- How to Check User’s Login History in Linux
- Tutorial Details
- What is the Last Command in Linux?
- Usage of the Last Command
- How to Check a Specific User’s Login History
- How to Check Login History Based on TTY
- Last Command Options
- Limit the Entries to N Number in the Output
- Display the Login History For Today and Yesterday
- Display the Login History For a Specific Date
- Display the Login History For Range of Dates
- Display the Login History for the Last Few Days
- Display the Reboot History
- Display the Shutdown History
- Display the Hostname Field in the Last Column
- Hide the Hostname Field From the Output
- Display the Full Login and Logout Timestamp
- Bonus Tip! How to Check a User’s Failed Login Attempts
- How to check user login history in Linux?
- How Linux store log files?
- How to check the login history?
- How to check the login history of a specific user?
- How to check the specific number of logins?
- How to check bad login attempts:
- Conclusion:
- About the author
- Sam U
- How do I find user login history?
- 2 Answers 2
- last command to the rescue
- Console only logins
How to Check User’s Login History in Linux
A Linux server is operated by multiple users who can login and logout at any given time without any restriction (of course, they should have the proper privileges).
In an occasion like a data breach, you might want to track user activity to investigate the incident, and as a sysadmin, you might want to know who, when, and from where logged into the target machine.
In this case, you can use the last command, a fantastic built-in Linux utility.
Tutorial Details
| Description | Show a Log of the User’s Login History |
| Difficulty Level | Low |
| Root or Sudo Privileges | No |
| Host System and Architecture | Ubuntu 22.10 (x64) |
| OS Compatibility | Ubuntu, Manjaro, Fedora, etc. |
| Prerequisites | last |
| Internet Required | No |
| Discussed Tools in this Article |
What is the Last Command in Linux?
The last command is a tool that sysadmins often use to keep track of user sessions on the server. It can list information about users, such as their usernames, when they log in and out of the system, where they log in from, etc.
This information is pulled from the “/var/log/wtmp” file, which is always modified in the event of a user’s login and logout. You can check out our dedicated article on this topic.
This article will focus mostly on how to use the last command and its different options.
Usage of the Last Command
The last command takes two arguments: one is the option, and the other is the username or TTY (all are optional).
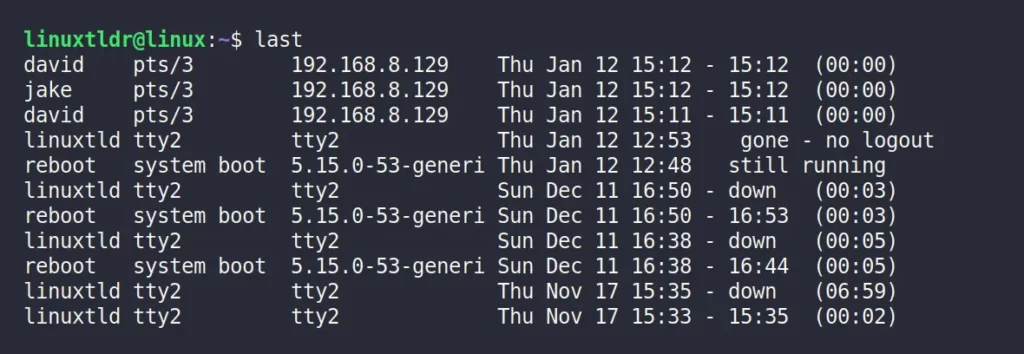
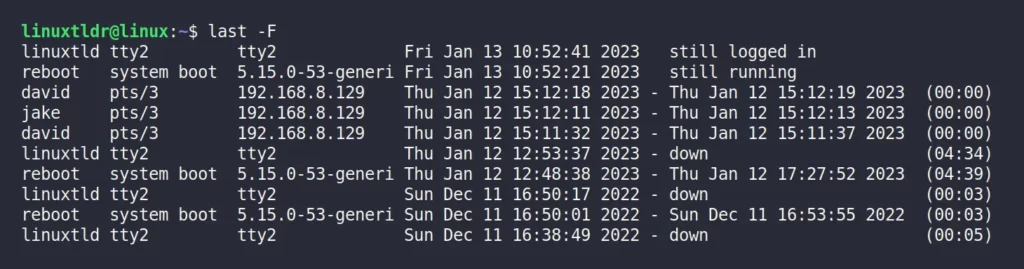
$ last [OPTION] [USERNAME/TTY]If you run the last command without any arguments, the following screen will appear:
Note that this record is listed in reverse chronological order; the first will be the latest record; in this case, the “david” user has recently logged in to the system.
The following is an explanation of each field in the output:
- The username, note that in the event of a system reboot or shutdown, the “last” shows special users “reboot” and “shutdown“.
- The tty user used to start the login process. “pts/*” means via SSH, “tty*” means via terminal, and “0:” means via the desktop environment.
- The host name or the IP address from which the user logged in.
- The login and logout times.
- The duration of the user session; if the user fails to logout, the message “no logout” appears. If the user is still active, it will show “still running” in place of duration.
Now, let’s move on to the next section.
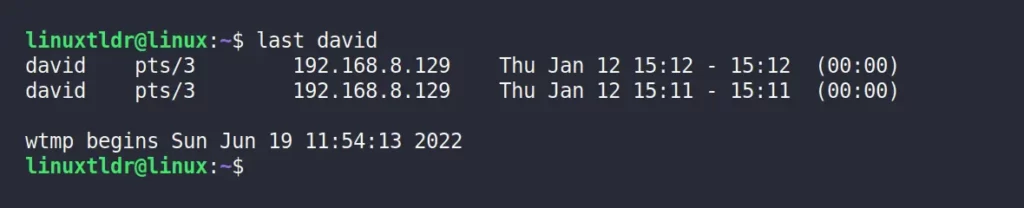
How to Check a Specific User’s Login History
If you know all the user’s login names on the target machine, then you can use that to filter out the result for a particular user.
$ last davidFrom the above picture, it appears that “david” has initiated the login process multiple times on the “Jan 12” date.
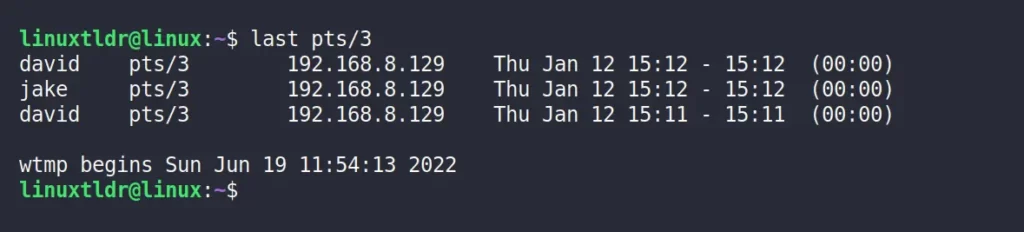
How to Check Login History Based on TTY
Unlike the previous command, you can investigate the user based on TTY; for example, you can specify “pts/*” to check the login attempts held on the target machine via SSH.
From the above picture, it appears that the “david” and “jake” users logged in to the target machine on the “Jan 12” date via SSH.
Now, let’s move on to the next section to check all the options offered by this command.
Last Command Options
The last command supports a variety of options that can limit the entries in the output, display login history for a specific or range of dates, hide/show columns, etc.
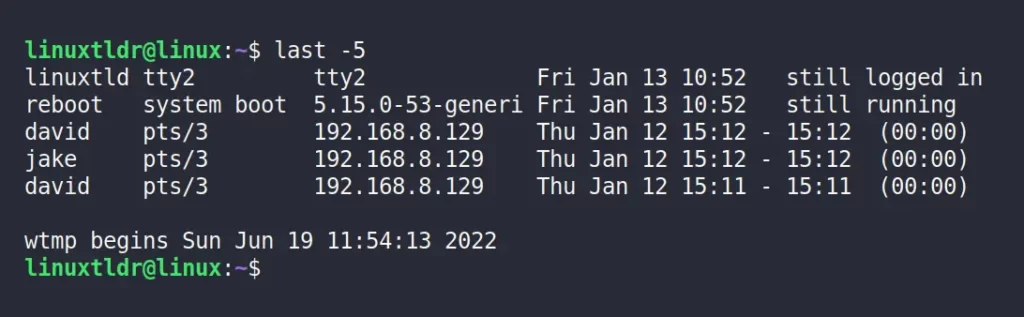
Limit the Entries to N Number in the Output
The “ -N ” option, where “N” refers to any positive integer, is used to specify the number of lines (or entries) to display in the output.
The above command will return the latest five entries in the output.
Display the Login History For Today and Yesterday
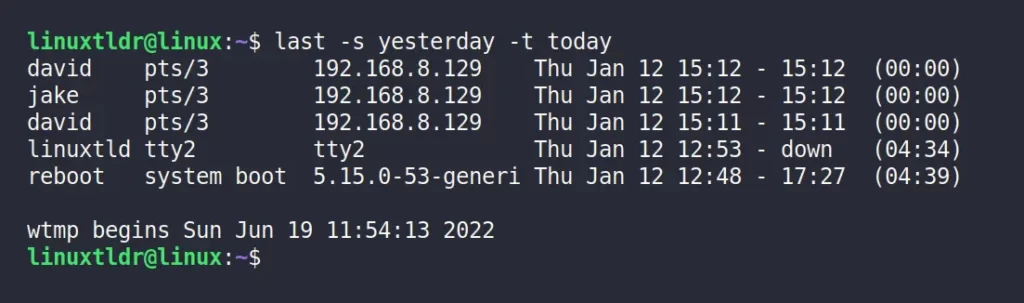
The following command will display the login history for today and yesterday, whereas the “ -s ” flag represents “since” and the “ -t ” flag represents “until“.
$ last -s yesterday -t todayDisplay the Login History For a Specific Date
The “ -p ” flag can be used to show the log of login history for a particular date specified in “YYYY-MM-DD” format.
$ last -p 2022-11-18 Display the Login History For Range of Dates
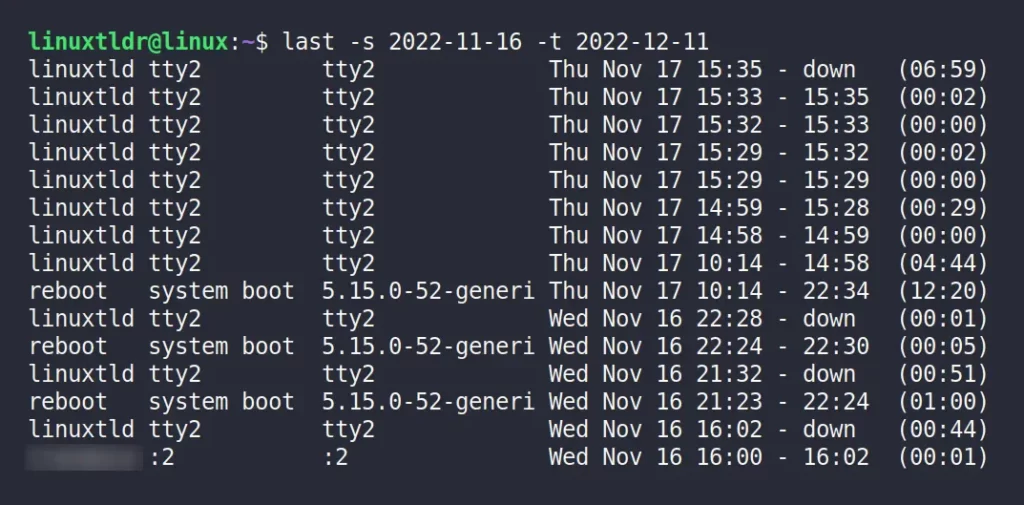
The following command will display the login history from “2022-11-16” to “2022-12-11“.
$ last -s 2022-11-16 -t 2022-12-11Display the Login History for the Last Few Days
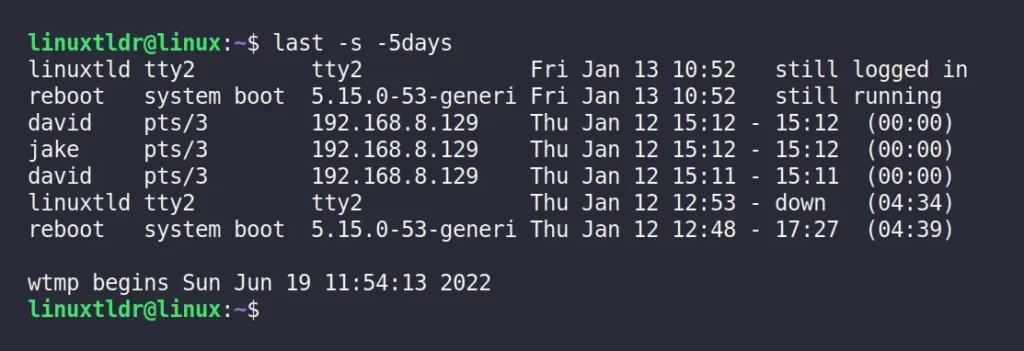
The following command will display the login history for the last five days.
$ last -s -5daysDisplay the Reboot History
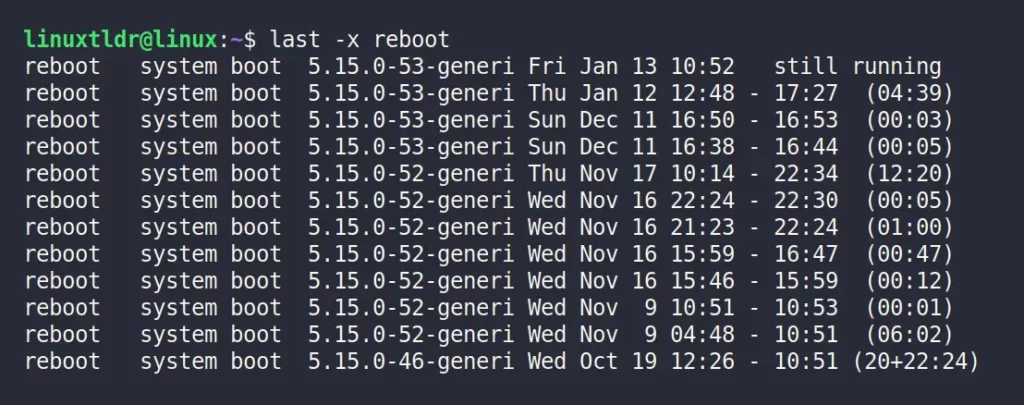
Each time a user reboots the system, a new entry is written in the file with a special “reboot” username that can be used to show a log of all reboots since the log file was created.
The following command will show all the entries with system reboots and run levels changes using the “ -x ” flag.
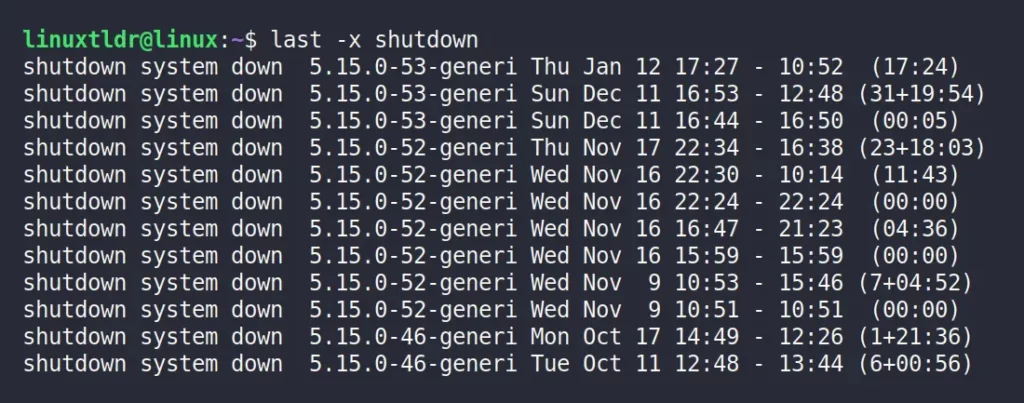
$ last -x rebootDisplay the Shutdown History
Similar to the previous command, whenever users shutdown the system, a new entry is written in the file with the special “shutdown” username.
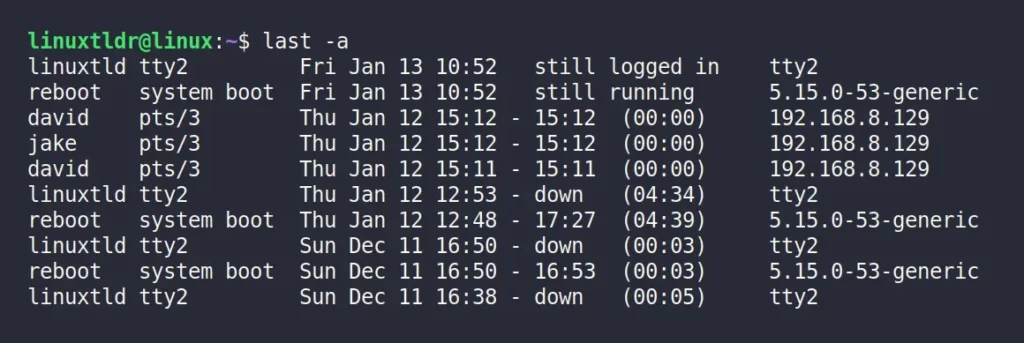
$ last -x shutdownDisplay the Hostname Field in the Last Column
The “ -a ” flag will move the hostname field to the last column so that the result doesn’t get cut off.
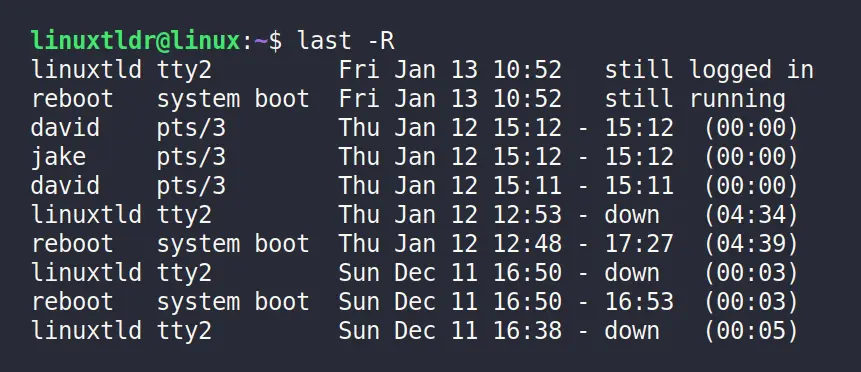
Hide the Hostname Field From the Output
The “ -R ” flag will remove the hostname field from the output.
Display the Full Login and Logout Timestamp
The “ -F ” flag will display the timestamp entries for login and logout in full format.
And here comes the end of all examples.
Bonus Tip! How to Check a User’s Failed Login Attempts
Isn’t it good to look up a user’s login and logout history? But while investigating the user’s login history, you must also consider the failed login attempts held on the target machine.
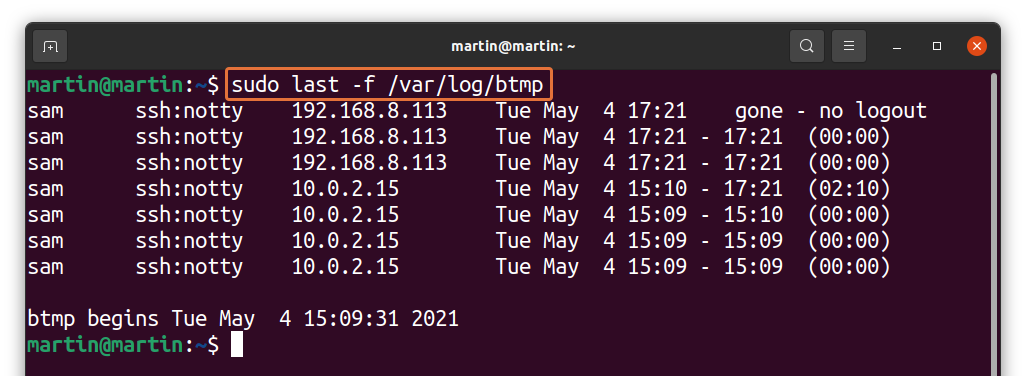
The last command does not display the failed login attempts by users; for this, you have to use another command-line tool known as the lastb command.
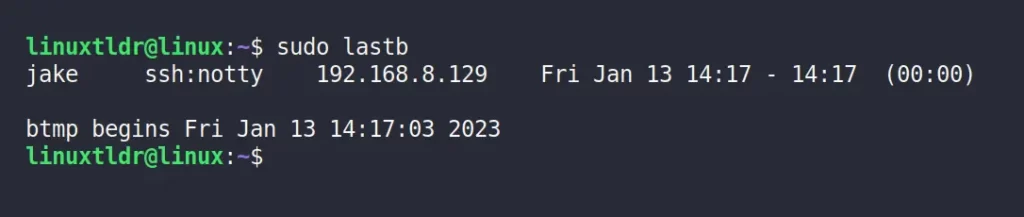
The following command will show a log of all the failed login attempts made by the users on the target machine.
$ sudo lastbThe above output shows that the “jake” user tried to access the target machine via SSH with the wrong authentication information.
Let’s finish this article here; I think you can dig further by yourself.
If you have any questions or queries related to this topic, then feel free to ask them in the comment section.
How to check user login history in Linux?
Linux is one of the most accepted operating systems for multi-user setup. A multi-user operating system means a system that more than one user can access. These systems are mostly used in servers of large organizations, businesses, government, and educational sectors.
Different users access the multi-user operating system, and to monitor users’ activity, it is important to keep an eye on login history. Login history gives useful information about different users who have accessed the machine, such as username, terminal name, IP address, date, and time of logging in. Moreover, login history also helps to identify different issues, especially for troubleshooting.
This write-up is focusing on an approach to check the user login history. Before getting into that, let’s understand how Linux arrange and manage login data:
How Linux store log files?
Linux (Ubuntu) stores login data into three locations:
- var/log/utmp – It contains information about users who are currently logged in
- var/log/utmw – It contains the history of all logged-in users
- var/log/btmp – It keeps all bad login attempts
All of these files stores login information and login attempts as well.
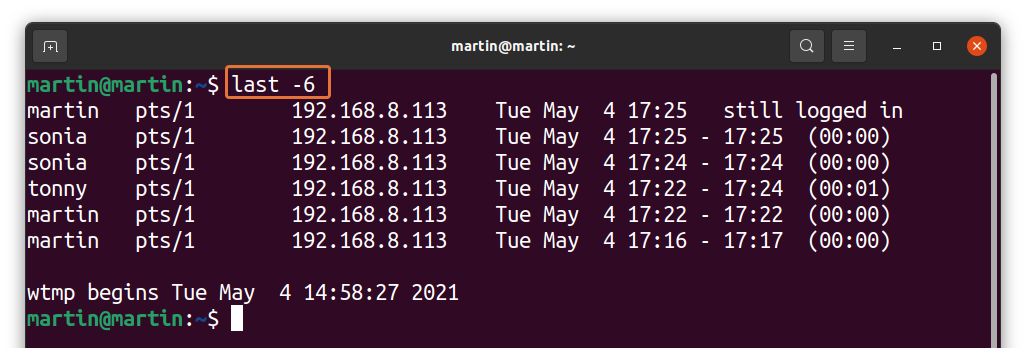
How to check the login history?
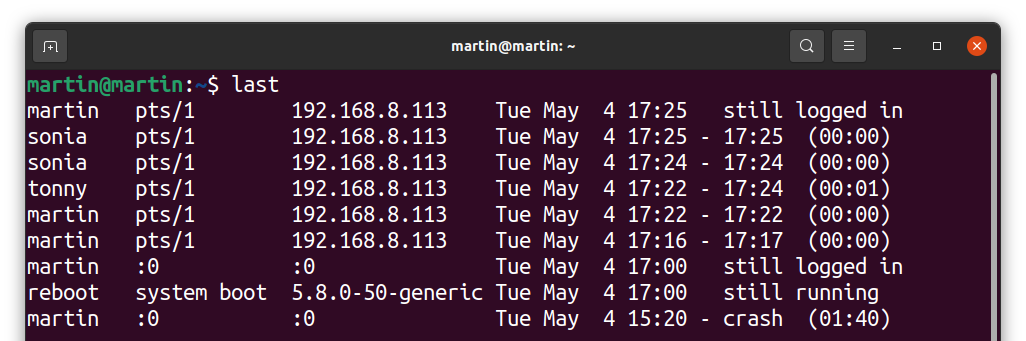
To check the login history, use the following command:
It gives information about all the users who logged in successfully. It searches through the “var/log/utmw” file and displays the history of all users who have logged in since creating the file.
The above output shows that the different users connected to the server from a machine with IP “192.168.8.113”, “pts/1” indicate that the server was accessed via SSH.
How to check the login history of a specific user?
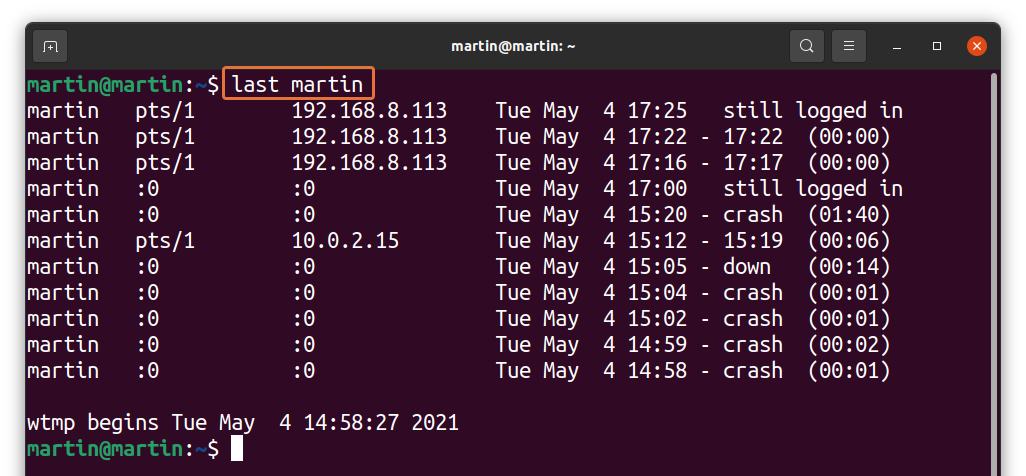
To check the login history of a specific user, uses the “last” command with the username of that particular user:
I am checking for “martin”; the command would be:
How to check the specific number of logins?
If numerous people are accessing the server, then the login history would be huge. To trim the number of logins, follow the below-mentioned syntax:
Replace “X” with the number of logins you want to display as standard output:
You can also use it with a specific username:
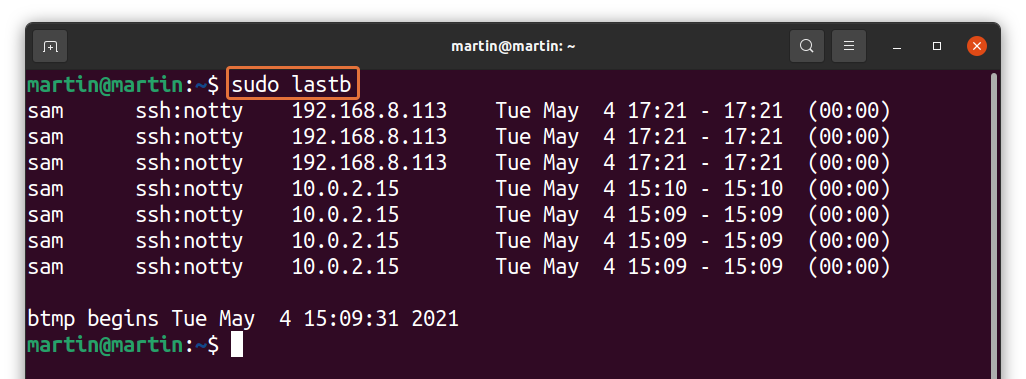
How to check bad login attempts:
As discussed above that Linux also keeps the information of bad login attempts. To display it, use the command given below:
Observing bad login attempts is very critical for security reasons of the server. You can easily identify an unknown IP address that is probably trying to access the server.
Conclusion:
Linux is the most preferred operating system for servers in many businesses because it is a secure multi-user platform. Many users access a server, and to keep a check on user activity, we need user login information. In this guide, we learned how to examine user login history in Linux. Moreover, we also analyzed how bad attempts can be tackled to secure the server. We used the “last” command, but another tool called “aureport” tracks successful and failed logins.
About the author
Sam U
I am a professional graphics designer with over 6 years of experience. Currently doing research in virtual reality, augmented reality and mixed reality.
I hardly watch movies but love to read tech related books and articles.
How do I find user login history?
So, I need to know when my account in ubuntu is accessed. Is there any command that will show me the Exact Time when that happened. I need this because I suspect someone is remotely controlling my computer, and changing things.
2 Answers 2
last command to the rescue
The last command shows by a given user name or all user names:
$ last rick rick tty7 :0 Wed Apr 24 16:25 gone - no logout rick tty8 :1 Wed Apr 24 16:24 - down (00:00) rick tty7 :0 Tue Apr 23 20:12 - down (20:06) rick tty7 :0 Tue Apr 23 18:30 - crash (01:42) (. SNIP. ) rick tty7 :0 Tue Apr 2 16:52 - down (00:31) rick tty7 :0 Tue Apr 2 03:14 - crash (13:37) By default it only shows history for the current month. If you need to go further back in history than one month, you can read the /var/log/wtmp.1 file with the last command.
last -f wtmp.1 rick will show the previous month’s history of logins for user rick :
$ last -f /var/log/wtmp.1 rick rick tty7 :0 Sun Mar 31 16:53 gone - no logout rick tty7 :0 Sat Mar 30 19:18 - down (13:20) (. SNIP. ) rick tty7 :0 Fri Mar 1 20:55 - down (11:55) wtmp.1 begins Fri Mar 1 18:23:28 2019 Security is hardened such that normal users can’t write or delete the file:
$ ll /var/log/wtmp.1 -rw-rw-r-- 1 root utmp 107520 Mar 31 16:53 /var/log/wtmp.1 Console only logins
The console uses the login command which records data to /var/log/lastlog :
$ ll /var/log/lastlog -rw-rw-r-- 1 root utmp 292292 Apr 24 16:22 /var/log/lastlog The lastlog file though cannot be tampered with so easily when you look at the File Owner and File Group above. «Normal» users just have read access. It’s a binary file though so you can’t just cat it and get meaningful information. Use this command instead:
$ lastlog Username Port From Latest root **Never logged in** daemon **Never logged in** bin **Never logged in** sys **Never logged in** (. SNIP. ) usbmux **Never logged in** rick tty1 Wed Nov 28 04:19:53 -0700 2018 vnstat **Never logged in** It’s interesting to see all the different user IDs that could log in but never have and never should. I was surprised I haven’t logged into the console / terminal since November last year.