- Can a Linux be hacked? How to prevent it?
- How Can Linux be Hacked?
- Running outdated apps and programs
- Installing third party or compromised apps
- User Errors
- How is Linux is so Secure?
- Linux is more secure by design
- How Linux’s open-source nature makes it more secure
- Tips to improve the security and prevent Linux from getting hacked.
- Firewall:
- Downloads:
- Browser:
- Updates:
- Conclusion:
- How to Detect if Your Linux System has been Hacked
- Install A Intrusion Detection System (IDS) to know if the system has been hacked
- Monitor Users’ activity to know if the system has been hacked
- Checking network traffic to know if the system has been hacked
- Checking processes to know if the system has been hacked
- Checking your system for Rootkits infections:
- About the author
- David Adams
Can a Linux be hacked? How to prevent it?
If you have installed Linux or even if you are just thinking about installing one, you might be worried about its security and can it be hacked? I was also worried about the same when I was first installing Linux on my PC. This question is very obvious as there are always people out there who always want to do such things.
You might also have heard this, “Linux is very secure” as its one of the features of Linux. But is it true or just a myth? That’s why I thought about writing this article to answer all these questions.
So, Can Linux be hacked? The answer to this question is Yes, Linux systems can be hacked. Even though they are very secure, hacking a Linux system is still possible. But the chances of getting it hacked are less as compared to Windows.
As there are various factors involved in making Linux a very secure OS. But still, some mistakes can make it vulnerable to hackers.
How Can Linux be Hacked?
Even though Linux is a very secure OS it can be hacked. It’s mainly because of the mistakes from the user’s side, like not updating apps, programs, installing vulnerable third-party apps, and user errors.
Running outdated apps and programs
Running outdated apps and programs can be one of the main reasons for being a Linux system hacked. As when most apps and programs are open source on Linux. Its source code can be seen by anyone to find vulnerabilities.
These vulnerabilities are fixed in updates, but if not updated these vulnerabilities can be used by attackers. The same is true for the Linux system also, if not updated vulnerabilities in it can work in favor of hackers.
Installing third party or compromised apps
Software and apps can work as a gateway for hackers if not downloaded from the official and reputed sources. As hackers bundle apps and software’s with malware inside. This can hack any system as they are installed unknowingly by authorized users.
Hackers take advantage of this and offer various interesting feature and paid software’s for free. But generally these are infected with some kind of malware.
User Errors
User Error can be the most common cause of getting a system hacked. Like downloading document that is instead an executable file. Which if executed can install malware. Or granting root access to a program that can infect the whole system. This is also the most common method of hacking even used on Windows.
The user is tricked into installing malware while the user wanted to install some program. These are some of the common reasons that can get the Linux system hacked.
Let’s now see how what makes Linux secure and then we will see how can we prevent it from possible hacks.
How is Linux is so Secure?
Linux is not like any other distro, it was created with security in mind. Now someone might say Linux is just a kernel. That’s true Linux is just a kernel but that kernel powers most number of servers all across the world. And there is a reason for that.
One most important thing here is the sheer number of malware created for Windows is way more than Linux. 77% of computers use Windows and only 2% use Linux. This explains why creators prefer to create malware for Linux instead of Windows. As malware developed for an operating system is directly proportional to its popularity. Because more popularity benefits scammers and black hat hackers to earn higher profits.
The other reason for Linux’s security is the launching of an executable file. Unlike Windows, in which launching an executable file is easy, the same is not the case with Linux. To launch an executable file (for example .deb files) on Linux requires a user account password is required. This makes the system secure in case of unauthorized installations even if one kept the system unattended for some time.
Linux is more secure by design
In Linux, all the important system-related files are owned by the “root” superuser. So even if the system somehow got infected, the malware or viruses remain at the user account level from where it was installed. This makes removing the malware easy, as these do not affect the whole system.
Only the root user has access to the whole system and system files. And popular Linux distros like Ubuntu do not normally use a root account. So even if a user account got infected. One should be able to fix it through the root user account.
How Linux’s open-source nature makes it more secure
One might think that Linux’s open-source nature makes it vulnerable to attacks as everyone can see its code and find vulnerabilities. But this same principle makes Linux more secure. Unlike Windows in which only a few selected can see the code, find and fix vulnerabilities. Linux has a huge community that’s looking at its code, which makes finding and fixing vulnerabilities fast.
But all these things still can’t prevent Linux from hacking, Linux can still be hacked just like any other operating system. There have already been few instances when Linux systems were hacked. But these instances are few because of the above-mentioned reasons. As Linux systems still can be hacked here is what you can do to save your system from being hacked.
Tips to improve the security and prevent Linux from getting hacked.
Firewall:
Almost all the Linux distributions come pre-installed with a firewall. But these firewalls are not preconfigured and activated. It’s better to enable and configure the firewall to improve security. Although it is not like your system at risk. As generally, all the ports on distros like Ubuntu are closed by default. Which prevents your system from being accessed by intruders.
But activating the firewall is always the better option to improve security. As even though firewall does not consume many resources when enabled, but does ads a layer of security if enabled.
Downloads:
Downloading apps and software from unknown resources is one of the most common causes of systems being hacked. So its better to look out from where you are downloading the software.
I would recommend always downloading the programs from the official repositories or software center only. And if the official repositories don’t have your required software or have an older version, then in such cases download from official websites of the publishers.
Browser:
Use a secure browser and always keep it updated. Firefox is one of them and contains built-in Phishing and malware protection. This keeps you safe from some common phishing attacks.
Updates:
Updates are one of the most important things for improving security of a system. Vulnerabilities when detected are fixed in future updates. So its important to keep your system as well as all the apps updated. This could prevent you from attacks due to any known vulnerability.
Conclusion:
Yes, a Linux distro can be hacked just like any other operating system. But due to the above-mentioned reasons, it’s somewhat more secure than Windows. But you still need to be aware to prevent your system from being hacked does not matter even if its Linux based.
How to Detect if Your Linux System has been Hacked
When there is suspicion a system was hacked the only safe solution is to install everything from the beginning, especially if the target was a server or a device containing information exceeding the user or admin personal privacy. Yet you may follow some procedures to try to realize if your system was really hacked or not.
Install A Intrusion Detection System (IDS) to know if the system has been hacked
First thing to do after suspicion of a hacker attack is to setup an IDS (Intrusion Detection System) to detect anomalies in the network traffic. After an attack has taken place the compromised device may become an automated zombie at the hacker service. If the hacker defined automatic tasks within the victim’s device, these tasks are likely to produce anomalous traffic which can be detected by Intrusion Detection Systems such as OSSEC or Snort which deserve a dedicated tutorial each, we have the following for you to get started with the most popular:
Additionally, to the IDS setup and proper configuration you’ll need to execute additional tasks listed below.
Monitor Users’ activity to know if the system has been hacked
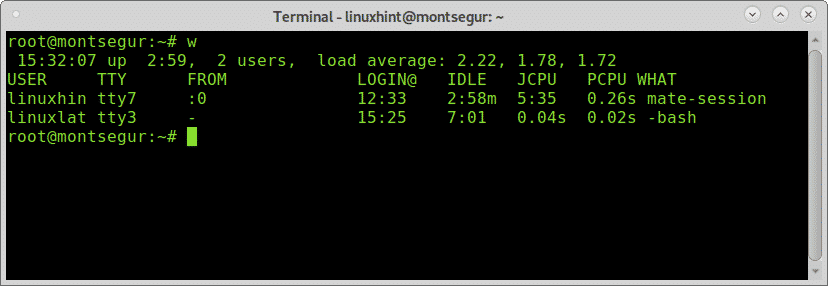
If you suspect you were hacked the first step is to make sure the intruder isn’t logged into your system, you can achieve it using commands “w” or “who”, the first one contains additional information:
Note: commands “w” and “who” may not show users logged from pseudo terminals like Xfce terminal or MATE terminal.
The first column shows the username, in this case linuxhint and linuxlat are logged, the second column TTY shows the terminal, the column FROM shows the user address, in this case there are not remote users but if they were you could see IP addresses there. The LOGIN@ column shows the login time, the column JCPU summarizes the minutes of process executed in the terminal or TTY. the PCPU shows the CPU consumed by the process listed in the last column WHAT. CPU information is estimative and not exact.
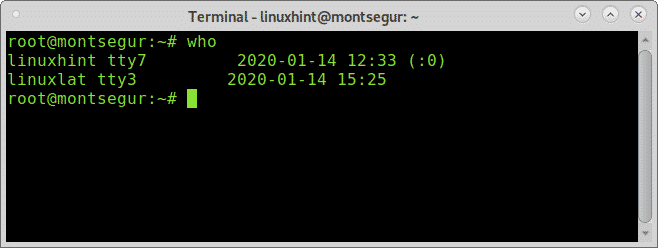
While w equals to executing uptime, who and ps -a together another alternative but less informative is the command “who”:
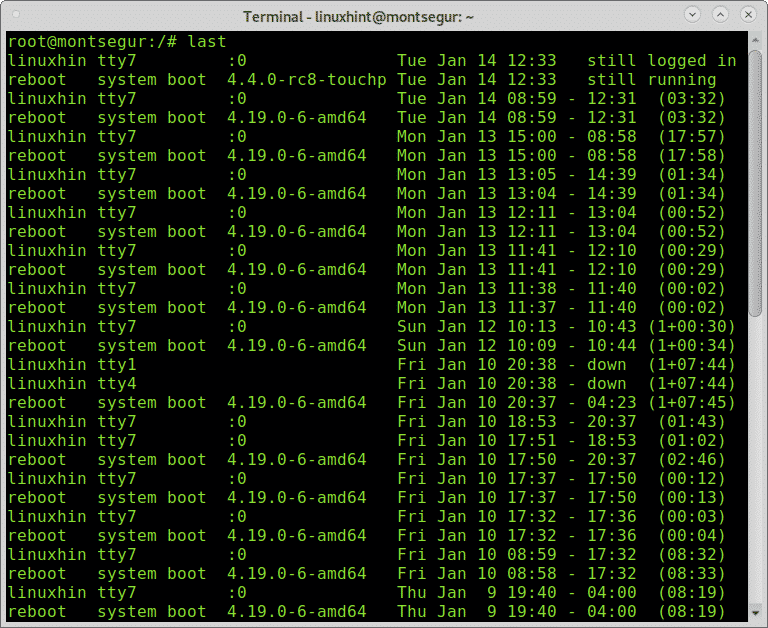
Other way to supervise users’ activity is through the command “last” which allows to read the file wtmp which contains information on login access, login source, login time, with features to improve specific login events, to try it run:
The output shows the username, terminal, source address, login time and session total time duration.
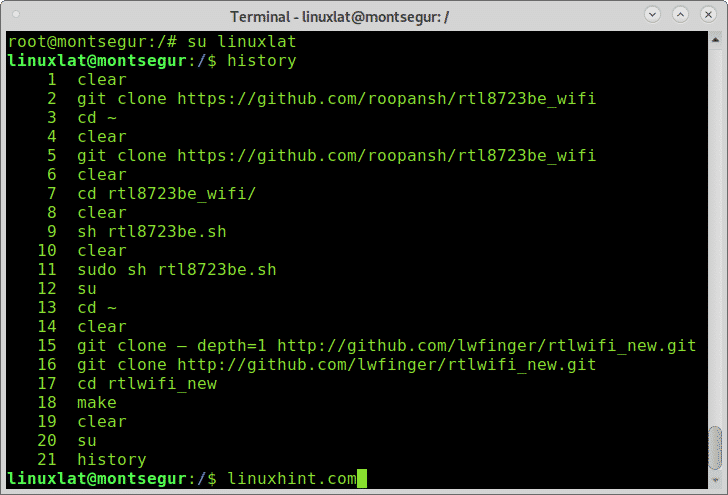
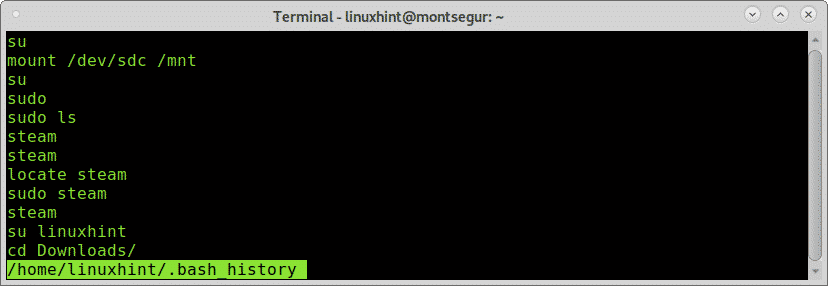
If you suspect about malicious activity by a specific user you can check the bash history, log in as the user you want to investigate and run the command history as in the following example:
Above you can see the commands history, this commands works by reading the file ~/.bash_history located in the users home:
You will see inside this file the same output than when using the command “history”.
Of course this file can be easily removed or its content forged, the information provided by it must not be taken as a fact, but if the attacker ran a “bad” command and forgot to remove the history it will be there.
Checking network traffic to know if the system has been hacked
If a hacker violated your security there are big probabilities he left a backdoor, a way to get back, a script delivering specified information like spam or mining bitcoins, at some stage if he kept something in your system communicating or sending any information you must be able to notice it by monitoring your traffic looking for unusual activity.
To begin lets run the command iftop which does not come on Debian standard installation by default. On its official website Iftop is described as “the top command for bandwidth usage”.
To install it on Debian and based Linux distributions run:
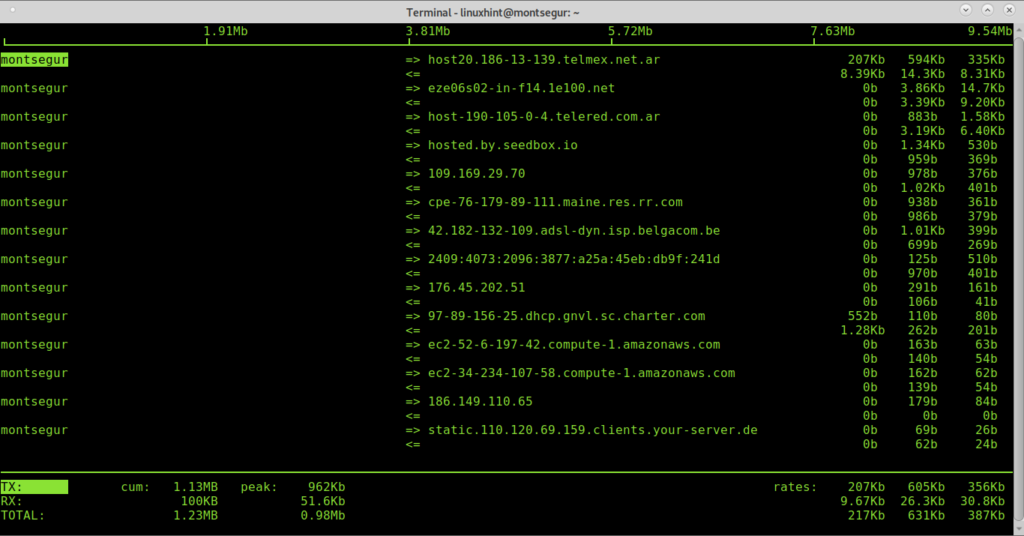
Once installed run it with sudo:
When using iftop close all programs using traffic like web browsers, messengers, in order to discard as many approved connections as possible to analyze what remains, identifying weird traffic isn’t hard.
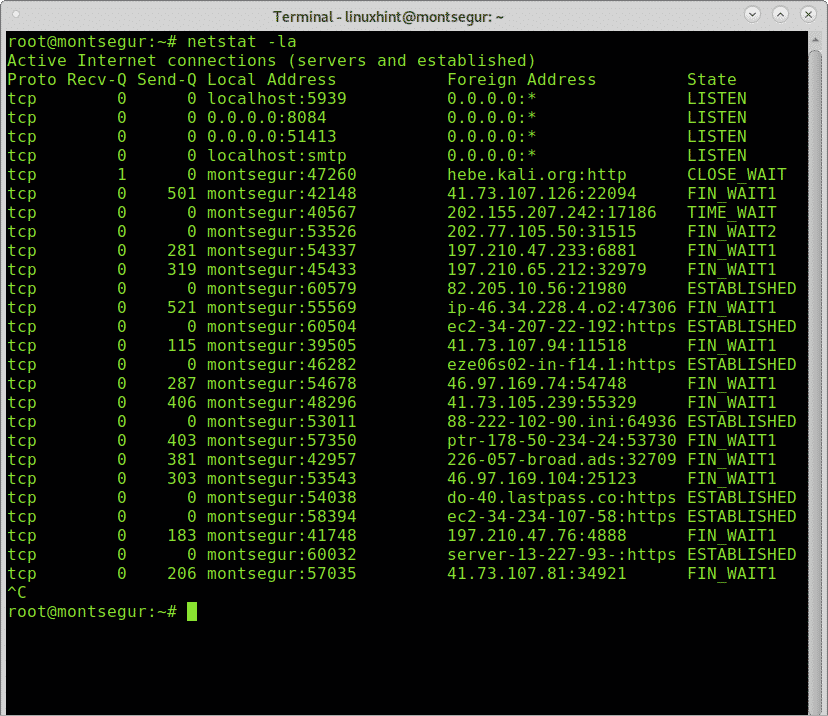
The command netstat is also one of the main options when monitoring network traffic. The following command will show listening (l) and active (a) ports.
You can find more information on netstat at How to check for open ports on Linux.
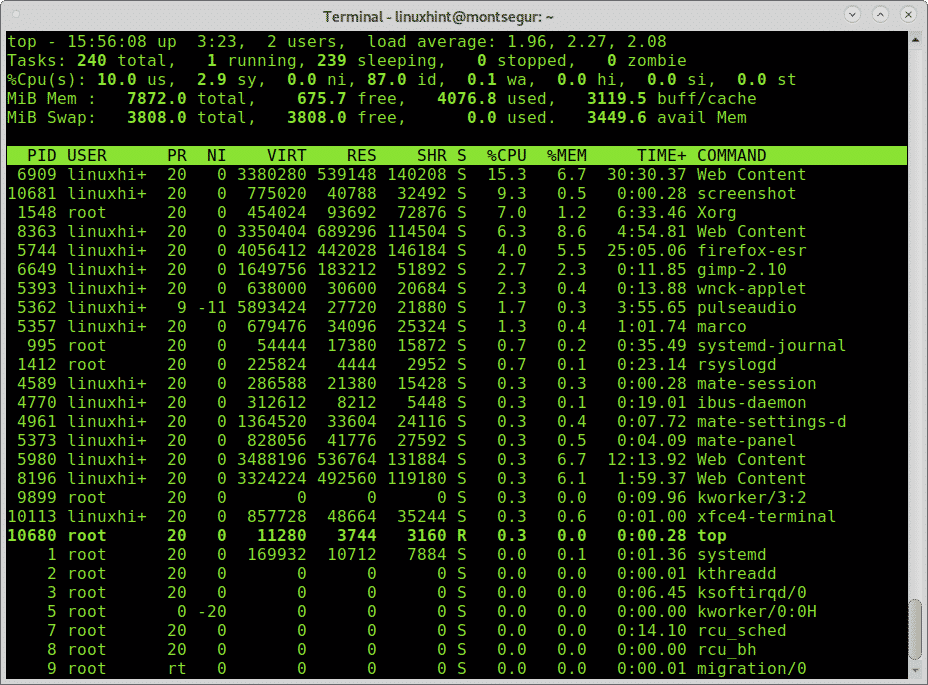
Checking processes to know if the system has been hacked
In every OS when something seems to go wrong one of the first things we look for are the processes to try to identify an unknown one or something suspicious.
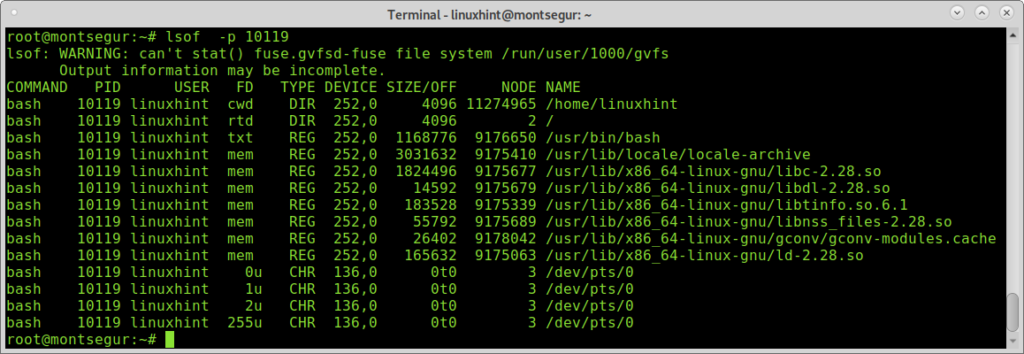
Contrary to classic viruses, a modern hack technique may not produce big packets if the hacker wants to avoid attention. Check the commands carefully and use the command lsof -p for suspicious processes. The command lsof allows to see what files are opened and their associated processes.
The process above 10119 belongs to a bash session.
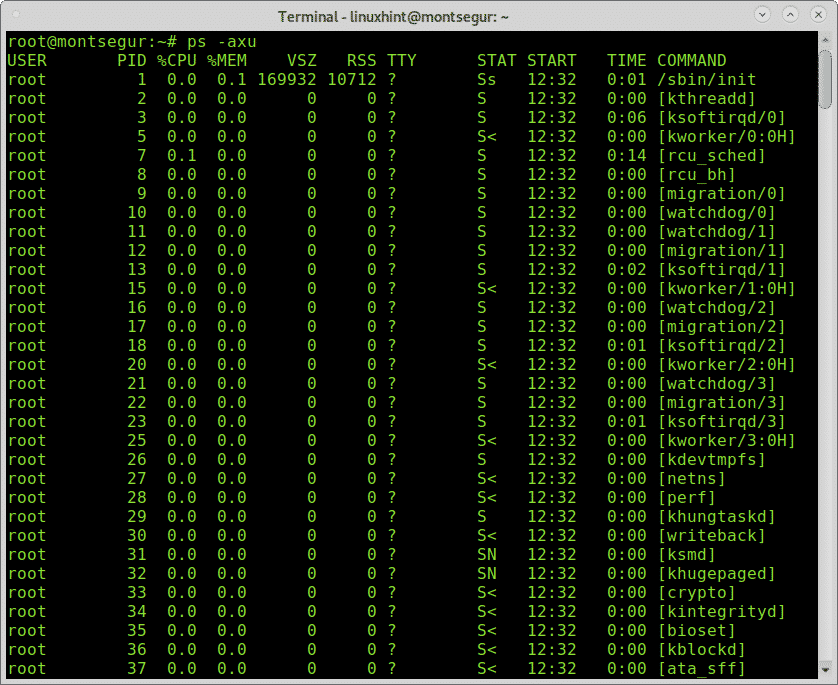
Of course to check processes there is the command ps too.
The ps -axu output above shows the user in the first colum (root), the Process ID (PID), which is unique, the CPU and memory usage by each process, virtual memory and resident set size, terminal, the process state, its start time and the command which started it.
If you identify something abnormal you can check with lsof with the PID number.
Checking your system for Rootkits infections:
Rootkits are among the most dangerous threats for devices if not the worse, once a rootkit was detected there is no other solution than reinstalling the system, sometimes a rootkit can even force a hardware replacement. Luckily there is a simple command which can help us to detect the most known rootkits, the command chkrootkit (check rootkits).
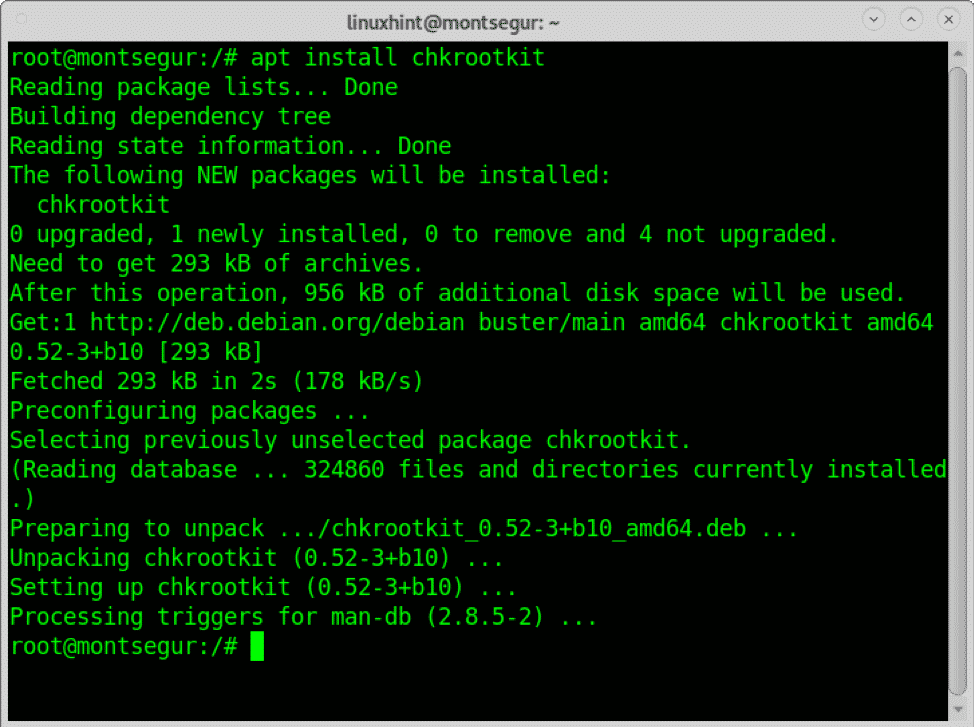
To install Chkrootkit on Debian and based Linux distributions run:
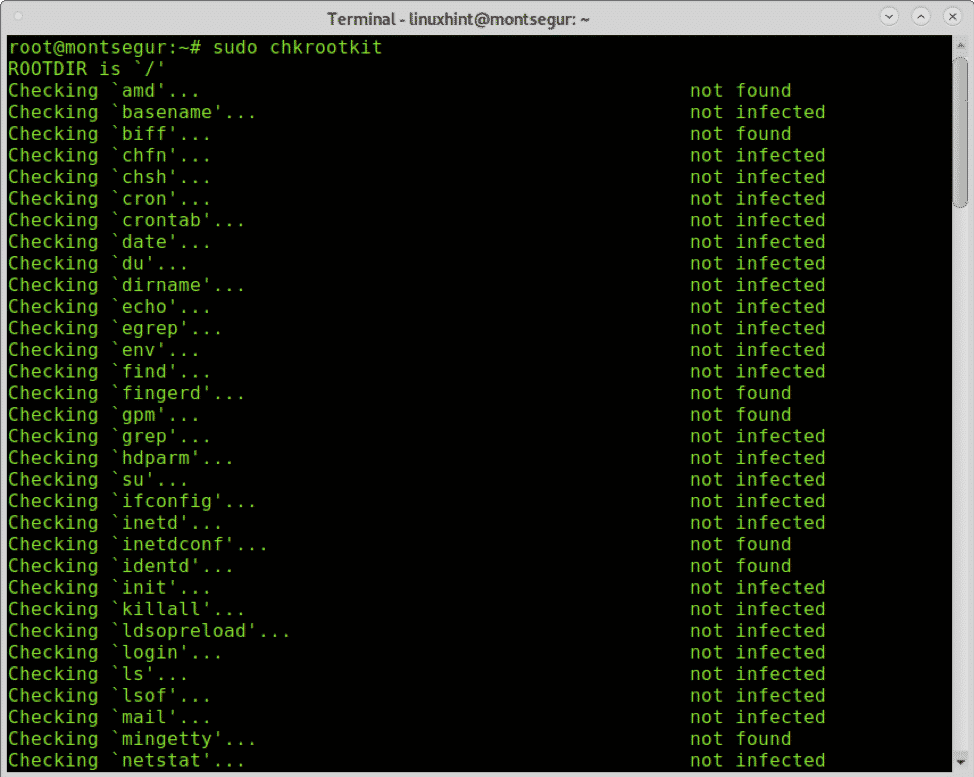
Once installed simply run:
As you see, no rootkits were found on the system.
I hope you found this tutorial on How To Detect If Your Linux System Has Been Hacked” useful.
About the author
David Adams
David Adams is a System Admin and writer that is focused on open source technologies, security software, and computer systems.