- List all internet connections
- 2 Answers 2
- Using netstat
- Similar to top :
- GUI Interface (just in case):
- How to list all the current network connections for a given PID?
- 4 Answers 4
- 12 ss Command Examples to Monitor Network Connections
- 1. Listing all Connections
- 2. Listing Listening and Non-listening Ports
- 3. Listing Listening Sockets
- 4. List all TCP Connections
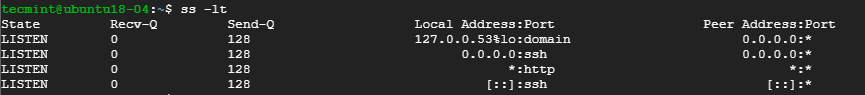
- 5. List all Listening TCP Connections
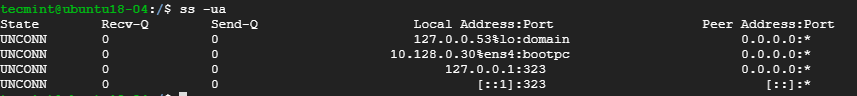
- 6. List all UDP Connections
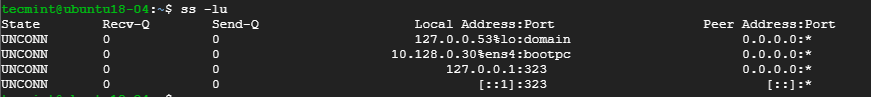
- 7. List all Listening UDP Connections
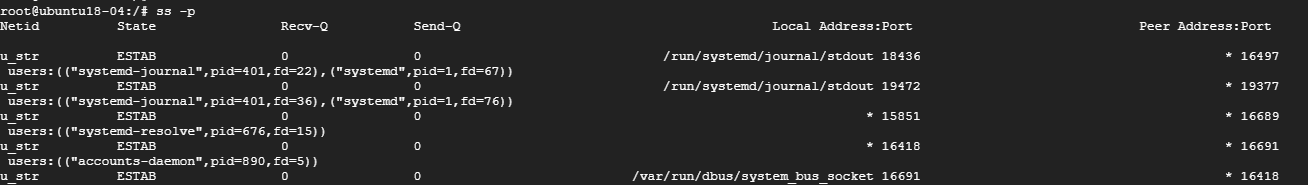
- 8. Display PID (Process IDs) of Sockets
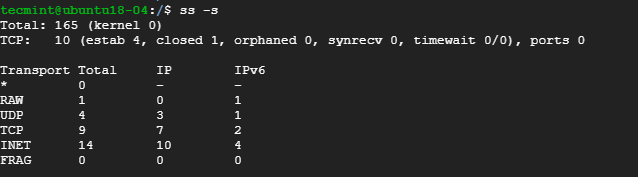
- 9. Display Summary Statistics
- 10. Display IPv4 and IPv6 Socket Connections
- 11. Filter Connections by Port Number
- 12. Check Man Pages for ss Command
- How can I monitor all outgoing requests/connections from my machine?
- 7 Answers 7
List all internet connections
I’d like to know all the connections my system is making to the internet. I tried netstat but that shows a lot of connections — all of which aren’t applicable I think. Can it be displayed like top does for processes ? I’m a little security conscious and would like to know all the incoming and outgoing connections happening on my system.
2 Answers 2
Using netstat
netstat by itself monitors all major protocols including TCP and UDP on every port.
If you want to display TCP and UDP connections:
If you want to display that continously:
Similar to top :
- nethogs — shows a list of the top processes that use bandwidth
- jnettop — shows list of top connections
- iftop — shows list of top connections with bandwidth bars
GUI Interface (just in case):
You may try ss as well, it’s more advanced than netstat .
List all TCP connections (including those with non-established state, e.g. SYN-SENT , LISTEN , and TIME-WAIT ). Read more about TCP states transition in RFC793.
State Recv-Q Send-Q Local Address:Port Peer Address:Port LISTEN 0 4096 127.0.0.1:5672 0.0.0.0:* ESTAB 0 0 192.168.1.4:57310 35.157.63.229:443 ESTAB 0 0 127.0.0.1:43764 127.0.0.1:8080 CLOSE-WAIT 1 0 192.168.1.4:34554 142.250.186.33:443 CLOSE-WAIT 1 0 192.168.1.4:34564 142.250.186.33:443 Include information about the owner process of the connections (e.g., process name and PID)
Display all established SSH connections.
List all the TCP sockets in state FIN-WAIT-1 for network 193.233.7/24 and look at their timers with —options , which shows timer information.
How to list all the current network connections for a given PID?
but this does not seem to work. I need a command that will take that PID and print all the open network connections but I have no idea how. I have seen on other forms about strace but this does not make sense to me.
4 Answers 4
If you’re not root , you’ll only be able to get that for your processes.
Technically, that’s only for the internet sockets (connected or not).
If you want all established connections (or associations), internet or not (like for Unix domain sockets), you could try (at least on Linux and with lsof 4.89):
lsof -Ep "$pid" | grep -e '(ESTABLISHED)$' -e '->INO=.* ' For instance, for the process I use to write this answer, that gives:
firefox 6261 chazelas 3u unix 0xffff88026785d000 0t0 741948 type=STREAM ->INO=743009 4244,dbus-daem,58u firefox 6261 chazelas 4u unix 0xffff88017194c000 0t0 741280 type=STREAM ->INO=742999 3575,Xorg,57u firefox 6261 chazelas 6u unix 0xffff8802f544d400 0t0 743000 type=STREAM ->INO=741281 4244,dbus-daem,56u firefox 6261 chazelas 11u unix 0xffff8802f544e800 0t0 743004 type=STREAM ->INO=737278 4167,cinnamon-,21u firefox 6261 chazelas 14u unix 0xffff8801474b3c00 0t0 737279 type=STREAM ->INO=737280 6261,firefox,15u firefox 6261 chazelas 15u unix 0xffff8801474b7c00 0t0 737280 type=STREAM ->INO=737279 6261,firefox,14u firefox 6261 chazelas 34u unix 0xffff8801d0d01800 0t0 741294 type=STREAM ->INO=743006 4244,dbus-daem,57u firefox 6261 chazelas 45u IPv4 741950 0t0 TCP UNKNOWN:44232->host24-rangeA-akamai-aanp.cdn.thlon.isp.sky.com:http (ESTABLISHED) firefox 6261 chazelas 53u unix 0xffff880178356800 0t0 741947 type=STREAM ->INO=743008 3575,Xorg,56u firefox 6261 chazelas 60u IPv4 743011 0t0 TCP UNKNOWN:52760->a95-101-128-57.deploy.akamaitechnologies.com:http (ESTABLISHED) firefox 6261 chazelas 73u IPv4 742158 0t0 TCP UNKNOWN:54674->lhr35s01-in-f14.1e100.net:http (ESTABLISHED) firefox 6261 chazelas 87u IPv4 743521 0t0 TCP UNKNOWN:33564->stackoverflow.com:https (ESTABLISHED) firefox 6261 chazelas 91u IPv4 743522 0t0 TCP UNKNOWN:53940->93.184.220.29:http (ESTABLISHED) firefox 6261 chazelas 92u IPv4 742153 0t0 TCP UNKNOWN:36836->151.101.65.69:https (ESTABLISHED) firefox 6261 chazelas 94u IPv4 742154 0t0 TCP UNKNOWN:33716->192.0.73.2:https (ESTABLISHED) firefox 6261 chazelas 96u IPv4 742157 0t0 TCP UNKNOWN:51166->lhr26s04-in-f234.1e100.net:https (ESTABLISHED) firefox 6261 chazelas 113u IPv4 744875 0t0 TCP UNKNOWN:43262->lhr35s01-in-f1.1e100.net:https (ESTABLISHED) 12 ss Command Examples to Monitor Network Connections
ss command is a tool that is used for displaying network socket related information on a Linux system. The tool displays more detailed information that the netstat command which is used for displaying active socket connections.
In this guide, we delve in and see how the ss command can be used to display varied socket connection information in Linux.
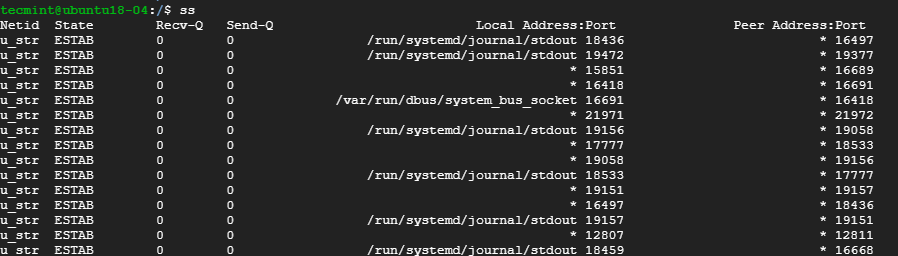
1. Listing all Connections
The basic ss command without any options simply lists all the connections regardless of the state they are in.
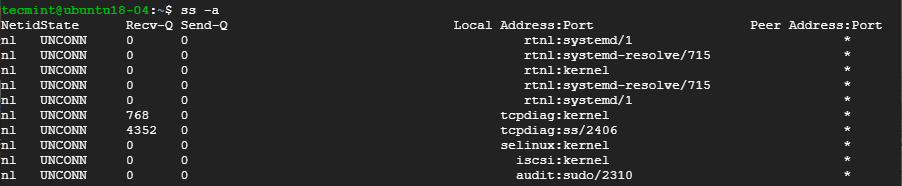
2. Listing Listening and Non-listening Ports
You can retrieve a list of both listening and non-listening ports using the -a option as shown below.
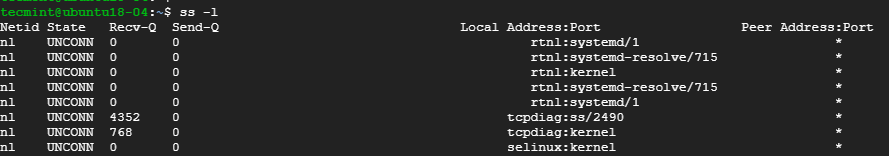
3. Listing Listening Sockets
To display listening sockets only, use the -l flag as shown.
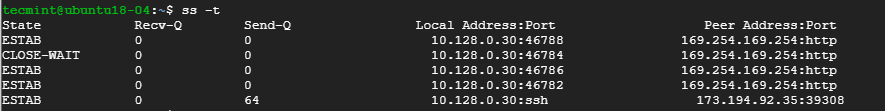
4. List all TCP Connections
To display all TCP connection, use the -t option as shown.
5. List all Listening TCP Connections
To have a view of all the listening TCP socket connection use the -lt combination as shown.
6. List all UDP Connections
To view all the UDP socket connections use the -ua option as shown.
7. List all Listening UDP Connections
To list listening UDP connections use the -lu option.
8. Display PID (Process IDs) of Sockets
To display the Process IDs related to socket connections, use the -p flag as shown.
9. Display Summary Statistics
To list the summary statistics, use the -s option.
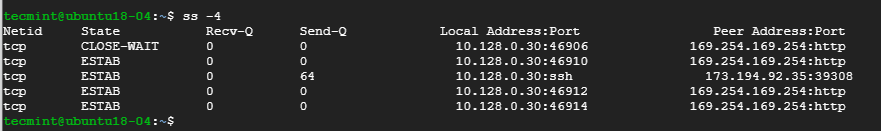
10. Display IPv4 and IPv6 Socket Connections
If you are curious about the IPv4 socket connections use the -4 option.
To display IPv6 connections, use the -6 option.
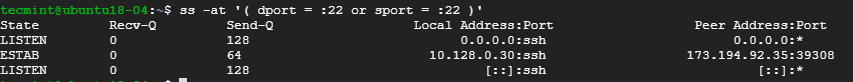
11. Filter Connections by Port Number
ss command also lets you filter socket port number or address number. For example, to display all socket connections with a destination or source port of ssh run the command.
$ ss -at '( dport = :22 or sport = :22 )'
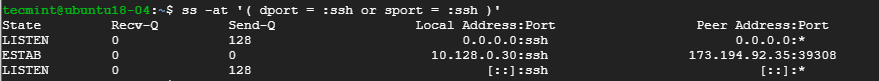
Alternatively, you can run the command.
$ ss -at '( dport = :ssh or sport = :ssh )'
12. Check Man Pages for ss Command
To get more insights into the ss command usage, check the man pages using the command.
Those are some of the commonly used options that are used with ss command. The command is considered more superior to netstat command and provide detailed information about network connections.
How can I monitor all outgoing requests/connections from my machine?
My machine is a server so I want to ignore connections being made to my server (e.g. when someone visits my website). I want to see only connections/requests being made by my server to other places. How do I see only those outgoing connections? EDIT: I’m new to these type of things. What I’m trying to do is just see if anything from my server is being sent out other than data for my web apps. For example, if someone visits my websites, then obviously my server will send out data to the client’s browser. But suppose there’s also code somewhere in my web app’s framework that sends statistical data to somewhere else I’m not aware of. I’d like to see those places my server is sending data to, if any. It’s probably not likely, but suppose you decide to use a php or nodejs framework that you didn’t write: there’s a small chance it may send some type of data somewhere. If so, that’s what I’d like to see.
7 Answers 7
$ netstat -nputw Active Internet connections (w/o servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name [. ] tcp 0 0 192.168.25.222:22 192.168.0.134:42903 ESTABLISHED 32663/sshd: gert [p lists all UDP ( u ), TCP ( t ) and RAW ( w ) outgoing connections (not using l or a ) in a numeric form ( n , prevents possible long-running DNS queries) and includes the program ( p ) associated with that.
Consider adding the c option to get output being updated continuously.
Completely inappropriate hijack (except that this answer googled well): This answer works with Windows as well. To use netstat in «continuous mode» there, -c doesn’t work. You use numbers instead, like netstat -na 1 | find «[Scan_Host_IP_Addr]» for it to update every 1 second (in this example). (source).
Is there a way to display more user-friendly information such as domain names, info about the ip? Perhaps using a custom script?
@awm Well, that would be doable with strace on the process, filtering for nameserver lookups (no details, this is not a full answer to it). Alternatively, you could show the reverse DNS of the IPs listed in netstat by omitting the n option included in my answer.
I’ve tried a bunch of tools, including iftop , ntop , iptraf , and of course the very useful built-in netstat -tupln (supported options are OS-dependent), but the most practical for my use case turned out to be nethogs — it aggregates connections by the originating app, and is the least noisy of all.
sudo apt-get install nethogs If your goal is to just see all TCP connections initiated by any app then you could use:
sudo tcpdump -i lo -A | grep Host: If you just want to just log every connection attempt, the easiest is probably iptables LOG target on Linux (or the equivalent firewall logging feature on your system).
If you need more information like duration of the connection and amount of data exchanged in both directions, then conntrackd (on Linux) is probably the best option.
However note that those two above only log the traffic that goes through netfilter, which is generally all the traffic but doesn’t account traffic generated with IP stacks in user space (like virtual machines or anything using raw sockets) or bridged traffic.
For more general solutions, you can have a look at things like argus , bro-ids , sancp or ntop that log all sorts of information based on traffic they sniff on an interface.
tcpdump allows you to see all IP traffic flowing to/from a specific interface with the ability to filter based on certain criteria. tcpdump is typically installed on most *nix systems by default, if not there’s usually a port somewhere to grab it for your specific distro.
What I think you want to do is get a list of listening ports and then remove them from any other TCP connections, then that will be all of the outgoing connections. The ss (socket status) command outputs «Local Address:Port» and «Peer Address:Port» columns, we need to remove the listening ports from the «Local Address:Port» column and not the «Peer Address:Port» column, otherwise you may miss some outgoing connections. So to achieve that I’m using \s+ behind the «:$port» string in the grep to match on the spaces that exist behind the «Local Address:Port» column; that column has two or more white spaces behind it, where the «Peer Address:Port» has one space and then a newline (grrr. should just have a newline, IMO, then I could have used \s+ instead of \s+ .) Normally I might try to use the filtering functionality of ss, like with ss -tn state established ‘(sport != : and sport !=:)’ src . But it appears there is a limit on how long that string can be, it bombed out on a system where I had a lot of listening ports. So I’m trying to do the same thing with grep. I believe the following will work:
FILTER=$(ss -tn state listening | gawk 'NR > 1 END +|", B[i]; printf ":%s\\s+", B[i]>') ss -tn state established dst :* | grep -P -v "$FILTER" Note this depends on the version of ss you’re using, older versions (like: ss utility, iproute2-ss111117) has a different output format, so you may have to use $3 instead of $4 in awk. Note also ss -tln and ss -tn state listening gives you different output, which is a little counter-intuitive to me. YMMV.
I found a slightly more elegant solution that doesn’t require knowing host’s IP, ss -tn state established dst :* works well, I modified the command lines above.