- Linux password file name
- NAME
- DESCRIPTION
- FILES
- SEE ALSO
- Where and How are Passwords Stored on Linux
- Examining the /etc/passwd File
- Searching User in the /etc/passwd File
- View the /etc/passwd File’s Permissions
- Examine the File /etc/shadow
- Conclusion
- About the author
- Karim Buzdar
- passwd(5) — Linux man page
- Files
- Notes
Linux password file name
NAME
passwd - the password file
DESCRIPTION
/etc/passwd contains one line for each user account, with seven fields delimited by colons (“:”). These fields are: • login name • optional encrypted password • numerical user ID • numerical group ID • user name or comment field • user home directory • optional user command interpreter If the password field is a lower-case “x”, then the encrypted password is actually stored in the shadow(5) file instead; there must be a corresponding line in the /etc/shadow file, or else the user account is invalid. The encrypted password field may be empty, in which case no password is required to authenticate as the specified login name. However, some applications which read the /etc/passwd file may decide not to permit any access at all if the password field is blank. A password field which starts with an exclamation mark means that the password is locked. The remaining characters on the line represent the password field before the password was locked. Refer to crypt(3) for details on how this string is interpreted. If the password field contains some string that is not a valid result of crypt(3), for instance ! or *, the user will not be able to use a unix password to log in (but the user may log in the system by other means). The comment field is used by various system utilities, such as finger(1). The home directory field provides the name of the initial working directory. The login program uses this information to set the value of the $HOME environmental variable. The command interpreter field provides the name of the user's command language interpreter, or the name of the initial program to execute. The login program uses this information to set the value of the $SHELL environmental variable. If this field is empty, it defaults to the value /bin/sh.
FILES
/etc/passwd User account information. /etc/shadow optional encrypted password file /etc/passwd- Backup file for /etc/passwd. Note that this file is used by the tools of the shadow toolsuite, but not by all user and password management tools.
SEE ALSO
crypt(3), getent(1), getpwnam(3), login(1), passwd(1), pwck(8), pwconv(8), pwunconv(8), shadow(5), su(1), sulogin(8).
© 2019 Canonical Ltd. Ubuntu and Canonical are registered trademarks of Canonical Ltd.
Where and How are Passwords Stored on Linux
“A username and password for a single account are the primary requirements for accessing a Linux system. In order to verify a user during a system login attempt, all user accounts passwords are saved in a file or database. Finding this file on a user’s machine is beyond the knowledge and abilities of every user. Linux checks the password given by the user against an entry in one or more files located in the directory named “/etc.” when the user logs in with a username and password.
All the crucial data required for user login is stored in the /etc/passwd files. The user’s account information is kept in the /etc/passwd file, to put it another way. The entire list of users on your Linux system is contained in this plain text file. It contains data about the user name, password, group ID, user id, shell, and home directory. Only superuser or root user accounts should have restricted write access permissions.”
This article will show you where and how to save the passwords for system user accounts on Linux distributions.
Examining the /etc/passwd File
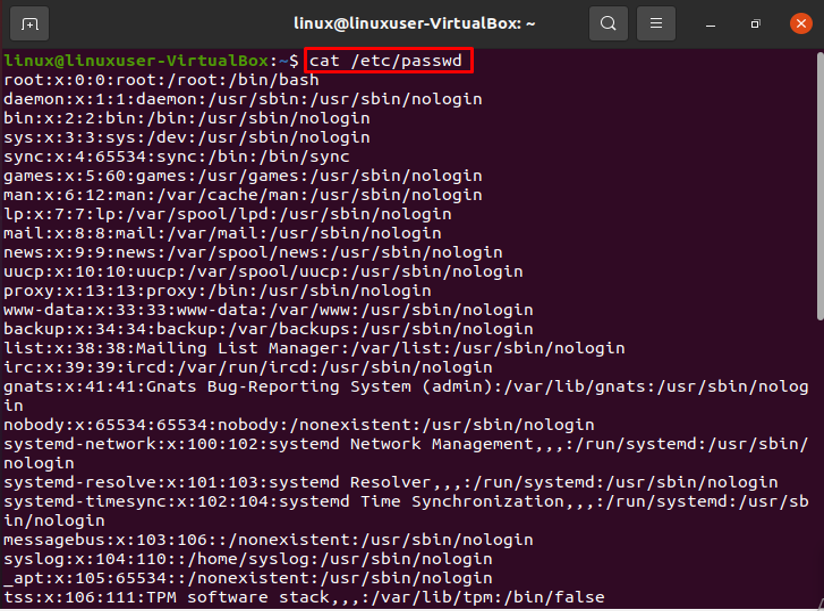
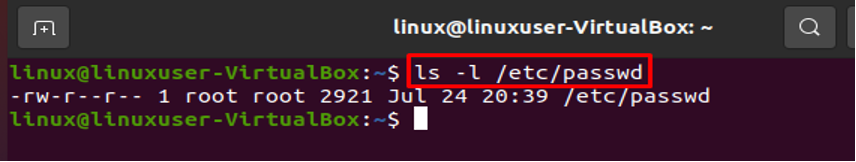
In order to run administrative commands, you must have root access. The details of your system’s user account are in the /etc/passwd file. The colon “:” symbol separates each stored field. The following command will display each entry in the /etc/passwd file:
The command mentioned above will list every user on your Linux system, and hence terminal’s screen will show the following format:
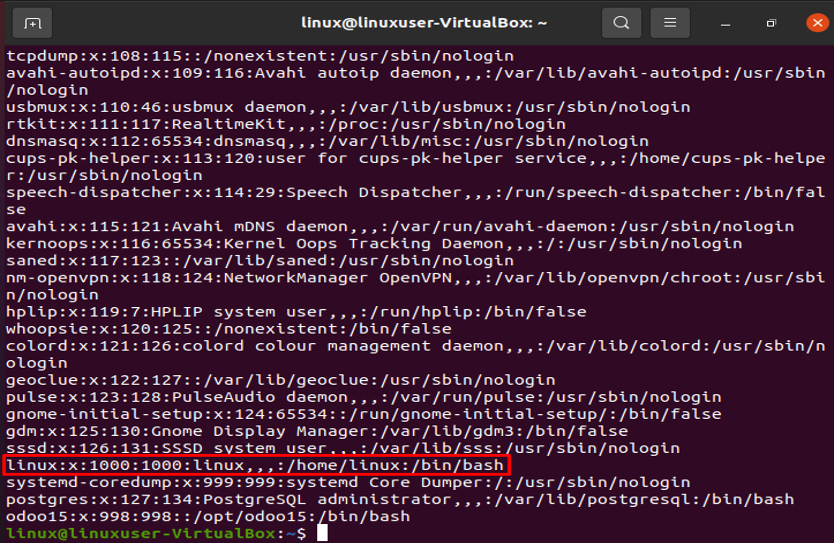
The information about the currently used account is shown in the highlighted portion below.
There are several fields of data divided by colons (:).
Linux: Username is shown in field one. The username field can only have between 1 and 32 characters. Linux is the username in the sample above.
Password (x): The “x” character denotes the encrypted password, as can be seen in the aforementioned example.
UID (1000): Each user must have their own unique user ID. The user ID in the aforementioned screenshot is 1000.
GID (1000): The group ID is represented by the following field. The GID is kept in the file /etc/group. The example indicates that the user is a member of group 1000.
Details (linux): Comments should go in the field below. You can enter further details about the identified person in this box, such as the individual’s complete name, contact information, etc. The user does not offer a phone number in the case above, though.
Home directory (/home/linux): The location of the user’s current home directory is displayed in this field. It will show “/” if the requested directory does not exist.
/bin/bash shell: /bin/bash is the default absolute path for a shell or command.
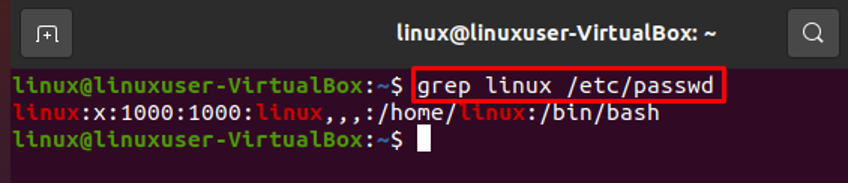
Searching User in the /etc/passwd File
A specific user can be found easily by using the grep command. For instance, if we wish to search for the username “linux” in the /etc/passwd file, we may quickly do it by using the following command, which will save us time:
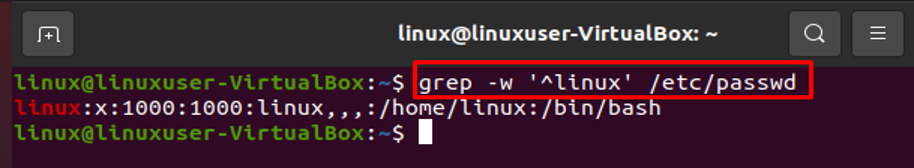
In this regard, we can also use the following command:
View the /etc/passwd File’s Permissions
As we stated above, the /etc/passwd file must have the owner be superuser or root, and all users other than root should have read rights.
To check the read rights on the file, type the following:
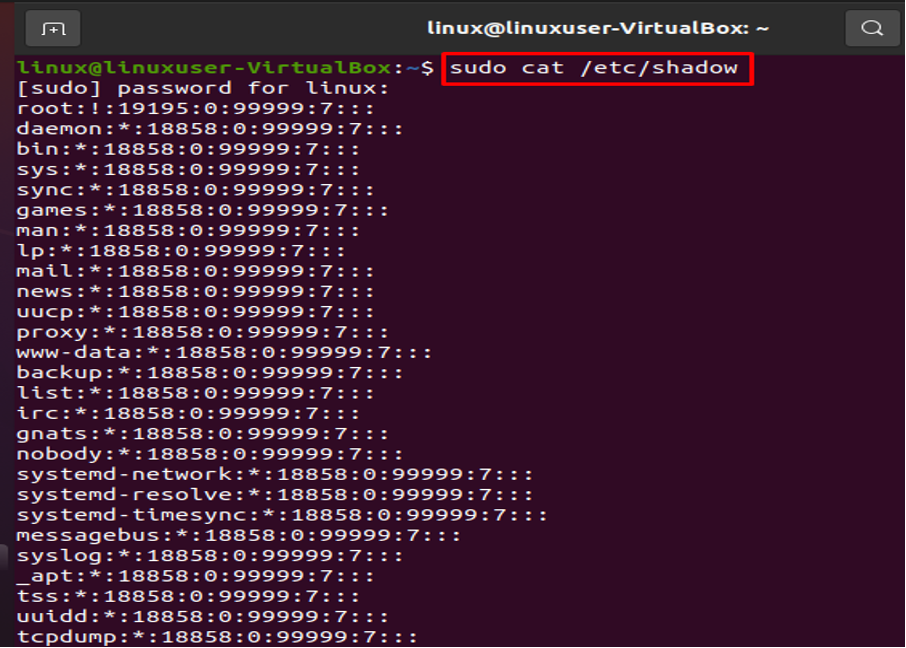
Examine the File /etc/shadow
Your whole encrypted password collection is stored in the root-only /etc/shadow file. Every password is viewable in encrypted form. Let’s execute the next command to show the content:
Conclusion
The aforementioned article demonstrates that the Linux operating system keeps all user account details and passwords in the /etc/passwd file. Additionally, we have seen every encrypted password kept in the /etc/shadow file. To learn more about the user’s group, you can also look through the /etc/group file.
About the author
Karim Buzdar
Karim Buzdar holds a degree in telecommunication engineering and holds several sysadmin certifications. As an IT engineer and technical author, he writes for various web sites. He blogs at LinuxWays.
passwd(5) — Linux man page
The /etc/passwd file is a text file that describes user login accounts for the system. It should have read permission allowed for all users (many utilities, like ls(1) use it to map user IDs to usernames), but write access only for the superuser.
In the good old days there was no great problem with this general read permission. Everybody could read the encrypted passwords, but the hardware was too slow to crack a well-chosen password, and moreover the basic assumption used to be that of a friendly user-community. These days many people run some version of the shadow password suite, where /etc/passwd has an aqxaq character in the password field, and the encrypted passwords are in /etc/shadow, which is readable by the superuser only.
If the encrypted password, whether in /etc/passwd or in /etc/shadow, is an empty string, login is allowed without even asking for a password. Note that this functionality may be intentionally disabled in applications, or configurable (for example using the «nullok» or «nonull» arguments to pam_unix.so).
If the encrypted password in /etc/passwd is «*NP*» (without the quotes), the shadow record should be obtained from an NIS+ server.
Regardless of whether shadow passwords are used, many system administrators use an asterisk (*) in the encrypted password field to make sure that this user can not authenticate him- or herself using a password. (But see NOTES below.)
If you create a new login, first put an asterisk (*) in the password field, then use passwd(1) to set it.
Each line of the file describes a single user, and contains seven colon-separated fields:
The field are as follows: name This is the user’s login name. It should not contain capital letters. password This is either the encrypted user password, an asterisk (*), or the letter aqxaq. (See pwconv(8) for an explanation of aqxaq.) UID The privileged root login account (superuser) has the user ID 0. GID This is the numeric primary group ID for this user. (Additional groups for the user are defined in the system group file; see group(5)). GECOS This field (sometimes called the «comment field») is optional and used only for informational purposes. Usually, it contains the full username. Some programs (for example, finger(1)) display information from this field. GECOS stands for «General Electric Comprehensive Operating System», which was renamed to GCOS when GE’s large systems division was sold to Honeywell. Dennis Ritchie has reported: «Sometimes we sent printer output or batch jobs to the GCOS machine. The gcos field in the password file was a place to stash the information for the $IDENTcard. Not elegant.» directory This is the user’s home directory: the initial directory where the user is placed after logging in. The value in this field is used to set the HOME environment variable. shell This is the program to run at login (if empty, use /bin/sh). If set to a nonexistent executable, the user will be unable to login through login(1). The value in this field is used to set the SHELL environment variable.
Files
Notes
If the encrypted password is set to an asterisk (*), the user will be unable to login using login(1), but may still login using rlogin(1), run existing processes and initiate new ones through rsh(1), cron(8), at(1), or mail filters, etc. Trying to lock an account by simply changing the shell field yields the same result and additionally allows the use of su(1).