и работоспособность DNS.
Затем присоединитесь к домену AD. Замените admin1 на имя администратора и укажите пароль.
Проверьте, возможен ли прием информации о пользователе AD. Замените user1 на имя пользователя вашего домена.
id user1@office.localuid=687821651(user1@office.local) gid=687800512(user1@office.local) groups=687800512(domain users@office.local)
Шаг 4. Последние настройки и авторизация.
Необходимо произвести настройку, чтобы в будущем каждый раз не добавлять имя домена к имени пользователя.
Измените значение use_fully_qualified_names на False. Перезагрузите и проверьте:
sudo systemctl restart sssdid useruid=687821651(user1@office.local) gid=687800512(user1@office.local) groups=687800512(domain users@office.local)
Теперь нужно настроить создание домашних каталогов для пользователей AD при входе в систему.
sudo nano /etc/pam.d/common-session#add this line in the end of filesession optional pam_mkhomedir.so skel=/etc/skel umask=077
Войдите в систему как пользователь AD.
Это означает, что вы успешно вошли в систему как пользователь AD.
Также вы можете разрешить авторизацию для некоторых пользователей и групп AD или же ограничить других. В приведенном ниже примере настроен запрет для всех пользователей, кроме user0, user1 и группы Main Admins.
sudo realm deny –allsudo realm permit user0@office.local user1@office.localsudo realm permit -g ‘Main Admins’
Настройка пользователей AD для получения root-прав такая же, как и для локальных, но выполняется в другом файле.
Добавьте к нему нужные строки. Например:
LDAP on Cumulus Linux Using Server 2008 Active Directory
This article provides an example of how to set up LDAP authentication and authorization on Cumulus Linux using Active Directory. It applies to any Debian Wheezy-based server or switch. The method described in the article applies ONLY to Windows Server 2008. This method does not work as well with Windows Server 2012.
Prerequisites
Active Directory Setup
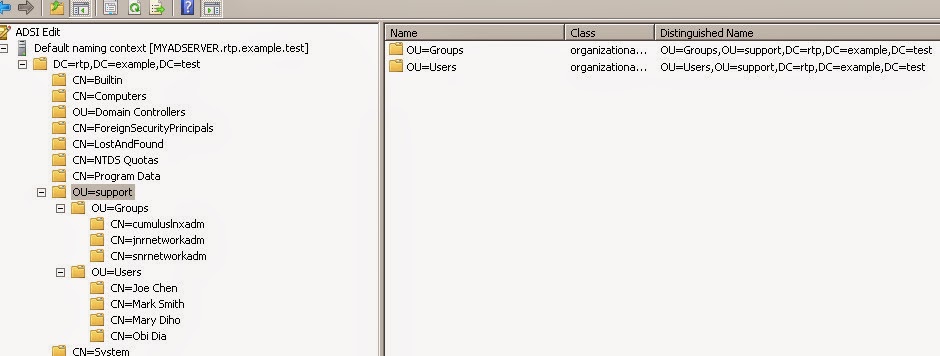
- Base DN: CN=Cumulus Admin, DC=RTP, DC=Example, DC=test
- Base OU: OU=Support, DC=RTP, DC=Example, DC=Test
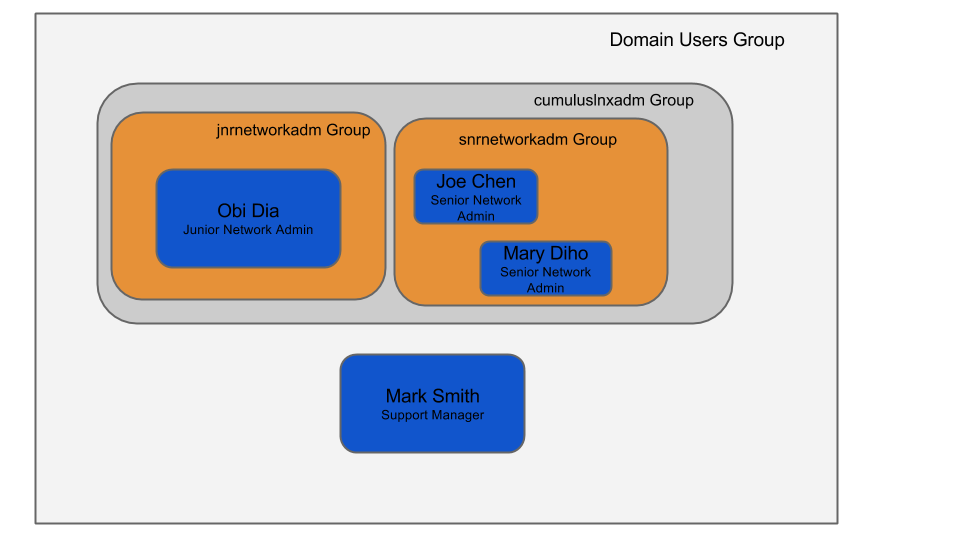
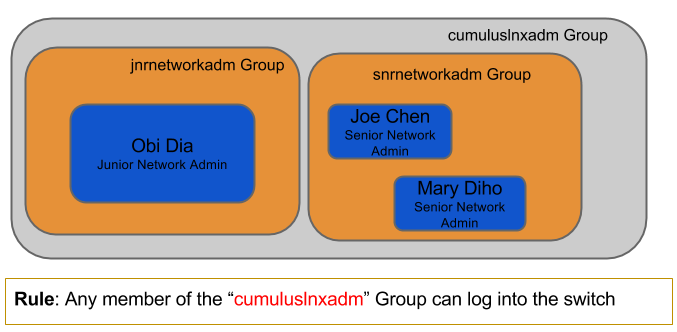
- Users and Groups: This example has three users that can access a Cumulus Linux switch. Two are in the senior network engineer group, one in the junior engineering group. The last user, Mark Smith, does not have access to the switches because he is not a member of the cumuluslnxadm group.
Layout of users and groups in AD schema
Goals
- Configure LDAP authentication without changing the default AD schema.
- Support nested groups. The following should work:
- User directories are automatically created the first time an authorized user logs into the switch.
- Senior network admins via sudo can run any command on the switch.
- Junior network admins can:
- Log in and access any non-privileged command.
- Run sudo lldpctl without prompting for a password. lldpctl is an important network troubleshooting tool, but requires root access.
- Use all ip commands (iproute2 commands).
- Not access FRR via vtysh or non-modal CLI like cl-ospf .
Configure Cumulus Linux
- Update PAM to support automatic creation of directories (optional). This information is from the Debian wiki. The alternative is to set the homeDirectory attribute for users in AD to /home/cumulus, and all users map to the predefined user account. Create the following file /usr/share/pam-configs/mkhomedir :
Name: Create home directory during login Default: yes Priority: 900 Session-Type: Additional Session: required pam_mkhomedir.so umask=0022 skel=/etc/skel root# apt-get install debconf-utils root# debconf-set-selections root# debconf-show nslcd * nslcd/ldap-bindpw: (password omitted) nslcd/restart-failed: nslcd/ldap-sasl-authcid: nslcd/restart-services: nslcd/ldap-sasl-realm: * nslcd/ldap-sasl-mech: * nslcd/ldap-starttls: false * nslcd/ldap-base: ou=support,dc=rtp,dc=example,dc=test nslcd/ldap-sasl-krb5-ccname: /var/run/nslcd/nslcd.tkt * nslcd/ldap-auth-type: none nslcd/disable-screensaver: * libraries/restart-without-asking: true * nslcd/ldap-reqcert: never nslcd/ldap-cacertfile: /etc/ssl/certs/ca-certificates.crt nslcd/ldap-sasl-authzid: * nslcd/ldap-uris: ldaps://myadserver.rtp.example.test * libraries/restart-without-asking:: true nslcd/ldap-sasl-secprops: nslcd/xdm-needs-restart: * nslcd/ldap-binddn: root# debconf-show libpam-runtime libpam-runtime/override: false libpam-runtime/profiles: mkhomedir, unix, ldap, capability, auditd libpam-runtime/title: libpam-runtime/conflicts: libpam-runtime/no_profiles_chosen: root# debconf-show man-db * man-db/auto-update: true man-db/install-setuid: false root# debconf-show libnss-ldapd * libnss-ldapd/nsswitch: group, passwd, shadow * libnss-ldapd/clean_nsswitch: false
root# apt-get -t wheezy-backports install libnss-ldapd ldap-utils

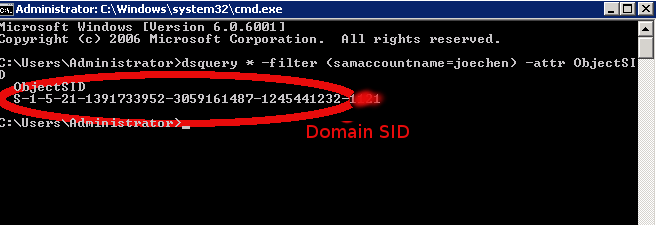
Get the Active Directory Domain SID. Use the dsquery command on the Windows server to get the domain SID. For more information, read this good reference on Object SIDs. Configure nslcd.conf . Update /etc/nslcd.conf with the following: - Specify the Bind DN path.
- Specify the Bind DN password.
- Configure LDAP search filter. The filter states that only users in the cumuluslnxadm group can log in. The search filter performs the nested group lookup.
- Configure Unix to AD mappings.
- Configure nested group support.
Here is the /etc/nslcd.conf config with comments:
# /etc/nslcd.conf # nslcd configuration file. See nslcd.conf(5) # for details. # The user and group nslcd should run as. uid nslcd gid nslcd # The location at which the LDAP server(s) should be reachable. # If planning to use secure LDAP, use fqdn that matches name # in the server SSL cert sent during negotiation. Debugging # nslcd will show this error if found uri ldap://myadserver.rtp.example.test # The search base that will be used for all queries. base ou=support,dc=rtp,dc=example,dc=test # The LDAP protocol version to use. #ldap_version 3 # The DN to bind with for normal lookups. # defconf-set-selections doesn't seem to set this. so have to manually set this. binddn CN=cumulus admin,CN=Users,DC=rtp,DC=example,DC=test bindpw 1Q2w3e4r! # The DN used for password modifications by root. #rootpwmoddn cn=admin,dc=example,dc=com # SSL options #ssl off (default) # default tls setting of 'demand' requires CA public cert # for AD server be defined in "tls_cacertfile" # use PEM format for CA cert, not DER format. tls_reqcert never #tls_cacertfile /etc/ssl/certs/ca-certificates.crt # The search scope. #scope sub # Add nested group support # Supported in nslcd 0.9 and higher. # default wheezy install of nslcd supports on 0.8. wheezy-backports has 0.9 nss_nested_groups yes # Mappings for Active Directory # (replace the SIDs in the objectSid mappings with the value for your domain) # "dsquery * -filter (samaccountname=testuser1) -attr ObjectSID" pagesize 1000 referrals off idle_timelimit 1000 # Do not allow uids lower than 100 to login (aka Administrator) # not needed as pam already has this support # nss_min_uid 1000 # This filter says to get all users who are part of the cumuluslnxadm group. Supports nested groups search filter. # Example, mary is part of the snrnetworkadm group which is part of cumuluslnxadm group # Ref: http://msdn.microsoft.com/en-us/library/aa746475%28VS.85%29.aspx (LDAP_MATCHING_RULE_IN_CHAIN) filter passwd (&(Objectclass=user)(!(objectClass=computer))(memberOf:1.2.840.113556.1.4.1941:=cn=cumuluslnxadm,ou=groups,ou=support,dc=rtp,dc=example,dc=test)) map passwd uid sAMAccountName map passwd uidNumber objectSid:S-1-5-21-1391733952-3059161487-1245441232 map passwd gidNumber objectSid:S-1-5-21-1391733952-3059161487-1245441232 map passwd homeDirectory "/home/$sAMAccountName" map passwd gecos displayName map passwd loginShell "/bin/bash" # Filter for any AD group or user in the baseDN. the reason for filtering for the # user to make sure group listing for user files don't say ' '. instead will say ' ' # So for cosmetic reasons..nothing more. filter group (&(|(objectClass=group)(Objectclass=user))(!(objectClass=computer))) map group gidNumber objectSid:S-1-5-21-1391733952-3059161487-1245441232 map group cn sAMAccountName
- Copy the LDAP CA certificate (in PEM format) to the directory, specified in the nslcd.conf tls_cacertfile option, on the client device. Ensure the file specified matches the filename copied.
- Set the tls_reqcert option to demand .
- Change the URI to use ldaps:// .
root# nscd --invalidate=group root# nscd --invalidate=passwd
root# service nslcd stop root# nslcd -d
root# getent passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/bin/sh . . _lldpd:x:105:107::/var/run/lldpd:/bin/false joechen:*:1121:1121:Joe Chen:/home/joechen:/bin/bash marydiho:*:1124:1124:Mary Diho:/home/marydiho:/bin/bash obidia:*:1128:1128:Obi Dia:/home/obidia:/bin/bash
group list: GIDs of each user should be present. Because you enabled nested group support, all nested groups get mapped to the right users.
root# getent group .. . ssh:x:105: nslcd:x:106 _lldpd:x:107: joechen:*:1121: marydiho:*:1124: marksmith:*:1125: obidia:*:1128: jnrnetworkadm:*:1118:obidia cumuluslnxadm:*:1120:obidia,marydiho,joechen snrnetworkadm:*:1126:marydiho,joechen
- Senior engineers can run any privileged and non-privileged command.
- Junior engineers can run lldpctl without a password. By default, lldpctl requires root access.
Add two files to the /etc/sudoers.d directory, one for senior engineers and the other for junior engineers. You can configure this in the /etc/sudoers file, but this keeps things modular.
# allow any senior engineer root privilege after they type their password %snrnetworkadm ALL=(ALL) ALL
Cmnd_Alias LLDP_CMDS = /usr/sbin/lldpctl # allow any junior network engineer to run lldpctl without root permission %jnrnetworkadm ALL=(ALL) NOPASSWD: LLDP_CMDS
Automate It with Ansible
An Ansible Playbook is available on GitHub that automates the configuration shown in this article.