- How to ssh to localhost without password?
- Configure SSH for login without a password
- Background
- What do you need
- What is an SSH key pair?
- Generate an SSH key pair
- Register the private SSH key on your PC
- Copy the public SSH key to the server
- Login via SSH without using a password
- Further SSH security hardening
- Wrap up
- PragmaticLinux
- how to SSH Login Without Password [closed]
- 4 Answers 4
How to ssh to localhost without password?
EDIT: Putting exactly what was done I need to SSH localhost without password, the usual way of doing it (with public keys) do not work.
user@PC:~$ rm -rf .ssh/* user@PC:~$ ssh-keygen -t rsa > /dev/null Enter file in which to save the key (/home/user/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: user@PC:~$ ls .ssh/ id_rsa id_rsa.pub user@PC:~$ ssh-copy-id -i localhost The authenticity of host 'localhost (::1)' can't be established. RSA key fingerprint is f7:87:b5:4e:31:a1:72:11:8e:5f:d2:61:bd:b3:40:1a. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'localhost' (RSA) to the list of known hosts. user@localhost's password: Now try logging into the machine, with "ssh 'localhost'", and check in: .ssh/authorized_keys to make sure we haven't added extra keys that you weren't expecting. user@PC:~$ ssh-agent $SHELL user@PC:~$ ssh-add -L The agent has no identities. user@PC:~$ ssh-add Identity added: /home/user/.ssh/id_rsa (/home/user/.ssh/id_rsa) user@PC:~$ ssh-add -L ssh-rsa . MY KEY HERE user@PC:~$ ssh-copy-id -i localhost user@localhost's password: Now try logging into the machine, with "ssh 'localhost'", and check in: .ssh/authorized_keys to make sure we haven't added extra keys that you weren't expecting. user@PC:~$ ssh localhost echo 'testing' user@localhost's password: user@PC:~$ So as you can see in the last command it is still asking the password! How can I fix that? Ubuntu-10.04, OpenSSH_5.3p1 EDIT2: Adding some info about the sshd
user@PC:~$ cat /etc/ssh/sshd_config | grep Authentication # Authentication: RSAAuthentication yes PubkeyAuthentication yes RhostsRSAAuthentication no HostbasedAuthentication no # Uncomment if you don't trust ~/.ssh/known_hosts for RhostsRSAAuthentication ChallengeResponseAuthentication no # PasswordAuthentication yes $ssh -vv localhost . debug1: Authentications that can continue: publickey,password debug1: Next authentication method: publickey debug1: Trying private key: /home/user/.ssh/identity debug1: Offering public key: /home/user/.ssh/id_rsa debug2: we sent a publickey packet, wait for reply debug1: Authentications that can continue: publickey,password debug1: Trying private key: /home/user/.ssh/id_dsa debug2: we did not send a packet, disable method debug1: Next authentication method: password user@localhost's password: Configure SSH for login without a password
Looking for a way to login to your Linux server via SSH without specifying a password? Using an SSH key pair is the way to go then. If done properly, this results in more convenience for you and more security for your server. In this article you’ll learn step-by-step how to setup an SSH key pair for logging into your server via SSH, without having to enter a password.
Background
SSH stands for Secure Shell Protocol. SSH makes it possible for you to open up a remote terminal session on your server. More importantly, it does so while using a cryptographic based communication protocol. This means that all communication between your PC and your server is secure, even over an unsecured network. Consequently, SSH is the ideal method for remotely administering a Linux server.
After you setup Linux on your server, the installer probably already installed the OpenSSH server software. With OpenSSH running on your server, you can login to your server with the ssh program, using command syntax:
Replace [USERNAME] with the username of your user account on the server. Next, replace [HOST] with its IP-address, hostname or fully qualified domain name. The -p [PORT] part can be left out, if you use the default port 22, otherwise replace [PORT] with the SSH port you configured on the server. Example:
- ssh [email protected]
After running the ssh command to remotely login to your server, you need to enter your password in order to establish the connection. This makes sense, yet also poses a security threat. Especially with an Internet facing server, someone will figure out its IP address and try to login via SSH by guessing a username and password combination. With enough persistence and patience, they might eventually succeed.
What if I told you that it’s possible to login via SSH without a password and at the same time close this security threat? So increased convenience for you and increased security for your server. The trick is to use an SSH key pair, instead of a password. In this article I’ll explain how you can configure SSH to login with the help of an SSH key pair.
What do you need
This article assumes you already run a Linux server somewhere with:
- A user account setup that has sudo access.
- OpenSSH running such that you can remotely login via SSH.
The server can be a VirtualBox virtual machine, a cloud server or even a Raspberry PI. In case you quickly want to setup such a server, follow the instructions in one of these tutorials:
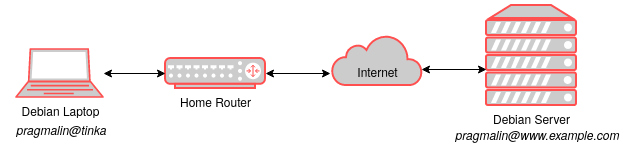
My system setup for this article consists of my Debian laptop ( tinka ) and a Debian server with www.example.com as the fully qualified domain name:
What is an SSH key pair?
An SSH key pair essentially consist of two files that belong together. One is called the public key and the other one the private key. This key pair forms a unique combination, with its contents based on hard to crack cryptography. Think of the SSH key pair as a key and lock system, as illustrated in the following image:
Others might find your server, but only you have the SSH private key on your PC. Therefore, only you can unlock access to your server via SSH. As the name implies: do not share the private key with anyone else.
Generate an SSH key pair
Now that we know what an SSH key pair is, it’s time for the next step for making it possible to login via SSH without a password. This step involves the actual creation of the SSH key pair. So afterwards we should end up with two files:
- The private SSH key file, which we later on register on our own PC.
- The public SSH key file, which we later on store on our server.
On a Linux system, you can find SSH keys in the .ssh directory of your home folder. Before we generate the SSH key pair, we first make sure that this directory exists and set it as the current directory:
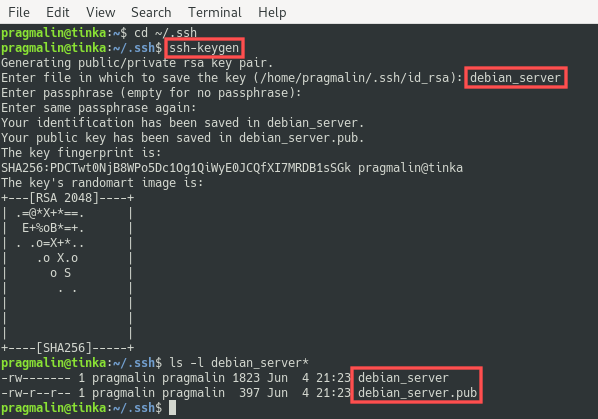
From the .ssh directory, start the SSH key pair creation process by entering command:
The program prompts you to enter a file name for the key pair. In this example I specify debian_server as the name, but you can change this to whatever name you prefer. Next, the program prompts you for a passphrase. This is a text string of your choice that you would need to enter each time you use the key for authentication purposes. For convenience you can leave the passphrase empty by simple pressing Enter twice. You now have a brand spanking new SSH key pair. The private key file is called debian_server and the public key file is called debian_server.pub :
Register the private SSH key on your PC
With the SSH key pair in place, we are one step closer to setting things up for logging into SSH without a password. The next step involves registering the private SSH key file on our PC. Think of it as attaching the new key to your key-chain.
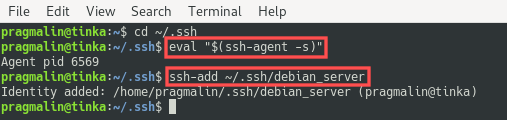
Before registering the private SSH key file, open the terminal and verify that the SSH authentication agent is actually running. Next, register the private SSH key file with the help of the ssh-add program:
Setup of the private SSH key file on your own PC is now done. Note that if you ever need to unregister the private SSH key file from the authentication agent, you can do so with the same command and specifying the -D option: ssh-add -D ~/.ssh/debian_server .
Copy the public SSH key to the server
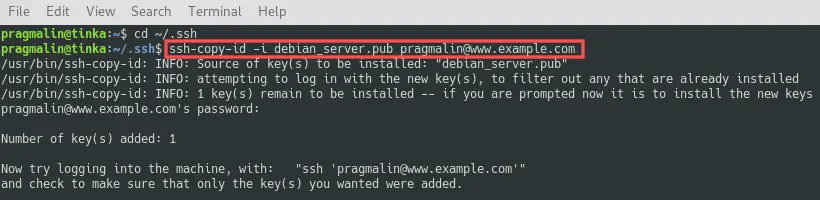
You only need to complete one more step, before you can login to your server over SSH, without specifying a password. This step involves copying the public SSH key file over to your server. Think of it as installing the lock on your server.
The program ssh-copy-id assists with this step. Assuming that your working directory is set to ~/.ssh , the command syntax is:
- ssh-copy-id -i debian_server.pub [email protected]
This adds the public SSH key file to ~/.ssh/authorizedkeys on your server.
Login via SSH without using a password
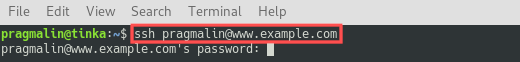
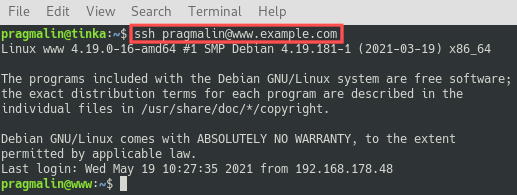
At this point we prepared everything and it should be possible to login our server via SSH, without entering a password. Let’s give it a try. You can use the usual command for connecting to the server via SSH, so
For my server the command is:
- ssh [email protected]
As you can see in the screenshot, I was able to login via SSH without being prompted for a password. This proves that the new SSH key pair works.
Further SSH security hardening
In the previous steps, we managed to setup an SSH key pair, which enables us to login to our server without specifying a password. We can further improve the server’s security by:
- Disabling the root user from logging in.
- Completely disabling password authentication, since we don’t need it anymore.
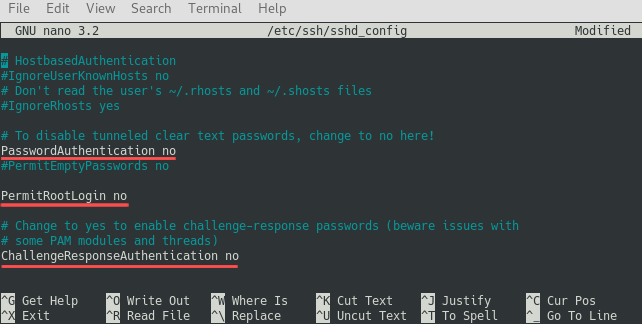
To proceed with these steps, connect to your server via SSH and edit file /etc/ssh/sshd_config , for example using the Nano terminal editor:
Next, make sure that the following variables are set to no :
- PermitRootLogin
- PasswordAuthentication
- ChallengeResponseAuthentication
Next, save the changes to the file and exit the Nano editor. As a final step, restart the SSH server to activate the new configuration settings:
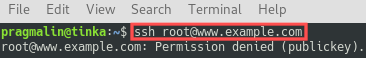
That’s it. It is now impossible for the root user to login via SSH. All other users can login, but only with an SSH key pair. No longer with a username and password. Here’s what happens if someone tries to login as the root user now:
Wrap up
This article explained step-by-step how you can configure the SSH connection with your server, such that you can login without a password. We achieved this with the help of an SSH key pair. Not only does this give you more convenience, but also more security. We completed the following steps:
- Generated the SSH key pair.
- Registered the private SSH key on your PC.
- Copied the public SSH key to the server.
Now that the SSH login without a password works, we performed some extra SSH security hardening on your server by disabling password authentication altogether. While we were at it, we disabled the root user from logging in as well.
With these measures in place, you no longer have to worry about unwanted third parties gaining access to your server via SSH. They will still try though. To further discourage them from such SSH brute force attacks, you could consider installing Fail2ban.
PragmaticLinux
Long term Linux enthusiast, open source software developer and technical writer.
how to SSH Login Without Password [closed]
Closed. This question does not meet Stack Overflow guidelines. It is not currently accepting answers.
This question does not appear to be about a specific programming problem, a software algorithm, or software tools primarily used by programmers. If you believe the question would be on-topic on another Stack Exchange site, you can leave a comment to explain where the question may be able to be answered.
To use sftp in a script without user interaction (non-interactive). For example to login to an anonymous ftp server and not have to manually.
Do you have access to your server?, because you will need to edit the configuration file. So it will allow Anonymous connections. Correct me if i am wrong. Hope this helps. Wesley.
4 Answers 4
On your computer
press the enter key at every prompt
Generating public/private dsa key pair. Enter file in which to save the key (/home/user/.ssh/id_dsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/user/.ssh/id_dsa. Your public key has been saved in /home/user/.ssh/id_dsa.pub. The key fingerprint is: ad:98:43:13:c9:ea:66:8e:d0:d9:66:59:d8:3a:f7:29 The key's randomart image is: +--[ DSA 1024]----+ | | | . . | | + | | + . . | | o = S . | | . + = + . | |. o @ = . | | . B oEo . | | . . .o | +-----------------+ you will get 2 files id_dsa and id_dsa.pub use scp or other utility to copy file to your server
scp ~/.ssh/id_dsa.pub user@host:~/.ssh/ On your server
Add the new key to the file ~/.ssh/authorized_keys.
cat ~/.ssh/id_dsa.pub >> ~/.ssh/authorized_keys Finally change the access modes;
chmod 600 ~/.ssh/authorized_keys chmod 700 ~/.ssh Verify that access mode is correct for ~
to correct your home access.