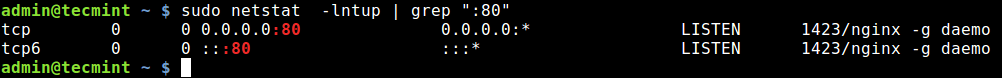Efficiently test if a port is open on Linux?
From a bash script how can I quickly find out whether a port 445 is open/listening on a server. I have tried a couple of options, but I want something quick:
1. lsof -i :445 (Takes seconds)
2. netstat -an |grep 445 |grep LISTEN (Takes seconds)
3. telnet (it doesn’t return)
4. nmap , netcat are not available on the server It will be nice to know of a way that doesn’t enumerate first and greps after that.
netstat -lnt (with -t and without -a ) will limit output to listening TCP connections only. It may speed-up a little bit. You can add -4 for IPv4 only if you don’t need IPv6.
I don’t know why lsof is slow for you, but normally it is the best of the solutions you listed. Your netstat solution is not very reliable (you can guess it whenever you use grep ; anyway it returns true if someone is listening on e.g. 4450). telnet and netcat actually attempt to create a connection, which may not always be what you want.
14 Answers 14
A surprise I found out recently is that Bash natively supports tcp connections as file descriptors. To use:
exec 6<>/dev/tcp/ip.addr.of.server/445 echo -e "GET / HTTP/1.0\n" >&6 cat I'm using 6 as the file descriptor because 0,1,2 are stdin, stdout, and stderr. 5 is sometimes used by Bash for child processes, so 3,4,6,7,8, and 9 should be safe.
As per the comment below, to test for listening on a local server in a script:
exec 6<>/dev/tcp/127.0.0.1/445 || echo "No one is listening!" exec 6>&- # close output connection exec 6
To determine if someone is listening, attempt to connect by loopback. If it fails, then the port is closed or we aren't allowed access. Afterwards, close the connection.
Modify this for your use case, such as sending an email, exiting the script on failure, or starting the required service.
@AmanJain cat waits for EOF or Ctrl-C to quit. You'll need to adjust this for your protocol. BTW are you running this to a remote server?
@AmanJain I've updated it for a local system. You do just want to check if it's listening correct? There isn't any protocol checking, such as requesting a page via http?
if a port is taken, it returns nothing, is there any way to make it say "port is taken by " or smth
This is not a reliable method since not all OS (e.g. ubuntu 16 as I discovered today) are shipped with bash compiled for building the /dev/tcp/IP/PORT tree
I use it with 127.0.0.1 as "remote" address.
this returns "0" if the port is open and "1" if the port is closed
-z Specifies that nc should just scan for listening daemons, without sending any data to them. It is an error to use this option in conjunc- tion with the -l option.
That seems to be the easiest way, thanks. The sample script link is not working anymore though, yet it's quite self-explaining anyways.
Nice! This is much faster than the other answers on a server with many ports open. Returns in
The -z flag is not available in the nmap based ncat which most recent distros ship with: Fedora, Centos, etc. (nmap-ncat-6.01-9.fc18.x86_64)
@Sean unix commands typically return '0' to indicate success and non-zero for failure. So '0' indicates that it successfully connected and non-zero that it didn't connect for some reason. Note, however, that some versions of 'nc' don't support the '-z' argument so stackoverflow.com/a/25793128/6773916 is arguably a better solution.
You can use netstat this way for much faster results:
netstat -lnt | awk '$6 == "LISTEN" && $4 ~ /\.445$/'
netstat -anp tcp | awk '$6 == "LISTEN" && $4 ~ /\.445$/'
This will output a list of processes listening on the port (445 in this example) or it will output nothing if the port is free.
Actually it is correct syntax but probably you're using Linux and I am on Mac. For Linux use this: netstat -lnt | awk '$6 == "LISTEN" && $4 ~ ".445"'
In order to check for port 80 I needed to use awk '$6 == "LISTEN" && $4 ~ "80$"' . Instead of checking for the dot before the port number with \.80 , I used 80$ . Otherwise, this also matched IP addresses containing .80 and ports starting with 80 such as 8000 .
@PatrickOscity: Good point, but to make this robust to you need to combine both approaches: awk '$6 == "LISTEN" && $4 ~ "\.80$"'
You can use netcat for this.
connects to the server and directly closes the connection again. If netcat is not able to connect, it returns a non-zero exit code. The exit code is stored in the variable $?. As an example,
will return 0 if and only if netcat could successfully connect to the port.
This answer needs more upvotes. nc works perfectly for this case. the /dev/tcp trick is clever, but seems difficult to implement a script with signal interrupts.
nc has the -z flag for this purpose, which doesn't require taking input from /dev/null . There's already an answer using the -z flag above.
@AbeVoelker Not all versions of nc support the -z flag. I am on CentOS 7 and found Tony's solution to be what I needed.
Based on Spencer Rathbun's answer, using bash:
Good, it will suppress "Connection Refused" message. Auto-exits if the service accept the connection without wait forever.
Best solution for services that send no data after a new connection. About 20 times faster than calling netcat. Can be shortened to : &>/dev/null
I'd add a timeout to get a closed result faster: timeout 5s bash -c ': &>/dev/null ' && echo open || echo closed
@user1338062 This happens on an Ubuntu Bionic on Azure against external IP (not localhost or 127.0.0.1 ).
they're listed in /proc/net/tcp.
it's the second column, after the ":", in hex:
> cat /proc/net/tcp sl local_address rem_address st tx_queue rx_queue tr tm->when retrnsmt uid timeout inode 0: 00000000:0016 00000000:0000 0A 00000000:00000000 00:00000000 00000000 0 0 10863 1 ffff88020c785400 99 0 0 10 -1 1: 0100007F:0277 00000000:0000 0A 00000000:00000000 00:00000000 00000000 0 0 7983 1 ffff88020eb7b3c0 99 0 0 10 -1 2: 0500010A:948F 0900010A:2328 01 00000000:00000000 02:00000576 00000000 1000 0 10562454 2 ffff88010040f7c0 22 3 30 5 3 3: 0500010A:E077 5F2F7D4A:0050 01 00000000:00000000 02:00000176 00000000 1000 0 10701021 2 ffff880100474080 41 3 22 10 -1 4: 0500010A:8773 16EC97D1:0050 01 00000000:00000000 02:00000BDC 00000000 1000 0 10700849 2 ffff880104335440 57 3 18 10 -1 5: 0500010A:8772 16EC97D1:0050 01 00000000:00000000 02:00000BF5 00000000 1000 0 10698952 2 ffff88010040e440 46 3 0 10 -1 6: 0500010A:DD2C 0900010A:0016 01 00000000:00000000 02:0006E764 00000000 1000 0 9562907 2 ffff880104334740 22 3 30 5 4 7: 0500010A:AAA4 6A717D4A:0050 08 00000000:00000001 02:00000929 00000000 1000 0 10696677 2 ffff880106cc77c0 45 3 0 10 -1
so i guess one of those :50 in the third column must be stackoverflow :o)
look in man 5 proc for more details. and picking that apart with sed etc is left as an exercise for the gentle reader.
4 Ways to Find Out What Ports Are Listening in Linux
The state of a port is either open, filtered, closed, or unfiltered. A port is said to be open if an application on the target machine is listening for connections/packets on that port.
In this article, we will explain four ways to check open ports and also will show you how to find which application is listening on what port in Linux.
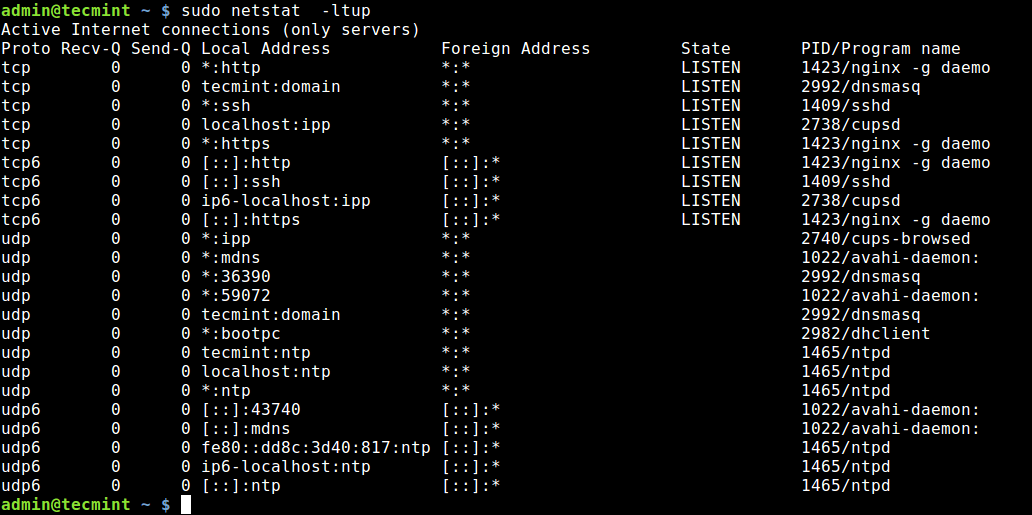
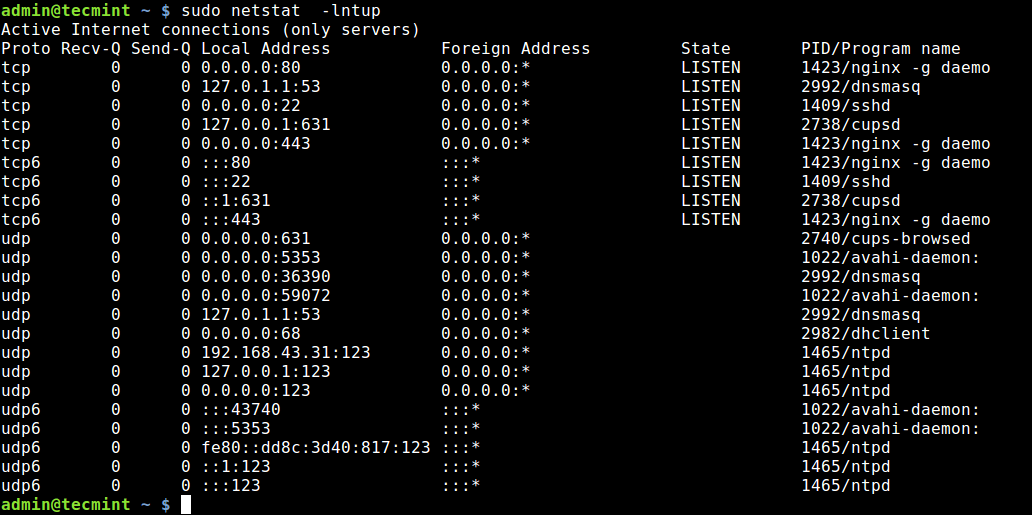
1. Using Netstat Command
Netstat is a widely used tool for querying information about the Linux networking subsystem. You can use it to print all open ports like this:
The flag -l tells netstat to print all listening sockets, -t shows all TCP connections, -u displays all UDP connections and -p enables printing of application/program name listening on the port.

To print numeric values rather than service names, add the -n flag.

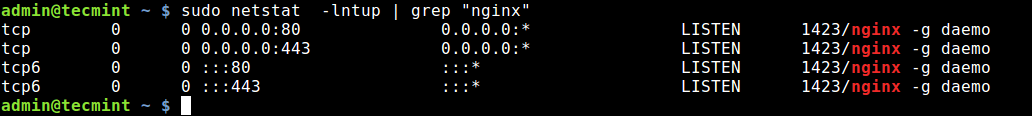
You can also use grep command to find out which application is listening on a particular port, for example.
$ sudo netstat -lntup | grep "nginx"

Alternatively, you can specify the port and find the application bound to, as shown.
$ sudo netstat -lntup | grep ":80"

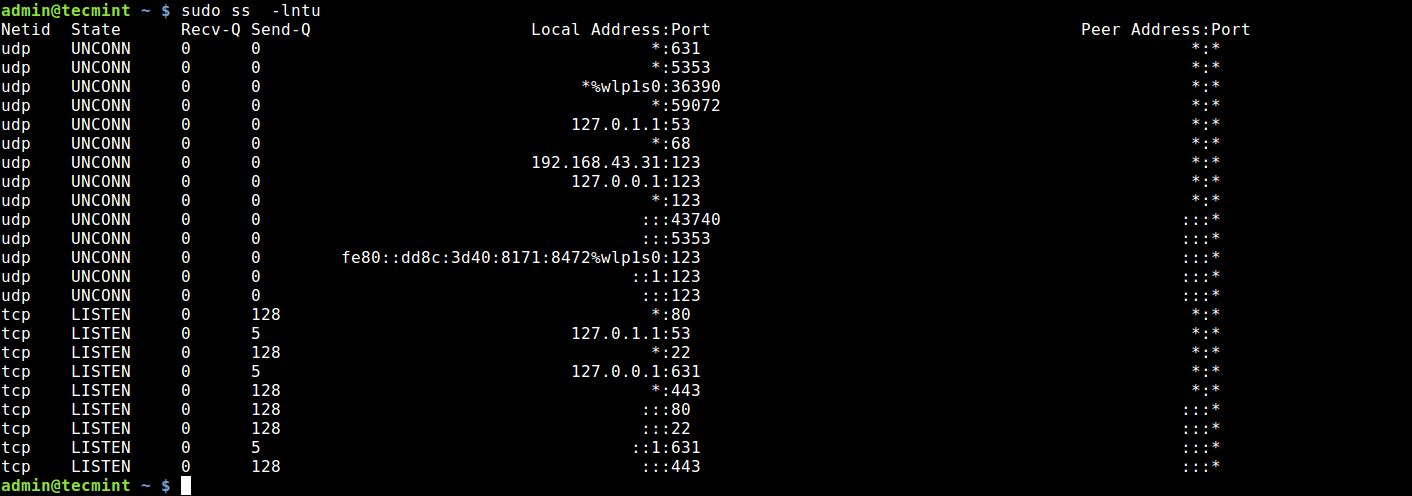
2. Using ss Command
ss command is another useful tool for displaying information about sockets. It’s output looks similar to that of netstat. The following command will show all listening ports for TCP and UDP connections in numeric value.

3. Using Nmap Command
Nmap is a powerful and popular network exploration tool and port scanner. To install nmap on your system, use your default package manager as shown.
$ sudo apt install nmap [On Debian/Ubuntu] $ sudo yum install nmap [On CentOS/RHEL] $ sudo dnf install nmap [On Fedora 22+]
To scan all open/listening ports in your Linux system, run the following command (which should take a long time to complete).
$ sudo nmap -n -PN -sT -sU -p- localhost
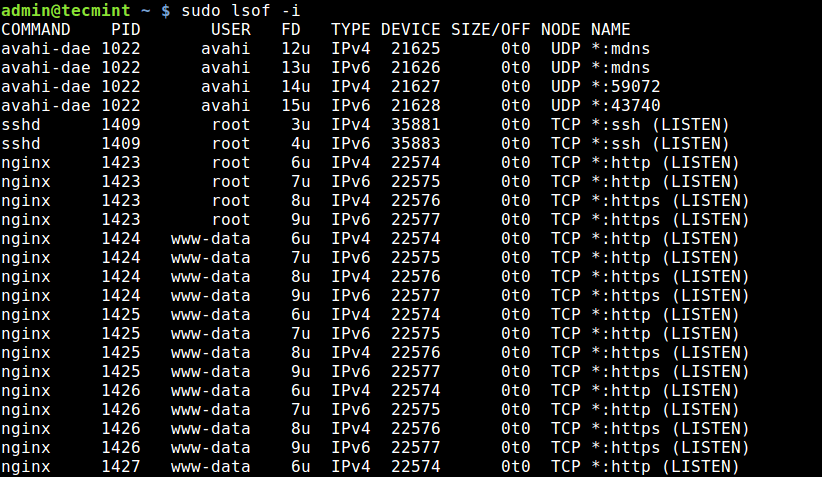
4. Using lsof Command
The final tool we will cover for querying open ports is lsof command, which is used to list open files in Linux. Since everything is a file in Unix/Linux, an open file may be a stream or a network file.
To list all Internet and network files, use the -i option. Note that this command shows a mix of service names and numeric ports.

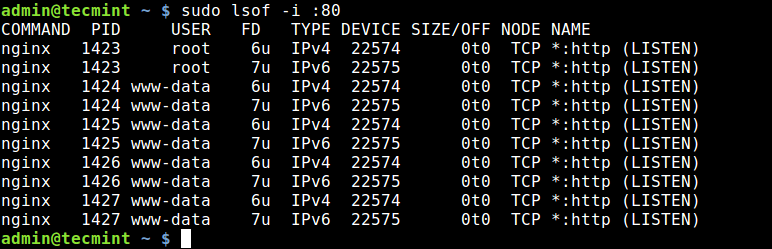
To find which application is listening on a particular port, run lsof in this form.

That’s all! In this article, we have explained four ways to check open ports in Linux. We also showed how to check which processes are bound upon particular ports. You can share your thoughts or ask any questions via the feedback form below.
How can I see what ports are open on my machine?
I would like to see what ports are open on my machine, e.g. what ports my machine is listening on. E.g. port 80 if I have installed a web server, and so on. Is there any command for this?
10 Answers 10
If the netstat command is not available, install it with:
sudo apt install net-tools
-l already filters for listening. grep LISTEN won't help beyond hiding 2 lines of header information.
-t : tcp, -l : listening socket, -p : show pid and program name, -n : print 127.0.0.1:80 instead of localhost:http . Reference: linux.die.net/man/8/netstat
The expanded command is sudo netstat --tcp --listening --programs --numeric . There’s no need to use grep unless you want to eliminate column headers.
nmap (install)
Nmap ("Network Mapper") is a free and open source utility for network exploration or security auditing.
Use nmap 192.168.1.33 for internal PC or nmap external IP address .
More information man nmap .
Zenmap is the official GUI frontend.
Remember that there is a difference between nmap localhost and nmap 192.168.0.3 (or what ever you machine IP is)
I think netstat is a better answer to this. netstat will list what the system is listening on directly, and without using an additional application or doing unnecessary calls over localhost or thought the network.
This is stupid. If you have access to the computer, just use netstat -ln . You'll instantly see all the open ports.
nmap localhost didn't find services that were bound only to localhost. For example, I run influxd with bind-address:localhost:8086 . That didn't show up in sudo nmap localhost , but did show up in sudo netstat -tulpn .
Other good ways to find out what ports are listenting and what your firewall rules are:
To list open ports use the netstat command.
$ sudo netstat -tulpn | grep LISTEN tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 5452/dnsmasq tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1037/cupsd tcp6 0 0 ::1:631 . * LISTEN 1037/cupsd
In the above example three services are bound to the loopback address.
IPv4 services bound to the loopback address "127.0.0.1" are only available on the local machine. The equivalent loopback address for IPv6 is "::1". The IPv4 address "0.0.0.0" means "any IP address", which would mean that other machines could potentially connect to any of the locally configured network interfaces on the specific port.
Another method is to use the lsof command:
$ sudo lsof -nP -i | grep LISTEN cupsd 1037 root 9u IPv6 11276 0t0 TCP [::1]:631 (LISTEN) cupsd 1037 root 10u IPv4 11277 0t0 TCP 127.0.0.1:631 (LISTEN) dnsmasq 5452 nobody 5u IPv4 212707 0t0 TCP 127.0.0.1:53 (LISTEN)
For more details see man netstat or man lsof .