- How to check the checksum through commandline?
- 12 Answers 12
- Test:
- How to Verify Checksum on Linux [Beginner Guide]
- How is a Checksum generated?
- Installing GtkHash on Ubuntu
- Using GtkHash
- Verify checksums via Linux command line
- Generating and Verifying SHA256 Checksum with sha256sum
- How accurately does this work?
- How to Use the md5sum Command in Linux
- The md5sum Command with Examples
- Read in Binary Mode
- Read in Text Mode
- Create a BSD-Style Checksum
- Validate md5 Checksum with a File
- Validate Multiple Files
- Display Only Modified Files
- Generate Status Only
- Check Improperly Formatted Checksum Lines
- Skip Reporting Status for Missing Files
- Show Help and Version Information
How to check the checksum through commandline?
I dont want to write a separate script text page just to check this.
This above thing is showing syntax error. But there must be a slick way to get around this? How to do this?
12 Answers 12
shasum httpd-2.4.7.tar.bz2 | awk '$1=="19asdasdasd56462e44d61a093ea57e964cf0af05c0e"' So normally you get this output from shasum
19asdasdasd56462e44d61a093ea57e964cf0af05c0e *httpd-2.4.7.tar.bz2
What my command does it is takes the first field $1 , and compares it against your string. If the strings match, then awk prints «good to go».
Note that for anything other than sha-1 , you need to specify your algorithm. For example, for sha 256 , you can do:
shasum -a256 httpd-2.4.7.tar.bz2 The -a flag specifies the algorithm.
Maybe obvious for most, but, for sha256, use sha256sum . Also, for those wondering, like me: awk and awk.
Also maybe not obvious to everyone, shashum -a256 and sha256sum are not different names for the same command. They are different utilities that may or may not already be on your system depending on your platform.
echo "19asdasdasd56462e44d61a093ea57e964cf0af05c0e httpd-2.4.7.tar.bz2" \ | shasum -c Simply using grep seems to be the best approach:
> shasum httpd-2.4.7.tar.bz2 | grep 19ed9ee56462e44d61a093ea57e964cf0af05c0e The checksum will be highlighted when it is correct:
And when checksum is incorrect, nothing shows.
- Check $? in bash scripting. grep exits with code 0 while something is found, and code 1 while nothing found.
- If you are given an upper-case checksum, use grep -i .
- This approach is typically used in situations when you can ensure that checksum doesn’t exist in the file name, like, curl -o or wget -O then check.
I use the exit code of the previous/last command:
If the checksum is valid the exit code of the last executed command is 0 :
> echo "$ prometheus-$.linux-arm64.tar.gz" | sha256sum -c > echo $? 0 If the checksum is not correct, then the exit code is different than 0 :
> export PROMETHEUS_CHECKSUM='some garbage' > echo "$ prometheus-$.linux-arm64.tar.gz" | sha256sum -c prometheus-2.0.0.linux-arm64.tar.gz: FAILED sha256sum: WARNING: 1 computed checksum did NOT match > echo $? 1 And here is the whole example with an if statement:
#!/bin/bash . echo "$ prometheus-$.linux-arm64.tar.gz" | sha256sum -c if [ $? != 0 ]; then echo 'Prometheus checksum is not valid' exit 1 fi shasum httpd-2.4.7.tar.bz2 | while read -r sum _ ; do [[ $sum == 19asdasdasd56462e44d61a093ea57e964cf0af05c0e ]] && echo "good" || echo "bad" done The test operator is enclosed in [ .. ] and the proper syntax is if; then; fi but you can use && and || operators to simulate it.
Test:
$ touch httpd-2.4.7.tar.bz2 $ shasum httpd-2.4.7.tar.bz2 | while read -r sum _ ; do [[ $sum == 19asdasdasd56462e44d61a093ea57e964cf0af05c0e ]] && echo "good" || echo "bad"; done bad $ shasum httpd-2.4.7.tar.bz2 | while read -r sum _ ; do [[ $sum != 19asdasdasd56462e44d61a093ea57e964cf0af05c0e ]] && echo "good" || echo "bad"; done good $ bash --version GNU bash, version 3.2.51(1)-release (x86_64-apple-darwin13) Copyright (C) 2007 Free Software Foundation, Inc. How to Verify Checksum on Linux [Beginner Guide]
A checksum is a small-sized datum from a block of digital data for the purpose of detecting errors which may have been introduced during its transmission or storage.
So a checksum is a long string of data containing various letters and numbers. You’ll generally find them when downloading files from the web, e.g. Linux distribution images, software packages, etc.
The most common use of checksums is for checking if a downloaded file is corrupted.
For instance, the Ubuntu MATE download page includes an SHA-256 checksum for every image it makes available. So after you’ve downloaded an image, you can generate an SHA-256 checksum for it and verify that the checksum value matches the one listed on the site.
If it doesn’t, that means your downloaded image’s integrity is compromised (maybe it was corrupted during the download process). We will use an Ubuntu MATE “ubuntu-mate-16.10-desktop-amd64.iso” image file for this guide.
How is a Checksum generated?
Each checksum is generated by a checksum algorithm. Without going into the technical details let’s just say it takes a file as input and outputs the checksum value of that file. There are various algorithms for generating checksums. The most popular checksum algorithms are:
Let’s see how to verify a checksum on Linux.
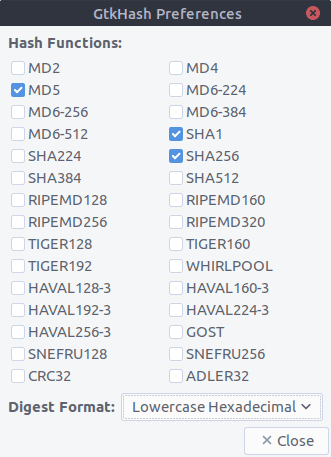
Installing GtkHash on Ubuntu
To install GtkHash on your Ubuntu system, simply run the following command:
That’s it. Then select the checksum algorithms to use:
- Go to Edit >Preferences in the menu.
- Select the ones you’d like to use.
- Hit the Close button.
By default, MD5, SHA-1 and SHA256 are selected.
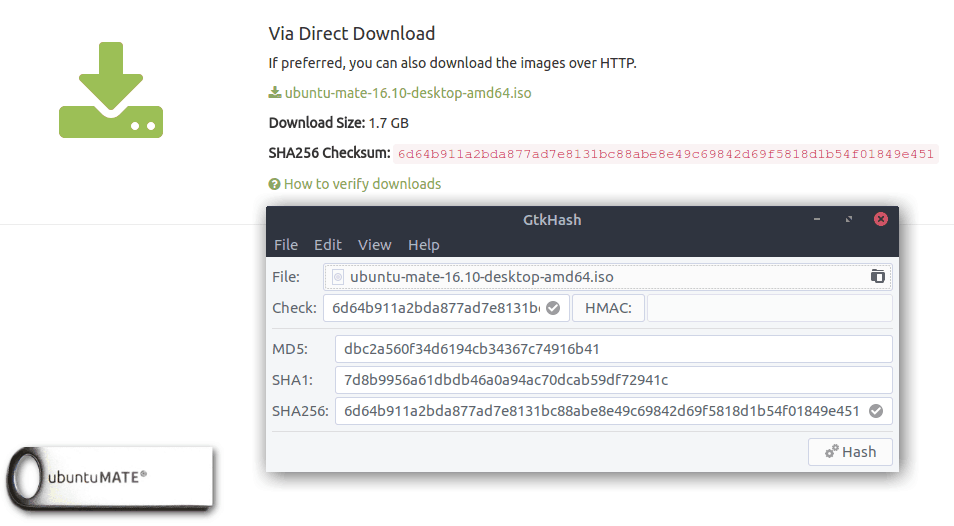
Using GtkHash
Using it is quite straight-forward.
- Select the file you want to check.
- Get the Checksum value from the website and put it in the Check box.
- Click the Hash button.
- This will generate the checksum values with the algorithms you selected.
- If any one of them matches with the Check box, it will show a small tick sign beside it.
Here’s an example showing GtkHash generating a checksum for the Ubuntu MATE iso image (ubuntu-mate-16.10-desktop-amd64.iso):
Verify checksums via Linux command line
Every Linux distribution comes with tools for various checksum algorithms. You can generate and verify checksums with them. The command-line checksum tools are the following:
- MD5 checksum tool is called md5sum
- SHA-1 checksum tool is called sha1sum
- SHA-256 checksum tool is called sha256sum
There are some more available, e.g. sha224sum, sha384sum, etc. All of them use similar command formats. Let’s see an example using sha256sum. We’ll use the same “ubuntu-mate-16.10-desktop-amd64.iso” image file that we used before.
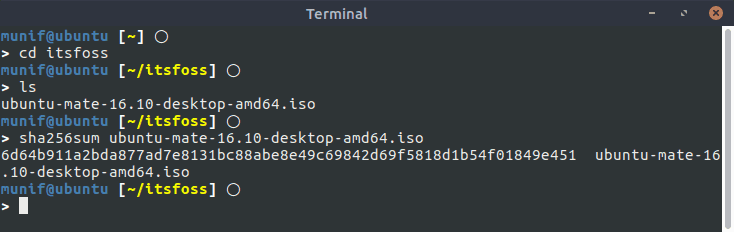
Generating and Verifying SHA256 Checksum with sha256sum
First go to the directory where the .iso image is stored:
Now, to generate the SHA-256 checksum, enter the following command:
sha256sum ubuntu-mate-16.10-desktop-amd64.isoYou’ll see the SHA-256 checksum in your terminal window! Easy, isn’t it?
If the generated checksum matches the one provided on the Ubuntu MATE download page, that will mean no data was changed while you downloaded the file – in other words, your downloaded file is not corrupted.
The other tools mentioned work similarly.
How accurately does this work?
If you’re wondering how accurately these checksums detect corrupted files – if you delete or change even one character from any one of the text files inside the iso image, the checksum algorithm will generate a totally different value for that changed image. And that will definitely not match the checksum provided on the download page.
Do you checksum?
One of the suggested steps while installing Linux is to verify the checksum of your Linux ISO. Do you always follow this step or do you do it only when something goes wrong with the installation?
Was this guide helpful? If you have any questions, let us know! And if you need a similar guide for something else, reach out to us, we’re here to help.
How to Use the md5sum Command in Linux
When you download a file from the internet, it is a good safety practice to check whether you received the original version. Comparing checksums you received from the file creator with the ones you obtain by checking the file yourself is a reliable way to confirm your download’s integrity.
The md5sum command in Linux helps create, read, and check file checksums.
In this tutorial, you will learn how to use the md5sum command to validate the files you receive.
The md5sum Command with Examples
When used on a file without any options, the md5sum command displays the file’s hash value alongside the filename. The syntax is:
After obtaining the hash value, compare it with the MD5 value provided by the file creator.
Note: While md5sum is a reliable method for testing whether the file you received has been compromised, it is useful only if you know that the website you downloaded it from is secure. If hackers gain access to the website, they can change both the file and its checksum, making it appear as if the file you are downloading is safe.
Read in Binary Mode
To read the file in binary mode, use the -b option ( —binary ):
The * character before the file name means that md5sum read it in binary mode.
Read in Text Mode
Use the -t option ( —text ) to read the file in text mode:
Text mode is the default mode for reading files with md5sum .
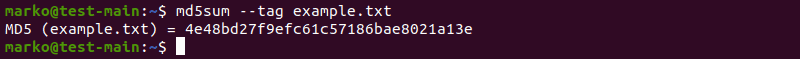
Create a BSD-Style Checksum
Using the —tag option outputs the hash value in the BSD-style format:
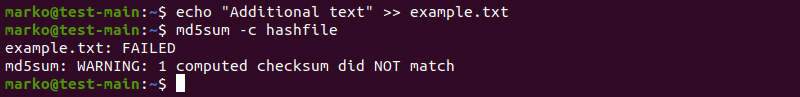
Validate md5 Checksum with a File
To check a file by comparing its hash value with the value provided in a hash file, use the -c option.
1. As an example, create a hash file containing the md5sum output:
md5sum [filename] > [file-containing-hashes]2. Use the following syntax to compare the hash value from the file you created against the current hash value of the .txt file:
md5sum -c [file-containing-hashes]3. If you change the contents of the file and repeat the check, a warning message is displayed:
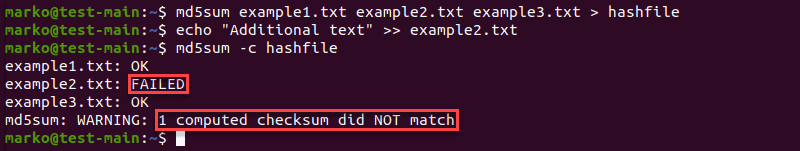
Validate Multiple Files
Use the same md5sum -c procedure to check the integrity of multiple files:
md5sum [filename1] [filename2] [filename3] > [file-containing-hashes]In the following example, the contents of example2.txt have changed, resulting in a warning message from md5sum :
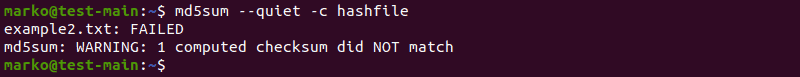
Display Only Modified Files
The —quiet option displays only the files whose hash value has changed. It skips the output of validated files.
md5sum --quiet -c [file-containing-hashes]Generate Status Only
The md5sum command with the —status option does not produce any output but returns 0 if there are no changes and 1 if it detects changes. This argument is useful for scripting, where there is no need for standard output.
The example script below illustrates the use of the —status option:
#!/bin/bash md5sum --status -c hashfile Status=$? echo "File check status is: $Status" exit $StatusWhen the script executes, it shows status 1 , meaning that md5sum detected the change made earlier in example2.txt .
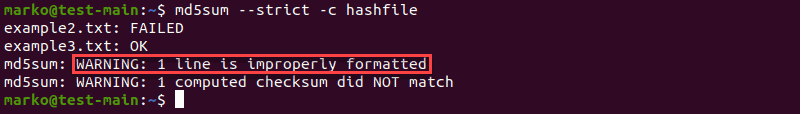
Check Improperly Formatted Checksum Lines
Add the —strict option to exit non-zero for improperly formatted hash values:
md5sum --strict -c [file-containing-hashes]The example shows the output of md5sum —strict when you put invalid characters in the first line of the file containing hashes:
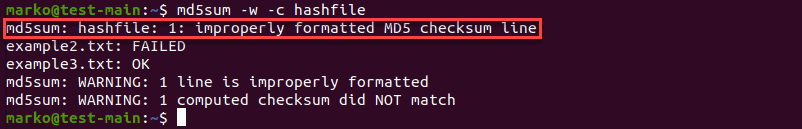
To display which line has an invalid hash, use -w ( —warn ):
md5sum -w -c [file-containing-hashes]The example above shows the -w option displaying that the improperly formatted MD5 checksum line is line 1 of the file.
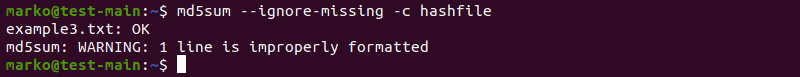
Skip Reporting Status for Missing Files
By default, md5sum shows warnings about the files it cannot find on the system. To override this behavior, use the —ignore-missing option:
md5sum --ignore-missing -c [file-containing-hashes]In the example below, example1.txt was deleted before running the md5sum command. The output ignores the deleted file:
Show Help and Version Information
To get the official help for the md5sum command, type:
To check md5sum version, type:
Note: You should also check out our overview of the diff command to learn how to compare two files line by line.
After completing this tutorial, you should know how to properly use the md5sum command to create, print, or check MD5 checksums.
Marko Aleksić is a Technical Writer at phoenixNAP. His innate curiosity regarding all things IT, combined with over a decade long background in writing, teaching and working in IT-related fields, led him to technical writing, where he has an opportunity to employ his skills and make technology less daunting to everyone.
The echo command prints out a text string you provide as the output message. This tutorial covers the echo.
The ls command (short for list) lists information about directories and any type of files in the working.
A list of all the important Linux commands in one place. Find the command you need, whenever you need it or.
Creating a file in Linux might seem straightforward, but there are some surprising and clever techniques. In.