- Unix / Linux — System Logging
- Syslog Facilities
- Syslog Priorities
- The /etc/syslog.conf file
- Logging Actions
- The logger Command
- Log Rotation
- Important Log Locations
- Classic SysAdmin: Viewing Linux Logs from the Command Line
- /var/log
- Viewing logs with less
- Viewing logs with dmesg
- Viewing logs with tail
- There are other tools
Unix / Linux — System Logging
In this chapter, we will discuss in detail about system logging in Unix.
Unix systems have a very flexible and powerful logging system, which enables you to record almost anything you can imagine and then manipulate the logs to retrieve the information you require.
Many versions of Unix provide a general-purpose logging facility called syslog. Individual programs that need to have information logged, send the information to syslog.
Unix syslog is a host-configurable, uniform system logging facility. The system uses a centralized system logging process that runs the program /etc/syslogd or /etc/syslog.
The operation of the system logger is quite straightforward. Programs send their log entries to syslogd, which consults the configuration file /etc/syslogd.conf or /etc/syslog and, when a match is found, writes the log message to the desired log file.
There are four basic syslog terms that you should understand −
The identifier used to describe the application or process that submitted the log message. For example, mail, kernel, and ftp.
An indicator of the importance of the message. Levels are defined within syslog as guidelines, from debugging information to critical events.
A combination of one or more facilities and levels. When an incoming event matches a selector, an action is performed.
What happens to an incoming message that matches a selector — Actions can write the message to a log file, echo the message to a console or other device, write the message to a logged in user, or send the message along to another syslog server.
Syslog Facilities
We will now understand about the syslog facilities. Here are the available facilities for the selector. Not all facilities are present on all versions of Unix.
Activity related to requesting name and password (getty, su, login)
Same as auth but logged to a file that can only be read by selected users
Used to capture messages that are generally directed to the system console
Messages from the cron system scheduler
Messages relating to the ftp daemon
Local facilities defined per site
Messages from the line printing system
Messages relating to the mail system
Pseudo-event used to generate timestamps in log files
Messages relating to network news protocol (nntp)
Messages relating to network time protocol
Syslog Priorities
The syslog priorities are summarized in the following table −
Emergency condition, such as an imminent system crash, usually broadcast to all users
Condition that should be corrected immediately, such as a corrupted system database
Critical condition, such as a hardware error
Condition that is not an error, but possibly should be handled in a special way
Messages that are used when debugging programs
Pseudo level used to specify not to log messages
The combination of facilities and levels enables you to be discerning about what is logged and where that information goes.
As each program sends its messages dutifully to the system logger, the logger makes decisions on what to keep track of and what to discard based on the levels defined in the selector.
When you specify a level, the system will keep track of everything at that level and higher.
The /etc/syslog.conf file
The /etc/syslog.conf file controls where messages are logged. A typical syslog.conf file might look like this −
*.err;kern.debug;auth.notice /dev/console daemon,auth.notice /var/log/messages lpr.info /var/log/lpr.log mail.* /var/log/mail.log ftp.* /var/log/ftp.log auth.* @prep.ai.mit.edu auth.* root,amrood netinfo.err /var/log/netinfo.log install.* /var/log/install.log *.emerg * *.alert |program_name mark.* /dev/console
Each line of the file contains two parts −
- A message selector that specifies which kind of messages to log. For example, all error messages or all debugging messages from the kernel.
- An action field that says what should be done with the message. For example, put it in a file or send the message to a user’s terminal.
Following are the notable points for the above configuration −
- Message selectors have two parts: a facility and a priority. For example, kern.debug selects all debug messages (the priority) generated by the kernel (the facility).
- Message selector kern.debug selects all priorities that are greater than debug.
- An asterisk in place of either the facility or the priority indicates «all». For example, *.debug means all debug messages, while kern.* means all messages generated by the kernel.
- You can also use commas to specify multiple facilities. Two or more selectors can be grouped together by using a semicolon.
Logging Actions
The action field specifies one of five actions −
- Log message to a file or a device. For example, /var/log/lpr.log or /dev/console.
- Send a message to a user. You can specify multiple usernames by separating them with commas; for example, root, amrood.
- Send a message to all users. In this case, the action field consists of an asterisk; for example, *.
- Pipe the message to a program. In this case, the program is specified after the Unix pipe symbol (|).
- Send the message to the syslog on another host. In this case, the action field consists of a hostname, preceded by an at sign; for example, @tutorialspoint.com.
The logger Command
Unix provides the logger command, which is an extremely useful command to deal with system logging. The logger command sends logging messages to the syslogd daemon, and consequently provokes system logging.
This means we can check from the command line at any time the syslogd daemon and its configuration. The logger command provides a method for adding one-line entries to the system log file from the command line.
The format of the command is −
logger [-i] [-f file] [-p priority] [-t tag] [message].
Here is the detail of the parameters −
Uses the contents of file filename as the message to log.
Logs the process ID of the logger process with each line.
Enters the message with the specified priority (specified selector entry); the message priority can be specified numerically, or as a facility.priority pair. The default priority is user.notice.
Marks each line added to the log with the specified tag.
The string arguments whose contents are concatenated together in the specified order, separated by the space.
You can use Manpage Help to check complete syntax for this command.
Log Rotation
Log files have the propensity to grow very fast and consume large amounts of disk space. To enable log rotations, most distributions use tools such as newsyslog or logrotate.
These tools should be called on a frequent time interval using the cron daemon. Check the man pages for newsyslog or logrotate for more details.
Important Log Locations
All the system applications create their log files in /var/log and its sub-directories. Here are few important applications and their corresponding log directories −
| Application | Directory |
|---|---|
| httpd | /var/log/httpd |
| samba | /var/log/samba |
| cron | /var/log/ |
| /var/log/ | |
| mysql | /var/log/ |
Classic SysAdmin: Viewing Linux Logs from the Command Line
This is a classic article written by Jack Wallen from the Linux.com archives. For more great SysAdmin tips and techniques check out our free intro to Linux course.
At some point in your career as a Linux administrator, you are going to have to view log files. After all, they are there for one very important reason…to help you troubleshoot an issue. In fact, every seasoned administrator will immediately tell you that the first thing to be done, when a problem arises, is to view the logs.
And there are plenty of logs to be found: logs for the system, logs for the kernel, for package managers, for Xorg, for the boot process, for Apache, for MySQL… For nearly anything you can think of, there is a log file.
Most log files can be found in one convenient location: /var/log. These are all system and service logs, those which you will lean on heavily when there is an issue with your operating system or one of the major services. For desktop app-specific issues, log files will be written to different locations (e.g., Thunderbird writes crash reports to ‘~/.thunderbird/Crash Reports’). Where a desktop application will write logs will depend upon the developer and if the app allows for custom log configuration.
We are going to be focus on system logs, as that is where the heart of Linux troubleshooting lies. And the key issue here is, how do you view those log files?
Fortunately there are numerous ways in which you can view your system logs, all quite simply executed from the command line.
/var/log
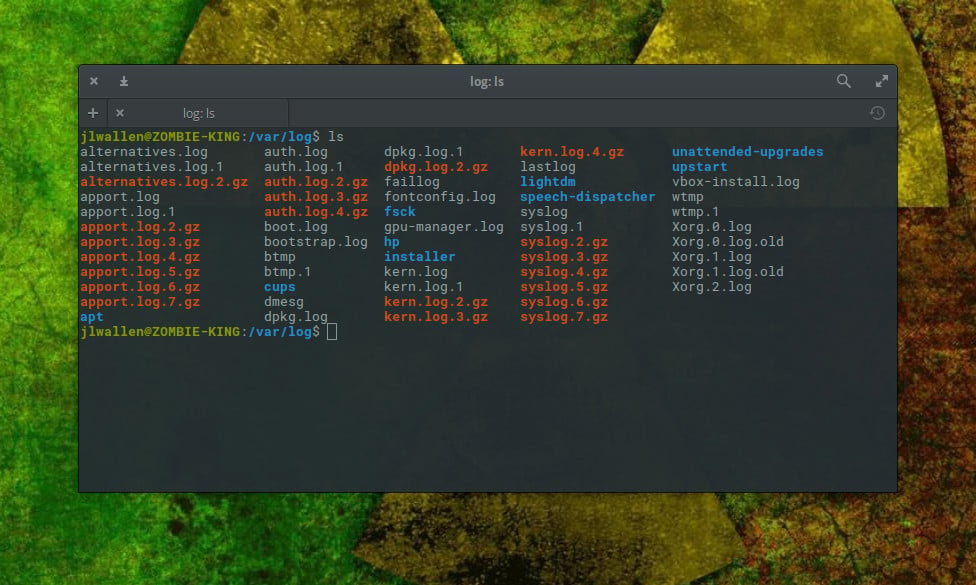
This is such a crucial folder on your Linux systems. Open up a terminal window and issue the command cd /var/log. Now issue the command ls and you will see the logs housed within this directory (Figure 1).
Now, let’s take a peek into one of those logs.
Viewing logs with less
One of the most important logs contained within /var/log is syslog. This particular log file logs everything except auth-related messages. Say you want to view the contents of that particular log file. To do that, you could quickly issue the command less /var/log/syslog. This command will open the syslog log file to the top. You can then use the arrow keys to scroll down one line at a time, the spacebar to scroll down one page at a time, or the mouse wheel to easily scroll through the file.
The one problem with this method is that syslog can grow fairly large; and, considering what you’re looking for will most likely be at or near the bottom, you might not want to spend the time scrolling line or page at a time to reach that end. Will syslog open in the less command, you could also hit the [Shift]+[g] combination to immediately go to the end of the log file. The end will be denoted by (END). You can then scroll up with the arrow keys or the scroll wheel to find exactly what you want.
This, of course, isn’t terribly efficient.
Viewing logs with dmesg
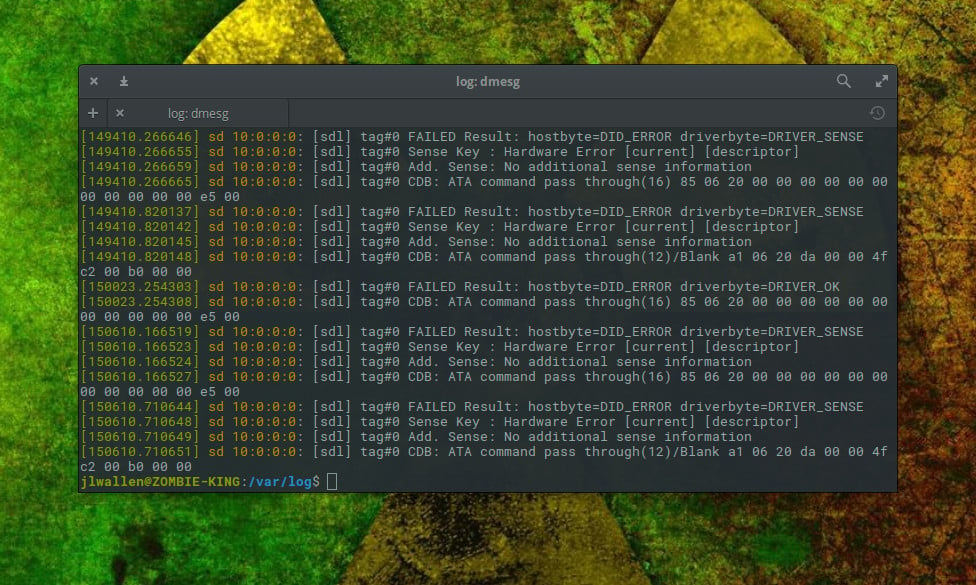
The dmesg command prints the kernel ring buffer. By default, the command will display all messages from the kernel ring buffer. From the terminal window, issue the command dmesg and the entire kernel ring buffer will print out (Figure 2).
Fortunately, there is a built-in control mechanism that allows you to print out only certain facilities (such as daemon).
Say you want to view log entries for the user facility. To do this, issue the command dmesg –facility=user. If anything has been logged to that facility, it will print out.
Unlike the less command, issuing dmesg will display the full contents of the log and send you to the end of the file. You can always use your scroll wheel to browse through the buffer of your terminal window (if applicable). Instead, you’ll want to pipe the output of dmesg to the less command like so:
The above command will print out the contents of dmesg and allow you to scroll through the output just as you did viewing a standard log with the less command.
Viewing logs with tail
The tail command is probably one of the single most handy tools you have at your disposal for the viewing of log files. What tail does is output the last part of files. So, if you issue the command tail /var/log/syslog, it will print out only the last few lines of the syslog file.
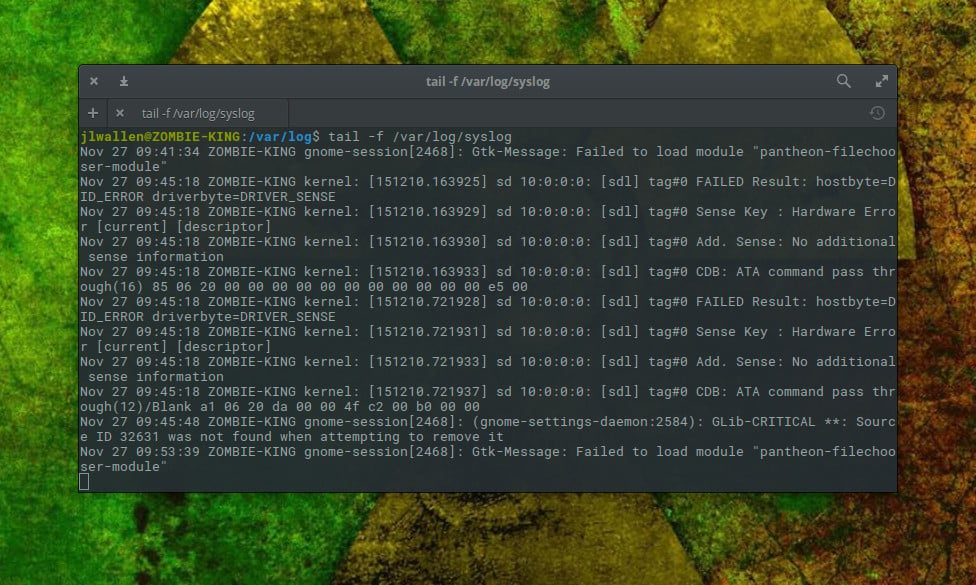
But wait, the fun doesn’t end there. The tail command has a very important trick up its sleeve, by way of the -f option. When you issue the command tail -f /var/log/syslog, tail will continue watching the log file and print out the next line written to the file. This means you can follow what is written to syslog, as it happens, within your terminal window (Figure 3).
Using tail in this manner is invaluable for troubleshooting issues.
To escape the tail command (when following a file), hit the [Ctrl]+[x] combination.
You can also instruct tail to only follow a specific amount of lines. Say you only want to view the last five lines written to syslog; for that you could issue the command:
The above command would follow input to syslog and only print out the most recent five lines. As soon as a new line is written to syslog, it would remove the oldest from the top. This is a great way to make the process of following a log file even easier. I strongly recommend not using this to view anything less than four or five lines, as you’ll wind up getting input cut off and won’t get the full details of the entry.
There are other tools
You’ll find plenty of other commands (and even a few decent GUI tools) to enable the viewing of log files. Look to more, grep, head, cat, multitail, and System Log Viewer to aid you in your quest to troubleshooting systems via log files.
Advance your career with Linux system administration skills. Check out the Essentials of System Administration course from The Linux Foundation.