- Finding the PID of the process using a specific port?
- 7 Answers 7
- How to know what program is listening on a given port?
- 8 Answers 8
- Check Which Process Is Using a Port on Linux
- What Will We Talk About?
- How Are Ports Analogous to Physical Ports?
- A Bit About Port of a Service
- Checking the Ports on Linux
- 1. Lsof Command
- 2. SS Command
- 3. Netstat Command
- 4. Fuser Command
- Conclusion
- About the author
- Ali Imran Nagori
Finding the PID of the process using a specific port?
I am installing hadoop on my Ubuntu system. When I start it, it reports that port 9000 is busy. I used:
tcp 0 0 127.0.0.1:9000 0.0.0.0:* LISTEN netstat command might work in many operations systems to allow you get that, you just have to find the arguments that will ensure it will show pids along each known opened port.
7 Answers 7
Your existing command doesn’t work because Linux requires you to either be root or the owner of the process to get the information you desire.
On modern systems, ss is the appropriate tool to use to get this information:
$ sudo ss -lptn 'sport = :80' State Local Address:Port Peer Address:Port LISTEN 127.0.0.1:80 *:* users:(("nginx",pid=125004,fd=12)) LISTEN ::1:80 . * users:(("nginx",pid=125004,fd=11)) You can also use the same invocation you’re currently using, but you must first elevate with sudo :
$ sudo netstat -nlp | grep :80 tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 125004/nginx $ sudo lsof -n -i :80 | grep LISTEN nginx 125004 nginx 3u IPv4 6645 0t0 TCP 0.0.0.0:80 (LISTEN) @AdamB Unless a Mac user arrived here searching for Finding the PID of the process using a specific port
Also you can use lsof utility. Need to be root.
# lsof -i :25 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME exim4 2799 Debian-exim 3u IPv4 6645 0t0 TCP localhost:smtp (LISTEN) exim4 2799 Debian-exim 4u IPv6 6646 0t0 TCP localhost:smtp (LISTEN) This command will also give you processes with established connections, not just processes that are listening .
Not necessarily to be root. And, for those who want to get PID only, you can lsof -i :25 -Fp , which produces output like p1234 .
Important to note that you may need to run as sudo as some processes may be inaccessible to the user.
I am using «CentOS 7 minimal» which has nor netstat neither lsof . But a lot of linux distributions have the socket statistics command (i.e. ss ).
Here is an example of execution:
# ss -tanp | grep 6379 LISTEN 0 128 127.0.0.1:6379 *:* users:(("redis-server",pid=2531,fd=4)) USER PID ACCESS COMMAND 22/tcp: root 598 F. sshd This is a good thing to remember generally. Commands in Linux generally won’t give information on processes started by root/sudo unless the command is run with Sudo. This is true even when the command does not normally need sudo to run correctly.
Running the command with sudo would give you the PID . On my development machine I get:
$ netstat -nlp | grep 8080 tcp6 0 0 . 8080 . * LISTEN - $ sudo netstat -nlp | grep 8080 tcp6 0 0 . 8080 . * LISTEN 16449/java And as mentioned in other answers you can also use the ss or the lsof commands.
I’m working on a Yocto Linux system that has a limited set of available Linux tools. I managed to find the process of a running port using the following commands (where I find the process using port 1883):
root@root:~# netstat -lt Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 0.0.0.0:hostmon 0.0.0.0:* LISTEN tcp 0 0 localhost.localdomain:domain 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:9080 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:1883 0.0.0.0:* LISTEN tcp 0 0 . hostmon . * LISTEN tcp 0 0 localhost:domain . * LISTEN tcp 0 0 . ssh . * LISTEN tcp 0 0 . 1883 . * LISTEN root@root:~# fuser 1883/tcp 290 root@root:~# ps | grep 290 290 mosquitt 25508 S /usr/sbin/mosquitto -c /etc/mosquitto/mosquitto.conf 12141 root 8444 S grep 290 As we can see above, it’s the program /usr/sbin/mosquitto that’s using port 1883.
Proto Recv-Q Send-Q Local Address Foreign Address State Benutzer Inode PID/Program name tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 0 55233 - tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN 1000 3166326 364815/node tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN 127 36032 - tcp 0 0 127.0.0.1:587 0.0.0.0:* LISTEN 0 55234 - tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 0 2927660 - tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN 127 36034 - tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 0 30995 - tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN 101 26903 - tcp 0 0 127.0.0.1:6379 0.0.0.0:* LISTEN 132 32262 - tcp6 0 0 127.0.0.1:9300 . * LISTEN 129 40952 - tcp6 0 0 . 35729 . * LISTEN 1000 3088940 355480/grunt tcp6 0 0 ::1:9300 . * LISTEN 129 40945 - tcp6 0 0 ::1:9200 . * LISTEN 129 41261 - tcp6 0 0 ::1:631 . * LISTEN 0 2927659 - tcp6 0 0 127.0.0.1:9200 . * LISTEN 129 41262 - tcp6 0 0 . 9003 . * LISTEN 1000 3234646 373445/code tcp6 0 0 . 22 . * LISTEN 0 31006 - tcp6 0 0 . 80 . * LISTEN 0 940224 - tcp6 0 0 ::1:6379 . * LISTEN 132 32263 - udp 0 0 127.0.0.53:53 0.0.0.0:* 101 26902 - udp 0 0 0.0.0.0:631 0.0.0.0:* 0 2927684 - udp 0 0 0.0.0.0:5353 0.0.0.0:* 115 29345 - udp 0 0 0.0.0.0:42443 0.0.0.0:* 115 29347 - udp6 0 0 . 5353 . * 115 29346 - udp6 0 0 . 34477 . * 115 29348 - How to know what program is listening on a given port?
I suspect a program is listening on port 8000 on my machine. When I run the following command, I get this error:
> python -m SimpleHTTPServer # Lots of python error socket.error: [Errno 98] Address already in use If I use another port ( 8000 is the default), the web server runs fine. If I run wget localhost:8000 from the command line, it returns 404 Not Found . What can I do (or what tools are available) to find what program is listening on port 8000 , and from there where that program is configured?
8 Answers 8
Open your terminal and type as
that command will list you the application used by that port with PID. (If no results run via sudo since your might have no permission to certain processes.)
For example, with port 8000 ( python3 -m http.server ):
$ lsof -i :8000 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME python3 3269 user 3u IPv4 1783216 0t0 TCP *:8000 (LISTEN) $ sudo lsof -i :22 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME sshd 998 root 3u IPv4 1442116 0t0 TCP *:ssh (LISTEN) sshd 998 root 4u IPv6 1442118 0t0 TCP *:ssh (LISTEN) @Imray the example searches for port 8881. The PID column contains the process IDs and the NAME column contains the ports.
You can use netstat to see which process is listening on which port.
You can use this command to have a full detail :
if you need to know exactly which one is listening on port 8000 you can use this :
sudo netstat -peanut | grep ":8000 " There is no process that can hide from netstat.
To kill/end the process use kill
To expound on the answer by @33833 you can get some very detailed info, for example:
$ lsof -i :8000 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME squid3 1289 proxy 15u IPv6 14810490 0t0 TCP *:8000 (LISTEN) $ ps -fp 1289 UID PID PPID C STIME TTY TIME CMD proxy 1289 1 0 09:48 ? 00:00:00 /usr/sbin/squid3 -N -f /etc/squid-deb-proxy/squid-deb-proxy.conf I can see right there that squid is the process, but it is actualy my squid-deb-proxy that is taking up the port.
Another good example of a java app:
$ lsof -i :4242 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME java 3075 root 86u IPv4 12019 0t0 TCP *:4242 (LISTEN) $ ps -fp 3075 UID PID PPID C STIME TTY TIME CMD root 3075 1 15 May24 ? 3-16:07:25 /usr/local/crashplan/jre/bin/java -Dfile.encoding=UTF-8 -Dapp=CrashPlanService -DappBaseName=CrashPl You can see in lsof (LiSt Open Files) that it is java, which is less than helpful. Running the ps command with the PID we can see right away that it is CrashPlan.
Check Which Process Is Using a Port on Linux
In computer networking, a port represents a logical entry and exit point for a connection. Ports are based on software and are entirely virtual. These ports on a computer are managed by the operating system.
What Will We Talk About?
This quick tutorial demonstrates the various methods to determine which Linux process or service is currently listening on a specific port. Let’s talk about ports and their purpose.
How Are Ports Analogous to Physical Ports?
Just as physical ports help to interact with various peripheral devices connected to a computer, ports help the different services to communicate with each other. These services can be on the same computer or on different computers.
A Bit About Port of a Service
To listen for incoming connection requests, a process associates itself with a port number. Most processes are set up with a default port, and they have to use that port as per their specification. They do not automatically switch to the other port unless their configuration is explicitly modified.
A few examples of protocols and their associated default ports include the Secure Shell (SSH) protocol (port22), the Apache HTTP (port80), the MySQL database server (port3306), and so forth. You may use this information to discover which default port does a service utilizes.
The config file of these services can be edited to use some other port as well.
Checking the Ports on Linux
Let’s now see how to check what port/ports a process is using on Linux. Here, we will show you the different commands for this purpose.
1. Lsof Command
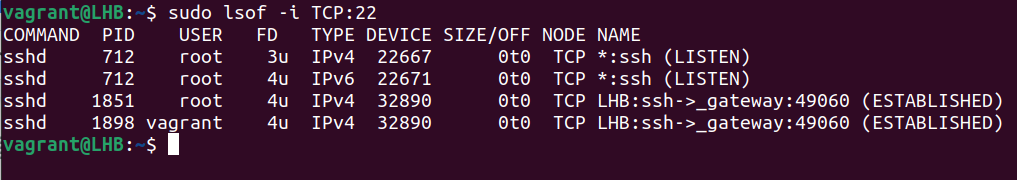
The lsof utility is helpful to obtain a list of the ports which are used by your system. Let’s consider the following example to get an information about a process (processes) using the TCP port 22:
The lsof command gives more information like the user’s name and what process IDs are linked to each process. It works with both TCP and UDP ports.
2. SS Command
The ss command is another way to find out which processes are linked to a certain port. Although lsof is the more common abbreviation, some people may find ss to be more handy.
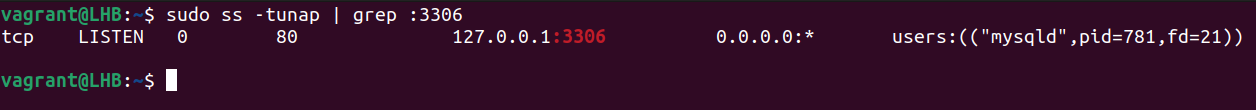
Let’s look for the processes or services that listen on port 3306:
Let’s break down this command:
1. t: It tells the ss command to display the TCP packets.
2. u: It tells the ss command to display the UDP packets.
3. n: It is used to display the port numbers instead of their translations.
4. a: It is used to display the listening as well as non-listening sockets of all types.
5. p: It is used to display the processes that utilize a socket.
The result of the previous command shows which process is utilizing which port. You may also issue the following command:
Here, sport signifies the source port.
These two approaches may help you find the IDs of the processes that are connected to different ports.
3. Netstat Command
The netstat command shows the information about your network and can be used to fix the problems or change the way that your network is set up. It can also keep a close watch on your network connections.
This command is often used to see an information about inbound and outbound connections, routing tables, port listening, and usage stats. Although it has been rendered obsolete in recent years, netstat is still a useful tool for analyzing networks.
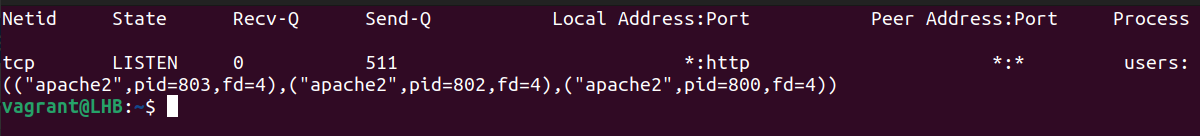
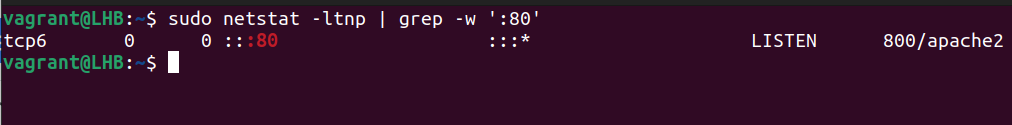
With the grep command, netstat can determine which process or service is using a certain port (by mentioning the port):
The options used here can be classified as follows:
1. t: It only shows the TCP connection.
2. l: It is used to display the results in a list.
3. n: It displays addresses and port numbers in numerical format.
4. p: It displays the PID and program name which are associated with each socket.
4. Fuser Command
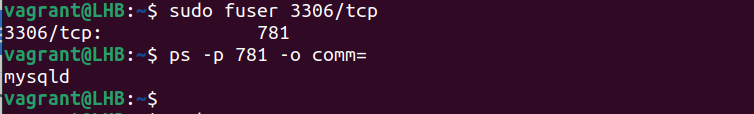
The fuser command determines the processes that utilize the files or sockets. You can use it to list the services which run on a specific port. Let’s take the example of port 3306 and see what services are running here:
This provides us with the process numbers using this port. You can use this process number to find the corresponding process names. For example, if the process number is 15809, the command to use here is as follows:
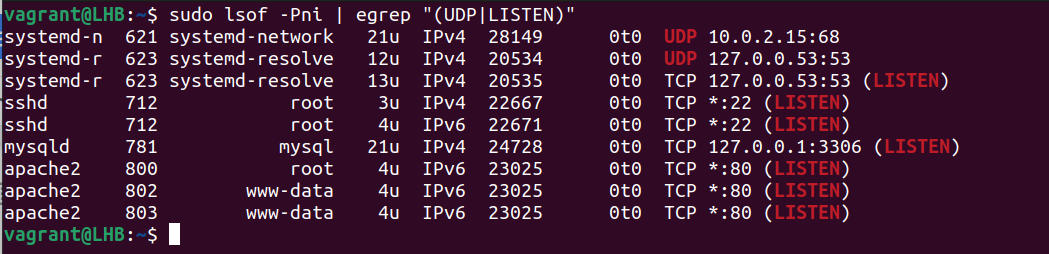
However, certain tools are required to identify the processes that utilize a non-standard port. “LSOF” is a tool for discovering what services are available on a network and what ports they use. Consider the following example. This shows how to list the UDP and TCP listening ports:
The following is a description of the options that are used here:
1. P: It suppresses the port service name lookup.
2. n: It displays the numeric network addresses.
3. i: It lists the IP sockets.
Both the ports and the associated processes are shown in the previously-mentioned result. This way is particularly useful for processes with non-default ports.
Conclusion
In this article, we talked about four possible Linux command-line tools and provided the examples on how to use them to find out which process is listening on a certain port.
About the author
Ali Imran Nagori
Ali imran is a technical writer and Linux enthusiast who loves to write about Linux system administration and related technologies. You can connect with him on LinkedIn
.