How to find all the used IP addresses on a network
In my work there is a lot of computer and I want make a joke. I can close computer over the network but finding IP addresses is hard to me. How can I easily find all online IP adresses from 192.168.1.aa to 192.168.1.zz?
5 Answers 5
Generally, nmap is quite useful to quickly scan networks.
To install nmap, enter the following command in the terminal:
Once the application is installed, enter the following command:
This will show you which hosts responded to ping requests on the network between 192.168.1.0 and 192.168.1.255.
For older versions of Nmap, use -sP :
For additional references, see the following pages:
It is a very useful tool to learn.
If all the computers in your network are Ubuntu or any other distribution that makes use of avahi-daemon (DNS-SD), you can get a detailed list of them (with hostname and IP address) by doing:
avahi-browse -rt _workstation._tcp If you want to know all the IP addresses used in your network, you can use arp-scan :
As it is not installed by default, you’ll have to install it with sudo apt-get install arp-scan . arp-scan send ARP packets to the local network and displays the responses received, so it shows even firewalled hosts (that block traffic based on IP packets).
This command is definitely better than the one above. Running nmap took ages, but this one replied instantly with the nodes in the specified network.
In my case, very often, arp-scan doesn’t find all the devices associated to my wireless network. Now, for example, sudo arp-scan 192.168.2.0/24 shows 2 results (.1 and .1), while nmap -sn 192.168.2.0/24 shows 4 results (.1, .2, .3 and .4). So, it seems that nmap is more accurate (I know for sure that there is 4 devices attached to the network). Why is this?
Maybe I found the answer in a comment to another question. «It should be noted that some devices might not show up unless they are turned on. My nexus 4 won’t show up unless the screen is on.» However, it’s interesting that the same devices always respond to pings from nmap .
Note to the reader: Original answer has been posted a while ago and at the time of when I was only learning shell scripting. See the revisited version below for a new and improved script that performs much faster.
Original Answer
nmap would be my #1 choice, but what if you don’t have it ? The DIY way would be with a ping script that goes through each possible ip address on the network manually. What we have here is just while loop, where we set last number in the address, make silent single ping to the address, check if the command succeed or not (and if it did succeed,then host is obviously up ), and printf statement. Quick and dirty way, took me about 10 mins to write it, but runtime might be a bit slow,though.
#!/bin/sh # set -x NUM=1 while [ $NUM -lt 256 ];do ping -q -c 1 192.168.0.$NUM > /dev/null RESULT=$(echo $?) if [ $RESULT -eq 0 ]; then printf 192.168.0.$NUM"\n" fi NUM=$(expr $NUM + 1) done Revisited Answer
I originally posted this answer in August of 2015. Since then I’ve learned a bit more about shell scripting, and I once I saw this script, I thought it would be a good idea to revisit this answer to add a few improvements. Here’s a few ideas:
- The script is obviously slow and ping waits for response from the host. By default, ping for two RTT, which can vary depending on how congested is your network , and as far as I understand TCP protocol doubles the wait time each time(at least according to this). So we could force ping to time out with -w 1 flag. Since we have 256 addresses and we assume 1 second for each address, the script will take about 256/60 = 4.27 minutes.
- Doing a command and then capturing its exit status with $? wasn’t really necessary. The if . then;. fi can operate on commands directly. In other words, it’s sufficient to do this:
if ping -w 1 -q -c 1 192.168.0.$NUM > /dev/null ; then fi printf "IP %s is up\n" 192.168.0."$NUM" #!/bin/sh # Uncomment for debugging #set -x pingf() < if ping -w 2 -q -c 1 192.168.0."$1" >/dev/null ; then printf "IP %s is up\n" 192.168.0."$1" fi > main() < NUM=1 while [ $NUM -lt 255 ];do pingf "$NUM" & NUM=$(expr "$NUM" + 1) done wait >main How much better does that work ? Not bad, actually, takes a matter of seconds.
$ time ./ping_script.sh IP 192.168.0.1 is up IP 192.168.0.101 is up IP 192.168.0.27 is up IP 192.168.0.29 is up 0m02.50s real 0m00.01s user 0m00.12s system Things to Keep in Mind
- Windows ( starting since Windows 7 , I think ) have started blocking response to ICMP echo requests. There’s quite a few questions about that on Ask Ubuntu and other sites of the sort «Hey, my Linux computer can be pinged, but not Windows ones, what’s up with that ?» Just be aware of the fact that for newer Windows versions you do need to enable response to ICMP echo.
Find Out All Live Hosts IP Addresses Connected on Network in Linux
There are plenty of network monitoring tools you can find in the Linux ecosystem, that can generate for you a summary of the total number of devices on a network including all their IP addresses and more.
However, sometimes what you actually need may be a simple command line tool that can provide you the same information by running a single command.
This tutorial will explain you how to find out all live hosts IP addresses connected to a given network. Here, we will use Nmap tool to find out all IP addresses of devices connected on a same network.
The Nmap (short form for Network Mapper) is an open source, powerful and a very versatile command line tool for exploring networks, perform security scans, network audit and finding open ports on remote machine and so much more.
In case you do not have Nmap installed on your system, run the appropriate command below for your distribution to install it:
$ sudo yum install nmap [On RedHat based systems] $ sudo dnf install nmap [On Fedora 22+ versions] $ sudo apt-get install nmap [On Debian/Ubuntu based systems]
Once you have Nmap installed, the syntax for using it is:
Where the argument , can be replaced by hostnames, IP addresses, networks and so on.
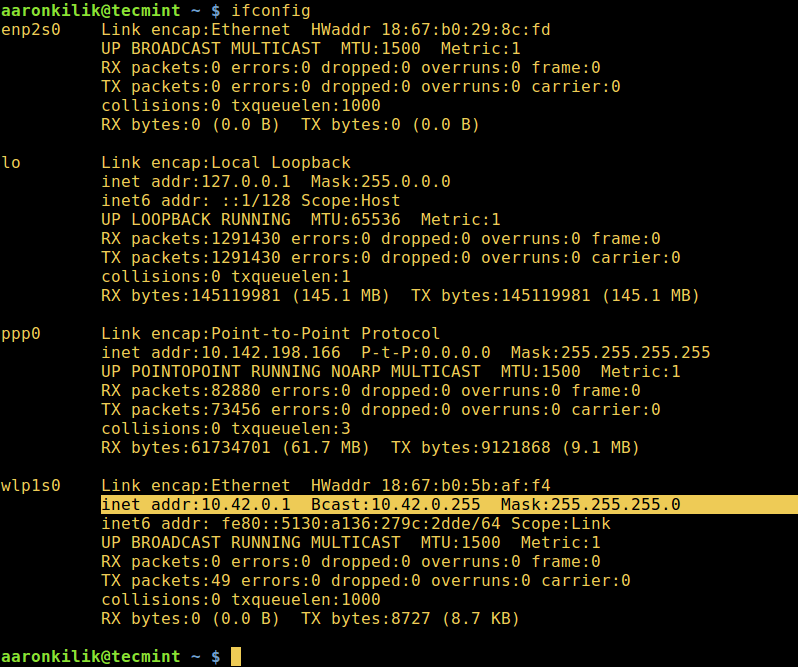
Therefore to list the IP addresses of all hosts connected to a given network, first of all identify the network and its subnet mask using the ifconfig command or ip command like so:
$ ifconfig OR $ ip addr show
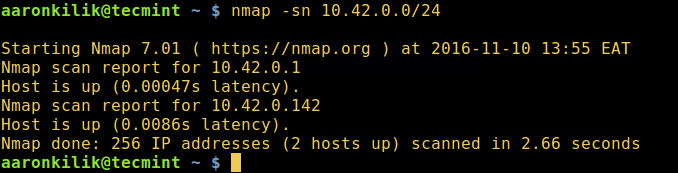
Next, run the Nmap command below:
- -sn – is the type of scan, which means a ping scan. By default, Nmap performs port scanning, but this scan will disable port scanning.
- 10.42.0.0/24 – is the target network, replace it with your actual network.
For a comprehensive usage information, make an effort to look into Nmap man page:
Else, run Nmap without any options and arguments to view a summarized usage information:
In addition, for those interested in learning security scanning techniques in Linux, you can read through this practical guide to Nmap in Kali Linux.
Well, that’s it for now, remember to send us your questions or comments through the response form below. You can as well share with us other methods for listing the IP addresses of all devices connected to a given network.
How to see incoming IPs in Linux?
I am wondering what is the command/utility to have a real-time view of incoming IPs to my server, ideally along with the port and connected.
6 Answers 6
interface: eth0 bps bps % desc 162.3 0% arp 286.5 0% llc 802.1d -> 802.1d 544.3 1% tcp 172.16.1.5:22 172.16.1.95:8074 34.0k 87% udp 172.16.1.1:514 172.16.1.5:514 350.1 0% udp 172.16.1.5:24330 209.18.47.62:53 329.4 0% udp 172.16.1.5:34870 209.18.47.62:53 388.3 0% udp 172.16.1.5:4470 209.18.47.62:53 407.4 1% udp 172.16.1.5:47008 209.18.47.62:53 741.6 1% udp 172.16.1.5:53 172.16.1.74:43289 663.6 1% udp 172.16.1.5:53 172.16.1.74:44589 647.7 1% udp 172.16.1.5:53 172.16.1.74:58223 128.9 0% udp 172.16.1.74:5353 224.0.0.251:5353 160.7 0% udp6 fe80::21c:bfff:fecf:a798,5353 ff02::fb,5353 The pktstat source code is hosted on Debian’s site, or you can get it from SourceArchive.com
Amazing. Exactly what I was looking for. It is quite obvious but to complete the answer you might want to add that it can be installed simply by ‘apt-get install pkstat’.
Also, if you get pktstat: pcap_lookupdev: no suitable device found when running this, you might need to be root.
For ‘purdy’ display, I’m partial to a tool called ‘iptraf’ that will do just what you mention, as well as per interface, and per port aggregates.
For core Linux tools, trusty netstat will do the trick.
IPtraf is the best tool I’ve seen in terms of usability and functionality — obviously you can still script some stuff using standard tools like netstat and ngrep and tcpdump but why would you want to reinvent the wheel 🙂
For completeness, iftop is similar to iptraf — an ncurses based app that uses bar graphs rather than just numbers — to display bandwidth usage per IP address. With the -P option you can get it per port as well.
Here is how to see all traffic coming to port 2222:
A tcpdump would show you that; if you just wanted a list of IPs, you could filter on SYN packets and only output the source IP address. Something like:
tcpdump -i eth0 -n 'tcp[tcpflags] & tcp-syn != 0 and not src and dst net localnet' | sed 's/^.*IP \([^ ]*) >.*$/\1/' Would get you the list of IPs, in realtime. You could also tee that to a file, and periodically do a sort -u on it to get a list of unique IP addresses that have sent connections your way.
You can use last to get an idea where your connections are coming from:
The results, now in chronological order look like this:
root pts/0 xx.yy.zz.1 Fri Jan 31 09:13 - 13:25 (04:11) root pts/1 master01-server.ne Fri Jan 31 09:36 still logged in root pts/2 xx.yy.zz.1 Fri Jan 31 10:29 - 14:41 (04:11) root pts/3 master01-server.ne Fri Jan 31 10:33 - 18:31 (07:58) root pts/4 master01-server.ne Fri Jan 31 13:04 - 18:32 (05:28) root pts/0 xx.yy.zz.1 Fri Jan 31 13:41 - 16:33 (02:52) root pts/0 master01-server.ne Mon Feb 3 08:37 still logged in If you want more details, and your sysadmin no longer allows netstat , use ss :
ss | grep xx.zx.yz.161 tcp ESTAB 0 0 nnn.mm.oo.6:ssh xx.zx.yz.161:49046 tcp ESTAB 0 0 nnn.mm.oo.6:ssh xx.zx.yz.161:54800