- How to :- Find Files Using SUID and SGID Permissions in Linux / Debian
- What is SUID and SGID in Linux?
- Find Files Using SUID and SGID Permissions
- Find Files suing SUID Permission in Linux
- Find Files suing SGID Permission in Linux
- How to audit permissions with the find command
- Quick example of find by name
- Linux security
- Absolute mode versus symbolic mode
- Absolute mode
- Symbolic mode
- Find resource permissions by using absolute mode
- Find by —
- Find by /
- Find resource permissions by using symbolic mode
- Find by —
- Find by /
- Find resources with special permissions configured
- Find files with SUID configured
- Find files with SGID configured
- Find files with the Sticky Bit configured
- Bonus examples
- Bonus 1: Use -not to negate results
- Bonus 2: Set permissions by using find and chmod
- Bonus 3: Display permissions by using ls and grep
- Bonus 4: Display ACL permissions
- Wrap up
- How to Find Files With SUID and SGID Permissions in Linux
- What is SUID and SGID?
- How to Find Files with SUID Set in Linux
- How to Find Files with SGID Set in Linux
How to :- Find Files Using SUID and SGID Permissions in Linux / Debian
In this article, I will explain how we can find files using SUID and SGID permissions in Unix/Debian system. Commonly these permission referred as ” Special Permission” in Linux.
What is SUID and SGID in Linux?
Set Owner User ID (SUID) it is a special file permission in linux given to a file. We can also say that it is temporary permission given to a user to run a specific program or files with specific permissions of the the file owner rather that user who runs it.
Set Group ID (SGID) it is a special file permission in Linux given to a file or folder. In Linux/Unix when a program runs it take access permissions from the logged in user. It is temporary permission to a user to run specific program or file with the specific permissions of the file group permission to be a member of that group to execute the file. So in simple word we can say that user will get file group’s permissions when executing a files.
SGID is similar as SUID. Main difference between both is that SUID is a owner of the file permission and SGID is a group’s permissions when executing a files instead of logged in user inherit permission.
Now let’s find the files which have SUID and SGID set using the find command.
Find Files Using SUID and SGID Permissions
Note :- Some directories like /etc/, bin, /sbin etc. require root privileges to access the or list. If you are a normal user you should have sudo access.
Find Files suing SUID Permission in Linux
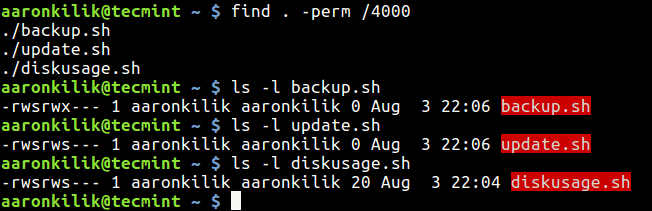
Follow this below command to find the all files with SUID set in the current directory using –perm options for example find the files only with permission set to 4000.
You can also use the ls command with –l option to view the permissions on the listed files.
Find Files suing SGID Permission in Linux
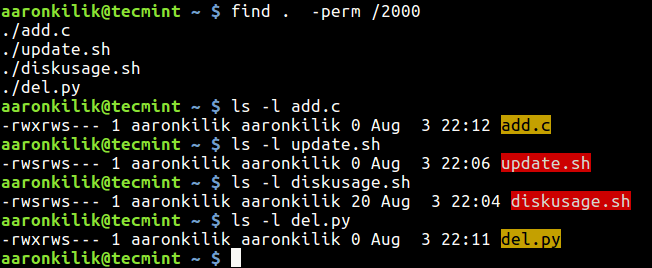
Follow this below command to find files with SGID set in current directory.
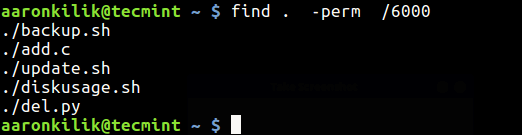
If you want to find both SUID or SGID set file, run the below command:
That’s all . In this article I explained how to find files using SUID and SGID in Linux.
Follow my this tutorial to learn about UMASK.
How to audit permissions with the find command
You can audit permissions on your Linux system by using the find command with the -perm option. Plus four bonus permissions auditing methods.
Let’s face it: The Linux filesystem can be complex. Add in mounted remote filesystems, removable media, and any server-specific directories you have created, and you or your users may find it difficult to remember exactly where a given file is stored. That’s where the find command comes in. It allows you to search for files or directories based on various criteria. I’ll do a basic review of find below, but this article’s focus is a bit different: Find resources by permissions.
Why do I need to find by permissions?
- Security audit
- Troubleshoot user access complaints
- Troubleshoot application access issues
Quick example of find by name
There are other articles on Enable Sysadmin that cover the find command effectively. I will quickly summarize the command here, however.
find (where to search) (what to search for)# find /etc -name rsyslog # find /home/user01 -type dLinux security
However, this article focuses on using the -perm option, which searches based on permissions settings.
Absolute mode versus symbolic mode
Recall that permissions are set by using the chmod command. The chmod command recognizes both absolute mode and symbolic mode. See my recent article How to manage Linux permissions for users, groups, and others for a review of managing resource access, including the two modes. The find command also recognizes either mode, so you’re able to use whichever comes most naturally to you. For me, that’s absolute mode. You need to recall a few things about absolute mode and symbolic mode to effectively use the find -perms command.
Absolute mode
Absolute mode uses octal values to represent permissions. The values are listed in order as the permission to be assigned to the user, group, and all others.
Sets the user with 7 (rwx), group with 6 (rw), and others with 4 (r) for file1 .
Symbolic mode
Symbolic mode uses symbols to represent access levels, and it uses mathematical operators to give (+) or remove (—) permissions.
Gives the others identity read and write to file1 .
Find resource permissions by using absolute mode
The most fundamental permissions search uses no additional parameters. The statement reads as «find a resource with these permissions.»
The command is: Search the /etc directory for resources with the 777 access level (rwx for all identities).
The above example only finds resources with exactly the specified permission—no more and no less. What if you need a little more flexibility? There are two additional parameters that can be very useful. The first is the — character (dash), and the second is the / character (slash). Let’s look at both.
Find by —
The use of the — option means «at least this permission level is set, and any higher permissions.»
This example displays all resources in the current directory with at least 644 permissions.
Find by /
The use of the / option means «any of the permissions listed are set.»
This example displays resources with 644 or greater permissions.
Find resource permissions by using symbolic mode
Symbolic mode uses the ugo symbols (user, group, others), rwx symbols (read, write, execute), and mathematical operators (such as + or —) to define permissions.
Find by —
The — option operates the same in symbolic mode as it did above in absolute mode. It displays resources with «at least this access level.»
Find by /
The / also functions the same in symbolic mode. It displays resources with «any permissions listed.»
Linux standard permissions are very common, and now you know how to search for resources with a given level of access configured. However, Linux also takes advantage of special permissions. The find command can display these permissions, as well.
Find resources with special permissions configured
Linux special permissions set additional access controls on resources. There are three special permissions: Set User ID (SUID), Set Group ID, (SGID), and the Sticky Bit. The details of each are outside the scope of this article, but let me quickly summarize:
| Special permission | Description |
| SUID | A file is executed by a user with the identity of the owner, even if that user is not the owner |
| SGID | The contents of a directory automatically inherit the group association of the parent folder (great for directories shared by project teams) |
| Sticky Bit | The file loads into memory automatically and cannot be deleted or altered by anyone other than the owner |
Take a look at this article for more information on the special permissions.
Special permissions are configured using a fourth bit (leftmost):
Tip: The output of the ls -l command will display an s in the executable field for the user if SUID is configured, an s in the executable field for the group if SGID is configured, and a T or t if the Sticky Bit is set (depending on whether execute is also set).
The following content covers searching for files with specific special permissions configured.
Find files with SUID configured
To find files where the SUID access level is defined, use the -perm option but include the fourth digit. SUID has an octal value of 4.
For example, to search for resources with the SUID configured:
Find files with SGID configured
You can use the same syntax to display resources with the SGID permission defined by using the SGID octal value of 2.
For example, to search for resources with the SGID configured:
Find files with the Sticky Bit configured
Finally, you can use the octal value of 1 to display resources with the Sticky Bit configured.
Here is a Sticky Bit example:
Note: The — and / parameters work the same with special permissions as they do with standard permissions.
Bonus examples
Here are a few additional commands that might be useful for displaying permissions. As I wrote the article, I kept thinking, Wait, what about this? and then adding bonus examples. So here are several additional commands for permissions auditing.
Bonus 1: Use -not to negate results
You can use the -not option with find to specify anything that does not match the given criteria.
The first example shows a normal find attempt, and the second displays find with -not .
The above example displays the resources inside of /etc/network that do have 777 permissions configured.
# find /etc/network -not -perm 777This example displays the resources inside of /etc/network that have any permissions other than 777 configured.
Bonus 2: Set permissions by using find and chmod
One of the benefits of find is that it includes an execute function. You can combine this with follow-up commands, such as xargs , rm , or chmod .
# find -perm -111 -exec chmod -R 777 <> \;In this example, the <> characters represent the results of the find command, and the \; characters represent a termination of the chmod command.
Warning: Be careful to understand exactly what the effect of your combined «find + other commands» execution will be. A typo could easily find all files in /etc and then attempt to delete them or configure permissions that lock legitimate users out of their home directories.
Bonus 3: Display permissions by using ls and grep
Sometimes you don’t need the advanced functionality of the find command. Instead, you just need a quick and easy display of specific permissions. In that case, rely on the ls and grep commands.
This command displays all directory contents with the specified permissions.
Bonus 4: Display ACL permissions
The find command does not easily display files with the Access Control List (ACL) permissions applied. In that case, use the getfacl command instead.
Wrap up
The find command is a handy utility to display directories or files that you need to locate. However, find can also be a great security tool because it shows directories and files with specified permissions. As a sysadmin, you can use that information to ensure that the server’s resources are set according to your company’s security policies. Don’t forget that you can use the >> redirector to document these permissions. Such a document can be used as a permissions baseline for future audits.
How to Find Files With SUID and SGID Permissions in Linux
In this tutorial, we will explain auxiliary file permissions, commonly referred to as “special permissions” in Linux, and also we will show you how to find files which have SUID (Setuid) and SGID (Setgid) set.
What is SUID and SGID?
SUID is a special file permission for executable files which enables other users to run the file with effective permissions of the file owner. Instead of the normal x which represents execute permissions, you will see an s (to indicate SUID) special permission for the user.
SGID is a special file permission that also applies to executable files and enables other users to inherit the effective GID of file group owner. Likewise, rather than the usual x which represents execute permissions, you will see an s (to indicate SGID) special permission for group user.
Let’s look at how to find files which have SUID and SGID set using the find command.
$ find directory -perm /permissions
Important: Certain directories (such as /etc, /bin, /sbin etc.) or files require root privileges in order to be accessed or listed, if you are managing your system as a normal user, use the sudo command to gain root privileges.
How to Find Files with SUID Set in Linux
This below example command will find all files with SUID set in the current directory using -perm (print files only with permissions set to 4000) option.
You can use the ls command with -l option (for long listing) to view the permissions on the listed files as shown in the image above.
How to Find Files with SGID Set in Linux
To find files which have SGID set, type the following command.
To find files which have both SUID and SGID set, run the command below.
You may also like to read these useful guides about file permissions in Linux:
That’s it for now! In this guide, we showed you how to find files which have SUID (Setuid) and SGID (Setgid) set in Linux. If you have any questions, use the feedback form below to share any queries or additional thoughts about this topic.