- 3 ways to check open ports in Linux
- Procedure to Check open ports in Linux
- Check open ports with netstat command in Linux
- Check port status with ss command in Linux
- Check open ports with lsof command in Linux
- How to Check Open Ports in Linux?
- Method 1: Checking open ports in the currently logged in Linux system using lsof command
- Method 2: Checking ports on any remote Linux server using the netcat command
- Conclusion
3 ways to check open ports in Linux
In this blog post, we will discuss 3 ways to check open ports in Linux. We will be using the command line to do this, so if you are not familiar with that environment, don’t worry! We will walk you through everything.
Checking port status is an important task for system administrators and developers . By knowing which ports are open and which ones are closed, you can better diagnose and fix networking issues.
To check open ports in Linux, we can use three methods: the netstat command, the ss command, and the lsof command. Open the terminal and type in any command above with the right option. It will list all the open ports in Linux.
- The netstat command is a network statistics utility that displays information about network connections, routing tables, and a number of network interface statistics.
- The ss command is a utility for displaying socket statistics. It can be used to report a variety of information, including open sockets.
- The lsof command is a utility for displaying information about files that are open by processes running on the system. The lsof command can be used to find out which ports are being used by which processes.
Each of these commands will give us different information about the open ports on our system. Try running each of them and see what results you get!
Procedure to Check open ports in Linux
- Open the terminal.
- Type netstat -tulpn and press Enter. This will show you a list of all the open ports on your system, as well as the PID and name of the program that is using each port.
- If you want to see more information about a specific port, type netstat -tulpn | grep portnumber and press Enter. Replace portnumber with the actual port number you want to check. The output will show you the PID and name of the program that is using that port.
Check open ports with netstat command in Linux
The easiest way to check open ports in Linux is using netstat command. You will need to open a terminal window. Then, type in the following command:
This will give you a list of all open ports on your system, as well as the programs that are using them.
The “l” flag will show you all the open ports. The ‘p’ flag will show you the program that is using the port, including the process ID (PID) and the user that owns it.
- -t : All TCP ports
- -u : All UDP ports
- -l : Display listening server sockets
- -p : Show the PID and name of the program to which each socket belongs
- -n : Don’t resolve names
- -a: Show both listening and non-listening (for TCP this means established connections) sockets.
From the following example, we can see that ports 111,22,5432,25 are open.
# netstat -utpnl
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 1/systemd
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1900/sshd
tcp 0 0 0.0.0.0:5432 0.0.0.0:* LISTEN 182374/postgres
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 2084/master
tcp6 0 0 . 111 . * LISTEN 1/systemd
tcp6 0 0 . 22 . * LISTEN 1900/sshd
tcp6 0 0 . 5432 . * LISTEN 182374/postgres
udp 0 0 0.0.0.0:111 0.0.0.0:* 1/systemd
udp6 0 0 . 111 . * 1/systemd
If you see a socket in the “LISTENING” state, it means that the port is open and waiting for a connection.
If you want to see more information about a specific port, you can use the following command:
For example, if you want to see information about port 22 (the standard SSH port), you would type in:
# netstat -tulpn | grep 22
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1900/sshd
tcp6 0 0 . 22 . * LISTEN 1900/sshd
This will show you all of the processes that are connected to port 22, as well as their PIDs and owners.
The netstat -a command will show you all of the active sockets on your system, both listening and non-listening. This can be useful for troubleshooting purposes, as it will show you all of the sockets that are currently in use.
From the following example, we can see that there is one more TCP connection. Its state is ESTABLISHED.
# netstat -tulapn | grep 22
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1900/sshd
tcp 0 80 10.244.13.128:22 10.79.96.124:53559 ESTABLISHED 1296958/sshd:
tcp6 0 0 . 22 . * LISTEN 1900/sshd
When you see a socket in the “ESTABLISHED” state, it means that the connection is established and both sides are actively communicating. This usually indicates that the connection is working properly.
If you see a socket in the “TIME_WAIT” state, it means that the connection has been terminated but the socket is still waiting for some time to expire so that it can be freed up.
Check port status with ss command in Linux
You can also use the ss command to check open ports in Linux. It stands for socket statistics , and it gives a snapshot of all active sockets on the system. The ss command is similar to netstat, but it provides more information about each connection.
To use the ss command, type in the following:
It will show more detailed information about ports than netstat . To use ss, you will need to install the iputils-ss package.
This will give you a list of all active sockets, including the following information: – The socket type ( tcp , udp , raw , etc.) – The local address – The remote address – The state ( LISTENING , ESTABLISHED , etc.)
This will give you a list of all open ports on your system.
Example:
# ss -tulpn
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
tcp LISTEN 0 128 0.0.0.0:111 0.0.0.0:* users:((«rpcbind»,pid=96374,fd=4),(«systemd»,pid=1,fd=58))
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:* users:((«sshd»,pid=1900,fd=5))
tcp LISTEN 0 4096 0.0.0.0:5432 0.0.0.0:* users:((«postgres»,pid=182374,fd=6))
tcp LISTEN 0 100 127.0.0.1:25 0.0.0.0:* users:((«master»,pid=2084,fd=16))
tcp LISTEN 0 128 [::]:111 [::]:* users:((«rpcbind»,pid=96374,fd=6),(«systemd»,pid=1,fd=60))
tcp LISTEN 0 128 [::]:22 [::]:* users:((«sshd»,pid=1900,fd=7))
tcp LISTEN 0 4096 [::]:5432 [::]:* users:((«postgres»,pid=182374,fd=7))
You can also use the following command to see information about a specific port:
For example, if you want to see information about port 22 (the standard SSH port), you would type in:
Example:
# ss -tulpn | grep «22»
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:* users:((«sshd»,pid=1900,fd=5))
tcp LISTEN 0 128 [::]:22 [::]:* users:((«sshd»,pid=1900,fd=7))
Check open ports with lsof command in Linux
we will cover the lsof command. The lsof command is a powerful tool that can be used to show a variety of information about open files on your system. To use it to check port status, type in the following:
lsof -i TCP -sTCP:LISTEN -n -P
This will give you a list of all open ports on your system, as well as the programs that are using them.
- -i TCP -sTCP:LISTEN: Look for listing ports
- -P : Inhibits the conversion of port numbers to port names for network files. Inhibiting the conversion may make lsof run a little faster. It is also useful when port name lookup is not working properly.
- -n : Do not use DNS name
# lsof -i TCP -sTCP:LISTEN -n -P
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
systemd 1 root 58u IPv4 13485027 0t0 TCP *:111 (LISTEN)
systemd 1 root 60u IPv6 13485029 0t0 TCP *:111 (LISTEN)
sshd 1900 root 5u IPv4 15494 0t0 TCP *:22 (LISTEN)
sshd 1900 root 7u IPv6 15496 0t0 TCP *:22 (LISTEN)
master 2084 root 16u IPv4 33300 0t0 TCP 127.0.0.1:25 (LISTEN)
rpcbind 96374 rpc 4u IPv4 13485027 0t0 TCP *:111 (LISTEN)
rpcbind 96374 rpc 6u IPv6 13485029 0t0 TCP *:111 (LISTEN)
postgres 182374 postgres 6u IPv4 14699999 0t0 TCP *:5432 (LISTEN)
postgres 182374 postgres 7u IPv6 14700000 0t0 TCP *:5432 (LISTEN)
You can also use the following command to see information about a specific port:
This will show you all of the processes that are connected to port 22.
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
sshd 1900 root 5u IPv4 15494 0t0 TCP *:22 (LISTEN)
sshd 1900 root 7u IPv6 15496 0t0 TCP *:22 (LISTEN)
sshd 1296958 root 5u IPv4 20115240 0t0 TCP 10.244.13.128:22->10.79.96.124:53559 (ESTABLISHED)
sshd 1296964 howtouselinux 5u IPv4 20115240 0t0 TCP 10.244.13.128:22->10.79.96.124:53559 (ESTABLISHED)
There you have it! Three ways to check port status in Linux. Which one is your favorite? Let us know in the comments below.
David is a Cloud & DevOps Enthusiast. He has years of experience as a Linux engineer. He had working experience in AMD, EMC. He likes Linux, Python, bash, and more. He is a technical blogger and a Software Engineer. He enjoys sharing his learning and contributing to open-source.
howtouselinux.com is dedicated to providing comprehensive information on using Linux.
We hope you find our site helpful and informative.
How to Check Open Ports in Linux?
Which ports are occupied by which service? How many open ports are there? Learn to scan for open ports on your Linux system or any remote system.
Whether you are using Linux as a server or desktop, knowing open ports or ports in use can be helpful in a variety of situations.
For example, if you are running an Apache or Ngnix based web server, the port in use should be 80 or 443. Checking the ports will confirm that. Similarly, you can check which port is being used by SMTP or SSH or some other services. Knowing which ports are in use can be helpful while allocating the ports to a new service.
You may also check if there are open ports for intrusion detection.
There are various ways for checking ports in Linux. I’ll share two of my favorite methods in this quick tip.
Method 1: Checking open ports in the currently logged in Linux system using lsof command
If you are logged into a system, either directly or via SSH, you can use the lsof command to check its ports.
This lsof command is used to find the files and processes used by a user. The options used here are:
- -i: If no IP address is specified, this option selects the listing of all network files
- -P: inhibits the conversion of port numbers to port names for network files
- -n: inhibits the conversion of network numbers to host names for network files
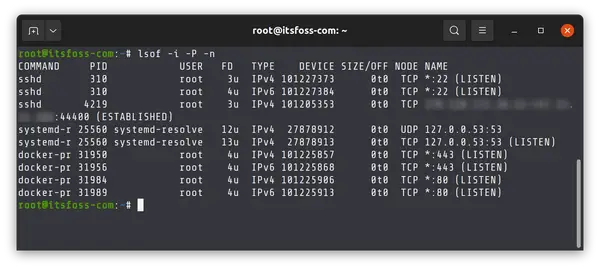
This way, it will list open ports in the Linux terminal:
But, this also shows us a lot of extra ports that the computer does not actually listen to.
You can list the listening ports by piping this output to the grep command and matching the pattern «LISTEN», like this:
sudo lsof -i -P -n | grep LISTENThis will only show the ports our computer is actively listening to and which service is using said open port.
Now, let’s see another method to check open ports in bash shell.
Method 2: Checking ports on any remote Linux server using the netcat command
nc (Netcat) is a command line utility that reads and writes data between computers over the network using the TCP and UDP protocols.
Given below is the syntax for nc command:
This utility has a nifty -z flag. When used, it will make nc scan for listening daemons without actually sending any data to the port.
Combine this with the -v flag, enabling verbosity, you can get a detailed output.
Below is the command you can use to scan for open ports using the nc command:
nc -z -v 1-65535 2>&1 | grep -v 'Connection refused'Replace IP-ADDRESS with the IP address of the Linux system you are checking the ports for.
As for why I selected values 1 to 65535 , that is because the port range starts from 1 and ends at 65535 .
Finally, pipe the output to the grep command. Using the -v option excludes any line that has «Connection refused» as a matched pattern.
This will show all the ports that are open on the computer which are accessible by another machine on the network.
Conclusion
Of the two methods, I prefer the lsof command. It’s quicker than nc command. However, you need to be logged into the system and have sudo access for that. In other words, lsof is more suitable a choice if you are managing a system.
The nc command has the flexibility of scanning ports without being logged in.
Both commands can be used for checking open ports in Linux based on the scenario you are in. Enjoy.