- Checking Open and Listening Ports on Linux Using netstat and ss
- What is a Port in Computer Networking?
- How to Check Which Linux Ports Are in Use?
- Using netstat
- Using ss
- Using lsof
- Check Which Process Is Using a Port on Linux
- What Will We Talk About?
- How Are Ports Analogous to Physical Ports?
- A Bit About Port of a Service
- Checking the Ports on Linux
- 1. Lsof Command
- 2. SS Command
- 3. Netstat Command
- 4. Fuser Command
- Conclusion
- About the author
- Ali Imran Nagori
Checking Open and Listening Ports on Linux Using netstat and ss
Estamos traduciendo nuestros guías y tutoriales al Español. Es posible que usted esté viendo una traducción generada automáticamente. Estamos trabajando con traductores profesionales para verificar las traducciones de nuestro sitio web. Este proyecto es un trabajo en curso.
One step in securing a Linux computer system is identifying which ports are active. Your system’s active ports give you information about which outside applications may be connected to your system. You can also discover if you are unintentionally exposing an application or service to the internet, like a MySQL database. There are several Linux tools that help you discover which ports are in use and identify both ends of active communications. This guide introduces three common tools you can use with links to guides that dive deeper into each tool.
What is a Port in Computer Networking?
Service names and port numbers are used to distinguish between different services that run over transport protocols. Common transport protocols are TCP, UDP, DCCP, and SCTP. These protocols enable communication between applications by establishing a connection and ensuring data is transmitted successfully. Well-known port assignments, such as HTTP at port 80 over TCP and UDP, are listed at the IANA Service Name and Transport Protocol Port Number Registry. These port assignments help distinguish different types of network traffic across the same connection.
How to Check Which Linux Ports Are in Use?
Three tools to help you check ports in use on a Linux system are:
- netstat: This tool shows your server’s network status.
- ss: You can view socket statistics with the ss tool. For example, ss allows you to monitor TCP, UDP, and UNIX sockets.
- lsof: This Linux utility lists open files. Since everything on a Linux system can be considered a file, lsof provides a lot of information on your entire system.
While all three tools help you learn how to check if a port is open in Linux, each program has its own advantages and disadvantages. See the following examples to identify which tool is the best fit for your purpose.
Using netstat
The netstat tool is great for inspecting the following areas of your Linux system:
- Unix sockets and network connections
- Routing tables
- Network interfaces
- Network protocols
- Multicast group membership
Running netstat without any options displays all open sockets and network connections. While this checks if a port is open in Linux, it can generate a lot of output. You can control the output using netstat’s command-line options. For example, to view the PID and program name for a system’s listening TCP connections, run netstat with the following command-line options:
The output resembles the following:
Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:http-alt 0.0.0.0:* LISTEN 381070/monitorix-ht tcp 0 0 localhost:domain 0.0.0.0:* LISTEN 553/systemd-resolve tcp 0 0 0.0.0.0:ssh 0.0.0.0:* LISTEN 2145/sshd: /usr/sbi tcp 0 0 localhost:33060 0.0.0.0:* LISTEN 9638/mysqld tcp 0 0 localhost:mysql 0.0.0.0:* LISTEN 9638/mysqld tcp6 0 0 [::]:http [::]:* LISTEN 10997/apache2 tcp6 0 0 [::]:ssh [::]:* LISTEN 2145/sshd: /usr/sbiTo learn how to install netstat, interpret its output, and view common command line options, see our Inspecting Network Information with netstat guide.
Using ss
Another way to have Linux check ports is via the ss tool. ss was created to improve upon netstat and provides more functionality. It allows you to monitor TCP, UDP, and UNIX sockets. A socket enables programs to communicate with each other across a network and is comprised of an IP address and a port number.
Running the ss with no options displays TCP, UDP, and UNIX sockets. Similar to netstat, this unrestricted list can get quite big on busy machines, so it is useful to restrict the ss command’s output by using command-line options. For example, to view all listening and non-listening TCP sockets issue the following command:
The output resembles the following:
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process LISTEN 0 4096 0.0.0.0:http-alt 0.0.0.0:* LISTEN 0 4096 127.0.0.53%lo:domain 0.0.0.0:* LISTEN 0 128 0.0.0.0:ssh 0.0.0.0:* LISTEN 0 70 127.0.0.1:33060 0.0.0.0:* LISTEN 0 151 127.0.0.1:mysql 0.0.0.0:* ESTAB 0 0 192.0.2.0:ssh 192.0.2.1:51617 TIME-WAIT 0 0 192.0.2.0:ssh 192.0.2.2:60630 TIME-WAIT 0 0 192.0.2.0:ssh 192.0.2.3:51312 TIME-WAIT 0 0 127.0.0.1:http-alt 127.0.0.1:52456 TIME-WAIT 0 0 192.0.2.0:ssh 192.0.2.4:44364 ESTAB 0 0 192.0.2.0:ssh 192.0.2.5:51718 LISTEN 0 511 *:http *:* LISTEN 0 128 [::]:ssh [::]:*Using just the -l parameter tells ss to list all Linux’s listening ports, which are omitted by default, making it easier to check for listening ports in Linux.
To take a deeper dive into the ss tool, read our Learning to Use the ss Tool to its Full Potential guide. This guide provides commands specific to each protocol, commands to view general statistics about a system’s current connections, and ways to filter your output.
Using lsof
Since everything on a Linux system can be considered a file, the lsof tool can report on many aspects of a system, including open network interfaces and network connections. By default, it will list open ports in Linux. The lsof tool is preinstalled on many Linux distributions, so you may consider using it before a tool you need to install.
While one of the most frequent uses of lsof is determining which program listens to a given TCP port, one unique feature of the lsof tool is repeat mode*. This mode allows you to run the lsof command continuously on a timed interval. When inspecting your system to find information about which ports are in use, lsof can return information about which user and processes are using a specific port. For example, when working with a local development environment you may want to find which localhost ports are currently in use. Use the following command to retrieve this information:
The output returns a similar response:
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME Adobe\x20 932 jdoe 14u IPv4 0x3dab8c45775e6b5b 0t0 TCP localhost:15292 (LISTEN) Code\x20H 38254 jdoe 81u IPv4 0x3dab8c45922118fb 0t0 TCP localhost:49336 (LISTEN) VBoxHeadl 49798 jdoe 15u IPv4 0x3dab8c45a01fcf1b 0t0 TCP localhost:rockwell-csp2 (LISTEN) Google 55001 jdoe 37u IPv4 0x3dab8c457579acbb 0t0 TCP localhost:51706->localhost:bmc_patroldb (ESTABLISHED) hugo 57981 jdoe 8041u IPv4 0x3dab8c45a423853b 0t0 TCP localhost:bmc_patroldb (LISTEN) hugo 57981 jdoe 8042u IPv4 0x3dab8c45a3a8e2db 0t0 TCP localhost:bmc_patroldb->localhost:51706 (ESTABLISHED)lsof is a powerful diagnostic tool capable of a significant number of ways that you can combine its command line options to troubleshoot various issues. To learn more about the lsof command read our How to List Open Files with lsof guide. This guide provides information about command-line options, the anatomy of the lsof output, and filtering your output with regular expressions.
This page was originally published on Thursday, February 25, 2021.
Check Which Process Is Using a Port on Linux
In computer networking, a port represents a logical entry and exit point for a connection. Ports are based on software and are entirely virtual. These ports on a computer are managed by the operating system.
What Will We Talk About?
This quick tutorial demonstrates the various methods to determine which Linux process or service is currently listening on a specific port. Let’s talk about ports and their purpose.
How Are Ports Analogous to Physical Ports?
Just as physical ports help to interact with various peripheral devices connected to a computer, ports help the different services to communicate with each other. These services can be on the same computer or on different computers.
A Bit About Port of a Service
To listen for incoming connection requests, a process associates itself with a port number. Most processes are set up with a default port, and they have to use that port as per their specification. They do not automatically switch to the other port unless their configuration is explicitly modified.
A few examples of protocols and their associated default ports include the Secure Shell (SSH) protocol (port22), the Apache HTTP (port80), the MySQL database server (port3306), and so forth. You may use this information to discover which default port does a service utilizes.
The config file of these services can be edited to use some other port as well.
Checking the Ports on Linux
Let’s now see how to check what port/ports a process is using on Linux. Here, we will show you the different commands for this purpose.
1. Lsof Command
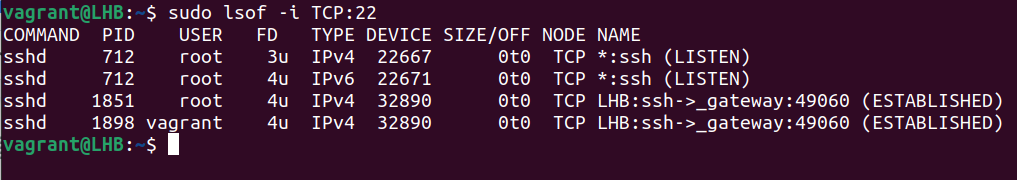
The lsof utility is helpful to obtain a list of the ports which are used by your system. Let’s consider the following example to get an information about a process (processes) using the TCP port 22:
The lsof command gives more information like the user’s name and what process IDs are linked to each process. It works with both TCP and UDP ports.
2. SS Command
The ss command is another way to find out which processes are linked to a certain port. Although lsof is the more common abbreviation, some people may find ss to be more handy.
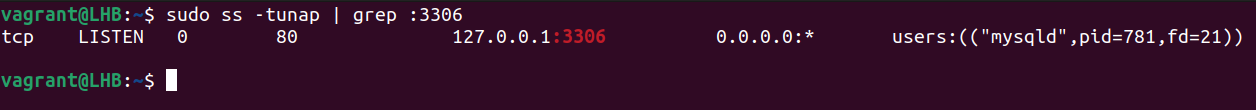
Let’s look for the processes or services that listen on port 3306:
Let’s break down this command:
1. t: It tells the ss command to display the TCP packets.
2. u: It tells the ss command to display the UDP packets.
3. n: It is used to display the port numbers instead of their translations.
4. a: It is used to display the listening as well as non-listening sockets of all types.
5. p: It is used to display the processes that utilize a socket.
The result of the previous command shows which process is utilizing which port. You may also issue the following command:
Here, sport signifies the source port.
These two approaches may help you find the IDs of the processes that are connected to different ports.
3. Netstat Command
The netstat command shows the information about your network and can be used to fix the problems or change the way that your network is set up. It can also keep a close watch on your network connections.
This command is often used to see an information about inbound and outbound connections, routing tables, port listening, and usage stats. Although it has been rendered obsolete in recent years, netstat is still a useful tool for analyzing networks.
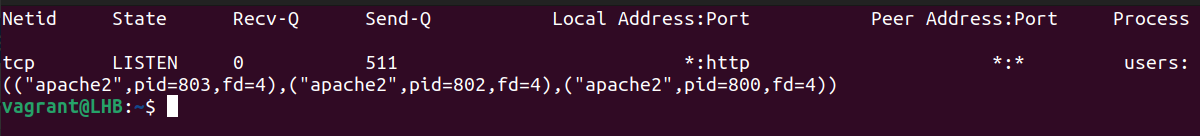
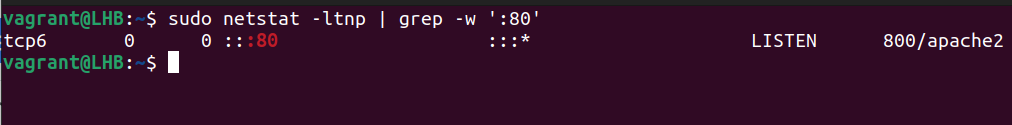
With the grep command, netstat can determine which process or service is using a certain port (by mentioning the port):
The options used here can be classified as follows:
1. t: It only shows the TCP connection.
2. l: It is used to display the results in a list.
3. n: It displays addresses and port numbers in numerical format.
4. p: It displays the PID and program name which are associated with each socket.
4. Fuser Command
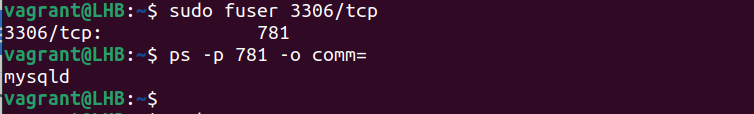
The fuser command determines the processes that utilize the files or sockets. You can use it to list the services which run on a specific port. Let’s take the example of port 3306 and see what services are running here:
This provides us with the process numbers using this port. You can use this process number to find the corresponding process names. For example, if the process number is 15809, the command to use here is as follows:
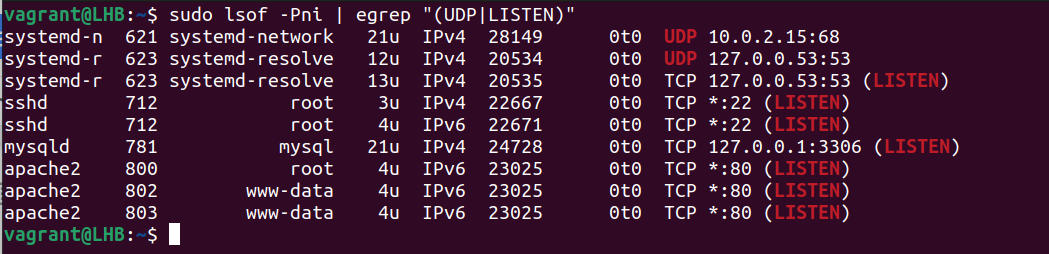
However, certain tools are required to identify the processes that utilize a non-standard port. “LSOF” is a tool for discovering what services are available on a network and what ports they use. Consider the following example. This shows how to list the UDP and TCP listening ports:
The following is a description of the options that are used here:
1. P: It suppresses the port service name lookup.
2. n: It displays the numeric network addresses.
3. i: It lists the IP sockets.
Both the ports and the associated processes are shown in the previously-mentioned result. This way is particularly useful for processes with non-default ports.
Conclusion
In this article, we talked about four possible Linux command-line tools and provided the examples on how to use them to find out which process is listening on a certain port.
About the author
Ali Imran Nagori
Ali imran is a technical writer and Linux enthusiast who loves to write about Linux system administration and related technologies. You can connect with him on LinkedIn
.