- How to Change or Set User Password in Linux
- Changing a User Password in Linux
- Managing Linux Users with the passwd Command
- Remove User Password in Linux
- Lock User Password in Linux
- Unlock User Password in Linux
- Force User to Change Password in Linux
- Change or set password interactively prompt in linux
- How to Use Pass, a Command-Line Password Manager for Linux Systems
- Getting Setup
- Adding Passwords to the Store
- Retrieving Your Passwords
- Multiline Passwords
- Git Integration
- Interacting with Other Tools
- Automated change password on linux servers
- Kali linux how to change password
- when i change password in kali linux dont’t change
- How to pass password to scp?
How to Change or Set User Password in Linux
As a regular user, you have a password that safeguards your account, and this account contains all your personal settings and files and therefore requires important protection.
Hence, it is a good practice to change your password consistently to decrease the possibility that someone else gets to recognize your password and can use your credentials to authenticate.
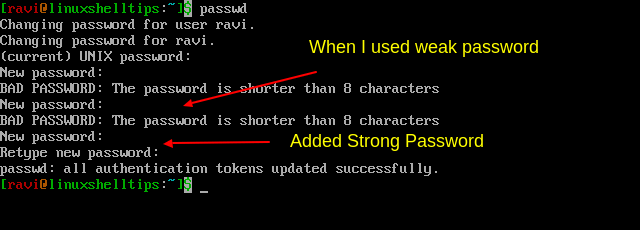
When changing a user password, make sure it meets the following minimal requirements:
- A password must be strong: at least six or eight characters or more is better.
- Make sure to use complex passwords by mixing letters, numbers, and other characters to make the password as hard to guess as possible.
- Use upper and lowercase letters to make the password harder to crack by an attacker.
- Make sure to avoid using any dictionary word as a password, because attackers use a brute-force password cracker to scan the whole contents of a dictionary, and if your password is in the dictionary, they can easily crack it.
Changing a User Password in Linux
Changing a user password is not that hard, just use the passwd command to change the password of your own account (it could be a root user or regular user).
Now, you need to enter your old password, as this is to prevent others from changing your password. Next, you need to enter the new password twice and make sure that your password meets the complexity rules as explained above; else, it will not be changed.
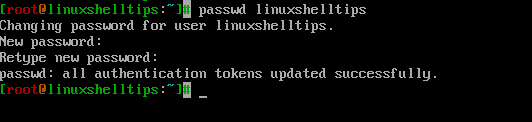
If you are logged in as a root user, you can change the password of other system users by typing the passwd command followed by the name of the user whose password you want to change.
It won’t prompt you for the old password, since you are logged in as a root user, you should be able to change the user’s passwords without knowing the old password.
Managing Linux Users with the passwd Command
There are other useful options that you can use while changing a user’s password and they are:
Remove User Password in Linux
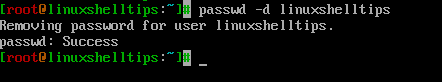
Use the -d argument to remove the password for the specified user account.
Lock User Password in Linux
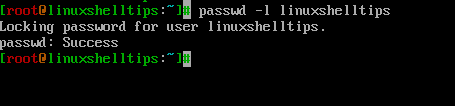
Use the -l argument to lock the password for a user account if it is not used for a given period of time.
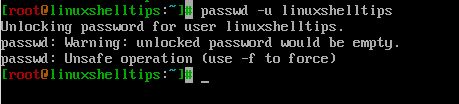
Unlock User Password in Linux
Use the -u argument to unlock the user password that has been locked with -l option.
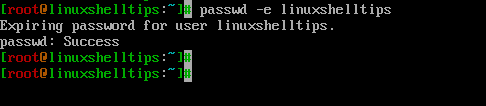
Force User to Change Password in Linux
Use the -e argument to force the user to change the password during the next login attempt.
The passwd command is pretty useful to manage system users on your Linux system. It manipulates the user entries in the /etc/passwd file, and the system administrator must have this as a toolkit.
Change or set password interactively prompt in linux
That results in only a single place where to enforce password policies and/or reset passwords for your admins and users. Typically such a system will also periodically reset privileged account passwords and after an admin was granted access to a system such software will also reset the password again, to deny the admin future access when i change password in kali linux dont’t change Solution 1: Use sshpass: or so the password does not show in the bash history The above copies contents of path from the remote host to your local.
How to Use Pass, a Command-Line Password Manager for Linux Systems
Pass is a command-line password manager built with the Unix philosophy in mind. It enables you to interact with your passwords using regular Unix commands. Credentials are stored in GPG-encrypted files.
Getting Setup
pass is available within the package managers of most popular Linux distributions. Try to install it as pass using the package manager relevant to you, such as apt for Ubuntu/Debian or yum for Fedora/RHEL. Specific guidance for each supported distribution is available on the Pass website.
Before continuing, you’ll need a GPG key available. The key will be used to encrypt the contents of your password store. You can create a new one using the following terminal command:
Follow the prompts to create your key, taking care to note down its ID. You should use the default key type (RSA and RSA) but change the keysize to 4,096 bits for maximum security.
With your GPG key available, you’re now ready to initialise pass . Run the following command, substituting placeholder-gpg-id with your own GPG ID.
pass init placeholder-gpg-key
A new directory, .password-store , will be created within your home folder. Pass will store your passwords here. Each password gets its own file, making it simple to backup credentials either individually or en masse.
You can optionally use multiple password stores by setting the PASSWORD_STORE_DIR environment variable in your shell. This enables you to override the default store directory and access passwords stored in an arbitrary location.
Adding Passwords to the Store
Passwords are added to the store using the pass insert command. This accepts the name of the service as an argument and interactively prompts you to enter the password.
The password will be saved to a new encrypted file inside your store. You can create a credential hierarchy by using forward slashes in your service names. This will result in a tree of subdirectories within the password store’s root.
Pass can generate new passwords for you. Use pass generate , followed by the service name and then the character length to produce. By default, a strong password consisting of alphanumeric and special characters will be created. You can prevent special characters from appearing using the —no-symbols ( -n ) flag.
pass generate cloudsavvy/example-generated 32 --no-symbols
The command shown above will generate a new 32-character password, store it as cloudsavvy/example-generated , and emit it to the terminal. You can have it copied to the clipboard instead by passing the —clip ( -c ) flag.
Retrieving Your Passwords
To list the names of all your passwords, run the pass command without any arguments.
To retrieve the value of a password, supply its name as the only argument to the command.
The password will be emitted to the terminal by default. You can copy it to the clipboard instead by passing the —clip ( -c ) flag. Clipboard data is automatically cleared after 45 seconds to maintain security.
Passwords are removed by passing a credential’s name to pass rm (e.g. pass rm cloudsavvy/example ). Similarly, you can edit passwords using pass edit . The password’s file will be opened in your default text editor.
Any interactions with passwords will display a system prompt to unlock your GPG key. You’ll need to enter your key’s passphrase if it’s protected. This acts as the master key protecting your entire password store.
Multiline Passwords
Because passwords are just plain text files, it’s possible to add multiple lines of data. This is ideal when you need to store additional security details, such as two-factor authentication recovery codes.
Use the pass edit command to open a password file in your editor. Add additional lines to the file to attach any extra metadata you require. The actual password must remain on the first line, unprefixed, to ensure it’s recognized correctly by Pass’s clipboard shorthand commands.
You can save time when creating passwords by passing the —multiline ( -m ) option to the pass insert command. This will enable you to enter multiple lines into your terminal. Press Ctrl+D when done to save the credentials into your store.
Git Integration
Pass has built-in support for Git. This enables you to version control your passwords and provides a simple mechanism to keep data synchronised across machines. Run pass git init to add Git to your password store.
You can now use Pass as normal. A Git commit will be created each time a password is added, changed, or removed. You can interact with the Git repository by using regular Git commands, prefixed by pass git :
pass git remote add origin example-server:/passwords.git pass git push -u origin master
The previous command adds a remote Git repository to your password store. You can then git push your passwords into it, giving you a backup in case you lose access to your current machine.
Interacting with Other Tools
Pass is an intentionally minimal solution. It’s much simpler than most graphical password managers, favoring a file-based approach that aligns with Unix principles. A strong ecosystem of third-party projects supports the Pass core, enabling integration with other apps and operating systems.
Data importers are available for most popular password managers, including 1Password, Keepass, and Lastpass. Compatible client apps are available for Android, iOS and Windows. dmenu users can utilize the passmenu script to rapidly search and select passwords without opening a terminal window.
The Pass website lists many notable community projects that extend the tool’s functionality and enable data portability to other platforms. You can obtain further guidance on using Pass itself from its manual page, accessed by running man pass in a terminal.
How to provide password to a command that prompts, Restart the terminal to ensure that sudo asks us for the password again. Go to /home/el again and do this: touch myfile.txt autoexpect -f my_test_expect.exp sudo chown root:root myfile.txt [enter password which authorizes the chown to root] autoexpect done, file is my_test_expect.exp.
Automated change password on linux servers
Honestly, with 8723 servers you should already have some automation and configuration management and if you don’t: this is a perfect use-case to start introducing it. Resetting local (root) passwords is fairly trivial to automate with tools Puppet, chef, Ansible, Red Hat Satellite etc.
- Replace local (management) accounts with centralised authentication in the form of LDAP, FreeIPA, radius or even AD. That results in only a single place where to enforce password policies and/or reset passwords for your admins and users.
- Configure sudo with access rights based on group membership and nobody needs to know or use the actual root password(s) anymore, negating the need both set a valid/known root password or to ever change that password.
- In the rare cases that you would need actual root access you can boot in single user mode or from a rescue image (or follow the RHEL7 root password recovery procedure )
- If you do need valid root paswords look in to privileged password management software which automates securely storing passwords and controlling access to them. Typically such a system will also periodically reset privileged account passwords and after an admin was granted access to a system such software will also reset the password again, to deny the admin future access
How to reset password in linux Code Example, # sudo -i without password sudo visudo
Kali linux how to change password
when i change password in kali linux dont’t change
$ sudo apt update $ sudo apt install kali-root-login $ sudo passwd [Enter password twice] [logout then login as root]
Show current user password linux Code Example, permission in linux; chmod command; change or set password interactively prompt in linux; how to disable a user linux; Command to Change Users in a Linux; customize ubuntu terminal in windows; reset password postgres ubuntu; linux edit crontab via script; postgre create user; linux add user; …
How to pass password to scp?
sshpass -p "password" scp -r user@example.com:/some/remote/path /some/local/path or so the password does not show in the bash history
sshpass -f "/path/to/passwordfile" scp -r user@example.com:/some/remote/path /some/local/path The above copies contents of path from the remote host to your local.
- ubuntu/debian
- apt install sshpass
- yum install sshpass
- port install sshpass
- brew install https://raw.githubusercontent.com/kadwanev/bigboybrew/master/Library/Formula/sshpass.rb
just generate a ssh key like:
ssh-keygen -t rsa -C "your_email@youremail.com"copy the content of ~/.ssh/id_rsa.pub and lastly add it to the remote machines ~/.ssh/authorized_keys
make sure remote machine have the permissions 0700 for ~./ssh folder and 0600 for ~/.ssh/authorized_keys
If you are connecting to the server from Windows, the Putty version of scp («pscp») lets you pass the password with the -pw parameter.
This is mentioned in the documentation here.
Sudoers no password prompt Code Example, Create a utility that automatically adds any new user entry created (not any service user) into sudoers file and give him NOPASSWD sudo access. how to give your user full sudo access without password in linux. debian sudo nopasswd. add user to sudoers no password\. username ALL= (ALL) …