Force Linux User to Change Password
If we create a user account with the default password, we can use this trick to force the user to change their account’s default password when they first login to their account. This will hopefully improve the security of their account. We can achieve this in two ways.
Using passwd Command
The passwd command is used to change the password of a user account. A normal user can run passwd to change their own password, and the root user can use passwd to change another user’s password or define how each user account’s password can be used or changed.
To force a user to change his password we use passwd command with -e or –expire switches. The –expire or -e switches will expire current password of the user account and forcing the user to change the current password to a new one on next login.
# passwd –expire test
Expiring password for user test.
passwd: Success
To verify the password expiration and aging information of user account test, we can use the chage command.
# chage -l test
Last password change : password must be changed
Password expires : password must be changed
Password inactive : password must be changed
Account expires : never
Minimum number of days between password change : 0
Maximum number of days between password change : 99999
Number of days of warning before password expires : 7
After setting the password expiration user will get the below screen on next login.
ssh test@159.89.174.23
test@159.89.174.23’s password:
You are required to change your password immediately (root enforced)
Last login: Tue Mar 13 04:22:24 2018 from 202.83.46.160
WARNING: Your password has expired.
You must change your password now and login again!
Changing password for user test.
Changing password for test.
(current) UNIX password:
New password:
Retype new password:
passwd: all authentication tokens updated successfully.
Connection to 159.89.174.23 closed.
Using chage command
The chage command changes the number of days between password changes and the date of the last password change. This information is used by the system to determine when a user must change his/her password.
Alternatively, we can use the chage command with -d or –lastday switches.
-d, –lastday LAST_DAY
Set the number of days since January 1st, 1970 when the password was last changed. The date may also be expressed in the format YYYY-MM-DD (or the format more commonly used in your area). If the LAST_DAY is set to 0 the user is forced to change his password on the next log on.
For this, we run the below command.
This command will tell the server that the password has not been changed since the above date (i.e. January 1st, 1970), so the password has literally expired and needs to be changed immediately before the user can access the server again.
To verify the user account test1’s password expiration and aging information we can use the below command.
When the user test1 try to login the server after the password expiration has been set, the user will get the below screen and force the user to change the password.
$ ssh test1@159.89.174.23
test1@159.89.174.23’s password:
You are required to change your password immediately (root enforced)
Last login: Tue Mar 13 05:33:55 2018 from 202.83.46.160
WARNING: Your password has expired.
You must change your password now and login again!
Changing password for user test1.
Changing password for test1.
(current) UNIX password:
New password:
Retype new password:
passwd: all authentication tokens updated successfully.
It is always recommended to remind users to change their account passwords regularly for security reasons. So we can use the above methods for forcing the user to change their password.
If you need any further assistance please contact our support department.
How to Force User to Change Password at Next Login in Linux
In our last article, we’ve explained you how to change user password expiry information in Linux, where we looked at different examples of the chage command. In this article, we will elaborate on how to forcefully make a user to change his/her password at the next login in Linux.
Note that if you have just created a user account with a default password, you can also use this trick to force that user to change their password upon the first login.
There are two possible ways to achieve this, as described in detail, below.
Using passwd Command
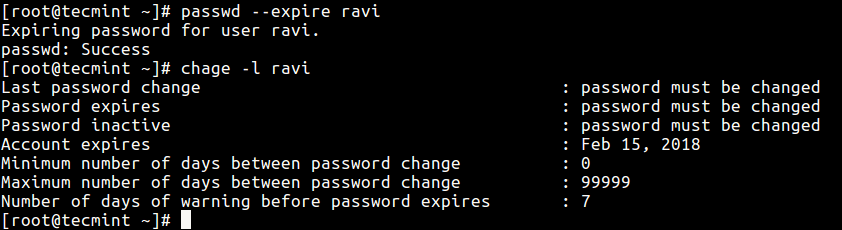
To force a user to change his/her password, first of all the password must have expired and to cause a user’s password to expire, you can use the passwd command, which is used to change a user’s password by specifying the -e or —expire switch along with username as shown.
Next verify the user ravi’s password expiration and aging information with the chage command as shown.
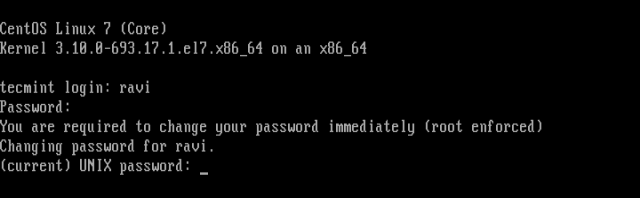
After running the passwd command above, you can see from the output of the chage command that the user’s password must be changed. Once the user ravi tries to login next time, he will be prompted to change his password before he can access a shell as shown in the following screen shot.
Using chage Command
Alternatively, you can use the chage command, with the -d or —lastday option which sets the number of days since January 1st, 1970 when the password was last changed.
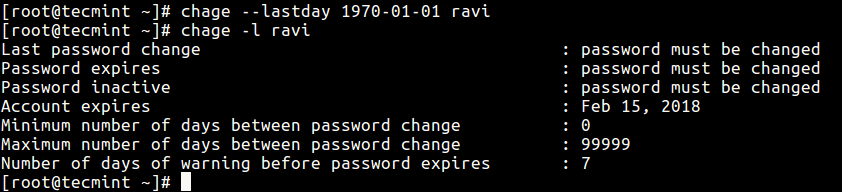
Now to set the password expiry of user, run the following command by specifying the day to zero (0), means that the password has not been changed since the above date (i.e. January 1st, 1970), so the password has literally expired and needs to be changed immediately before the user can access the system again.
# chage --lastday 0 ravi OR # chage --lastday 1970-01-01 ravi
Next check the user ravi’s password expiration and aging information with the chage command using -l option as shown.
Here are some additional user management guides for you.
Conclusion
It is always recommended to remind users to change their account passwords regularly for security reasons. In this article, we have explained two ways to force users to change their password in the next login. You can ask any questions via the comment form below.
How to force change linux password even if similar as previous
I am trying to change my current password in Red Hat Enterprise Linux Server release 5.10 (Tikanga) but it says my new password is too similar. Is there any way to force change ?
$ passwd Changing password for user XY Changing password for XY (current) UNIX password: New UNIX password: BAD PASSWORD: is too similar to the old one New UNIX password: I did not want to change to same password. let say I have Bilbo1 and I want to change to Bilbo2, I get message above: «BAD PASSWORD: is too similar to the old one». SO I am not changing to same password
If you had bothered to read the answers to that question, you’d have realized why you’re in the same position and how to resolve your problem.
@darnir, duplicates are when the question is already asked in same SO site. This one can not be a duplicate 🙂
5 Answers 5
If you can run the command as root, you can force the change to be accepted.
$ sudo passwd myusername Changing password for user myusername. New password: Retype new password: passwd: all authentication tokens updated successfully. If the user had super user access, they might as well change whatever settings enables these silly password restrictions. Since they are not asking about this, I’m assuming they do not have root access.
- change twice, e.g. old passwd is Bilbo1,
- change to Frodo1 (from Bilbo1),
- then change to Bilbo2 (from Frodo1).
- on the first change, Linux can only compare clear text Bilbo1 and Frodo1,
- on second Linux can only compare Frodo1 and Bilbo2 (and all the crypted passwd, you can’t revert to Bilbo1(*)).
- This suppose you can change twice, which may have been disable by your system admin, to prevent such work arround.
Needless to say, do not use such a silly password.
(*) On second tought, I am not sure about this point in Linux.
I did not want to change to same password. let say I have Bilbo1 and I want to change to Bilbo2, I get message above: «BAD PASSWORD: is too similar to the old one». SO I am not changing to same password
well, while trying change from Frodo1 to Bilbo2 I got message that: «You must wait longer to change your password» LOL
that was my third point. my favourite password pattern is Bilbo00 / Frodo00 with 00 the current month.
On CentOS, you can also use the -f option to force the password change.
$ passwd -f username Changing password for user username. New password: Retype new password:Since passwd uses PAM, you would have to modify the file: /etc/pam.d/common-password on Debian based systems like Ubuntu, or /etc/pam.d/system-auth on RedHat based systems.
The other answers solve the problem for most users. However, if you’re an admin using a Linux system with PAM, and want this policy removed for all users to change their password without needing to use sudo or root, then this needs to be changed in the PAM settings.
I don’t know about RHEL, but on Ubuntu, you can edit /etc/pam.d/common-password. There should be a line somewhere like this
password [success=1 default=ignore] pam_unix.so obscure use_authtok try_first_pass sha512The obscure keyword tells PAM to do a series of checks that compares the new password to the old password, and makes sure that the new password is different enough from the old one in the following ways
- The new password is not a palindrome of the old one
- The new password isn’t just a case change of the old one
- The new password isn’t too much like the previous one (the issue here)
- The password isn’t too simple
- The password isn’t just a rotated version of the old one
More information can be found in man pam_unix
Removing this keyword and refreshing PAM would mean that the checks will not be done anymore. However, keep in mind that this may encourage bad passwords to be used and may affect the security of your system.
Try:
sudo busybox passwd XY
(XY is your user name)I have used the root privilege to set a weak password for a normal user, with a warning, but it worked in the end.
But I tried again recently and it failed.
My final solution is to use busybox’s internal passwd program, which is a different program, and it works.My system is gentoo, and after checking, the default passwd is from sys-apps/shadow-4.8.1-r2.
duke@duke-pc ~ $ sudo passwd duke You can now choose the new password or passphrase. A good password should be a mix of upper and lower case letters, digits, and other characters. You can use a password that consists of 8 characters. A passphrase should be of at least 3 words, 8 to 40 characters long, and contain enough different characters. Alternatively, if no one else can see your terminal now, you can pick this as your password: "sleep=Medal2brim". Enter new password: Weak password: too short. Try again. (. ) You can now choose the new password or passphrase. A good password should be a mix of upper and lower case letters, digits, and other characters. You can use a password that consists of 8 characters. A passphrase should be of at least 3 words, 8 to 40 characters long, and contain enough different characters. Alternatively, if no one else can see your terminal now, you can pick this as your password: "Freeze+six7nazi". Enter new password: Weak password: based on a dictionary word and not a passphrase. passwd: Authentication token manipulation error passwd: password unchanged duke@duke-pc ~ $ duke@duke-pc ~ $ sudo busybox passwd duke Changing password for duke New password: Bad password: too weak Retype password: passwd: password for duke changed by root duke@duke-pc ~ $