- The 22 Best Linux Distros for Hackers (Pentesting)
- 01. Kali Linux
- 02. Pentoo Linux
- Watch the video on how to install Pentoo
- 03. BackBox
- 04. Parrot Security OS
- 05. Live Hacking OS
- 06. DEFT Linux
- 07. Samurai Web Testing Framework
- 08. Network Security Toolkit
- 09. Bugtraq-II
- 10. NodeZero
- 11. BlackBuntu
- 12. Cyborg Hawk Linux
- 13. Knoppix STD
- 14. Weakerthan
- 15. BlackArch Linux
- 16. Matriux Linux
- 17. Dracos Linux
- 18. Fedora Security Lab
- 19. Caine
- 20. ArchStrike
- 21. URIX OS
- 22. GnackTrack
- Watch some videos we created about Pentesting
- How to Access Windows from Linux with Metasploit
- NOTE: THIS VIDEO IS IN PORTUGUESE
- Scanning Networks with NMAP
The 22 Best Linux Distros for Hackers (Pentesting)
Do you want to learn about computer and network security or find vulnerabilities in your network or are you looking for the best operating systems for ethical and pentesting hackers, or like to know which hackers’ favorite operating system is? — So stop! Here is the list of the most widely used infamous ethical hacker operating systems, or we can say digital forensic tools.
01. Kali Linux
Kali Linux, maintained and funded by Offensive Security Ltd., is one of the most popular and favorite ethical hacking operating systems used by hackers and security professionals. Kali is a Debian-derived Linux distribution designed for fReal or digital forensic hacking and intrusion testing. It was developed by Mati Aharoni and Devon Kearns, from Offensive Security, through the rewriting of BackTrack, their previous forensic Linux distribution, based on Ubuntu.
In addition to desktop support, Kali Linux also has a dedicated project for compatibility and portability for specific Android devices, called Kali Linux NetHunter. When it comes to security tools, this ethical hacking operating system is equipped with more than 600 preinstalled tools and is updated frequently and offered for different platforms, such as ARM and VMware. Kali Linux is now based on a continuous release model.
02. Pentoo Linux
Pentoo is a Live CD and Live USB designed for intrusion testing and security assessment. Based on Gentoo Linux, Pentoo ships as an installable 32- and 64-bit LiveCD. Pentoo is also available as an overlay for an existing Gentoo installation.
The Pentoo kernel includes grsecurity and PAX protection and extra fixes — with binaries compiled from a reinforced tool chain with the latest versions of some tools available.
Watch the video on how to install Pentoo
03. BackBox
BackBox is a Linux distribution for pentesting on Ubuntu. It provides targeted intrusion testing and security assessment, providing a toolkit for analyzing network and computer systems, as well as a complete set of other tools needed for ethical hackers and security testing.
It includes some of the most used Linux security and analysis tools to help security experts, from stress testing to sniffing, including vulnerability assessment, computer forensic analysis and exploitation.
04. Parrot Security OS
Parrot Security OS (or ParrotSec) is a GNU/LINUX distribution based on Debian. This Linux distribution for hackers is designed to perform intrusion testing, vulnerability assessment and mitigation, computer forensic analysis and anonymous browsing. It was developed by the Frozenbox team.
Parrot is a cloud-friendly Linux distribution and, unlike other ethical hacker operating systems, Parrot OS is a lightweight Linux distribution — runs on machines with 265Mb of minimum RAM and is suitable for 32-bit (i386) and 64-bit (amd64), with a special edition, works on old 32-bit machines (486).
05. Live Hacking OS
Live Hacking OS is a Linux distribution full of tools and utilities for ethical hackers, intrusion tests and countermeasures verification. Includes the built-in graphical GNOME user interface. A second variation is available that has only the command line and requires much less hardware requirements.
06. DEFT Linux
DEFT stands for Digital Evidence and Forensic Toolkit and is an open source Linux distribution created around DART (Digital Advanced Response Toolkit) software and based on the Ubuntu operating system. It was developed from the start to offer some of the best open source computer forensics and incident response tools that can be used by individuals, IT auditors, investigators, the military and police.
07. Samurai Web Testing Framework
The Samurai Web Testing Framework is an active Linux environment that has been preconfigured to function as a web pentesting environment. The CD contains the best free and open source tools that focus on testing and attacking websites. In developing this environment, we base our selection of tools on the tools we use in our security practice. We have included the tools used in the four stages of web pentesting.
08. Network Security Toolkit
The Network Security Toolkit (NST) is a Linux-based Live CD that provides a set of open source computer security and networking tools to perform routine security and network monitoring and diagnostic tasks. Distribution can be used as a network security analysis, validation and monitoring tool on servers hosting virtual machines. Most of the tools published in Insecure.org’s “Top 125 security tools” article are available in the toolkit.
09. Bugtraq-II
Bugtraq-II is a GNU/Linux distribution focused on digital forensics, intrusion testing, malware labs and GSM forensics. Bugtraq-II is available in 11 languages, with over 500 ethical security hacker tools installed and configured. Depending on the desktop environment, features vary. The minimum requirements are based on XFCE and KDE;this ethical hacking system needs a 1 GHz x86 processor and 512 MB of system memory and 15 GB of disk space for installation.
10. NodeZero
NodeZero is an open source ethical hacker operating system based on the Linux kernel derived from Ubuntu and designed for use in intrusion test operations.
In addition to allowing the active system to boot, the boot menu contains several advanced options, such as the ability to run a diagnostic test of the system memory, boot from a local drive, start the installer directly and boot the system . secure graphics mode, text mode or debug mode.
With NodeZero, you’ll have instant access to more than 300 intrusion testing tools, as well as a set of basic services needed in operations.
11. BlackBuntu
BlackBuntu is a penetration test distribution with the GNOME Desktop Environment, which was specially designed to train students and information security professionals. It is currently being built using Ubuntu 10.10 and works on the BackTrack reference.
12. Cyborg Hawk Linux
CYBORG HAWK LINUX is an Ubuntu-based hacker operating system created by the team at Ztrela Knowledge Solutions Pvt. Ltd. The Cyborg Hawk intrusion test distribution can be used for network security and assessment and also for digital forensic analysis.
It also has several tools suitable for mobile and wireless security testing. It has more than 700 tools, while other hacking distros have more than 300 and also dedicated tools and menus for malware analysis and mobile security.
13. Knoppix STD
STD is a Linux-based security tool used by hackers. In fact, it is a collection of hundreds, if not thousands, of open source security tools.
It is a Linux Live distribution and its sole purpose in life is to make as many security tools available to you, with the most accurate interface as possible. STD should be used by both novice and professional security professionals, but it is not ideal for Linux beginners.
14. Weakerthan
Weakerthan is another hacker distribution created out of Debian Squeeze. For the desktop environment, it uses Fluxbox. This ethical hacking operating system is ideal for WiFi hackers, as it contains many wireless tools. It has a very well maintained website and a dedicated community.
15. BlackArch Linux
BlackArch Linux — a Linux-based ethical hacker operating system for intrusion testers and security researchers. The new version also has a total of 1400 intrusion testing tools, with the old ones updated and added, making it a mandatory download for hackers and security researchers.
16. Matriux Linux
Matriux Linux — a Debian-based security distribution designed for intrusion testing and hacking. Although it is more suitable for hackers, it can also be used by any Linux user as a desktop system for everyday computing.
Matriux has more than 300 open source tools for intrusion testing and hacking. Because it is new, many security researchers say it is a better alternative to Kali Linux.
17. Dracos Linux
Dracos Linux — another hacker favorite operating system that emerged from Indonesia, built from Linux. Dracos was developed to be a fast, strong and powerful operating system, used to perform security tests (intrusion tests).
With hundreds of tools, including information gathering, forensic analysis, malware, access maintenance and reverse engineering, Dracos Linux is one of the best options for the hacker operating system.
18. Fedora Security Lab
Fedora Security Lab comes with the clean and fast Xfce desktop environment and an essential set of tools like — Wireshark, Sqlninja, Yersinia, Medusa, etc. — to follow a proper test path for security and pentesting. The Fedora Security Lab is maintained by a community of security testers and developers.
19. Caine
Caine — Computer Aided Research Environment — is a GNU/Linux live distribution based on Ubuntu created for ethical hackers and experts in digital forensics. It provides a complete forensic environment with a friendly graphical interface.
20. ArchStrike
ArchStrike is one of the perfect operating systems for Arch Linux-based ethical hackers for security experts. ArchStrike provides a live desktop environment based on the Openbox window manager, along with an extra repository of 32 and 64-bit build security software.
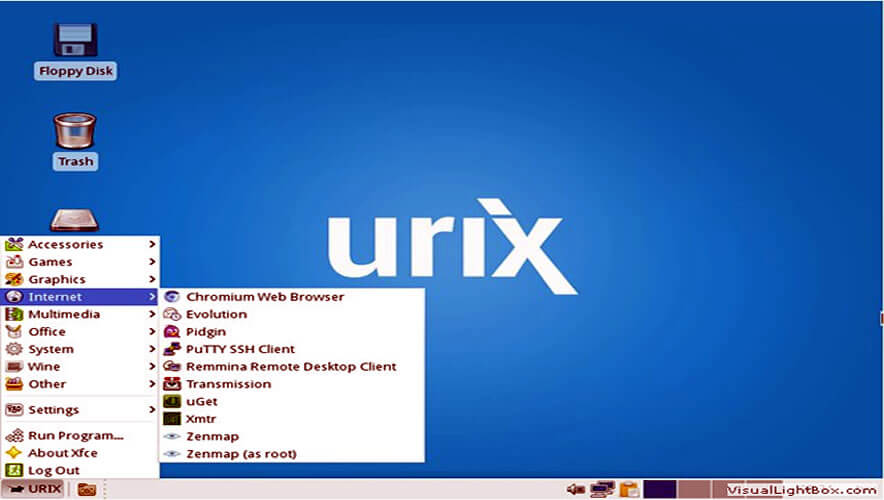
21. URIX OS
URIX OS is an ethical hacker distribution, focused on security, based on openSUSE. In URIX OS, security is enhanced by removing servers and closing entry doors. The distribution also provides several intrusion tools for testing purposes.
22. GnackTrack
GnackTrack — a Linux distribution based on Ubuntu for intrusion testing for GNOME fans.
GnackTrack mainly contains a collection of utilities for pentesting, which have been organized into some categories in the GnackTrack menu entry in the main menu.
Standard applications include Chromium, Firefox, Opera, Gedit text editor, FileZilla FTP client, network scanners, Wireshark and Zenmap, in addition to the XChat IRC client.
Watch some videos we created about Pentesting
How to Access Windows from Linux with Metasploit
NOTE: THIS VIDEO IS IN PORTUGUESE
Scanning Networks with NMAP
This article was based on a post from techlog360 with modifications.