- Linux LDAP authentication (Using Linux LDAP)
- Step 1: Install OpenLDAP Server
- Step 2: Set Access Controls
- Step 3: Add Base Data to the LDAP Tree
- Step 3: Add Users
- Step 4: Set Up the Client LDAP Server
- Step 5: Configure NSS
- Step 6: Configure PAM
- Step 7: Create Home Folders at the Login
- Step 8: Enable sudo
- Conclusion
- About the author
- Kennedy Brian
- LDAP Authentication From the Command Line in Linux
- 1. Overview
- 2. Authentication Using ldapsearch Command
- 2.1. Using Anonymous Bind
- 2.2. Using Simple Bind
- 2.3. Using SASL
- 3. Authentication Using ldapwhoami Command
- 3.1. Using Anonymous Bind
- 3.2. Using Simple Bind
- 3.3. Using SASL Authentication
- 4. Conclusion
Linux LDAP authentication (Using Linux LDAP)
This article will focus on using a Linux server to authenticate against the Linux directory. LDAP directories in Linux environments can either be local or network directories. Notably, network directories come in handy where and when there is a need for central authentication, while local directories operate within the same computer and not over a network.
While we will focus on LDAP protocol, discussing a Linux LDAP authentication is impossible without including NSS and PAM in the tutorial. Thus, we will also discuss how to configure NSS and PAM modules to work with client computers through the authentication process. This guide focuses on online authentication.
Step 1: Install OpenLDAP Server
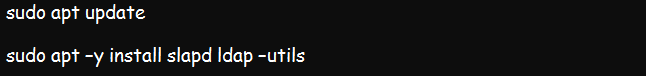
You will not authenticate with LDAP if you do not have it installed in your systems. So, the first step is ensuring that you have OpenLDAP installed in your system. We already discussed the installation process elaborately in our previous write-up.
This command should help you install OpenLDAP on Ubuntu 22:04:
Step 2: Set Access Controls
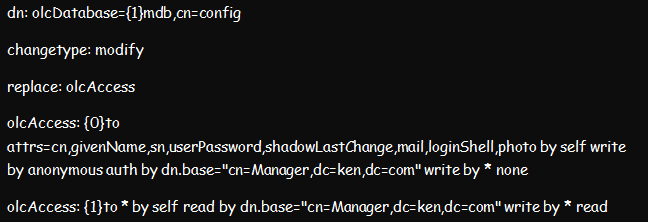
Once the installation process is complete, proceed to set up the access controls. Setting up the access controls ensures that no one can access and read any encrypted passwords from the LDAP server. Yet, users can still edit some of their attributes, such as personal passwords and photos.
You can achieve this setup by creating and importing the below ldif file. And once done, you can restart the slapd.service.
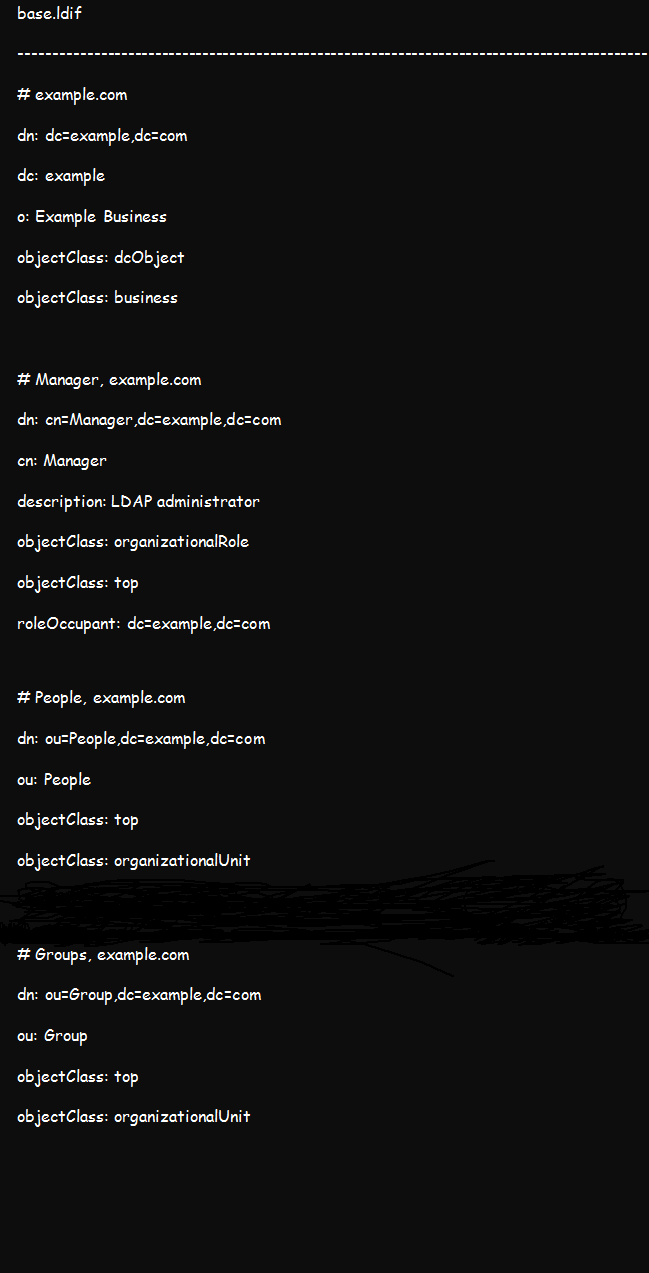
Step 3: Add Base Data to the LDAP Tree
Create a temporary base.ldif file containing the following details:
You can customize the details by replacing example and org with your actual domain credentials. Once done, add the above details to your OpenLDAP tee using this command:
Test using the below command to confirm if the data importation was successful:
Step 3: Add Users
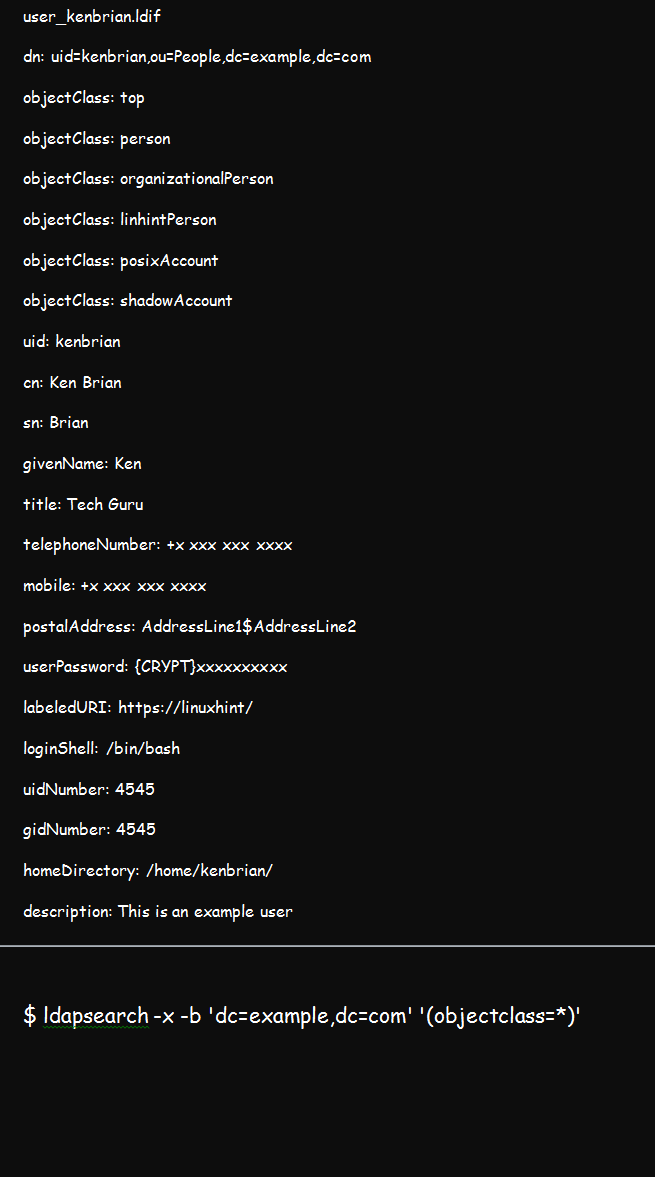
To add a user, you should create a .ldif file such as the one below. Our user for this demonstration is kenbrian and our domain credential is linhint.com.
The ********* present in the userPassword entry represents your password, which is the value of slappasswd or /etc/shadow. You can now add the user once you have the .ldif file using the below command:
You can also use the ldapadd command to add more than one user to the directory by creating their various credentials all at once and adding them using the above utility. A list of credentials can look like this:
Step 4: Set Up the Client LDAP Server
You can set up an OpenLDAP server and ensure you can successfully query the server using the ldapsearch command. Once set up, you can decide whether to proceed with online and offline or online-only authentication.
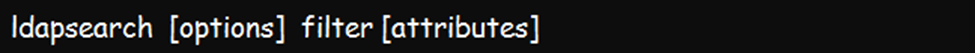
Below is the basic ldapsearch command line or syntax:
Step 5: Configure NSS
NSS, also known as Name Service Switch, is a system often used for managing configuration databases of different sources. So, you will find it vital in a range of LDAP applications. The following steps will be vital for configuring NSS:
- Install NSS using the nss-pam-ldapd package.
- Edit the NSS central configuration file, which is the /etc/nsswitch.conf. This file informs NSS of the files to use for respective system databases. Editing the file will require you to add ldap directives to the group, passwd, and shadow databases. Ensure that your edited file looks like this:
- You will also need to edit the /etc/nsswitch.conf. file to change the uri and base lines so that they fit your ldap server settings.
- If your LDAP server prompts for a password, edit both the bindpw and binddn sections. Continue to replace your /etc/nsswitch.conf permission from nslcd to 0600for a proper start.
- Use the systemd command to start the nslcd.service. With that, your LDAP users should be visible when you run getent passwd command on your client-server.
Step 6: Configure PAM
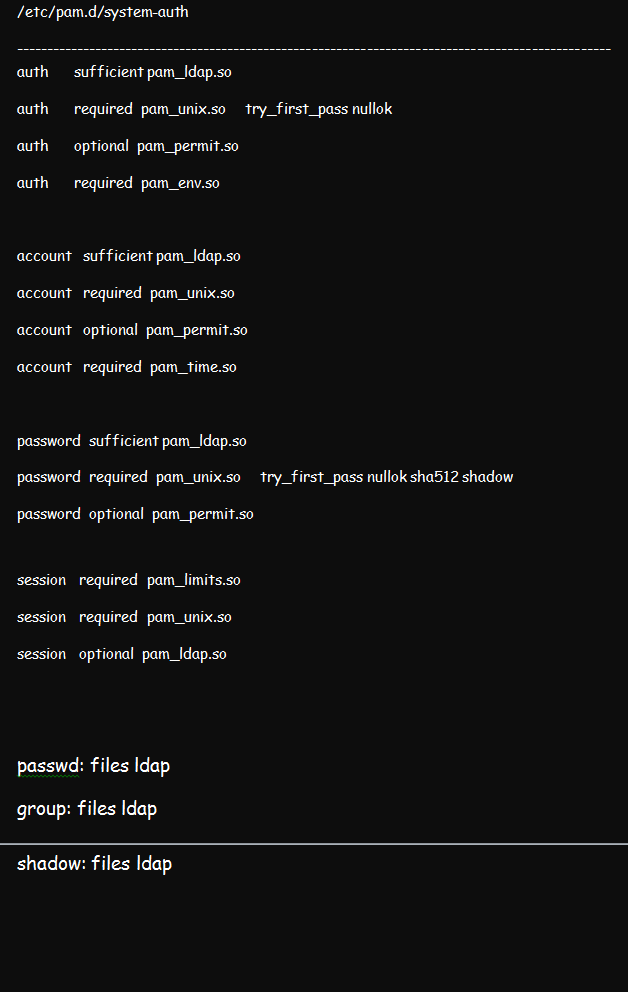
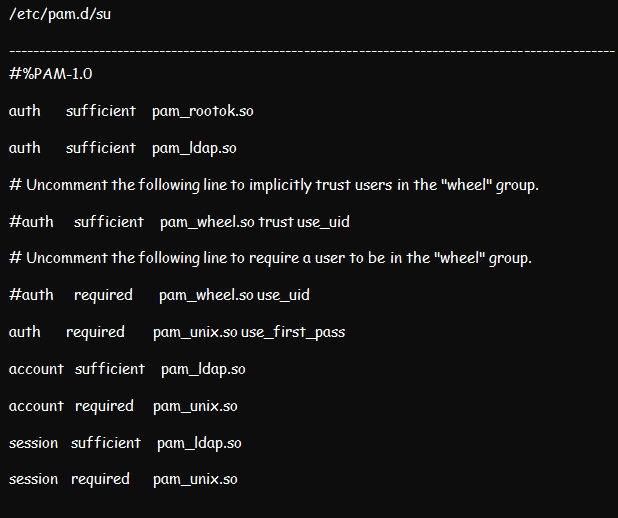
We discussed how to configure PAM in a Linux environment in a previous article. But for this illustration, ensure that you configure the Pluggable Authentication Module using the pam_ldap.so. While at that, edit the /etc/pam.d/system-auth file from pam.d. the result should be like in the figure below:
Proceed to edit the /etc/pam.d/su as well as the /etc/pam.d/su-l files. The /etc/pam.d/su-l file comes in handy whenever the /etc/pam.d/su login is run by the user. Place pam_ldap.so sufficient above each section except the pam_rootok.
Now, permit users to edit their passwords by making edits to the /etc/pam.d/passwd file.
Step 7: Create Home Folders at the Login
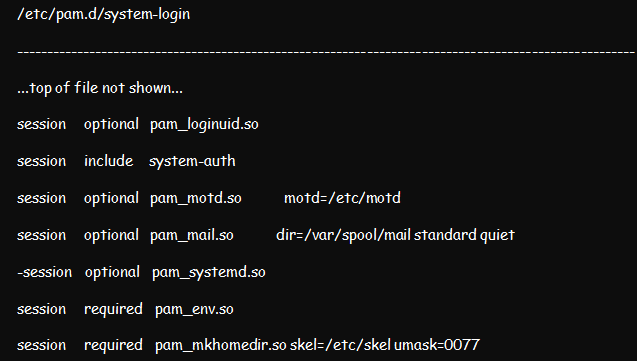
You can choose to create home folders at the login in case your system does not use NFS to store folders. Create a home folder at login by editing /etc/pam.d/system-login and then adding pam_mkhomedir.so to session sections above all sufficient items.
Step 8: Enable sudo
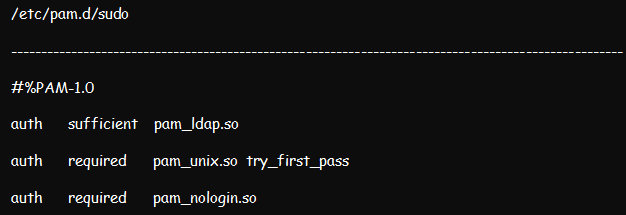
Enable sudo from the LDAP user by editing /etc/pam.d/sudo and modifying it appropriately.
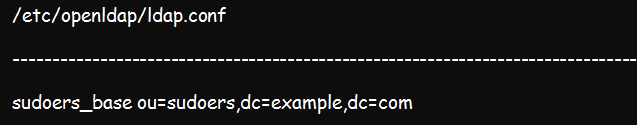
Add the command below to the /etc/openldap/ldap.conf file:
Conclusion
The above steps should help you implement an online authentication of Linux LDAP alongside PAM and NSS. This system comes in handy in securing your systems. More importantly, you can use it to query and manage your company information.
About the author
Kennedy Brian
Brian is a computer scientist with a bias for software development, programming, and technical content development. He has been in the profession since 2015. He reads novels, jogs, or plays table tennis whenever not on gadgets. He is an expert in Python, SQL, Java, and data and network security.
LDAP Authentication From the Command Line in Linux
The Kubernetes ecosystem is huge and quite complex, so it’s easy to forget about costs when trying out all of the exciting tools.
To avoid overspending on your Kubernetes cluster, definitely have a look at the free K8s cost monitoring tool from the automation platform CAST AI. You can view your costs in real time, allocate them, calculate burn rates for projects, spot anomalies or spikes, and get insightful reports you can share with your team.
Connect your cluster and start monitoring your K8s costs right away:
1. Overview
Clients usually provide authentication information to an LDAP server. Based on that, the LDAP server then figures out how much access to give the client.
In this tutorial, we’ll see how to perform LDAP authentication from the command line in Linux. Also, we’ll look at different authentication methods that apply here.
We’re using an Ubuntu 20.04 system. Also, we’ve already set up the OpenLDAP server, an LDAP implementation. Our base distinguished name (DN) is dc=example, dc=com. The admin user for this entry is cn=admin,dc=example,dc=com. The password for this user is the one chosen while setting up the slapd (stand-alone LDAP daemon) package.
2. Authentication Using ldapsearch Command
We can use the ldapsearch command to perform LDAP authentication. In essence, we can use three different authentication schemes:
Notably, SASL is a more complex approach.
Let’s see each one of them.
2.1. Using Anonymous Bind
Anonymous bind is the most basic method of client authentication. It’s used when there’s no need for authentication, i.e., for certain public areas of the LDAP directory. In such cases, a user requires no identity or password for the given operations against the LDAP server.
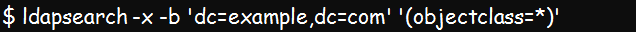
Let’s process a search against our server using the ldapsearch command. Basically, the ldapsearch command looks for the entries in the LDAP database and returns the results.
Now, let’s use the -x option with the ldapsearch command for an anonymous bind:
$ ldapsearch -x -LLL -H ldap:/// -b dc=example,dc=com dndn: dc=example,dc=com dn: cn=admin,dc=example,d. dn: ou=People,dc=example. .
Since we’ve not given any Bind DN using the -D option, no password is needed. Consequently, we have an anonymous bind.
2.2. Using Simple Bind
In simple authentication or simple bind, the DN of the account entry verifies that account for authentication. Along with that, it uses a password to confirm who we are.
Here’s the syntax for a simple bind or plain text authentication command:
$ ldapsearch -x -H ldap://ldap-server-hostname_or_IP -D "cn=username,ou=users,dc=example,dc=com" -W -b "dc=example,dc=com"We can put the values in the above expression as per our requirements:
- ldap-server-hostname– LDAP server’s hostname or IP address
- -D – user we want to authenticate with
- -b – DN of the search base
Now, let’s see this command in action by trying to authenticate our admin user:
$ ldapsearch -x -D "cn=admin,dc=example,dc=com" -W -H ldap://192.168.62.163 -b "ou=People,dc=example,dc=com" . id: baeldung cn: Baeldung Linux displayName: Baeldung Linux uidNumber: 10000 gidNumber: 5000 loginShell: /bin/bash . Importantly, the -x option means we use simple authentication. The -W option asks for the password of the user at runtime.
Since we’re working at the local server end, we can avoid using the LDAP server’s hostname or IP address. Thus, we can simply use the ldap:/// notation in this context.
2.3. Using SASL
SASL allows LDAP to work with any accepted authentication method between the LDAP client and server:
$ sudo ldapsearch -Q -LLL -Y EXTERNAL -H ldapi:/// -b "dc=example,dc=com" dn dn: dc=example,dc=com dn: cn=admin,dc=example,dc=com dn: ou=People,dc=example,dc=com dn: ou=Groups,dc=example,dc=com . Since we’re working on a local server, we can again leave out the server domain name or IP address. However, the ldapi scheme needs a local connection.
The -Q option enables the SASL quiet mode, while the -LLL option just formats the output style. In addition, the -Y option sets the SASL mechanism for authentication, EXTERNAL in this example.
3. Authentication Using ldapwhoami Command
Another way to perform LDAP authentication from the command line in Linux is via the ldapwhoami command. Basically, it has pretty much the same command structure as the ldapsearch command. Also, we can again use anonymous bind, simple bind, and SASL authentication here.
3.1. Using Anonymous Bind
First, let’s see how we can use ldapwhoami command with anonymous bind:
$ ldapwhoami -x -H ldap:/// anonymousAgain, the -x option indicates an anonymous bind. Further, providing no bind DN via the -D option confirms it as such.
3.2. Using Simple Bind
Let’s use ldapwhoami to authenticate our admin user using simple bind:
$ ldapwhoami -x -H ldap:/// -D "cn=admin,dc=example,dc=com" -W Enter LDAP Password: dn:cn=admin,dc=example,dc=comOn successful authentication, we see the DN of the user as the output. Otherwise, we see an error message.
Notably, the options in the above command are the same as the ones used in the ldapsearch case.
3.3. Using SASL Authentication
SASL authentication can also work in a similar way to simple bind with ldapwhoami. Again, in this case, we’re dealing with a local server. Thus, we don’t need to put in the server’s IP here:
$ ldapwhoami -Y EXTERNAL -H ldapi:/// -Q dn:gidNumber=1000+uidNumber=1000,cn=peercred,cn=external,cn=authFor successful authentication, we’ll get the uid and gid of the connecting user along with the suffix cn=peercred,cn=external,cn=auth.
4. Conclusion
In this article, we’ve seen how to perform LDAP authentication from the command line. Overall, clients connecting to LDAP servers should be authorized through an authentication mechanism. An anonymous authentication performs an LDAP request without first doing a bind. In such a case, a client sees a limited view of the LDAP directory.
In simple authentication, the client’s password is sent in clear text along with the DN of the client (user). This makes it easy for an attacker to acquire the password from the network. It’s therefore a security problem. Thus, best practices dictate always using simple authentication over SSL/TLS.
With SASL, applications should find the best way to communicate and authenticate with each other. SASL lets us authenticate LDAP with more than just simple passwords and SSL.