Linux Mint Forums
Forum rules
Before you post please read how to get help. Topics in this forum are automatically closed 6 months after creation.
how do I login as a windows domain user?
Post by wddossett » Fri Oct 12, 2018 2:37 pm
Hey, I’m on mint 19 tara brand new install. I’ve added it to my Windows AD domain and from a terminal window I can login as a domain user and modified pam so it creates the home dir. But I can’t do this on my cinnamon desktop UI. It only allows me to login as the user I created during the install. I saw an old post about linking mdm to gdm I think, but that doesn’t seem to help either. I get a switch user, but won’t let me just type a name in to login as. I’m pretty new to mint yet — I usually use centos and no desktop, but i have a fair number of users that would like to try mint, but I want them to login with their domain id with no pre-setup by myself other than an ansible job that joins the domain so they can authenticate using their AD creds. Thanks for any pointers anyone can offer.
Last edited by LockBot on Wed Dec 28, 2022 7:16 am, edited 1 time in total.
Reason: Topic automatically closed 6 months after creation. New replies are no longer allowed.
Re: how do I login as a windows domain user?
Post by wddossett » Fri Oct 12, 2018 3:52 pm
ah found it in the desktop anyway, Login Window -> allow manual login. Any idea how to change that from the terminal so I can do this using a configuration tool? Searching but may take a while to find the setting I need .
Linux Mint Forums
Forum rules
Before you post please read how to get help. Topics in this forum are automatically closed 6 months after creation.
luca72 Level 2
Posts: 97 Joined: Sat Apr 17, 2021 3:10 pm Location: Milano, Italy
How connect to windows domain?
Post by luca72 » Sat May 08, 2021 7:13 pm
hello everyone, sorry for the ignorance, but I have been using linux for only a month.
where are the settings to connect to a company windows domain?
what services do you need to add, which are not there by default, on a windows server, to make it talk to linux mint, and manage the user accounts?
System: Kernel: 5.8.0-50-generic x86_64 bits: 64 compiler: N/A Desktop: Cinnamon 4.8.6 wm: muffin dm: LightDM Distro: Linux Mint 20.1 Ulyssa base: Ubuntu 20.04 focal Machine: Type: Laptop System: HP product: HP Laptop 15-dw0xxx v: Type1ProductConfigId serial: Chassis: type: 10 serial: Mobo: HP model: 85F0 v: 36.41 serial: UEFI: Insyde v: F.43 date: 03/31/2021 Battery: ID-1: BAT1 charge: 11.9 Wh condition: 11.9/41.0 Wh (29%) volts: 12.9/11.4 model: Hewlett-Packard PABAS0241231 serial: status: Full CPU: Topology: Quad Core model: Intel Core i7-8565U bits: 64 type: MT MCP arch: Kaby Lake rev: B L2 cache: 8192 KiB flags: avx avx2 lm nx pae sse sse2 sse3 sse4_1 sse4_2 ssse3 vmx bogomips: 31999 Speed: 800 MHz min/max: 400/4600 MHz Core speeds (MHz): 1: 800 2: 800 3: 800 4: 800 5: 800 6: 800 7: 800 8: 800 Graphics: Device-1: Intel UHD Graphics 620 vendor: Hewlett-Packard driver: i915 v: kernel bus ID: 00:02.0 chip ID: 8086:3ea0 Device-2: NVIDIA GM108M [GeForce MX130] driver: nvidia v: 460.73.01 bus ID: 01:00.0 chip ID: 10de:174d Display: x11 server: X.Org 1.20.9 driver: modesetting,nvidia unloaded: fbdev,nouveau,vesa tty: N/A OpenGL: renderer: GeForce MX130/PCIe/SSE2 v: 4.6.0 NVIDIA 460.73.01 direct render: Yes Audio: Device-1: Intel Cannon Point-LP High Definition Audio vendor: Hewlett-Packard driver: snd_hda_intel v: kernel bus ID: 00:1f.3 chip ID: 8086:9dc8 Sound Server: ALSA v: k5.8.0-50-generic Network: Device-1: Realtek RTL8111/8168/8411 PCI Express Gigabit Ethernet vendor: Hewlett-Packard driver: r8169 v: kernel port: 4000 bus ID: 02:00.0 chip ID: 10ec:8168 IF: eno1 state: down mac: Device-2: Realtek RTL8821CE 802.11ac PCIe Wireless Network Adapter vendor: Hewlett-Packard driver: rtl8821ce v: v5.5.2.1_35598.20191029 port: 3000 bus ID: 03:00.0 chip ID: 10ec:c821 IF: wlo1 state: up mac: IF-ID-1: vboxnet0 state: down mac: Drives: Local Storage: total: 476.94 GiB used: 108.95 GiB (22.8%) ID-1: /dev/nvme0n1 vendor: Western Digital model: PC SN520 SDAPNUW-512G-1006 size: 476.94 GiB speed: 15.8 Gb/s lanes: 2 serial: RAID: Hardware-1: Intel 82801 Mobile SATA Controller [RAID mode] driver: ahci v: 3.0 bus ID: 00:17.0 chip ID: 8086.282a Partition: ID-1: / size: 169.88 GiB used: 108.88 GiB (64.1%) fs: ext4 dev: /dev/nvme0n1p5 Sensors: System Temperatures: cpu: 45.0 C mobo: 29.8 C gpu: nvidia temp: 42 C Fan Speeds (RPM): N/A Repos: No active apt repos in: /etc/apt/sources.list Active apt repos in: /etc/apt/sources.list.d/mkusb-ppa-focal.list 1: deb http: //ppa.launchpad.net/mkusb/ppa/ubuntu focal main Active apt repos in: /etc/apt/sources.list.d/official-package-repositories.list 1: deb http: //packages.linuxmint.com ulyssa main upstream import backport 2: deb http: //archive.ubuntu.com/ubuntu focal main restricted universe multiverse 3: deb http: //archive.ubuntu.com/ubuntu focal-updates main restricted universe multiverse 4: deb http: //archive.ubuntu.com/ubuntu focal-backports main restricted universe multiverse 5: deb http: //security.ubuntu.com/ubuntu/ focal-security main restricted universe multiverse 6: deb http: //archive.canonical.com/ubuntu/ focal partner Info: Processes: 251 Uptime: 23m Memory: 7.66 GiB used: 2.46 GiB (32.1%) Init: systemd v: 245 runlevel: 5 Compilers: gcc: 9.3.0 alt: 9 Client: Unknown python3.8 client inxi: 3.0.38 Last edited by LockBot on Wed Dec 28, 2022 7:16 am, edited 1 time in total.
Reason: Topic automatically closed 6 months after creation. New replies are no longer allowed.
Integrate Linux Mint 19.1 to Windows Server 2019 Active Directory Domain Controller
This tutorial will describe how you can join machines that run Linux Mint 17.1 OS to Windows 2012 Active Directory Domain Controller in order to authenticate remote accounts from AD back end identity provider to local Linux workstations with the help of SSSD service and Realmd system DBus service.
The System Security Services Daemon (SSSD) is a relative new service which provides cross-domain compatible methods for Active Directory users to authenticate to local machines using a combination of usernames and domain back end name to create the login identity, even if the Domain Controller goes offline (SSSD caches credentials).
REQUIREMENTS
- Windows Server 2012 configured as an Active Directory Domain Controller
- A Linux Mint 17.1 client machine which will be integrated to Windows PDC
Domain Settings:
- Domain Name: caezsar.lan
- Windows Server 2012 AD FQDN: server.caezsar.lan
- Windows Server 2012 AD IP Address: 192.168.1.130
- Linux Mint Hostname: mint-desktop
- Linux Mint IP Address: automatically assigned by DHCP
- Linux Mint first DNS IP Address: Manually assigned to point to AD PDC – 192.168.1.130
STEP ONE – Linux Mint Network Configuration
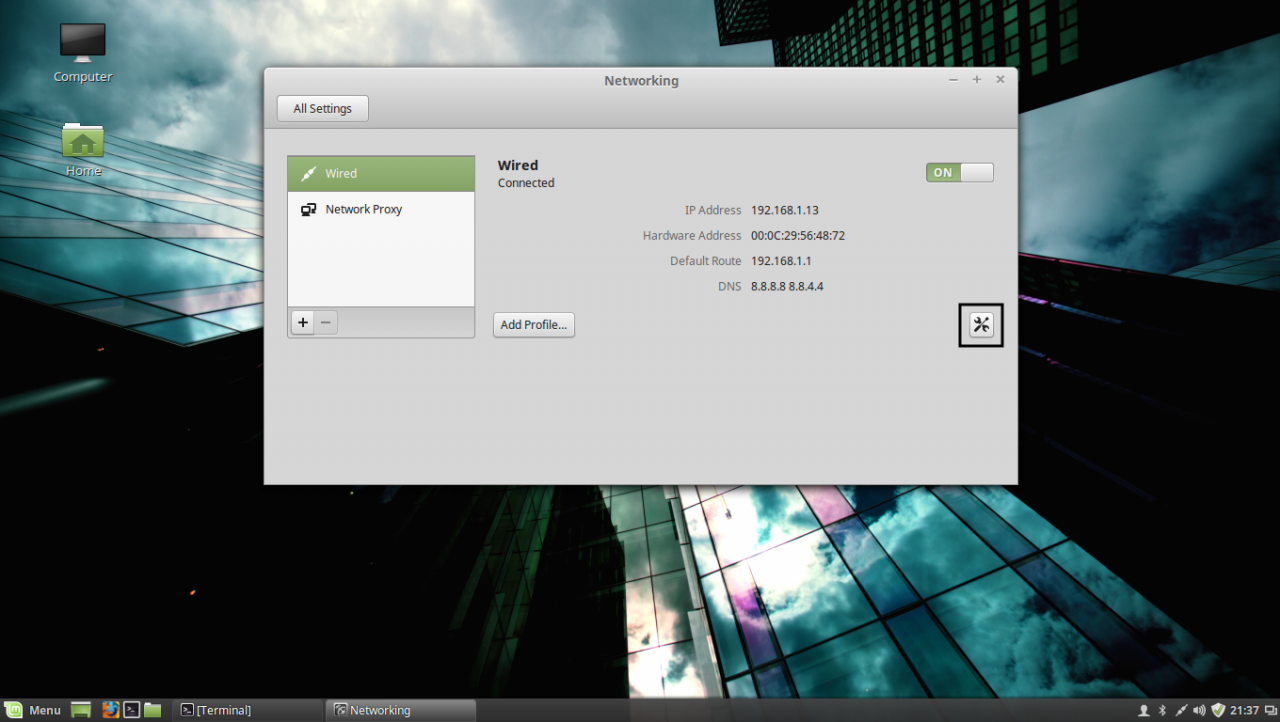
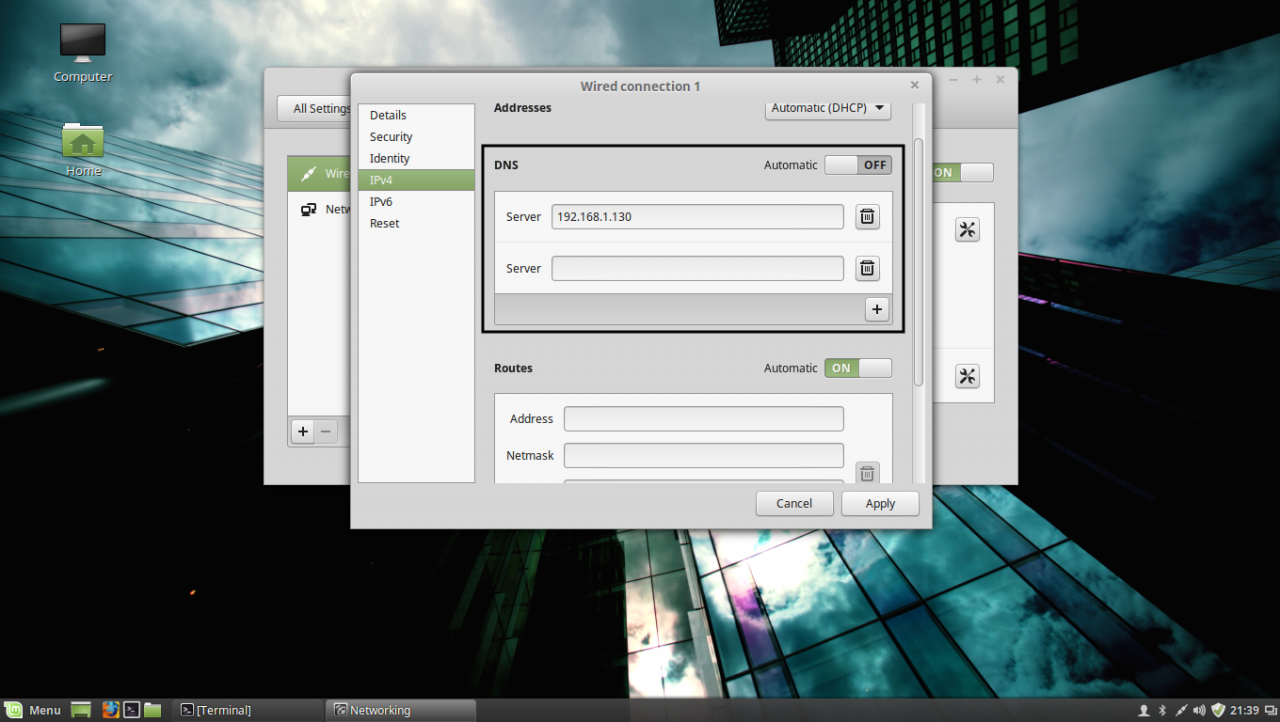
1. Before starting with installing the required services in order to integrate the local machine to the PDC Server, first we need to assure that Windows Domain Controller is reachable through DNS resolution on Linux Mint host by adding the DNS PDC IP Address on our Network Configuration. To achieve this goal, first open Network Settings , go to the Network Interface Card (in this case is the Wired Connection , but you can use a Wireless Connection also) , open it for editing (hit the settings icon from bottom right) and add your PDC IP Address on IPv4 DNS filed (switch Automatic DNS to OFF ) as illustrated in the following screenshots:
edit network interface settings
If multiple Domain Controllers machines exists on your network then you can also add their IP Addresses on IPv4 DNS settings fields.
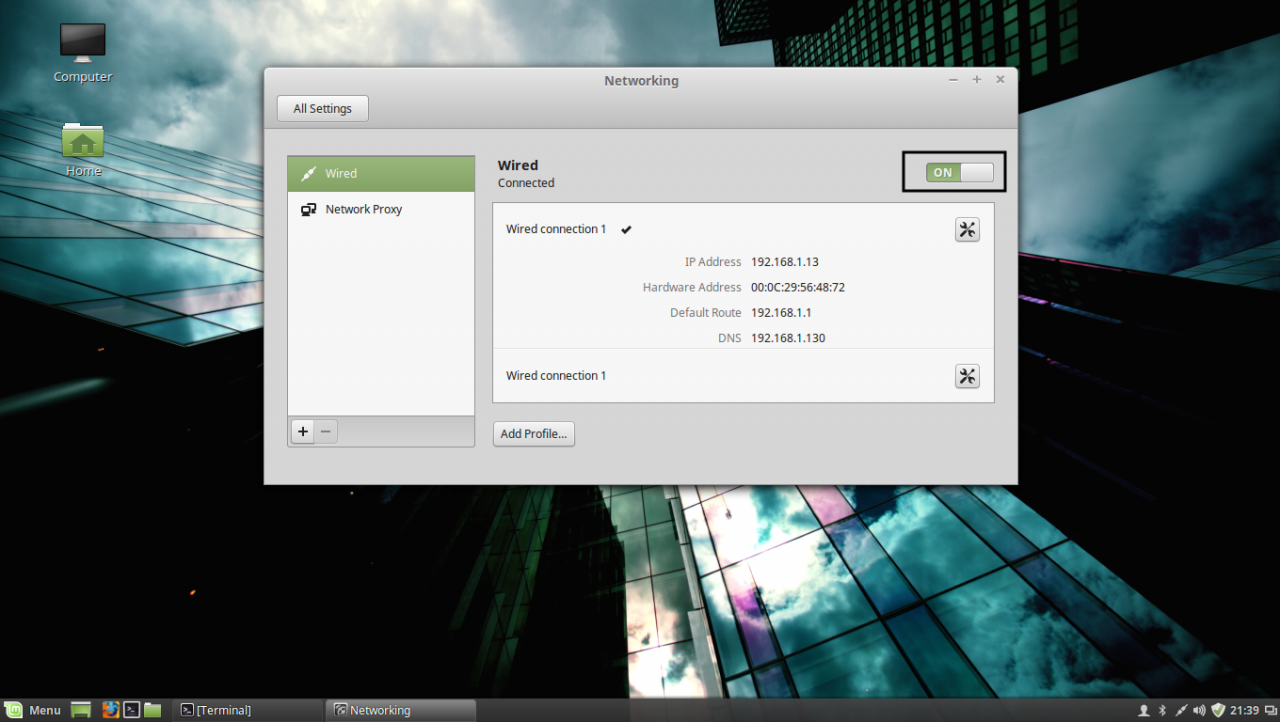
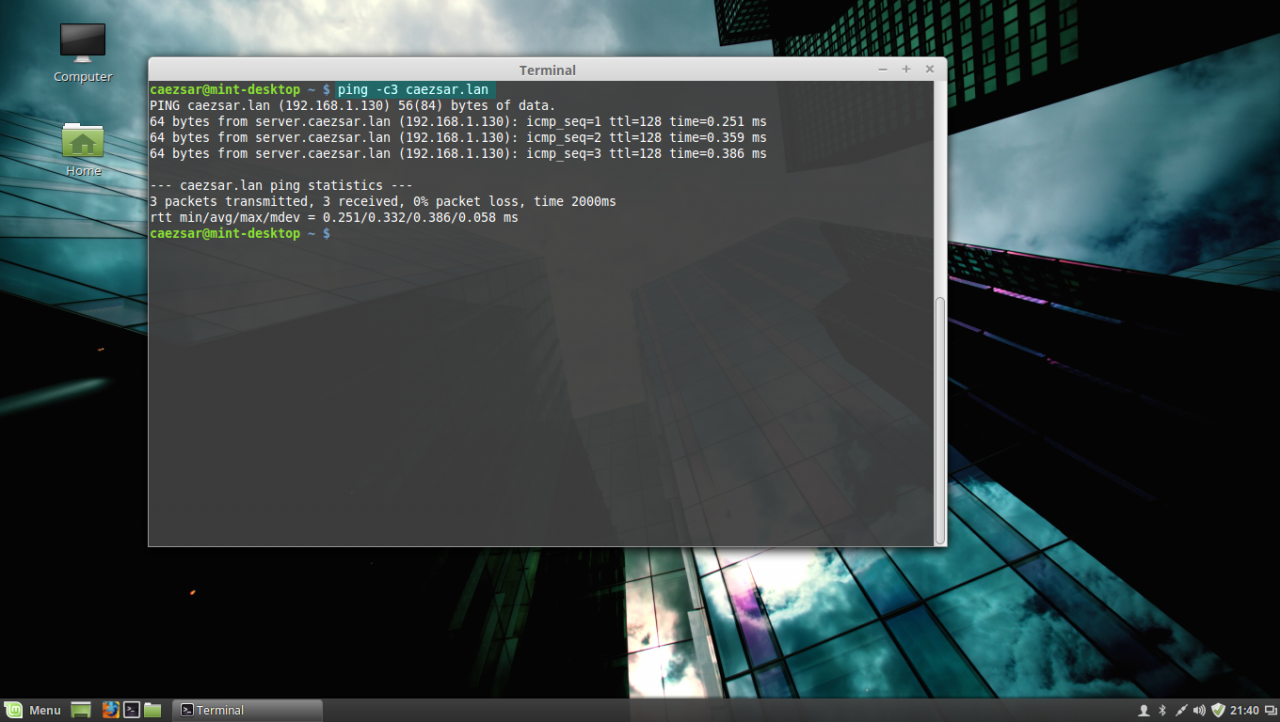
2. After you’re done, hit on Apply button and switch the edited Network Interface from ON to OFF and then back to ON in order to apply the new settings. After the network interface is started again, open a Terminal console and issue a ping command against your PDC domain name in order to verify if the settings are successfully applied and the domain name responds with the correct IP Address and FQDN of the PDC.
If you want to avoid all this manual settings, then configure a DHCP server at your premises to automatically assign network settings, especially DNS entries, that will point to your Windows PDC IP Addresses needed for DNS resolution in order to reach the AD PDC.
STEP TWO – Install Required Software Packages
As presented at the beginning of this tutorial, in order to integrate a Linux Mint machine to an Active Directory Domain Controller you need to install the SSSD service along with the following software packages and dependency:
– SSSD service (responsible with back end realm authentication) with the following dependencies: sssd-tools (optional, but useful for sssd cache, user and groups manipulation), libpam-sss (PAM modules for local authentication) and libnss-sss (NSS modules for local DNS resolution)
– Realmd (system DBus service which manages domain integration and local resources permissions)
– The following Samba Modules : samba-common-bin and samba-libs (File sharing compatibility between Windows and Linux machines)
– Krb5-user (Client network authentication and communication with the PDC server)
– ADcli (Tools for joining domain and perform other actions on an AD)
– PackageKit (Linux cross-platform packages management for interoperabillity and user privileges for software installations)
3. Now, let’s start installing the above enumerated packages by opening a Terminal console on Linux Mint and issuing the following commands with sudo privileges:
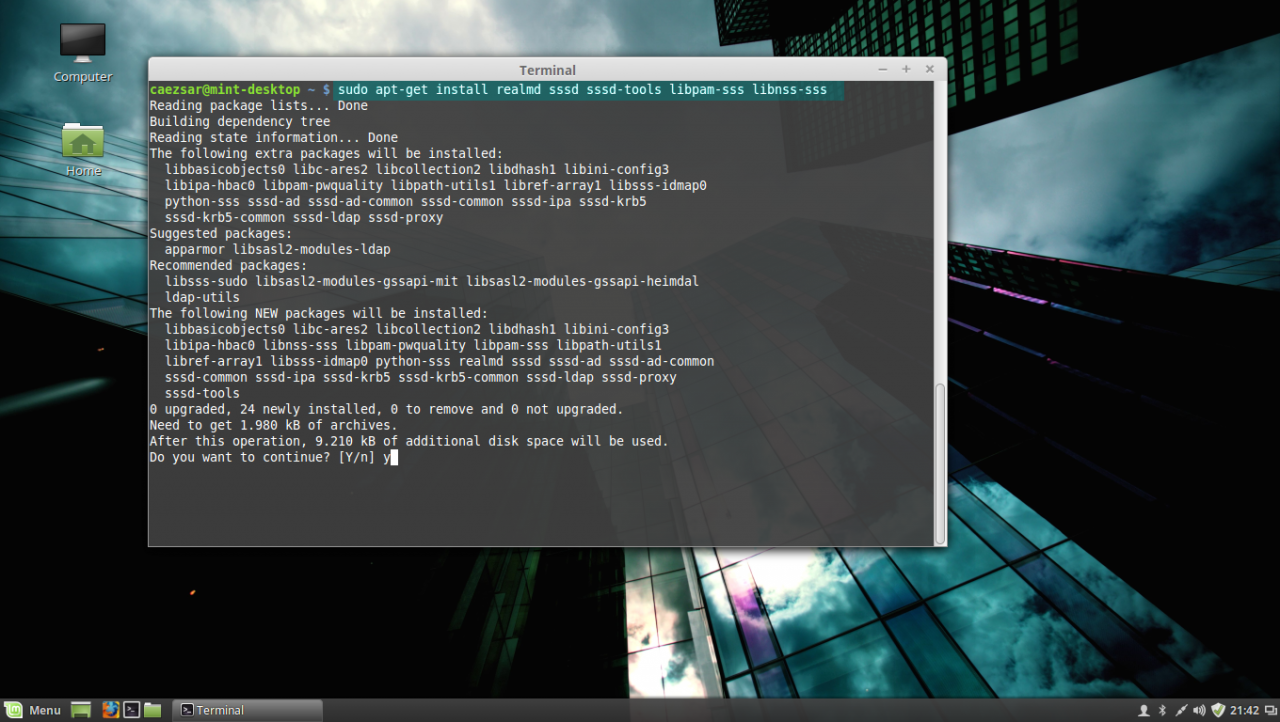
First install Realmd and SSSD service:
sudo apt-get install realmd sssd sssd-tools libpam-sss libnss-sssinstall realmd and sssd service
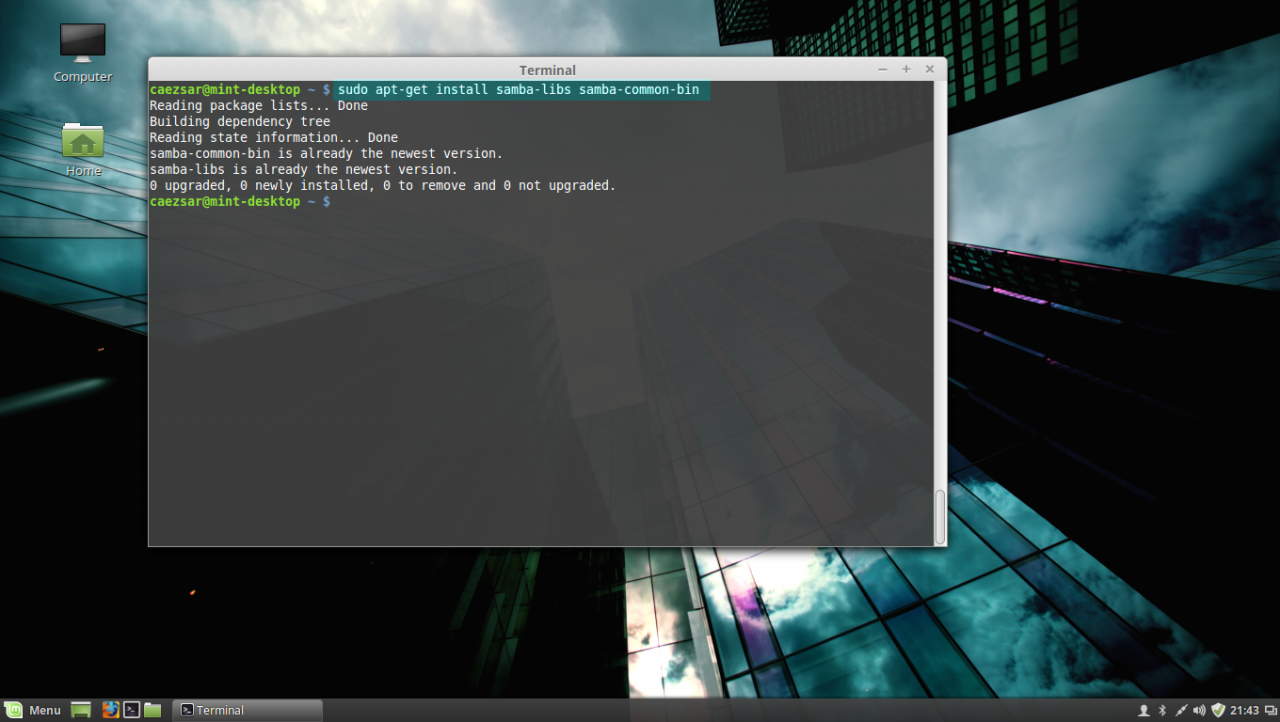
4. Next install Samba modules (by default this modules might be already installed on your system):
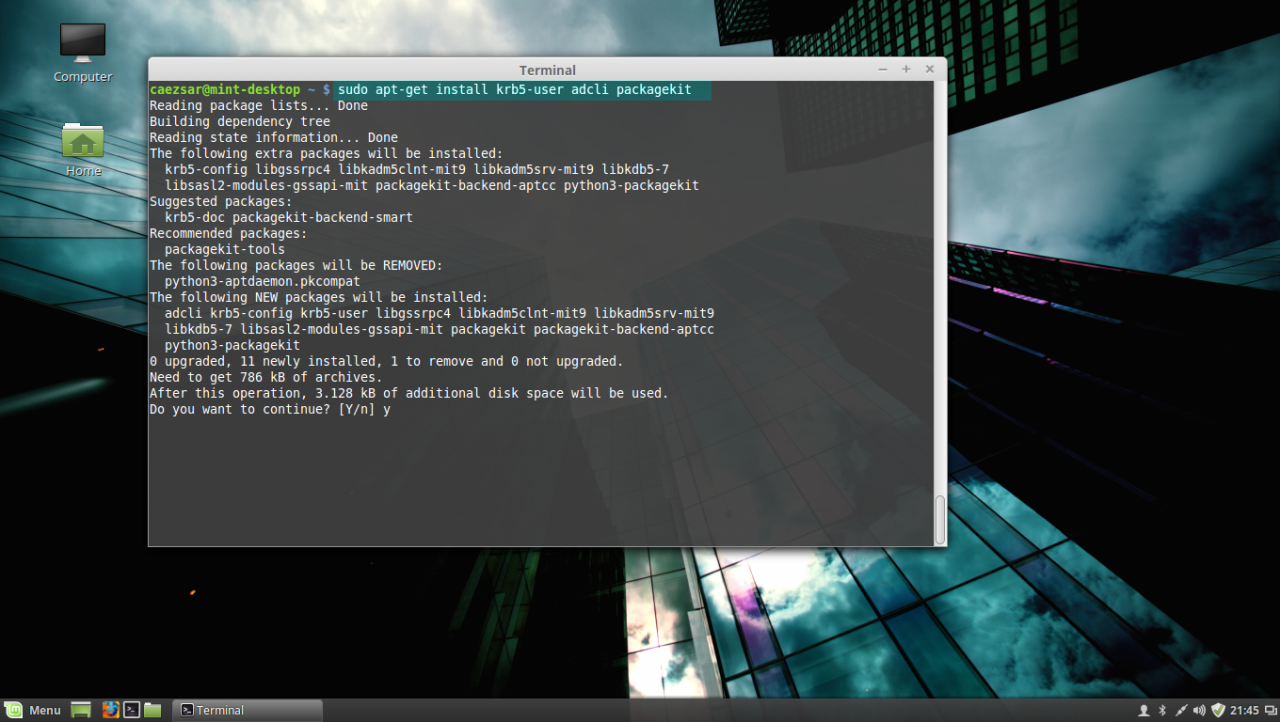
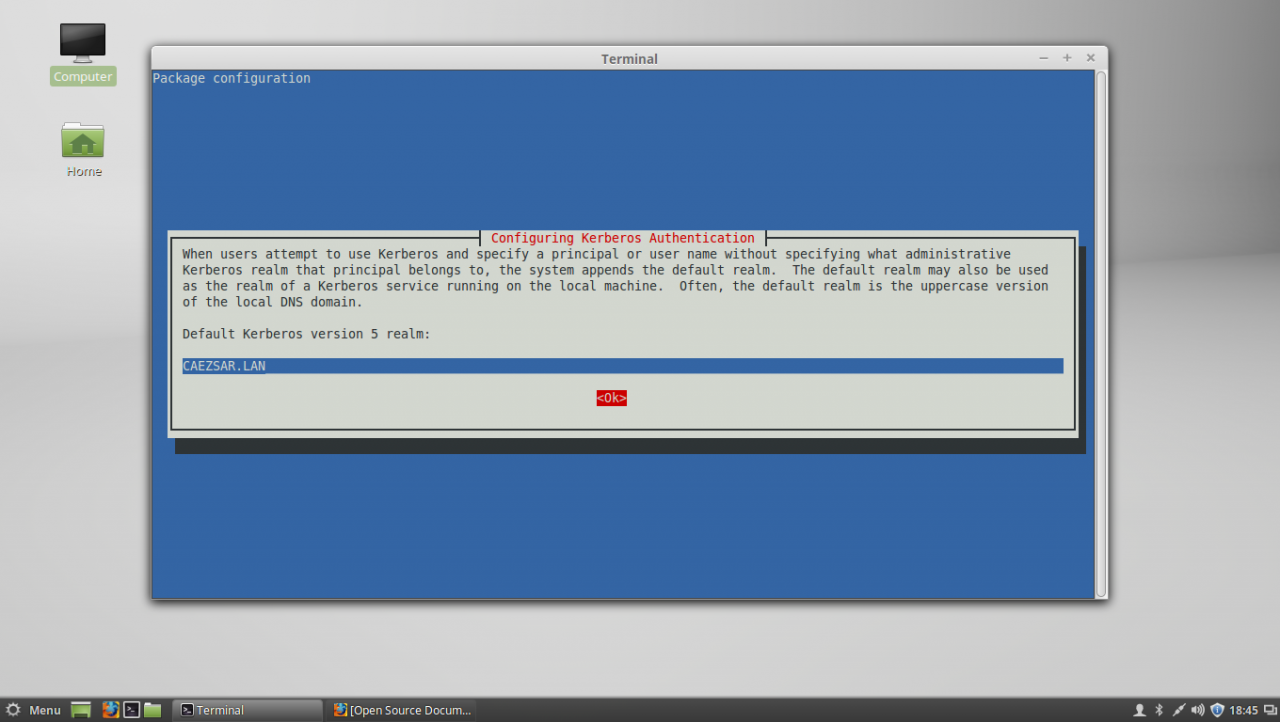
sudo apt-get install samba-libs samba-common-bin5. Last, install the other remained packages: krb5-user , adcli and packagekit . On krb5-user package, the installer will prompt you to enter the realm that will be used for Kerberos authentication. Use the name of the domain configured for your PDC with UPPERCASE (in this case the domain is CAEZSAR.LAN ), then hit Enter key to continue further with the installation packages.
sudo apt-get install krb5-user adcli packagekitinstall kerberos, adcli and packagekit packages
STEP THREE – Edit Configuration Files for SSSD, Realmd and PAM
6. Next step before starting joining Linux Mint to Windows Server AD PDC is to configure the local services for AD network authentication. By default the SSSD service has no configuration file defined on /etc/sssd/ path. In order to create a default configuration file for SSSD service, issue the following command to create and simultaneous edit the file:
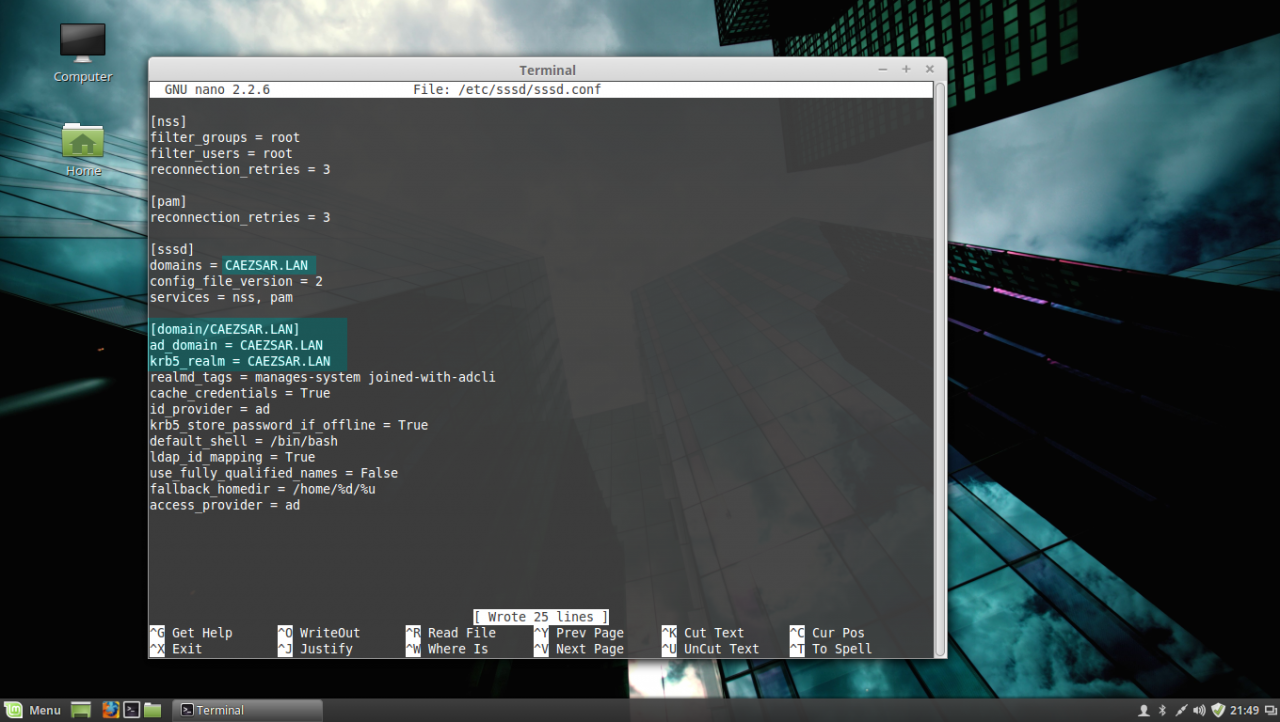
sudo nano /etc/sssd/sssd.confSSSD configuration file excerpt:
[nss] filter_groups = root filter_users = root reconnection_retries = 3 [pam] reconnection_retries = 3 [sssd] domains = CAEZSAR.LAN config_file_version = 2 services = nss, pam [domain/CAEZSAR.LAN] ad_domain = CAEZSAR.LAN krb5_realm = CAEZSAR.LAN realmd_tags = manages-system joined-with-adcli cache_credentials = True id_provider = ad krb5_store_password_if_offline = True default_shell = /bin/bash ldap_id_mapping = True use_fully_qualified_names = False fallback_homedir = /home/%d/%u access_provider = adWhile editing the file make sure you replace domains , [domain/] , ad_domain and krb5_realm parameters accordingly. Use the UPPERCASES as the above file excerpt suggests.
The fallback_homedir = /home/%d/%u parameter will cause the system to create home directories for all domain logged in users with the following path: /home/domain_name/domain_user , so practically all your domain users homes will be stored into a single directory named after your domain name on /home path. If you want to change this behavior so all domain users homes should be created as normal system users, /home/username , just remove %d variable and you’re done.
For other options and parameters concerning sssd.conf file run man sssd command.
After you finish editing the file, save it with CTRL+O , close it with CTRL+X and proceed further with the below instructions.
7. The next step is to create and edit a configuration file for Realmd in order to avoid some eventual package dependency problems by issuing the following command:
Use the following configurations for realmd file: