- Segmentation Fault in Linux
- 1. Introduction
- 2. What Is Segmentation Fault?
- 3. What Causes Segmentation Faults?
- 4. Example
- 5. How to Prevent Segmentation Faults?
- 6. Conclusion
- How to Debug Segmentation Faults in C?
- What is the Segmentation Fault?
- Using GDB Compiler for Segmentation Fault
- Key Points to Prevent Segmentation Faults
- Example 1: Program of Segmentation Fault by Dereferencing Pointer from Memory Block in C
- Example 2: Program of Segmentation Fault by Accessing Array Out of Bond in C
- Example 3: Program of Segmentation Fault by Dereferencing Null Pointer in C
- Example 4: Program of Segmentation Fault by Stack Overflow in C
- Conclusion
- About the author
- Kalsoom Bibi
Segmentation Fault in Linux
The Kubernetes ecosystem is huge and quite complex, so it’s easy to forget about costs when trying out all of the exciting tools.
To avoid overspending on your Kubernetes cluster, definitely have a look at the free K8s cost monitoring tool from the automation platform CAST AI. You can view your costs in real time, allocate them, calculate burn rates for projects, spot anomalies or spikes, and get insightful reports you can share with your team.
Connect your cluster and start monitoring your K8s costs right away:
1. Introduction
Understanding the meaning of error messages is an essential skill for any Linux administrator. While some errors like “No such file or directory” or “Permission denied” are clear in their meanings, others may sound a little cryptic. That is the case with the dreaded “Segmentation fault” error.
In this tutorial, we are going to learn what it is, what causes it, and how to troubleshoot the code that generates this kind of error.
2. What Is Segmentation Fault?
In a nutshell, segmentation fault refers to errors due to a process’s attempts to access memory regions that it shouldn’t. When the kernel detects odd memory access behaviors, it terminates the process issuing a segmentation violation signal (SIGSEGV).
Lower-level languages, including C (the foundational language that Unix systems, Linux included, are built on) usually allow a great deal of flexibility on memory usage and allocation. Thus, they leave many of the memory allocation control aspects to the developer’s discretion.
While it leads to more simple and, hopefully, faster binary compiled code, it’s more prone to programming errors and oversights in memory usage.
3. What Causes Segmentation Faults?
In Linux, the segmentation fault can occur in the following conditions:
- Segment Violation Mapping Error (SEGV_MAPERR): Accessing memory outside the application’s address space
- Segment Violation Access Error (SEGV_ACCERR): Accessing memory where the application has no permission or trying to write on read-only memory space
At first glance, it seems that only obvious errors would lead to those conditions. However, that is not true.
Errors like dereferencing null, non-initialized, or freed pointers (variables that reference memory areas), buffer, or stack overflows, can occur after very common programming mistakes.
For instance, calling functions with incorrect or non-initialized pointers as reference parameters, or recursive functions with failing stop conditions can result in a segmentation fault.
4. Example
Let’s see a very simple code snippet that will generate a segmentation violation:
We can compile and run it:
$ ulimit -S -c unlimited $ gcc -o seg_fault -ggdb seg_fault.c $ ./seg_fault Segmentation fault (core dumped)The ulimit command enables the generation of the process’s memory dump on errors. The compiling is done with gcc, the –ggdb option on the compile will insert debug info on the resulting binary.
In addition, we enabled the debug information and the core dumping so we can take a look at where the error occurred:
$ gdb ./seg_fault /var/crash/core.seg_fault . . Reading symbols from ./seg_fault. [New LWP 6291] Core was generated by `./seg_fault'. Program terminated with signal SIGSEGV, Segmentation fault. #0 0x000055ea4064c135 in main () at seg_fault.c:4 4 buffer[0] = 0;However, if we don’t have to debug information in the code, we would still get some useful information, like the name of the function name where that is giving errors.
5. How to Prevent Segmentation Faults?
When programming using pointers, references, and memory arrays, we have to ensure all memory accesses are within the correct boundaries and that they comply with current access restrictions.
More specifically, we must double-check things like:
- Dynamic memory allocation
- Indirect memory access through pointers
- Array indexes with values higher than their current allocated sizes
- Type consistency throughout the code and function parameters calling convention
- String and buffer operations
- Pointer and buffer allocations (watch-out for non-allocated pointers)
- Stop conditions in recursive functions
Additionally, these tips are important not only to increase code robustness but for security also. Moreover, some of those flaws might open our code to attack vectors like malicious code insertion or denial of service exploitation.
6. Conclusion
In this article, we have briefly discussed the “Segmentation fault” error, its causes, and how to pinpoint its occurrence in our code.
How to Debug Segmentation Faults in C?
An access violation happens when the CPU tries to the instruction set outside of its memory area or reads or writes to a reserved location that does not exist, resulting in a segmentation fault. The present application is halted as a result of this action, and an outcome designated as Segmentation Fault is generated. Because data is frequently shared across memory regions on a system, and program storage space is shared among applications, this issue occurs.
Some machines may experience Segmentation Fault, while others do not. If that happens, it usually means you have an issue with your code, and we managed to get away with it on that system by luck. It all relies on how memory is organized and whether or not it is zeroed. We’ll examine how to identify the program’s segmentation problem in this article.
What is the Segmentation Fault?
A segmentation fault, often known as a segfault, is a sort of computer error that happens when the processor attempts to access a memory address outside of its program storage region due to an unanticipated condition. The term “segmentation” refers to a virtual memory operating system’s memory protection method. When working with pointers in C++/C, we frequently run into this issue.
Using GDB Compiler for Segmentation Fault
To discover why the C programs create a segmentation fault, we’ll use GDB. The GDB is a C (and C++) debugger. It enables the program to run up to a specific point, then halts and reports the values of specified variables at that moment, or steps through the program one line at a time, printing the values of each variable after each line is executed. The GDB debugger will help us to figure out which lines are responsible for the segmentation issue.
Key Points to Prevent Segmentation Faults
While memory access failures cause the majority of segmentation faults, it’s critical to ensure that pointers used in a program always refer to acceptable data locations. The following are the ways to prevent segmentation faults.
- As memory access failures cause the majority of segmentation faults, it’s critical to ensure that application pointers always point to valid data locations.
- Before dereferencing a susceptive reference, such as one embedded in a struct that is kept in a list or an array, we should invoke Assert().
- Always remember to correctly initialize pointers.
- A mutex or a semaphore can be used to protect shared resources from concurrent access in multithreading.
- We should use the free() function
Example 1: Program of Segmentation Fault by Dereferencing Pointer from Memory Block in C
We have an illustration of a segmentation fault where we are trying to get access to the address of the pointer that has freed up. In the following C program main function, we have pointer variable declaration “int* a” and we have allocated the memory to the pointer variable “a”. A segmentation fault will be generated when the program tries to read from the dereferencing pointer *a.
int main ( int argc , char ** argv )
On the compilation of the above code seen on the screen below, the line *a=50 causes a segmentation fault.
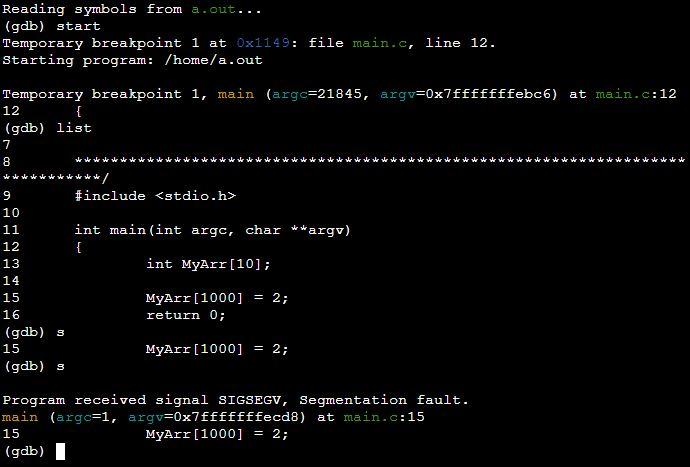
Example 2: Program of Segmentation Fault by Accessing Array Out of Bond in C
A segmentation fault occurs in most cases when a program tries to read or write memory beyond its bounds. In the following program, we have declared an array of index “10” Then, we are attempting to fetch the index of an array that is out of bound and initialized it with the numeric value. This is the point where we will get segmentation faults after executing the out-of-bound line of the program.
int main ( int argc , char ** argv )
int MyArr [ 10 ] ;
MyArr [ 1000 ] = 2 ;
return 0 ;
We are in the GDB compiler where we have used the GDB list command. The GDB list command has printed the line of code from the valve program. From the line “MyArr [1000] =2”, we have got a segmentation fault. You can see it in the following GDB console.
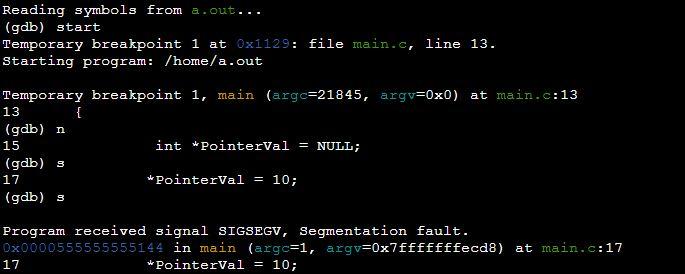
Example 3: Program of Segmentation Fault by Dereferencing Null Pointer in C
References are pointers in programming languages that indicate where an item is stored in memory. A null pointer is a pointer that points to no valid memory location. In the below program, we have declared a pointer variable “pointerVal” and assigned it a null value. The Null pointer exception is thrown or segmentation fault occurs when a null pointer is dereferencing at the line “*pointerVal=10”.
int main ( int argc , char ** argv )
The outcome of the above program has thrown segmentation fault upon execution on line “*PointerVal= 10” shown below.
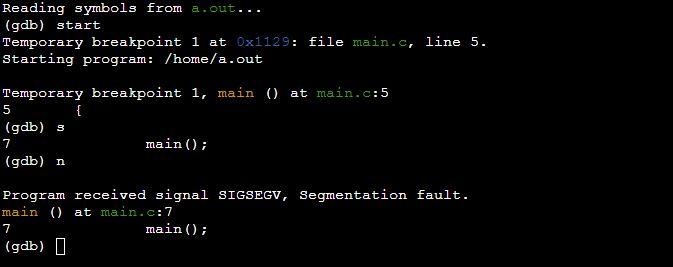
Example 4: Program of Segmentation Fault by Stack Overflow in C
Even if the code doesn’t have a single pointer, it isn’t a pointer issue. The stack overflow then occurs when the recursive function is invoked repeatedly, consuming all of the stack memory. Memory corruption can also happen when the stack runs out of space. It can be fixed by returning from the recursive function with a base condition.
Here in the program, we have the main function and in the body of the main function, we have invoked another main function. This leads to segmentation fault because of stack overflow.
You can see the GDB compiler gives the segmentation fault on line where we have invoked the main function in the program main function block.
Conclusion
The article shed some light on what is segmentation faults and how we can debug them by using the GDB compiler. The GDB compiler determines which lines are responsible for the segmentation failure. The debugging session of segmentation faults is very easy to handle with a GDB compiler in C programming. Then we have taken different scenarios where segmentation faults may occur. I hope this article clarified the segmentation fault problems.
About the author
Kalsoom Bibi
Hello, I am a freelance writer and usually write for Linux and other technology related content