- How to Kick Out SSH Users from the Linux System
- Tutorial Details
- Finding All the Logged-In Users in the Linux System
- Kick Out the SSH Users from the Linux System
- Forcefully Throw the User from the Linux System
- Send a Message to the Users Before Terminating the Session
- How to Terminate All the User Active Sessions from the Linux System
- How do I force-close all active ssh sessions that were started by a specific sshd daemon?
- 3 Answers 3
- You must log in to answer this question.
- Related
- Hot Network Questions
- Subscribe to RSS
- exit out of all SSH connections in one command and close PuTTY
- 7 Answers 7
- How do I exit an SSH connection?
- 7 Answers 7
How to Kick Out SSH Users from the Linux System
As a sysadmin, when you are working on a remote system or server, multiple users might be accessing the same system via SSH simultaneously.
Active users can gently disconnect from the server by issuing the “ exit ” command in the terminal once they are done with their work.
However, some careless users fail to logout and leave the session running in the background, which will logout the user only if you configured SSH to automatically kick out the user after a certain amount of idle time or the user logs out manually.
In this quick tutorial, you will learn how to kick out SSH-connected users from the target system from your end as a sysadmin.
Tutorial Details
| Description | Logout the SSH Users from the System |
| Difficulty Level | Low |
| Root or Sudo Privileges | Yes |
| Host System and Architecture | Ubuntu 22.10 (x64) |
| OS Compatibility | Ubuntu, Manjaro, Fedora, etc. |
| Prerequisites | who, kill, killall |
| Internet Required | No |
| Discussed Tools in this Article |
Finding All the Logged-In Users in the Linux System
The first thing you need to do is list all the logged-in users connected to the target machine via SSH; that can be achieved using the multiple command-line tool.
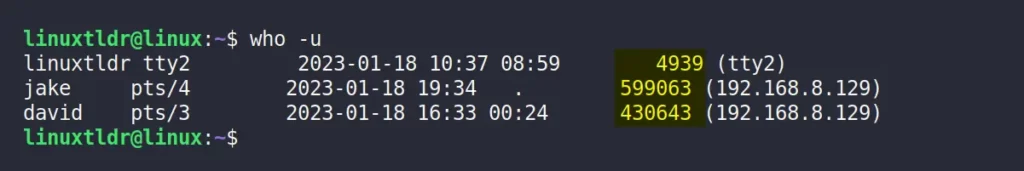
For now, I will use the who command along with the “ -u ” flag to list all the logged-in users along with their process ID.
From the above picture, it’s clear that the three users with account names linuxtldr (myself), jake, and david are connected to the target machine.
Next to each user’s account name, you can find their account information, like their TTY, date and time, process ID, and IP address.
Currently, we are only interested in users process ID to kick them out of the system (the primary objective of this article), which you will learn in the next section.
Kick Out the SSH Users from the Linux System
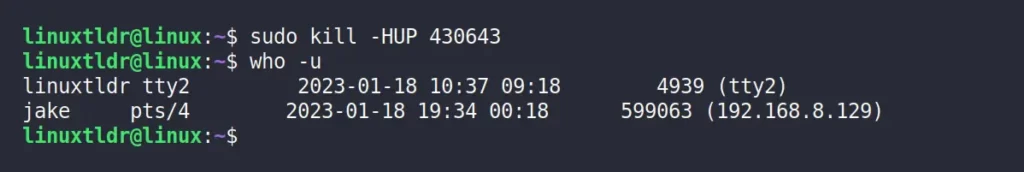
As you now have a list of all the logged-in users connected to the target machine along with their process ID, you can easily kick them out of the system using the kill command.
For example, I want to kick the “david” user from the system, so I will use his “430643” PID as an argument to the kill command with the “ -HUP ” option.
Note : The following command should be executed with a root or sudo account to avoid the “Operation not permitted” message.
$ sudo kill -HUP 430643The above command will send a “SIGHUP” signal to gently disconnect all the processes in the session from the controlling terminal.
Forcefully Throw the User from the Linux System
Sometimes the “SIGHUP” signal (responsible for gently disconnecting users) might not do the trick, especially when the SSH session becomes unresponsive.
In that case, you can aggressively kick out the users from the system by sending the “SIGKILL” signal.
$ sudo kill -SIGKILL 430643 #OR $ sudo kill -9 430643Send a Message to the Users Before Terminating the Session
Sometimes you want to intentionally terminate the user session for various reasons, and in that situation, it is quite possible that the user is working on something and terminating the session will lead to data loss.
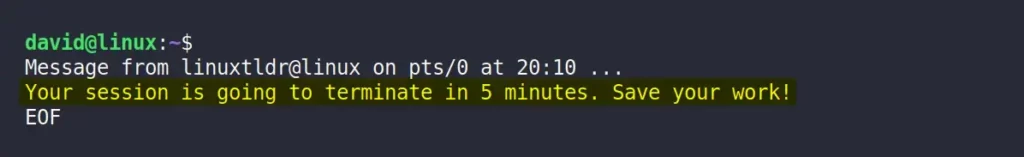
However, you can send them a relevant message before terminating the session using the write command.
$ echo "Your session is going to terminate in 5 minutes. Save your work!" | write david pts/3The following is an example of a target user’s terminal screen.
How to Terminate All the User Active Sessions from the Linux System
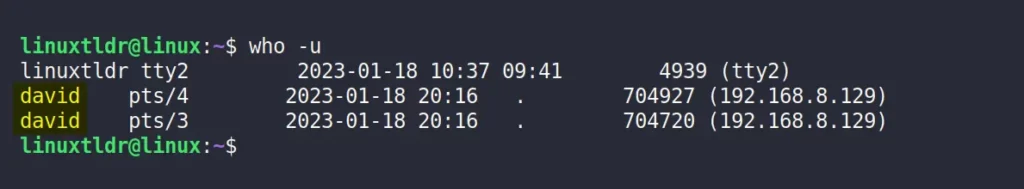
It’s entirely possible that the target machine is being operated by the same user from two different SSH sessions, as shown.
As you can see from the above picture, the “david” user is logged into the target machine with two different SSH sessions, giving him two different process IDs.
Now, one way to kick him out of the target machine is by specifying each session PID as an argument to the kill command (ineffective).
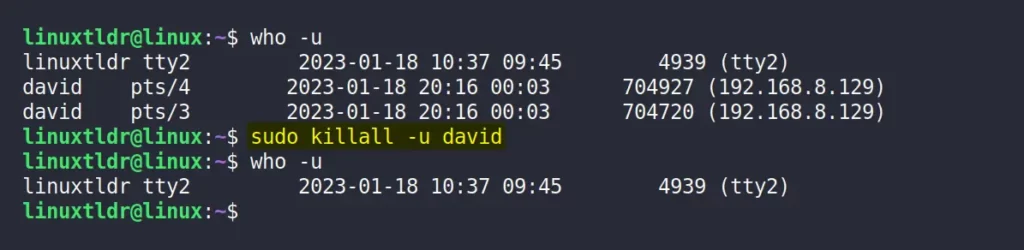
Or, you can specify the user account (or login) name as an argument to the killall command with the “ -u ” option to terminate all the active sessions of the referenced user.
$ sudo killall -u davidAnd here comes the end of this article.
I hope this article will help you achieve this task; however, if you have any questions or queries related to this topic, then feel free to ask them in the comment section.
How do I force-close all active ssh sessions that were started by a specific sshd daemon?
I have a system that runs multiple sshd daemons. Each daemon listens to a separate port. How can I terminate all sessions started by a specific daemon without affecting other ssh sessions?
3 Answers 3
If you know the ssh port, you can simply kill all current tcp sessions that were initiated through it:
This kills all active ssh sessions that were started through port 22 while leaving other ssh sessions intact. Don’t forget to stop the sshd daemon before you kill off its sessions.
Run this to find out which PIDs you’re interested in.
netstat -n -eep | grep port_number Run any of these commands to see the interesting processes children and terminate them:
if you have the pid of the sshd,
should send SIGTERM to all children of the sshd
maybe add —signal kill if you want to force-kill them
You must log in to answer this question.
Related
Hot Network Questions
Subscribe to RSS
To subscribe to this RSS feed, copy and paste this URL into your RSS reader.
Site design / logo © 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA . rev 2023.7.13.43531
Linux is a registered trademark of Linus Torvalds. UNIX is a registered trademark of The Open Group.
This site is not affiliated with Linus Torvalds or The Open Group in any way.
By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy.
exit out of all SSH connections in one command and close PuTTY
Is there a way to back out of all SSH connections and close PuTTY in «one shot»? I work in Windows 7 and use PuTTY to SSH to various Linux hosts. An example of the way I find myself working:
SSH to host1 with PuTTY. banjer@host1:~> #. doin some work. ooh! need to go check something on host8. banjer@host1:~> ssh host8 banjer@host8:~> #. doin some work. OK time for lunch. lets close putty. banjer@host8:~> exit banjer@host1:~> exit Putty closes. Per above, any way to get from host8 to closing PuTTY in one shot? Sometimes I find myself up to 5 or 10 hosts deep. I realize I can click the X to close the PuTTY window, but I like to make sure my SSH connections get closed properly by using the exit command. I also realize I’m asking for tips on how to increase laziness. I’ll just write it off as «how can I be more efficient».
@UlrichDangel I have never used that before, but also a quick way to back out of connections quickly.
Are you really nesting ssh sessions 5 to 10 levels deep? Do you realize that’s creating a convoluted tunnel that bounces all packets in your ssh session through all of those hosts? Could you make the problem go away by simply not nesting ssh sessions?
@jw013 No, I did not realize that, but makes sense. Honestly, 5-10 levels was an exaggeration, but I was trying to illustrate my question of «how to cleanly exit out of Putty in one fell swoop.»
7 Answers 7
Try using the ssh connection termination escape sequence.
In the ssh session, enter ~. (tilde dot). You won’t see the characters when you type them, but the session will terminate immediately.
$ ~. $ Connection to me.myhost.com closed. The supported escapes (assuming the default ‘~’) are: ~. Disconnect. ~^Z Background ssh. ~# List forwarded connections. ~& Background ssh at logout when waiting for forwarded connection / X11 sessions to terminate. ~? Display a list of escape characters. ~B Send a BREAK to the remote system (only useful for SSH protocol version 2 and if the peer supports it). ~C Open command line. Currently this allows the addition of port forwardings using the -L, -R and -D options (see above). It also allows the cancellation of existing remote port-forwardings using -KR[bind_address:]port. !command allows the user to execute a local command if the PermitLocalCommand option is enabled in ssh_config(5). Basic help is available, using the -h option. ~R Request rekeying of the connection (only useful for SSH protocol version 2 and if the peer supports it). How do I exit an SSH connection?
After the connection is established and I write the message and send it I can’t exit the text mode. I’m only allowed to enter more text and that’s it. Is there a command or a key combination that allows me to return to command mode?
7 Answers 7
How do I exit an SSH connection?
- closing the shell session will usually exit, for example:
- with the shell builtin command, exit , followed by Enter , or
- Ctrl — d , (end-of-file)
The first option should be intuitive, but how do we know the latter option?
We could learn this information from a careful reading of the man page.
gives us the SSH documentation, which has the following section on escape characters:
ESCAPE CHARACTERS When a pseudo-terminal has been requested, ssh supports a number of functions through the use of an escape character. A single tilde character can be sent as ~~ or by following the tilde by a character other than those described below. The escape character must always follow a newline to be interpreted as special. The escape character can be changed in configuration files using the EscapeChar configuration directive or on the command line by the -e option. The supported escapes (assuming the default ‘~’) are: ~. Disconnect. ~^Z Background ssh. ~# List forwarded connections. ~& Background ssh at logout when waiting for forwarded connection / X11 sessions to terminate. ~? Display a list of escape characters. ~B Send a BREAK to the remote system (only useful if the peer sup‐ ports it). ~C Open command line. Currently this allows the addition of port forwardings using the -L, -R and -D options (see above). It also allows the cancellation of existing port-forwardings with -KL[bind_address:]port for local, -KR[bind_address:]port for remote and -KD[bind_address:]port for dynamic port-forwardings. !command allows the user to execute a local command if the PermitLocalCommand option is enabled in ssh_config(5). Basic help is available, using the -h option. ~R Request rekeying of the connection (only useful if the peer supports it). ~V Decrease the verbosity (LogLevel) when errors are being written to stderr. ~v Increase the verbosity (LogLevel) when errors are being written to stderr.There is nothing special about exit to ssh, it’s just a way to exit the shell, which results in closing the ssh session:
$ type exit exit is a shell builtin $ help exit exit: exit [n] Exit the shell. Exits the shell with a status of N. If N is omitted, the exit status is that of the last command executed.Citing and quoting reference sources is to provide further evidence for what would otherwise be a perhaps demonstrable assertion of fact, as well as inform the user where more relevant information may be stored.
You want to know that you’re doing semantically the correct thing, as well as knowing that it works.
You don’t want to learn to invoke as a feature something that is documented as a bug and then later «fixed.» Doing the semantically correct thing will continue to be supported.