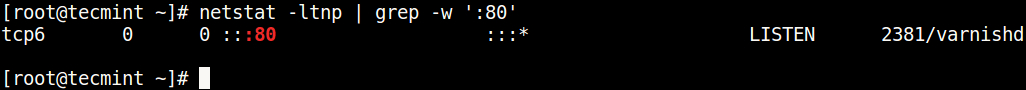- How to know what program is listening on a given port?
- 8 Answers 8
- 3 Ways to Find Out Which Process Listening on a Particular Port
- 1. Using netstat Command
- 2. Using lsof Command
- 3. Using fuser Command
- Finding the PID of the Process Using a Specific Port
- 1. Overview
- 2. root Permission
- 3. Using netstat
- 4. Using ss
- 5. Using lsof
- 6. Using fuser
- 7. Conclusion
How to know what program is listening on a given port?
I suspect a program is listening on port 8000 on my machine. When I run the following command, I get this error:
> python -m SimpleHTTPServer # Lots of python error socket.error: [Errno 98] Address already in use If I use another port ( 8000 is the default), the web server runs fine. If I run wget localhost:8000 from the command line, it returns 404 Not Found . What can I do (or what tools are available) to find what program is listening on port 8000 , and from there where that program is configured?
8 Answers 8
Open your terminal and type as
that command will list you the application used by that port with PID. (If no results run via sudo since your might have no permission to certain processes.)
For example, with port 8000 ( python3 -m http.server ):
$ lsof -i :8000 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME python3 3269 user 3u IPv4 1783216 0t0 TCP *:8000 (LISTEN) $ sudo lsof -i :22 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME sshd 998 root 3u IPv4 1442116 0t0 TCP *:ssh (LISTEN) sshd 998 root 4u IPv6 1442118 0t0 TCP *:ssh (LISTEN) @Imray the example searches for port 8881. The PID column contains the process IDs and the NAME column contains the ports.
You can use netstat to see which process is listening on which port.
You can use this command to have a full detail :
if you need to know exactly which one is listening on port 8000 you can use this :
sudo netstat -peanut | grep ":8000 " There is no process that can hide from netstat.
To kill/end the process use kill
To expound on the answer by @33833 you can get some very detailed info, for example:
$ lsof -i :8000 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME squid3 1289 proxy 15u IPv6 14810490 0t0 TCP *:8000 (LISTEN) $ ps -fp 1289 UID PID PPID C STIME TTY TIME CMD proxy 1289 1 0 09:48 ? 00:00:00 /usr/sbin/squid3 -N -f /etc/squid-deb-proxy/squid-deb-proxy.conf I can see right there that squid is the process, but it is actualy my squid-deb-proxy that is taking up the port.
Another good example of a java app:
$ lsof -i :4242 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME java 3075 root 86u IPv4 12019 0t0 TCP *:4242 (LISTEN) $ ps -fp 3075 UID PID PPID C STIME TTY TIME CMD root 3075 1 15 May24 ? 3-16:07:25 /usr/local/crashplan/jre/bin/java -Dfile.encoding=UTF-8 -Dapp=CrashPlanService -DappBaseName=CrashPl You can see in lsof (LiSt Open Files) that it is java, which is less than helpful. Running the ps command with the PID we can see right away that it is CrashPlan.
3 Ways to Find Out Which Process Listening on a Particular Port
A port is a logical entity that represents an endpoint of communication and is associated with a given process or service in an operating system. In previous articles, we explained how to find out the list of all open ports in Linux and how to check if remote ports are reachable using the Netcat command.
In this short guide, we will show different ways of finding the process/service listening on a particular port in Linux.
1. Using netstat Command
netstat (network statistics) command is used to display information concerning network connections, routing tables, interface stats, and beyond. It is available on all Unix-like operating systems including Linux and also on Windows OS.
In case you do not have it installed by default, use the following command to install it.
$ sudo apt-get install net-tools [On Debian/Ubuntu & Mint] $ sudo dnf install net-tools [On CentOS/RHEL/Fedora and Rocky Linux/AlmaLinux] $ pacman -S netstat-nat [On Arch Linux] $ emerge sys-apps/net-tools [On Gentoo] $ sudo dnf install net-tools [On Fedora] $ sudo zypper install net-tools [On openSUSE]
Once installed, you can use it with the grep command to find the process or service listening on a particular port in Linux as follows (specify the port).
In the above command, the flags.
- l – tells netstat to only show listening sockets.
- t – tells it to display tcp connections.
- n – instructs it to show numerical addresses.
- p – enables showing of the process ID and the process name.
- grep -w – shows matching of exact string (:80).
Note: The netstat command is deprecated and replaced by the modern ss command in Linux.
2. Using lsof Command
lsof command (List Open Files) is used to list all open files on a Linux system.
To install it on your system, type the command below.
$ sudo apt-get install lsof [On Debian, Ubuntu and Mint] $ sudo yum install lsof [On RHEL/CentOS/Fedora and Rocky Linux/AlmaLinux] $ sudo emerge -a sys-apps/lsof [On Gentoo Linux] $ sudo pacman -S lsof [On Arch Linux] $ sudo zypper install lsof [On OpenSUSE]
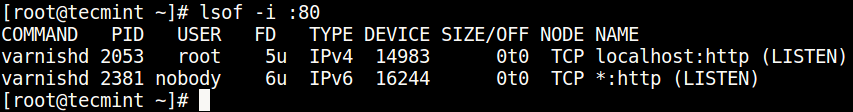
To find the process/service listening on a particular port, type (specify the port).
3. Using fuser Command
fuser command shows the PIDs of processes using the specified files or file systems in Linux.
You can install it as follows:
$ sudo apt-get install psmisc [On Debian, Ubuntu and Mint] $ sudo yum install psmisc [On RHEL/CentOS/Fedora and Rocky Linux/AlmaLinux] $ sudo emerge -a sys-apps/psmisc [On Gentoo Linux] $ sudo pacman -S psmisc [On Arch Linux] $ sudo zypper install psmisc [On OpenSUSE]
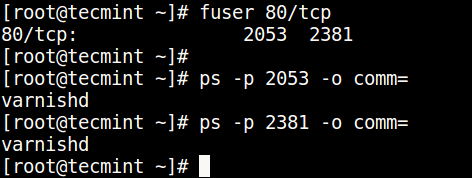
You can find the process/service listening on a particular port by running the command below (specify the port).
Then find the process name using PID number with the ps command like so.
$ ps -p 2053 -o comm= $ ps -p 2381 -o comm=
You can also check out these useful guides about processes in Linux.
You might also like:
That’s all! Do you know of any other ways of finding the process/service listening on a particular port in Linux, let us know via the comment form below.
Finding the PID of the Process Using a Specific Port
The Kubernetes ecosystem is huge and quite complex, so it’s easy to forget about costs when trying out all of the exciting tools.
To avoid overspending on your Kubernetes cluster, definitely have a look at the free K8s cost monitoring tool from the automation platform CAST AI. You can view your costs in real time, allocate them, calculate burn rates for projects, spot anomalies or spikes, and get insightful reports you can share with your team.
Connect your cluster and start monitoring your K8s costs right away:
1. Overview
We all know that a port can only be used by a single application or service at the same time. Sometimes we need to know which process is listening on a specific port.
In this tutorial, we’ll see different approaches to finding the process listening on a particular port in Linux.
2. root Permission
In Linux, only the root user or the process owner can obtain the detailed information of the process.
When we want to check a process listening on a particular port, we don’t know who the process belongs to.
With root permission, we can gain all the necessary information on the process, for instance, the process identifier.
Therefore, we may need to start our network tools with the root user (or with sudo).
3. Using netstat
The netstat command is a member of the net-tools package.
In the past, it came preinstalled in many Linux distributions. However, the net-tools package hasn’t been updated since 2011.
Due to its lack of the support of modern Linux kernel features and other reasons, the net-tools package has become obsolete.
That said, netstat itself is still widely used, so let’s take a look at how it can help.
First of all, let’s see an example output of the netstat command:
root# netstat -ltnup Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 127.0.0.1:17600 0.0.0.0:* LISTEN 1293/dropbox tcp 0 0 127.0.0.1:17603 0.0.0.0:* LISTEN 1293/dropbox tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 575/sshd tcp 0 0 127.0.0.1:9393 0.0.0.0:* LISTEN 900/perl tcp 0 0 . 80 . * LISTEN 9583/docker-proxy tcp 0 0 . 443 . * LISTEN 9571/docker-proxy udp 0 0 0.0.0.0:68 0.0.0.0:* 8822/dhcpcd . With the options ltnup, netstat shows us all ports in use in the above example.
Let’s have a look at what the options mean:
- l – show only listening sockets
- t – show TCP connections
- n – show addresses in a numerical form
- u – show UDP connections
- p – show process id/program name
If we review the above output, the last column is exactly what we’re looking for: the PID and Process name listening on a particular port.
We can simply pipe the netstat output to the grep command to get the process information on an individual port.
For example, let’s see which process is listening on port 22:
root# netstat -ltnup | grep ':22' tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 575/sshd4. Using ss
In the previous section, we discussed that the net-tools package is deprecated.
The ss command is the replacement of the netstat command.
Now let’s see how to use the ss command to see which process is listening on port 22:
root# ss -ltnup 'sport = :22' Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:* users:("sshd",pid=575,fd=3))If we check the options, we find that the options we passed to the ss command are the same as we passed to netstat.
The only difference is that we were making use of the state-filter of the ss utility instead of an extra grep process to filter the output.
Similar to the output of the netstat command, the expected process information lies in the last column, too.
5. Using lsof
The lsof command can list all open files in a Linux system.
We can use the lsof command to find the process using a specific port with the -i :port_number option:
root# lsof -i :22 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME sshd 575 root 3u IPv4 19373 0t0 TCP *:ssh (LISTEN) The first four columns in the above output tell us the process name listening on port 22 and its PID, owner, and the file descriptor.
We can pass multiple -i :port to the lsof command to find out the processes listening on various ports:
root# lsof -i :22 -i :68 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME sshd 575 root 3u IPv4 19373 0t0 TCP *:ssh (LISTEN) dhcpcd 8822 root 10u IPv4 49601 0t0 UDP *:bootpc 6. Using fuser
The fuser utility displays which processes are using named files, sockets, or file systems. It’s included in the psmisc package and preinstalled on many modern Linux distributions by default.
We can use this to view the information of the process running on a specific port. Again let’s find out the PID of the processing listening TCP port 22:
root# fuser 22/tcp 22/tcp: 575 The above output is pretty straightforward. We know that the process with PID 575 is listening on TCP port 22.
However, it doesn’t tell us detailed information about the process, for example, what’s the name of process 575? who owns the process? and so on.
If we want to obtain more details about the process, we can pass the “-v” option to the fuser command to have a verbose output:
root# fuser -v 22/tcp USER PID ACCESS COMMAND 22/tcp: root 575 F. sshdUsing the fuser command, we can also check the running process information on multiple TCP or UDP ports in one shot:
root# fuser -v 22/tcp 68/udp USER PID ACCESS COMMAND 22/tcp: root 575 F. sshd 68/udp: root 8822 F. dhcpcd7. Conclusion
In this short article, we’ve learned four different Linux command-line utilities with examples to figure out the information of the process listening on a particular port.
They are all very powerful tools to have in our arsenal on the Linux command line.