- How do I get the number of (currently) established TCP connections for a specific port?
- 4 Answers 4
- How to Find All Clients Connected to HTTP or HTTPS Ports
- View your Linux server’s network connections with netstat
- Install netstat
- Use netstat
- Next steps
- Learn netstat
- 7 steps to securing your Linux server
- 6 open source tools and tips to securing a Linux server for beginners
- 9 things to do in your first 10 minutes on a Linux server
- Check the Number of active connections on port 80?
- 5 Answers 5
How do I get the number of (currently) established TCP connections for a specific port?
How do I get the number of (currently) established TCP connections for a specific port? I have managed to get counters for traffic working by doing i.e for outgoing RTMP.
iptables -N $CHAIN iptables -I OUTPUT -j $CHAIN iptables -A $CHAIN -p tcp --sport 1935 iptables-save But now i need the number of current (not a counter) connections, for each protocol I can get the total number with: netstat -ant | grep ESTABLISHED | wc -l Can anyone help? Im not an iptables guru.
4 Answers 4
You say you’re not a guru, but which of us is? You’ve done most of the heavy lifting; I’m sure the rest will occur to you in a minute or two.
Until then, try netstat -an|grep ESTABLISHED | grep -w 1935 .
lsof -ni:1935 -sTCP:ESTABLISHED | wc -l has also been suggested to me?, is there any benefit between lsof and netstat?
They both hook into the underlying kernel structures. The binaries are about the same size, so will have comparable memory footprints. Offhand, I can think of no major difference.
I am being told they are supposed to be slow (The box will have like 20k connections), and to use iptables, but it looks unsuitable to me?
Iptables seems unsuitable to me, too. Both iptables and netstat/lsof are simply userspace tools that tap into kernel structures, so I’m not quite sure why one would be much slower than the others unless the userspace portions were wildly different in size (they’re not). How often do you intend to poll this statistic?
Then unless you’re running this on the slowest system ever built this year, then I doubt the overhead involved is significant in the slightest. Try it: run time . on the command, and see how many seconds of CPU it uses. Then work out what that is as a fraction of the product of 300s (five minutes) and the number of CPUs in the box. That’ll give you some idea what fraction of your system you’re about to burn in monitoring this. Nothing helps deal with FUD like real data.
How to Find All Clients Connected to HTTP or HTTPS Ports
In this short quick article, you will learn how to find all clients (using their IP addressees) connected to an Apache or Nginx web server on HTTP or HTTPS ports on a Linux server.
In Linux, every service running on the server listening to the socket for a client to make a connection request. Upon a successful connection from a client, a socket (a combination of an IP address and a port (a number which identifies an application/service the client is connected to)) is created.
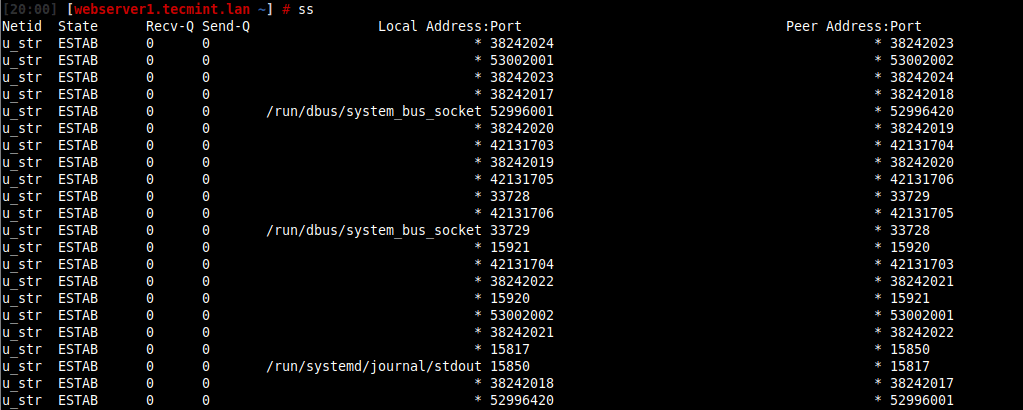
To get the detailed information of these sockets, we will use a ss command-line tool, which is used to display network socket related information on a Linux machine. You can also use the older netstat command, which displays active socket connections.
For example, you can use these tools to get the socket statistics information of all clients connected to a specific port or service.
To get the list of all clients connected to HTTP (Port 80) or HTTPS (Port 443), you can use the ss command or netstat command, which will list all the connections (regardless of the state they are in) including UNIX sockets statistics.
# ss -o state established '( sport = :http or sport = :https )' OR # netstat -o state established '( sport = :http or sport = :https )'
Alternatively, you can run the following command to list the numerical port numbers.
# ss -tn src :80 or src :443 OR # netstat -tn src :80 or src :443
You might also find the following articles useful:
That’s all we have in this short article. For more information about the ss utility, read its man page (man ss). You can reach us for any questions, via the comment form below.
View your Linux server’s network connections with netstat
The netstat command provides important insight into your Linux server, both for monitoring and network troubleshooting.
I shared some important first steps to help manage your personal Linux server in a previous article. I briefly mentioned monitoring network connections for listening ports, and I want to expand on this by using the netstat command for Linux systems.
Service monitoring and port scanning are standard industry practices. There’s very good software like Prometheus to help automate the process, and SELinux to help contextualize and protect system access. However, I believe that understanding how your server connects to other networks and devices is key to establishing a baseline of what’s normal for your server, which helps you recognize abnormalities that may suggest a bug or intrusion. As a beginner, I’ve discovered that the netstat command provides important insight into my server, both for monitoring and network troubleshooting.
Netstat and similar network monitoring tools, grouped together in the net-tools package, display information about active network connections. Because services running on open ports are often vulnerable to exploitation, practicing regular network monitoring can help you detect suspicious activity early.
Install netstat
Netstat is frequently pre-installed on Linux distributions. If netstat is not installed on your server, install it with your package manager. On a Debian-based system:
$ sudo apt-get install net-toolsUse netstat
On its own, the netstat command displays all established connections. You can use the netstat options above to specify the intended output further. For example, to show all listening and non-listening connections, use the —all ( -a for short) option. This returns a lot of results, so in this example I pipe the output to head to display just the first 15 lines of output:
$ netstat --all | head -n 15 Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 *:27036 *:* LISTEN tcp 0 0 localhost:27060 *:* LISTEN tcp 0 0 *:16001 *:* LISTEN tcp 0 0 localhost:6463 *:* LISTEN tcp 0 0 *:ssh *:* LISTEN tcp 0 0 localhost:57343 *:* LISTEN tcp 0 0 *:ipp *:* LISTEN tcp 0 0 *:4713 *:* LISTEN tcp 0 0 10.0.1.222:48388 syd15s17-in-f5.1e:https ESTABLISHED tcp 0 0 10.0.1.222:48194 ec2-35-86-38-2.us:https ESTABLISHED tcp 0 0 10.0.1.222:56075 103-10-125-164.va:27024 ESTABLISHED tcp 0 0 10.0.1.222:46680 syd15s20-in-f10.1:https ESTABLISHED tcp 0 0 10.0.1.222:52730 syd09s23-in-f3.1e:https ESTABLISHEDTo show only TCP ports, use the —all and —tcp options, or -at for short:
$ netstat -at | head -n 5 Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 *:27036 *:* LISTEN tcp 0 0 localhost:27060 *:* LISTEN tcp 0 0 *:16001 *:* LISTENTo show only UDP ports, use the —all and —udp options, or -au for short:
$ netstat -au | head -n 5 Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State udp 0 0 *:27036 *:* udp 0 0 10.0.1.222:44741 224.0.0.56:46164 ESTABLISHED udp 0 0 *:bootpc The options for netstat are often intuitive. For example, to show all listening TCP and UDP ports with process ID (PID) and numerical address:
$ sudo netstat --tcp --udp --listening --programs --numeric Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Addr State PID/Program name tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 1/systemd tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN 2500/dnsmasq tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1726/sshd tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1721/cupsd tcp 0 0 127.0.0.1:6010 0.0.0.0:* LISTEN 4023/sshd: tux@ tcp6 0 0 . 111 . * LISTEN 1/systemd tcp6 0 0 . 22 . * LISTEN 1726/sshd tcp6 0 0 ::1:631 . * LISTEN 1721/cupsd tcp6 0 0 ::1:6010 . * LISTEN 4023/sshd: tux@ udp 0 0 0.0.0.0:40514 0.0.0.0:* 1499/avahi-daemon: udp 0 0 192.168.122.1:53 0.0.0.0:* 2500/dnsmasq udp 0 0 0.0.0.0:67 0.0.0.0:* 2500/dnsmasq udp 0 0 0.0.0.0:111 0.0.0.0:* 1/systemd udp 0 0 0.0.0.0:5353 0.0.0.0:* 1499/avahi-daemon: udp6 0 0 . 111 . * 1/systemd udp6 0 0 . 44235 . * 1499/avahi-daemon: udp6 0 0 . 5353 . * 1499/avahi-daemon:The short version of this common combination is -tulpn .
To display information about a specific service, filter with grep :
$ sudo netstat -anlp | grep cups tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1721/cupsd tcp6 0 0 ::1:631 . * LISTEN 1721/cupsd unix 2 [ ACC ] STREAM LISTENING 27251 1/systemd /var/run/cups/cups.sock unix 2 [ ] DGRAM 59530 1721/cupsd unix 3 [ ] STREAM CONNECTED 55196 1721/cupsd /var/run/cups/cups.sockNext steps
Once you’ve run the netstat command, you can take steps to secure your system by ensuring that only services that you actively use are listening on your network.
- Recognize commonly exploited ports and services. As a general rule, close the ports you’re not actually using.
- Be on the lookout for uncommon port numbers, and learn to recognize legitimate ports in use on your system.
- Pay close attention to SELinux errors. Sometimes all you need to do is update contexts to match a legitimate change you’ve made to your system, but read the errors to make sure that SELinux isn’t alerting you of suspicious or malicious activity.
If you find that a port is running a suspicious service, or you simply want to close a port that you no longer use, you can manually deny port access through firewall rules by following these steps:
If you’re using firewall-cmd , run these commands:
$ sudo firewall-cmd –remove-port=/tcp $ sudo firewall-cmd –runtime-to-permanentIf you’re using UFW, run the following command:
Next, stop the service itself using systemctl :
Learn netstat
Netstat is a useful tool to quickly collect information about your server’s network connections. Regular network monitoring is important an important part of getting to know your system, and it helps you keep your system safe. To incorporate this step into your administrative routine, you can use network monitoring tools like netstat or ss, as well as open source port scanners such as Nmap or sniffers like Wireshark, which allow for scheduled tasks.
As servers house larger amounts of personal data, it’s increasingly important to ensure the security of personal servers. By understanding how your server connects to the Internet, you can decrease your machine’s vulnerability, while still benefiting from the growing connectivity of the digital age.
7 steps to securing your Linux server
Harden your Linux server in seven easy steps.
6 open source tools and tips to securing a Linux server for beginners
Use open source tools to protect your Linux environment from breaches.
9 things to do in your first 10 minutes on a Linux server
Before putting a newly provisioned server to work, make sure you know what you’re working with.
Check the Number of active connections on port 80?
Number of connections is not number of users. Each user browser can open multiple connections at the same time. On the opposite, while more rare, multiple users using the same proxy could appear only through one connection.
5 Answers 5
Try just counting the ESTABLISHED connections:
netstat -anp | grep :80 | grep ESTABLISHED | wc -l Also, be careful about not using a colon in your port grep statement. Just looking for 80 can lead to erroneous results from pids and other ports that happen to have the characters 80 in their output.
@MichaelHampton Both grep -w 80 and :80 will also count outgoing http connections, if any. netstat -ntp|awk ‘
This one is lil improved.. netstat -an | grep -w 80 | grep -i established | awk | cut -d: -f1 | sort | uniq -c | sort -n
This will show all connections to the local ports 80 or 443 (add/modify port(s) if needed).
Disclaimer: I realize this is an old question, but it’s still the top result at Google, so I think it deserves an answer utilizing modern utilities.
Taking @d34dh0r53 answer one step «further» (towards an answer with a «broader» perspective), you can also check all the connections sorted according to their state with the following:
netstat -ant | grep : | awk '' | sort | uniq -c | sort -n netstat -ant | grep :8000 | awk '' | sort | uniq -c | sort -n A possible output might be:
1 CLOSING 1 established 1 FIN_WAIT2 1 Foreign 2 CLOSE_WAIT 6 FIN_WAIT1 7 LAST_ACK 7 SYN_RECV 37 ESTABLISHED 44 LISTEN 297 TIME_WAIT Hope it helps and please rise up any elaborations and/or comments you have on the above.