- Linux LDAP authentication (Using Linux LDAP)
- Step 1: Install OpenLDAP Server
- Step 2: Set Access Controls
- Step 3: Add Base Data to the LDAP Tree
- Step 3: Add Users
- Step 4: Set Up the Client LDAP Server
- Step 5: Configure NSS
- Step 6: Configure PAM
- Step 7: Create Home Folders at the Login
- Step 8: Enable sudo
- Conclusion
- About the author
- Kennedy Brian
- Ubuntu Wiki
- Release Note
- Rationale
- Use Cases
- Assumptions
- Design
- Implementation
- libpam-ldap
- libnss-ldap
- ldap-auth-client
- ldap-auth-config
- auth-client-config
- Configuration
Linux LDAP authentication (Using Linux LDAP)
This article will focus on using a Linux server to authenticate against the Linux directory. LDAP directories in Linux environments can either be local or network directories. Notably, network directories come in handy where and when there is a need for central authentication, while local directories operate within the same computer and not over a network.
While we will focus on LDAP protocol, discussing a Linux LDAP authentication is impossible without including NSS and PAM in the tutorial. Thus, we will also discuss how to configure NSS and PAM modules to work with client computers through the authentication process. This guide focuses on online authentication.
Step 1: Install OpenLDAP Server
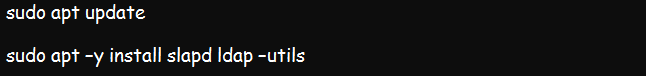
You will not authenticate with LDAP if you do not have it installed in your systems. So, the first step is ensuring that you have OpenLDAP installed in your system. We already discussed the installation process elaborately in our previous write-up.
This command should help you install OpenLDAP on Ubuntu 22:04:
Step 2: Set Access Controls
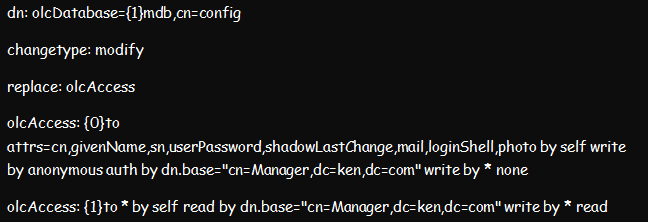
Once the installation process is complete, proceed to set up the access controls. Setting up the access controls ensures that no one can access and read any encrypted passwords from the LDAP server. Yet, users can still edit some of their attributes, such as personal passwords and photos.
You can achieve this setup by creating and importing the below ldif file. And once done, you can restart the slapd.service.
Step 3: Add Base Data to the LDAP Tree
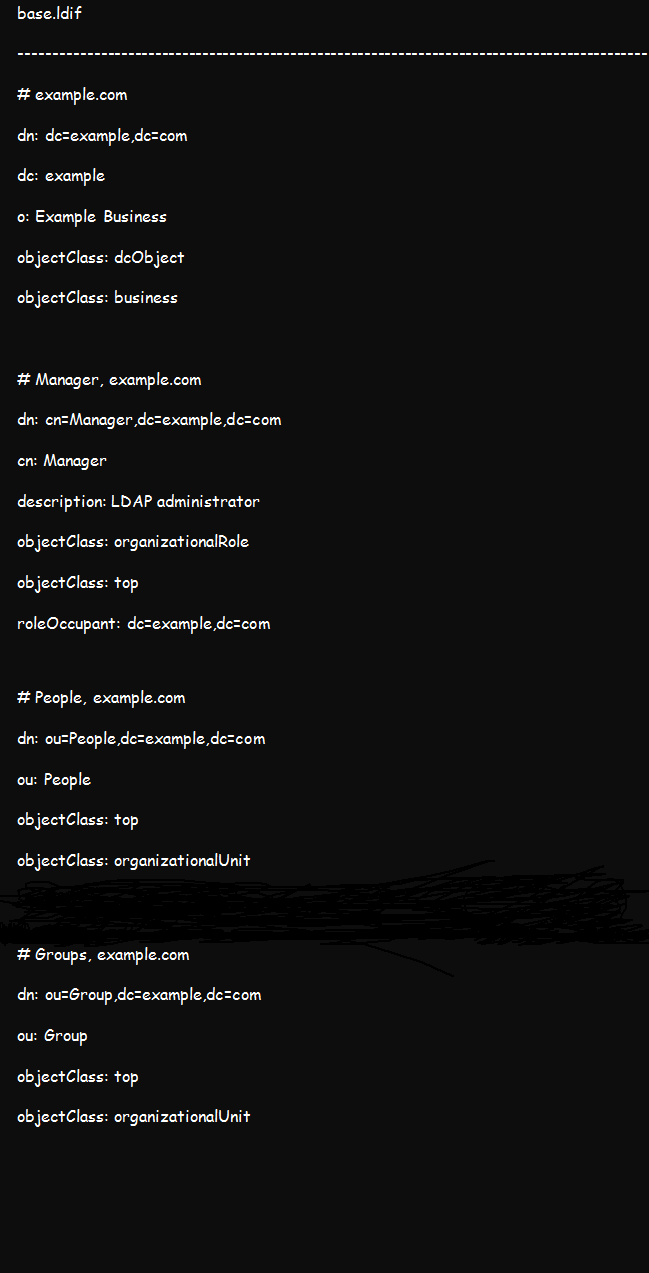
Create a temporary base.ldif file containing the following details:
You can customize the details by replacing example and org with your actual domain credentials. Once done, add the above details to your OpenLDAP tee using this command:
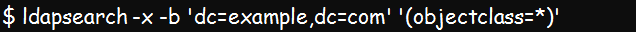
Test using the below command to confirm if the data importation was successful:
Step 3: Add Users
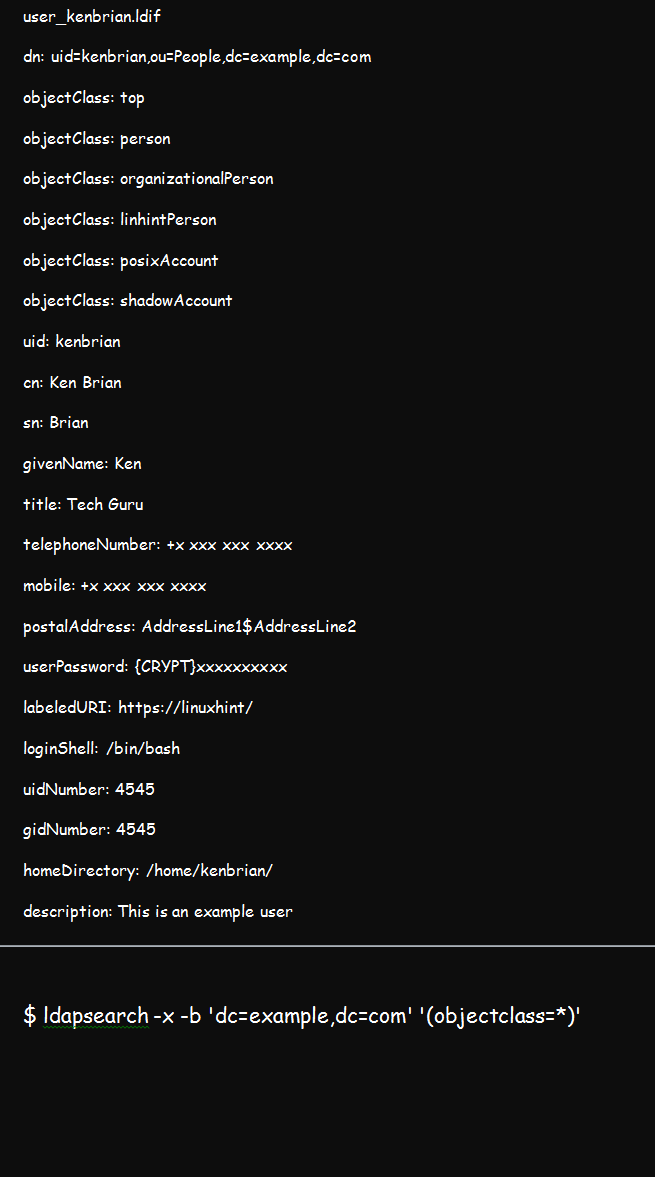
To add a user, you should create a .ldif file such as the one below. Our user for this demonstration is kenbrian and our domain credential is linhint.com.
The ********* present in the userPassword entry represents your password, which is the value of slappasswd or /etc/shadow. You can now add the user once you have the .ldif file using the below command:
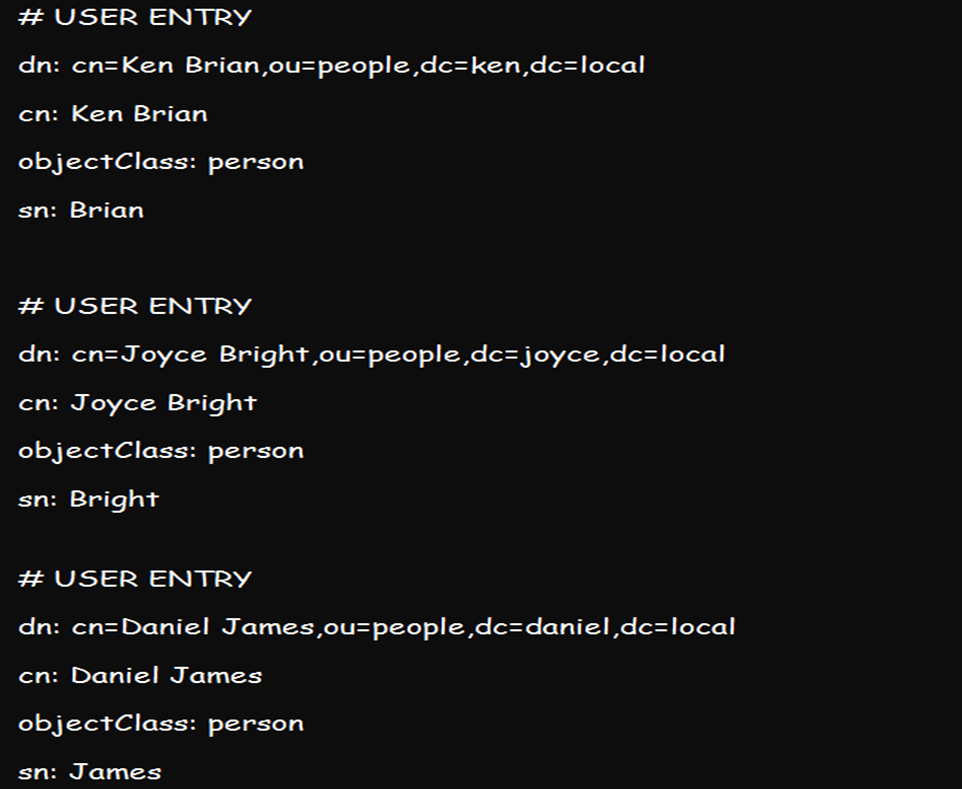
You can also use the ldapadd command to add more than one user to the directory by creating their various credentials all at once and adding them using the above utility. A list of credentials can look like this:
Step 4: Set Up the Client LDAP Server
You can set up an OpenLDAP server and ensure you can successfully query the server using the ldapsearch command. Once set up, you can decide whether to proceed with online and offline or online-only authentication.
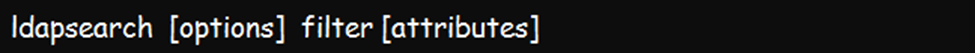
Below is the basic ldapsearch command line or syntax:
Step 5: Configure NSS
NSS, also known as Name Service Switch, is a system often used for managing configuration databases of different sources. So, you will find it vital in a range of LDAP applications. The following steps will be vital for configuring NSS:
- Install NSS using the nss-pam-ldapd package.
- Edit the NSS central configuration file, which is the /etc/nsswitch.conf. This file informs NSS of the files to use for respective system databases. Editing the file will require you to add ldap directives to the group, passwd, and shadow databases. Ensure that your edited file looks like this:
- You will also need to edit the /etc/nsswitch.conf. file to change the uri and base lines so that they fit your ldap server settings.
- If your LDAP server prompts for a password, edit both the bindpw and binddn sections. Continue to replace your /etc/nsswitch.conf permission from nslcd to 0600for a proper start.
- Use the systemd command to start the nslcd.service. With that, your LDAP users should be visible when you run getent passwd command on your client-server.
Step 6: Configure PAM
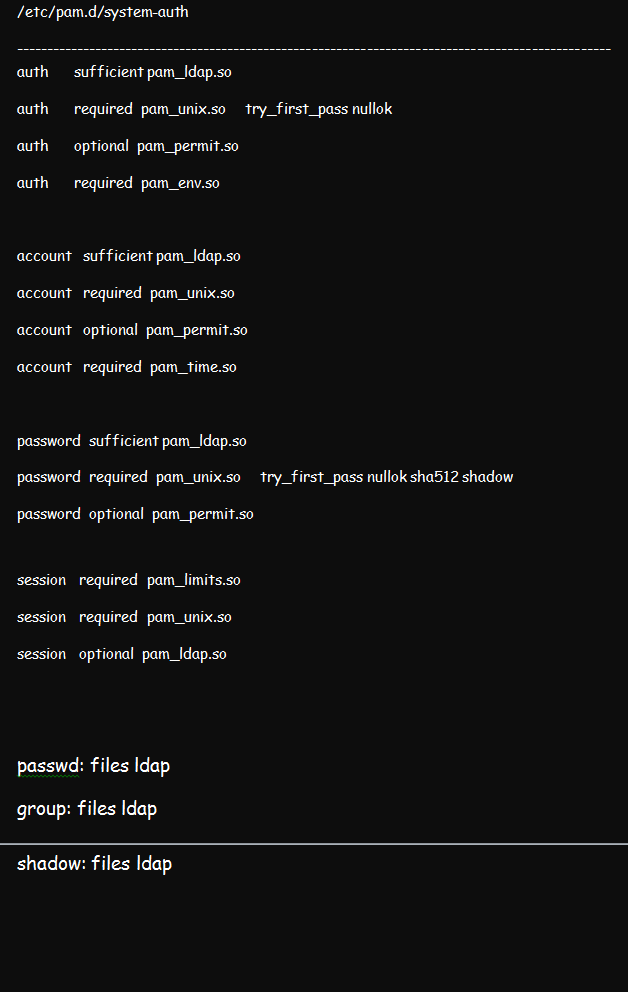
We discussed how to configure PAM in a Linux environment in a previous article. But for this illustration, ensure that you configure the Pluggable Authentication Module using the pam_ldap.so. While at that, edit the /etc/pam.d/system-auth file from pam.d. the result should be like in the figure below:
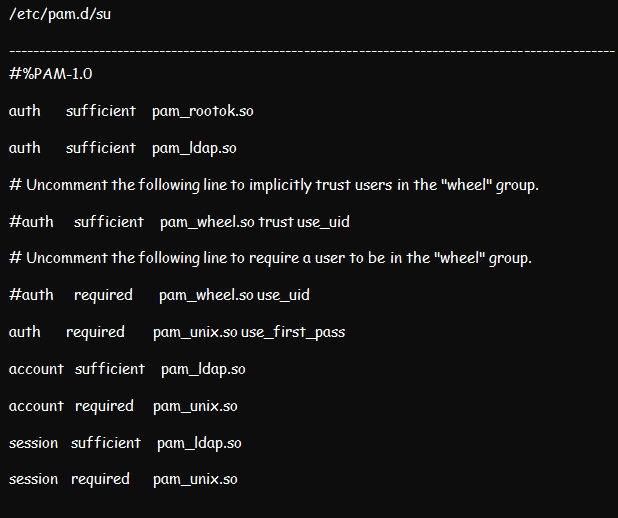
Proceed to edit the /etc/pam.d/su as well as the /etc/pam.d/su-l files. The /etc/pam.d/su-l file comes in handy whenever the /etc/pam.d/su login is run by the user. Place pam_ldap.so sufficient above each section except the pam_rootok.
Now, permit users to edit their passwords by making edits to the /etc/pam.d/passwd file.
Step 7: Create Home Folders at the Login
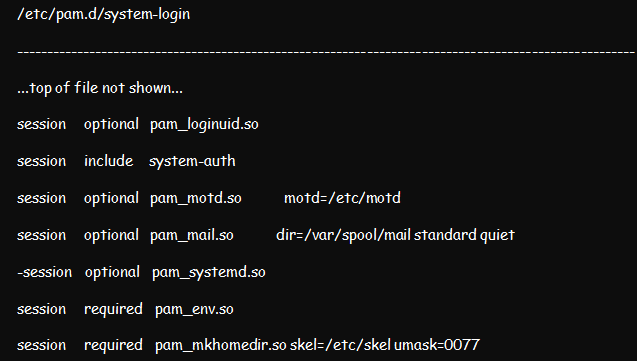
You can choose to create home folders at the login in case your system does not use NFS to store folders. Create a home folder at login by editing /etc/pam.d/system-login and then adding pam_mkhomedir.so to session sections above all sufficient items.
Step 8: Enable sudo
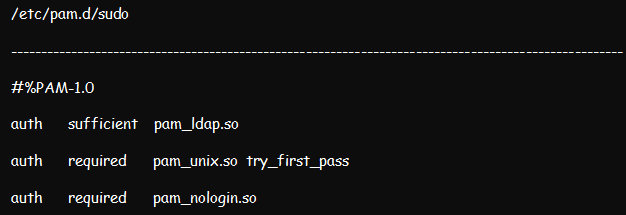
Enable sudo from the LDAP user by editing /etc/pam.d/sudo and modifying it appropriately.
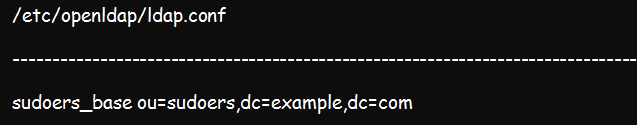
Add the command below to the /etc/openldap/ldap.conf file:
Conclusion
The above steps should help you implement an online authentication of Linux LDAP alongside PAM and NSS. This system comes in handy in securing your systems. More importantly, you can use it to query and manage your company information.
About the author
Kennedy Brian
Brian is a computer scientist with a bias for software development, programming, and technical content development. He has been in the profession since 2015. He reads novels, jogs, or plays table tennis whenever not on gadgets. He is an expert in Python, SQL, Java, and data and network security.
Ubuntu Wiki
Currently, in Ubuntu and Debian the packages libpam-ldap and libnss-ldap create separate configuration files and secret files. A ldap-auth-config package will be created that owns /etc/ldap.conf and /etc/ldap.secret. libpam-ldap and libnss-ldap will depend on ldap-auth-config. An ldap-auth-client meta package will be created that depends on libpam-ldap, libnss-ldap. The ldap-auth-client meta source package will contain the ldap-auth-config package. The ldap-auth-config package will own the config files, and the debconf scripts that were previously in libnss-ldap and libpam-ldap.
An auth-client-config package has been created to allow any package to configure nssswitch.conf and /etc/pam.d/*.
The main purpose of this spec is to fix the specified packages to bring them inline with the upstream authors intentions, and give Ubuntu a better base for LDAP authentication configuration ui’s.
Release Note
ldap-auth-client enables simplified installation and configuration of LDAP client systems.
Rationale
It is currently difficult to configure an Ubuntu client to use LDAP for authentication. It is a good idea to put all necessary packages and configuration under one meta package, to allow easier installation and configuration. The libpam-ldap and libnss-ldap packages, diverge from the original authors intentions, and the implementations of other Linux distributions. Furthermore, the Debian packages use different naming schemes for each package. This puts Ubuntu at a competitive disadvantage and is unnecessarily complicated for our users.
Use Cases
A medium size business has existing Linux/UNIX infrastructure that uses LDAP for authentication, and wants to use Ubuntu as a desktop client, to replace Redhat. The Sys admin wants to provide simple instructions for jr admins to add clients to the network.
Bob wants to use LDAP for NSS on a SMTP server, but want to authenticate locally.
Alice configured openldap as a client in Dapper or Feisty, and wants to upgrade to Gutsy.
Assumptions
libpam-ldap and libnss-ldap, which are linked to openldap2.1, will at least be minimally useful when used with an openldap2.3 server, or other ldap implementation.
There are no packages not identified in the spec that rely on the current libpam-ldap or libnss-ldap configuration files.
Design
Implementation
libpam-ldap
Remove the following files from the package:
debian/patches/00chfn.patch : This patch modifies the location/name ldap.conf in the chfn script.
debian/patches/00chsh.patch : This patch modifies the location/name ldap.conf in the chsh script.
Modify debian/rules to prevent the following files from being created:
Modify debian/libpam-ldap.postinst to remove configuration information, which will be handled instead by ldap-auth-config.
Add ldap-auth-config dependancy to debian/control.
libnss-ldap
Remove the following files from the package:
debian/patches/00debian_conf.patch : This patch modifies the location/name ldap.conf.
Modify debian/rules to prevent the following files from being created:
Modify debian/libnss-ldap.postinst to remove configuration information, which will be handled instead by ldap-auth-config.
Add ldap-auth-config dependancy to debian/control.
ldap-auth-client
Create a ldap-auth-client meta package that depends on libnss-ldap and libpam-ldap.
ldap-auth-config
Create a package that will install and configure /etc/ldap.conf and /etc/ldap.secret
auth-client-config
nssswitch.conf and /etc/pam.d/* will be managed by a new package called auth-client-config. Templates will be provided for different usecases, and the files will be configured accordingly. This package has already been created, is in universe and is undergoing community review for inclusion in main.
Currently, there is no functionality to migrate users from files to LDAP. That must be done by hand with tools that are already packaged. (migrationtools)
Configuration
All configuration will be done in ldap-client-config’s postinst.
If /etc/libnss-ldap.conf or /etc/pam_ldap.conf exist, preserve the exist files and notify user that he must manually migrate the files.
If /etc/libnss-ldap.conf and /etc/pam_ldap.conf !exist the postinst in ldap-auth-config will prompt for data and create /etc/ldap.conf