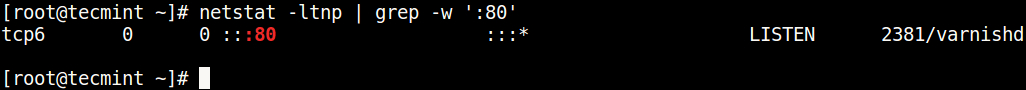- How can I see what ports are open on my machine?
- 10 Answers 10
- nmap (install)
- 3 Ways to Find Out Which Process Listening on a Particular Port
- 1. Using netstat Command
- 2. Using lsof Command
- 3. Using fuser Command
- How to find out which Port number a process is using
- 3 Answers 3
- Check Which Process Is Using a Port on Linux
- What Will We Talk About?
- How Are Ports Analogous to Physical Ports?
- A Bit About Port of a Service
- Checking the Ports on Linux
- 1. Lsof Command
- 2. SS Command
- 3. Netstat Command
- 4. Fuser Command
- Conclusion
- About the author
- Ali Imran Nagori
How can I see what ports are open on my machine?
I would like to see what ports are open on my machine, e.g. what ports my machine is listening on. E.g. port 80 if I have installed a web server, and so on. Is there any command for this?
10 Answers 10
If the netstat command is not available, install it with:
sudo apt install net-tools -l already filters for listening. grep LISTEN won’t help beyond hiding 2 lines of header information.
-t : tcp, -l : listening socket, -p : show pid and program name, -n : print 127.0.0.1:80 instead of localhost:http . Reference: linux.die.net/man/8/netstat
The expanded command is sudo netstat —tcp —listening —programs —numeric . There’s no need to use grep unless you want to eliminate column headers.
nmap (install)
Nmap («Network Mapper») is a free and open source utility for network exploration or security auditing.
Use nmap 192.168.1.33 for internal PC or nmap external IP address .
More information man nmap .
Zenmap is the official GUI frontend.
Remember that there is a difference between nmap localhost and nmap 192.168.0.3 (or what ever you machine IP is)
I think netstat is a better answer to this. netstat will list what the system is listening on directly, and without using an additional application or doing unnecessary calls over localhost or thought the network.
This is stupid. If you have access to the computer, just use netstat -ln . You’ll instantly see all the open ports.
nmap localhost didn’t find services that were bound only to localhost. For example, I run influxd with bind-address:localhost:8086 . That didn’t show up in sudo nmap localhost , but did show up in sudo netstat -tulpn .
Other good ways to find out what ports are listenting and what your firewall rules are:
To list open ports use the netstat command.
$ sudo netstat -tulpn | grep LISTEN tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 5452/dnsmasq tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1037/cupsd tcp6 0 0 ::1:631 . * LISTEN 1037/cupsd In the above example three services are bound to the loopback address.
IPv4 services bound to the loopback address «127.0.0.1» are only available on the local machine. The equivalent loopback address for IPv6 is «::1». The IPv4 address «0.0.0.0» means «any IP address», which would mean that other machines could potentially connect to any of the locally configured network interfaces on the specific port.
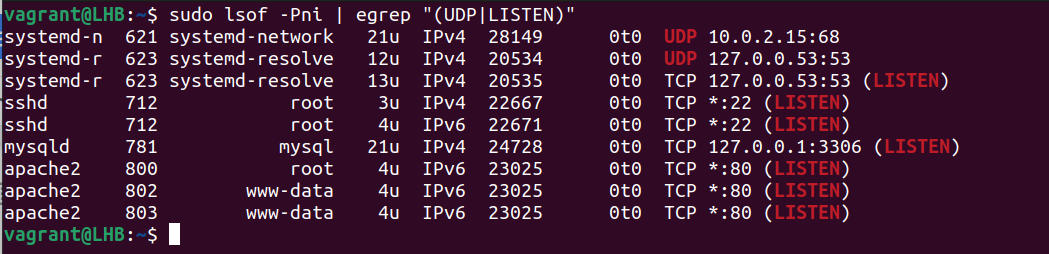
Another method is to use the lsof command:
$ sudo lsof -nP -i | grep LISTEN cupsd 1037 root 9u IPv6 11276 0t0 TCP [::1]:631 (LISTEN) cupsd 1037 root 10u IPv4 11277 0t0 TCP 127.0.0.1:631 (LISTEN) dnsmasq 5452 nobody 5u IPv4 212707 0t0 TCP 127.0.0.1:53 (LISTEN) For more details see man netstat or man lsof .
3 Ways to Find Out Which Process Listening on a Particular Port
A port is a logical entity that represents an endpoint of communication and is associated with a given process or service in an operating system. In previous articles, we explained how to find out the list of all open ports in Linux and how to check if remote ports are reachable using the Netcat command.
In this short guide, we will show different ways of finding the process/service listening on a particular port in Linux.
1. Using netstat Command
netstat (network statistics) command is used to display information concerning network connections, routing tables, interface stats, and beyond. It is available on all Unix-like operating systems including Linux and also on Windows OS.
In case you do not have it installed by default, use the following command to install it.
$ sudo apt-get install net-tools [On Debian/Ubuntu & Mint] $ sudo dnf install net-tools [On CentOS/RHEL/Fedora and Rocky Linux/AlmaLinux] $ pacman -S netstat-nat [On Arch Linux] $ emerge sys-apps/net-tools [On Gentoo] $ sudo dnf install net-tools [On Fedora] $ sudo zypper install net-tools [On openSUSE]
Once installed, you can use it with the grep command to find the process or service listening on a particular port in Linux as follows (specify the port).
In the above command, the flags.
- l – tells netstat to only show listening sockets.
- t – tells it to display tcp connections.
- n – instructs it to show numerical addresses.
- p – enables showing of the process ID and the process name.
- grep -w – shows matching of exact string (:80).
Note: The netstat command is deprecated and replaced by the modern ss command in Linux.
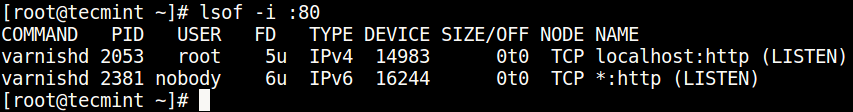
2. Using lsof Command
lsof command (List Open Files) is used to list all open files on a Linux system.
To install it on your system, type the command below.
$ sudo apt-get install lsof [On Debian, Ubuntu and Mint] $ sudo yum install lsof [On RHEL/CentOS/Fedora and Rocky Linux/AlmaLinux] $ sudo emerge -a sys-apps/lsof [On Gentoo Linux] $ sudo pacman -S lsof [On Arch Linux] $ sudo zypper install lsof [On OpenSUSE]
To find the process/service listening on a particular port, type (specify the port).
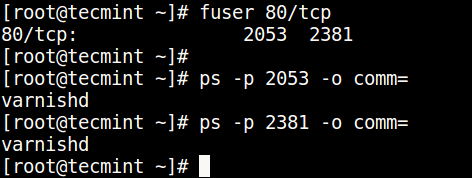
3. Using fuser Command
fuser command shows the PIDs of processes using the specified files or file systems in Linux.
You can install it as follows:
$ sudo apt-get install psmisc [On Debian, Ubuntu and Mint] $ sudo yum install psmisc [On RHEL/CentOS/Fedora and Rocky Linux/AlmaLinux] $ sudo emerge -a sys-apps/psmisc [On Gentoo Linux] $ sudo pacman -S psmisc [On Arch Linux] $ sudo zypper install psmisc [On OpenSUSE]
You can find the process/service listening on a particular port by running the command below (specify the port).
Then find the process name using PID number with the ps command like so.
$ ps -p 2053 -o comm= $ ps -p 2381 -o comm=
You can also check out these useful guides about processes in Linux.
You might also like:
That’s all! Do you know of any other ways of finding the process/service listening on a particular port in Linux, let us know via the comment form below.
How to find out which Port number a process is using
I want to be able to find out which port number a process is and filtering the results using a keyword. For example, I may want to quickly find out which port numbers are being used by «node» js apps. This did not work:
netstat tulnap | grep "node" By the way, i notice that on osx the command doesnt have a hyphen. Here are the results i got, not useful: Address Type Recv-Q Send-Q Inode Conn Refs Nextref Addr
3 Answers 3
This is how I found a solution:
» lsof -i -P | grep node node 14489 me 12u IPv4 0x. 0t0 TCP *:4000 (LISTEN) Also if i knew the port and I was looking for the process name I would:
» lsof -i :4000 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME node 14489 me 12u IPv4 0x. 0t0 TCP *:terabase (LISTEN) Active Internet connections (w/o servers)
Active Internet connections (only servers)
What you’re doing may also never work since GREP is never guaranteed to deliver either no, one, or more than 1 results.
But, in context of your specific case, any process IS actually unique, and has a unique number. So, you must do your search first to find a process number.
Doing a simple grep will still give you either none, one, or more than one process number. But you’ll need to find an additional filter, so that you end up with 1 process number.
If you have 1 process number, you can check port(s) being used by that process.
What makes you think «node» is reported in PS ? It may also not be.
Check Which Process Is Using a Port on Linux
In computer networking, a port represents a logical entry and exit point for a connection. Ports are based on software and are entirely virtual. These ports on a computer are managed by the operating system.
What Will We Talk About?
This quick tutorial demonstrates the various methods to determine which Linux process or service is currently listening on a specific port. Let’s talk about ports and their purpose.
How Are Ports Analogous to Physical Ports?
Just as physical ports help to interact with various peripheral devices connected to a computer, ports help the different services to communicate with each other. These services can be on the same computer or on different computers.
A Bit About Port of a Service
To listen for incoming connection requests, a process associates itself with a port number. Most processes are set up with a default port, and they have to use that port as per their specification. They do not automatically switch to the other port unless their configuration is explicitly modified.
A few examples of protocols and their associated default ports include the Secure Shell (SSH) protocol (port22), the Apache HTTP (port80), the MySQL database server (port3306), and so forth. You may use this information to discover which default port does a service utilizes.
The config file of these services can be edited to use some other port as well.
Checking the Ports on Linux
Let’s now see how to check what port/ports a process is using on Linux. Here, we will show you the different commands for this purpose.
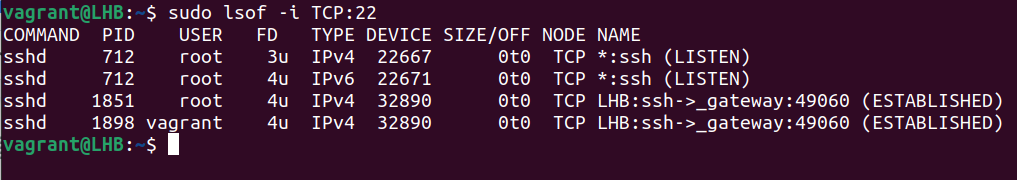
1. Lsof Command
The lsof utility is helpful to obtain a list of the ports which are used by your system. Let’s consider the following example to get an information about a process (processes) using the TCP port 22:
The lsof command gives more information like the user’s name and what process IDs are linked to each process. It works with both TCP and UDP ports.
2. SS Command
The ss command is another way to find out which processes are linked to a certain port. Although lsof is the more common abbreviation, some people may find ss to be more handy.
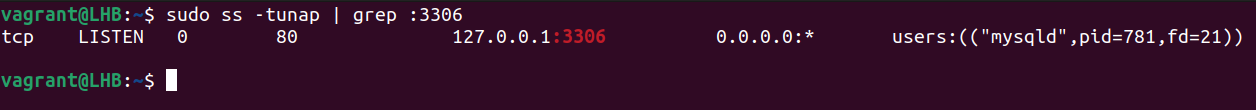
Let’s look for the processes or services that listen on port 3306:
Let’s break down this command:
1. t: It tells the ss command to display the TCP packets.
2. u: It tells the ss command to display the UDP packets.
3. n: It is used to display the port numbers instead of their translations.
4. a: It is used to display the listening as well as non-listening sockets of all types.
5. p: It is used to display the processes that utilize a socket.
The result of the previous command shows which process is utilizing which port. You may also issue the following command:
Here, sport signifies the source port.
These two approaches may help you find the IDs of the processes that are connected to different ports.
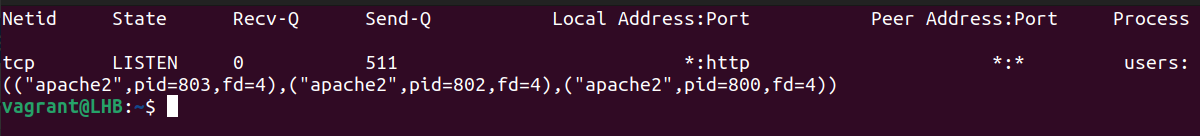
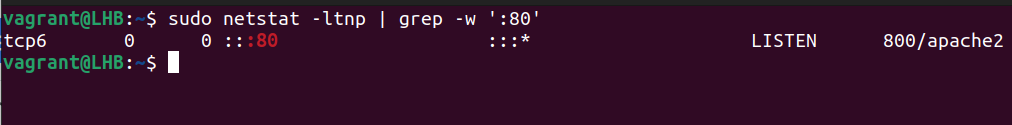
3. Netstat Command
The netstat command shows the information about your network and can be used to fix the problems or change the way that your network is set up. It can also keep a close watch on your network connections.
This command is often used to see an information about inbound and outbound connections, routing tables, port listening, and usage stats. Although it has been rendered obsolete in recent years, netstat is still a useful tool for analyzing networks.
With the grep command, netstat can determine which process or service is using a certain port (by mentioning the port):
The options used here can be classified as follows:
1. t: It only shows the TCP connection.
2. l: It is used to display the results in a list.
3. n: It displays addresses and port numbers in numerical format.
4. p: It displays the PID and program name which are associated with each socket.
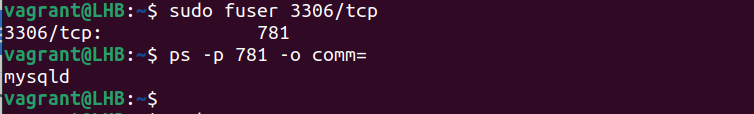
4. Fuser Command
The fuser command determines the processes that utilize the files or sockets. You can use it to list the services which run on a specific port. Let’s take the example of port 3306 and see what services are running here:
This provides us with the process numbers using this port. You can use this process number to find the corresponding process names. For example, if the process number is 15809, the command to use here is as follows:
However, certain tools are required to identify the processes that utilize a non-standard port. “LSOF” is a tool for discovering what services are available on a network and what ports they use. Consider the following example. This shows how to list the UDP and TCP listening ports:
The following is a description of the options that are used here:
1. P: It suppresses the port service name lookup.
2. n: It displays the numeric network addresses.
3. i: It lists the IP sockets.
Both the ports and the associated processes are shown in the previously-mentioned result. This way is particularly useful for processes with non-default ports.
Conclusion
In this article, we talked about four possible Linux command-line tools and provided the examples on how to use them to find out which process is listening on a certain port.
About the author
Ali Imran Nagori
Ali imran is a technical writer and Linux enthusiast who loves to write about Linux system administration and related technologies. You can connect with him on LinkedIn
.