- Powerhell Core Ubuntu 18.04 – PSRemoting to an Active Directory Machine
- Install and configuring Kerberos Client
- Configuring ssh
- Testing and working Kerberos Client
- What about setting in Windows Systems?
- Name Resolution Tip
- Testing connectivity
- Summary
- How To Connect to PowerShell Core
- References
- Sponsors
- Recent Posts
- Try to import module ActiveDirectory on a linux powershell
- 2 Answers 2
Powerhell Core Ubuntu 18.04 – PSRemoting to an Active Directory Machine
Sometime there’s the need to do PowerShell remoting from Linux to a Windows System. In my lab environment, I was able to install, configure, and established a PowerShell Remote connection from a Linux Ubuntu 18.04 system to *Active Directory joined Windows System.
*Note: Before trying to following steps, if you’re in a corporate domain, consult with your security team. I would recommend that you try this scenario in virtual machine environment.
I’ve been struggling trying to OpenSSH in both Windows 10 (Build 1803) and Windows Server 2019 with no success connecting from Linux. So, I decided to try install Kerberos component on my Ubuntu system and it works! And, with no need to joined my Linux system to my virtual Active Directory domain.
Install and configuring Kerberos Client
$ sudo apt-get install krb5-user
[libdefaults] default_realm = DOMAINNAME.COM # The following are custom settings for "DOMAINNAME" Kerberos: dns_lookup_realm = true dns_lookup_kdc = true default_tgs_enctypes = arcfour-hmac-md5 des-cbc-crc des-cbc-md5 default_tkt_enctypes = arcfour-hmac-md5 des-cbc-crc des-cbc-md5 permitted_enctypes = arcfour-hmac-md5 des-cbc-crc des-cbc-md5 [realms] TRINITY.COM = < kdc = DOMAINMACHINENAME admin_server = DOMAINMACHINENAME >[domain_realm] .com = DOMAINNAME
*Note: Make a copy of the krb5.conf file before any changes.
One thing to point out! Both DOMAINNAME and DOMAINMACHINENAME, must be in uppercase.
Configuring ssh
Next step involves in configuring the ssh for Kerberos negotiation. This is the ssh_config file (not sshd_config).
$ sudo vim /etc/ssh/ssh_config
Make sure the following parameters are set at the end of the *ssh_config file:
SendEnv LANG LC_* HashKnownHosts yes GSSAPIAuthentication yes GSSAPIDelegateCredentials no GSSAPIKeyExchange yes
*Note: If there are missing ones, don’t touch the commented ones. Just copy/paste and set the values.
After completing the changes, I would recommend a reboot.
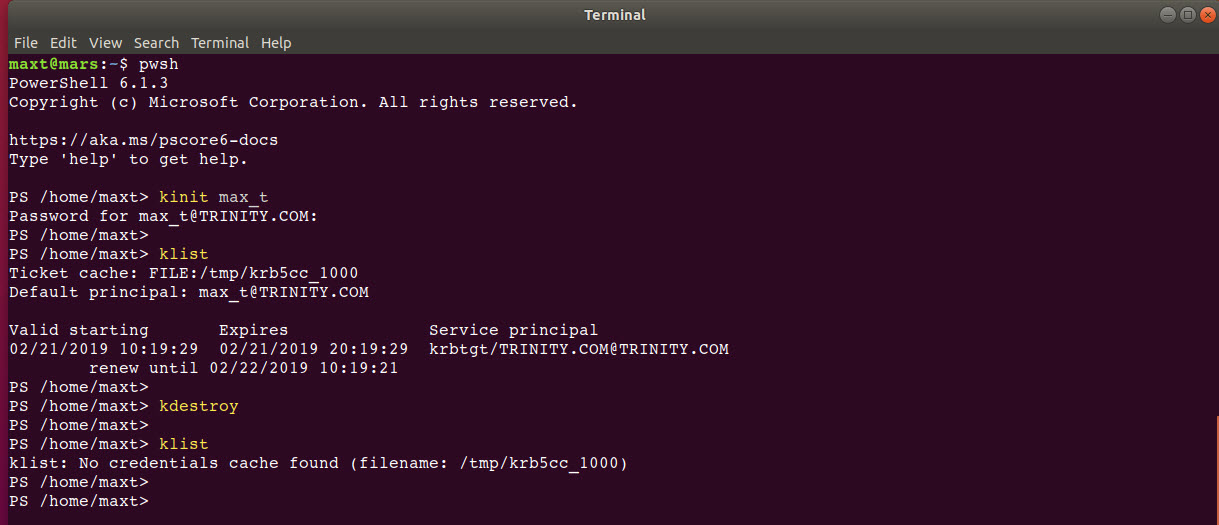
Testing and working Kerberos Client
Here are a few linux commands to work with Kerberos client. If the krb5.conf setting are set correctly, then the following commands should work without any issues.
1. This command will verify user domain, asking for password.
2. Shows the list of Kerberos Cached tickets and credential.
3. To delete\clear all Kerberos Cache entries:
What about setting in Windows Systems?
I’m will cover the whole PowerShell remoting setup. But, I will highlight what’s needed to make Linux connect to a Active Directory Domain system.
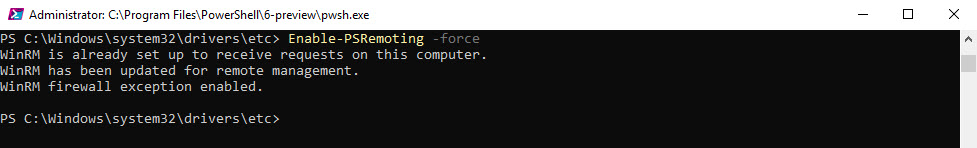
In PowerShell Conscole, run the “Enable-PSRemoting -force” command line on both client and server. This command will add the firewall rule to allow PowerShell remoting to work.
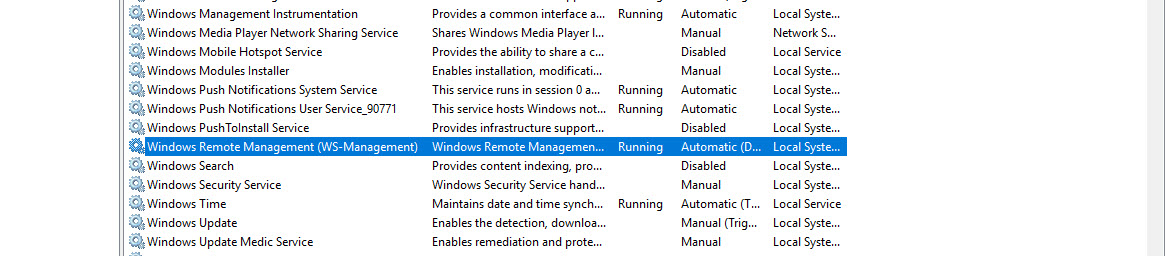
Check the Windows Remote Management service is running. By default, in Windows 10 client, this is set to “Manual”.
On the server, just verify that the service running.
Before, connecting Linux to a windows domain system, make sure to test PowerShell remoting between Windows machines. This will guarantee that you got everything working correctly.
Name Resolution Tip
I don’t join my Linux system to my AD domain. So, to resolve my name resolution issues, I manually update the hosts file on my systems. This will include the domain ip-address as well as all other systems
hosts file : xxx.xxx.xxx.xxx domainname.com :
Testing connectivity
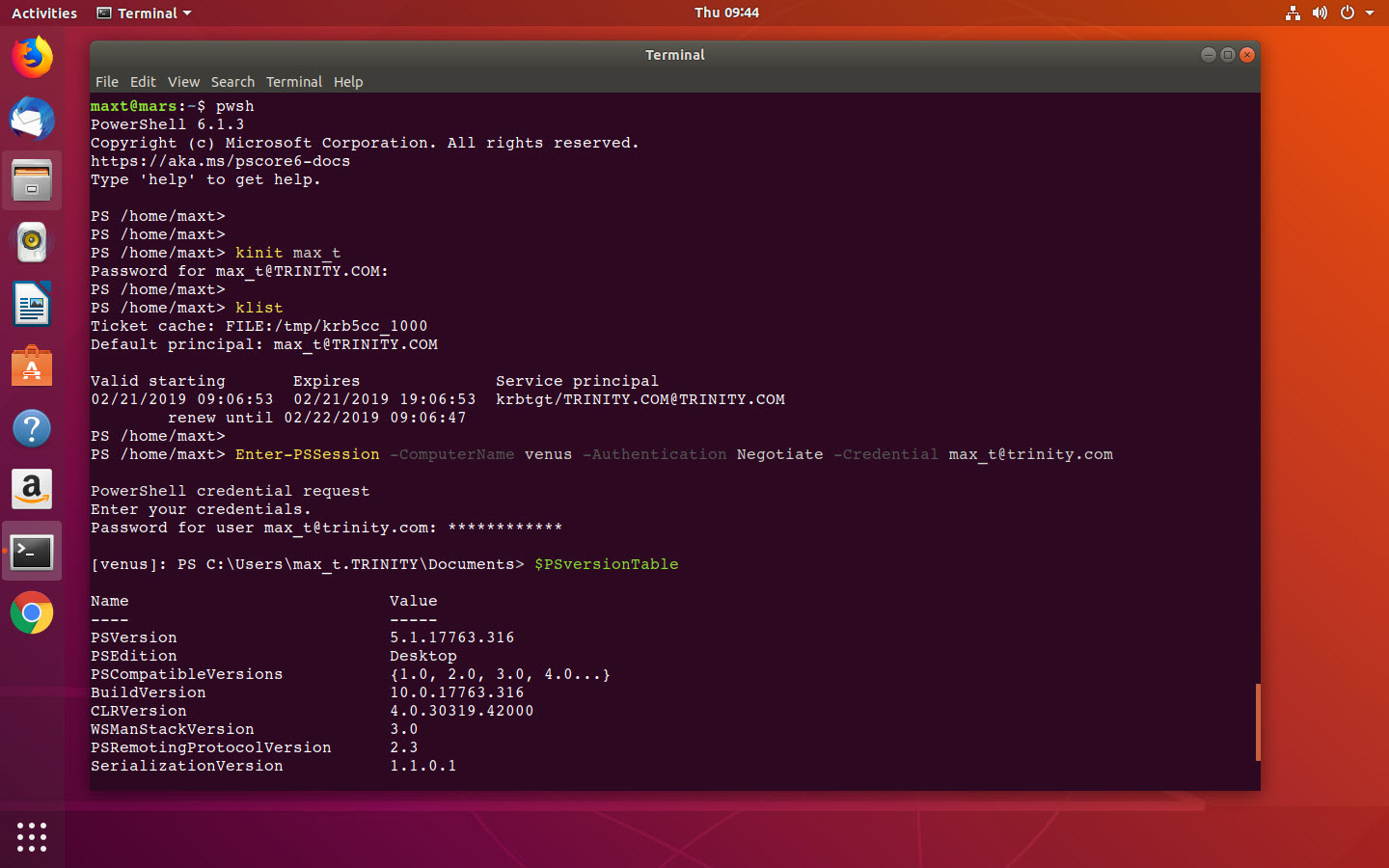
Ubuntu 18.04 Connecting to a domain system final test.
1. In Linux, open PowerShell:
2. Prepare the domain user:
PS /home/user> kinit domainuser
3. Create a *PowerShell Remote interactive session:
PS /home/user> Enter-PSSession -ComputerName wincomputer -Authentication Negotiate -Credential user@domainname.com
*Note: This remote connection will open Windows PowerShell and not PowerShell Core.
Summary
So, in Ubuntu 18.04 installing and configuring Kerberos user client only, you can connect your Linus system to a Active Directory Domain systems. But remember, this will connect to a Windows PowerShell session only.
I’m hoping that in the near future we can have the ability to select a PowerShell versions. Wait!! There’s a way to open a PowerShell Core session instead of Windows PowerShell!!
How To Connect to PowerShell Core
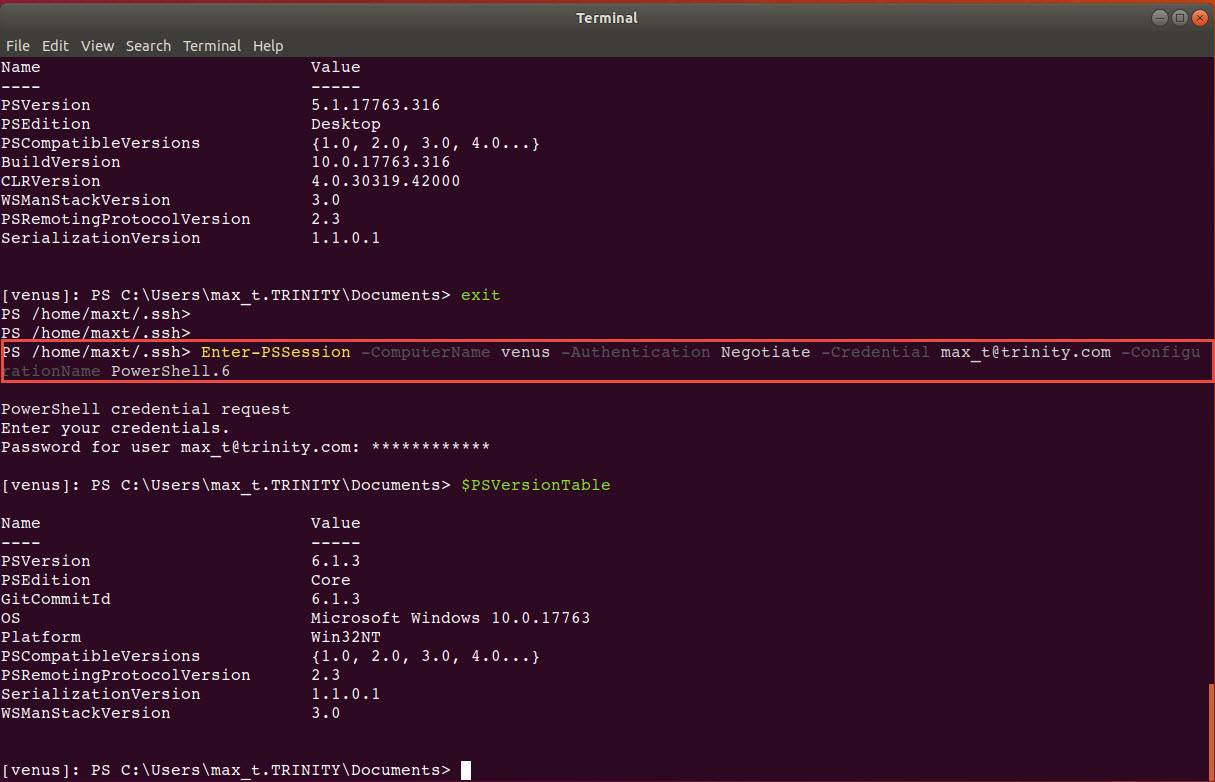
So, by default you’re going to connect to Windows PowerShell. But, if you use the following parameter ‘-ConfigurationName’ folllowed by either ‘ PowerShell.6 ‘ or ‘ PowerShell.6-Preview ‘ then you’ll get PowerShell Core session. Also, you can use an specific version ‘ PowerShell.6.1.0 ‘.
Enter-PSSession -ComputerName venus -Authentication Negotiate -Credential max_t@trinity.com -ConfigurationName PowerShell.6
Thanks to Steve Lee (Microsoft PowerShell Team) for letting me know this is already available.
References
The following links help figured out the needed components to make my lab environment work.
Sponsors
Recent Posts
Try to import module ActiveDirectory on a linux powershell
In my webpage I wanted to change the password of some accounts. So I got a script powershell. In this one I need to import the module Active-Directory to change the password of accounts. My server is on CentOS, so I install powershell on it. But when I do : Import-Module ActiveDirectory, the console return ‘Import-Module: The specified module ‘ActiveDirectory’ was not loaded because no valid module file was found in any module directory.’ Thanks
2 Answers 2
The short answer is. you can’t. The centos platform version of .net does not support the [System.DirectoryServices] types/classes yet, and I doubt they’ll be migrated over soon. Powershell’s ActiveDirectory module requires those to run, so this cannot currently be done in Powershell:
[System.DirectoryServices.ActiveDirectory.Domain]::GetCurrentDomain() MethodInvocationException: Exception calling "GetCurrentDomain" with "0" argument(s): "System.DirectoryServices is not supported on this platform." An alternative is using ldap commands from centos packages. Here’s some examples:
# Change a password that you already know - works with almost any configuration # You can provide the password from a file or as a parameter. By default it will prompt. # part of package samba-common-tools smbpasswd -U MyUsername -r ad.domain.tld Old SMB password: New SMB password: Retype new SMB password: Changing a password for an AD user when you don’t know the current one is more complicated and requires a much more specific configuration on your machine, but can be done with just passwd if:
- your centos machine is joined to the domain correctly
- you are using an admin account with write permission to AD
- You have sssd configured with chpass_provider=ad in \etc\sssd\sssd.conf
passwd DOMAIN\\SomeUsername Otherwise, the best option on linux is through python’s ldap module. I’m not as familiar with it, so I’m only linking working example code from a similar question: Modifying Active Directory Passwords via ldapmodify