Introduction to DNS on Linux
Estamos traduciendo nuestros guías y tutoriales al Español. Es posible que usted esté viendo una traducción generada automáticamente. Estamos trabajando con traductores profesionales para verificar las traducciones de nuestro sitio web. Este proyecto es un trabajo en curso.
The Domain Name System (DNS) is a worldwide directory that maps names to addresses and vice versa. It also provides many other types of information about computing resources. Although the DNS operates largely hidden from view, the global Internet would not work without it.
This guide explains what DNS is, how it works, and how to build your own authoritative name server.
This is the first in a series of four DNS guides. Future guides cover primary and secondary name server setup, securing DNS with DNSSEC, and other security measures to address user privacy concerns.
What Is DNS?
DNS is a global directory of computing resources. It can locate servers, PCs, phones, IoT devices, routers, switches, and essentially anything with an IP address. DNS also holds information linking computers to security keys, services such as instant messaging, GPS coordinates, and much more.
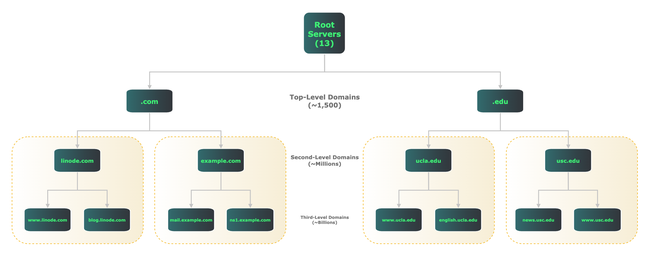
DNS design is hierarchical and distributed. The diagram below illustrates both points. It shows how DNS divides all resources into domains, and delegates different levels of name servers to provide information within each domain.
At the top of the DNS tree are the root servers, usually referred to by a single dot («.»). The root servers are actually comprised of 13 different sets of servers, each operated by a different organization. They act as a starting point for all other parts of the hierarchy.
Below the root servers are top-level domains (TLDs). Common TLDs include .com , .edu , and .org , but there are currently around 1,500 TLDs.
Further down in the hierarchy are second- and third-level domains, and so on, referring to their distance from the root. The domain example.com is an example of a second-level domain, while engineering.example.com is a third-level domain.
Regardless of level, all DNS name servers provide information about items within their domains. For example, linode.com name servers provide information about hostnames, addresses, mail servers, and name servers within that domain.
How Does DNS Work?
DNS clients use recursion, the concept of repeating a process multiple times using information gleaned from the previous step, to learn how to locate resources.
For example, when visiting www.linode.com, your system first conducts a series of recursive DNS exchanges to learn the server’s IP address before it can connect with the Linode web server.
First, your client checks to see if it has an IP address for the Linode webserver in its local cache. If not, it asks your local DNS server.
If the local DNS server doesn’t have an IP address in its cache, it then asks one of the root servers how to reach www.linode.com. The root server replies, essentially saying “I don’t know, but I see you’re asking about something in the .com domain. Here are some IP addresses for .com name servers”.
Your local DNS server then repeats its query, this time to a .com name server. The .com name server replies, “I don’t know, but I can tell you the IP addresses of name servers for linode.com”.
The local DNS server then asks, for the third time, what IP addresses correspond to the hostname www.linode.com. This time, the linode.com name servers are authorized to provide a direct answer to your question.
A Linode name server responds with IP addresses for the Linode web server. Your local DNS server passes along that information to your client, and caches it for future use.
Finally, your system has an IP address for the Linode web server. It can now set up a TCP connection and make an HTTP request.
Before you could retrieve the web page, your client and the local DNS server had multiple conversations with three outside sets of DNS servers, plus your local DNS server, just to get an IP address.
Believe it or not, that’s a relatively simple example. A popular commercial site, such as a news site, has advertising and other embedded third-party content. This could require having these sets of DNS conversations several dozen times, or more, just to load a single page.
While all this occurs in milliseconds, it underscores how critical DNS is to a functional Internet. Everything begins with a series of DNS queries.
Types of DNS Servers
There are several types of DNS servers: authoritative (both primary and secondary), forwarding, and recursive. All three types may reside on a single server, or may be assigned to separate dedicated servers for each type. Regardless of location, these servers work cooperatively to serve DNS information.
An authoritative server provides definitive responses for a given zone, which is a set of computing resources under common administrative control. While non-authoritative DNS servers may also store and forward answers about a zone’s contents, only an authoritative server can provide definitive answers.
A zone may be a domain such as linode.com, but there isn’t always a 1:1 relationship between domains and zones. Authoritative servers may delegate authority to subdomains. For example, the .com authoritative servers delegate responsibility for linode.com to Linode’s name servers. In this case, linode.com is part of the .com domain, but .com and linode.com represent different zones.
Each zone should have at least two authoritative name servers, for both redundancy and load-balancing of user queries. This guide covers setup of a primary name server.
Both primary and secondary name servers are authoritative, and appear nearly identical to the outside world. However, secondary name servers automatically receive all zone updates from the primary name server. After initial setup, zone configuration changes only need to be made once, on the primary name server. It then automatically pushes out all updates to any secondary name servers.
A forwarding server is one that makes external DNS requests on behalf of clients or other DNS servers. Your local DNS server, while not authoritative for most zones, is most likely either a forwarding server itself, or configured to send requests to one. When you ask for a DNS resource outside your zone, a forwarding server finds that resource.
A recursive resolver makes DNS queries, either for itself or on behalf of other clients, and optionally caches the replies. As with any type of caching, it’s best to store information as close as possible to your client. While your local client may perform recursion, your local DNS server almost certainly does.
By far the most common DNS server software is Bind 9, the open source package maintained by the Internet Systems Consortium. Bind can function as any type of DNS server. It also supports many DNS extensions that go well beyond it’s original design goals.
Because of Bind’s age and size, some users prefer smaller, more modern DNS implementations. Two of the more popular are NSD, an authoritative-only name server, and Unbound, a resolver that also does forwarding and caching. This guide covers authoritative name server setup using NSD.
Resource Records
Before diving into setup details, familiarize yourself with the different types of information DNS can provide within a given zone. Think of DNS as a distributed database, and zones as tables within the database. Resource records (RR) are entries within each table.
Each record describes a different type of information. For example, “A” records associate one hostname with one IPv4 address, while “AAAA” records do the same for IPv6.
There are dozens of RR types; this Linode guide covers some of the most common and important ones. Most authoritative name servers need at least the following RR types:
- A: Maps a hostname to an IPv4 address.
- AAAA: Maps a hostname to an IPv6 address (pronounced “quad-A”).
- MX: Identifies a mail server for a given zone, and gives its priority.
- NS: Identifies a name server for a given zone.
- SOA: (Start of Authority) lists primary name server, administrative email contact, serial number, and default timers for a given zone.
The above list is enough for a bare-bones setup, but other common RR types include:
- CNAME: Maps a hostname alias to a hostname defined in an A or AAAA record.
- PTR: Maps an IP address to a hostname (sometimes referred to as “reverse DNS” or “rDNS”).
- TXT: Provides information in text form and often aids in email security through use of SPF, DKIM, and DMARC records.
Before You Begin
- If you have not already done so, create a Linode account and Compute Instance. See our Getting Started with Linode and Creating a Compute Instance guides. This guide is for Ubuntu 22.04 LTS instances.
- Follow our Setting Up and Securing a Compute Instance guide to update your system. Set the timezone, configure your hostname, and create a limited user account. To follow along with this guide, give your server the hostname ns1 and configure the hosts file as follows:
Как посмотреть DNS в Linux
Служба DNS или Domain Name System позволяет превращать легко читаемый адрес сайта в ip адрес сервера на котором расположен этот сайт. Для этого используются DNS серверы, которые содержат таблицы соответствия ip адресов их доменным именам. По умолчанию система получает адрес DNS сервера автоматически по DHCP при подключении к сети.
В этой статье мы разберемся как посмотреть какие DNS серверы используются в Linux.
Как посмотреть DNS в Linux
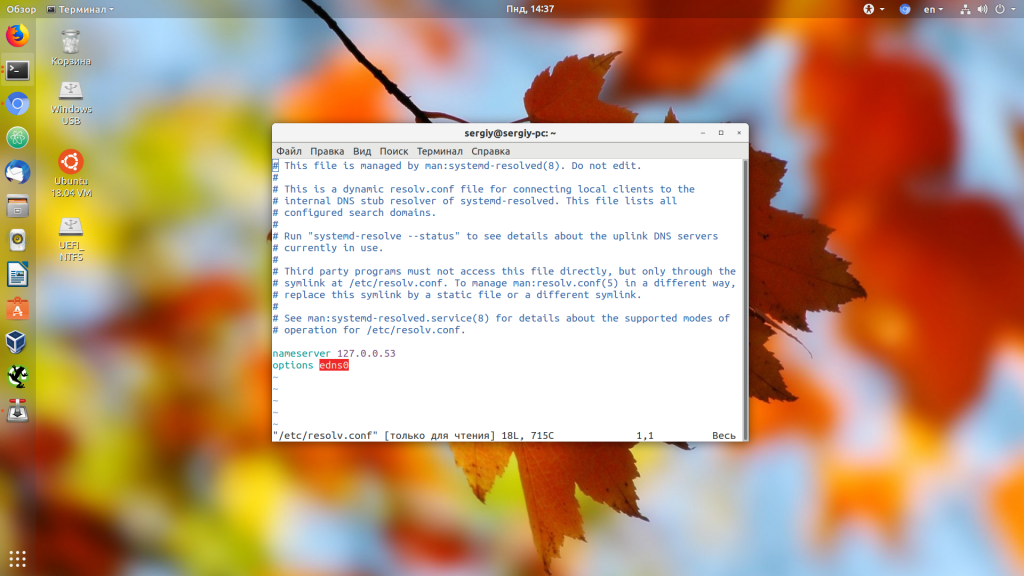
Если вы уже имели опыт настройки сети в Linux, то знаете, что DNS серверы, используемые для резолвинга доменных имен указаны в файле /etc/resolv.conf:
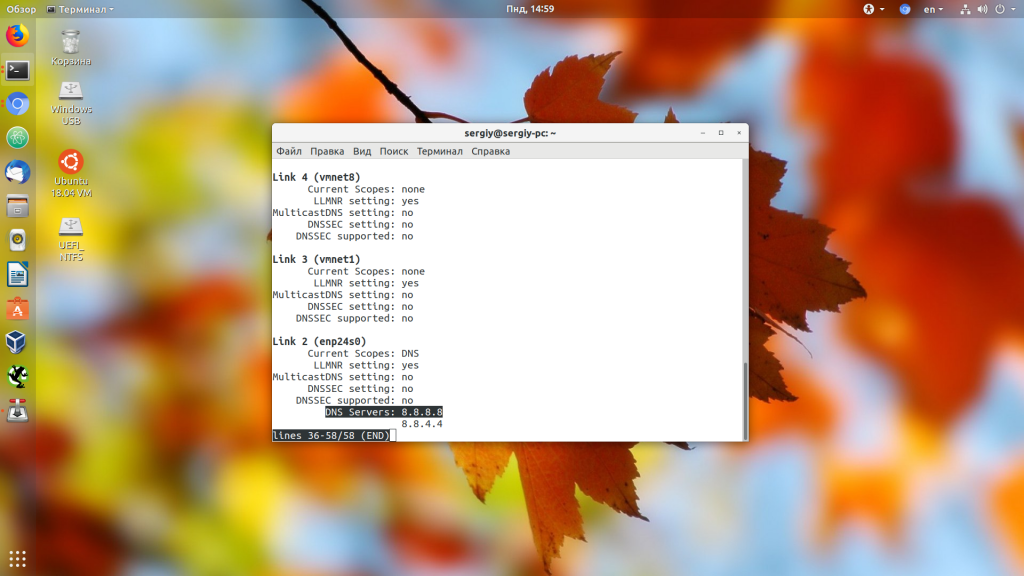
Но в современных дистрибутивах Linux с системой инициализации systemd обычно запущен локальный DNS сервер, адрес которого и прописан в этом файле, а какие сервера используются на самом деле непонятно. В таком случае можно воспользоваться утилитой systemd-resolve:
В самом низу вывода утилиты можно посмотреть DNS в Linux, которые сейчас используются. Информация выводится по каждому сетевому интерфейсу отдельно.
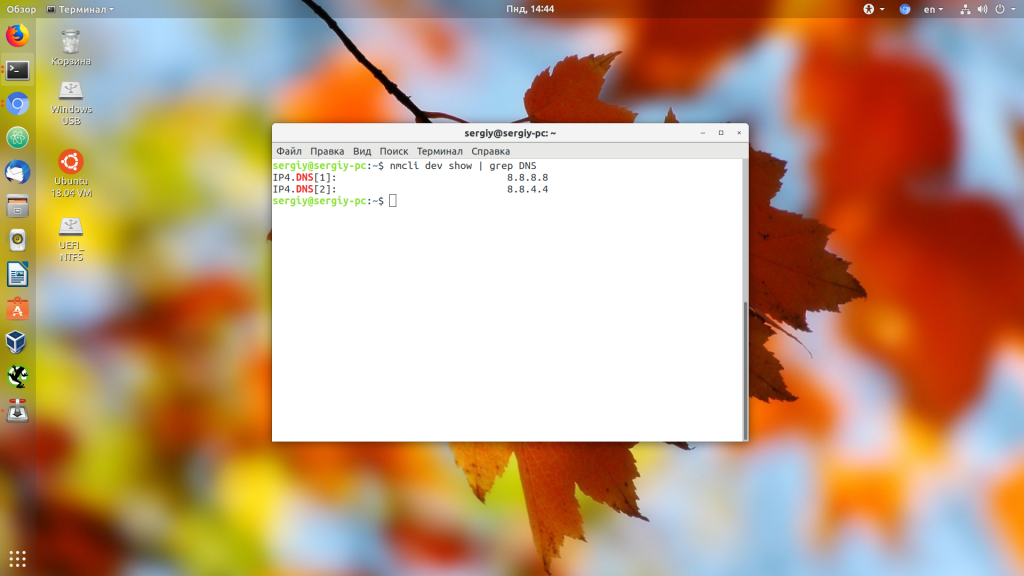
Также для решения подобной задачи можно использовать утилиту nmcli:
Как видите, все очень просто. А чтобы изменить DNS сервер тоже трогать /etc/resolv.conf не желательно, так как он будет автоматически обновляться после перезагрузки. Если вы используете NetworkManager, то можно настроить DNS для сетевого подключения в интерфейсе программы. Или же можно отредактировать файл /etc/systemd/resolved.conf и добавить нужные адреса в секцию Resolve:
sudo vi /etc/systemd/resolved.conf
Как видите, все очень просто. Надеюсь, эта информация была вам полезной.
Обнаружили ошибку в тексте? Сообщите мне об этом. Выделите текст с ошибкой и нажмите Ctrl+Enter.