An introduction to firewalld rules and scenarios
The firewall is a critical security component of your Linux system. See how to filter traffic with zones and rules.
A firewall is similar to a gatekeeper that prevents unwanted traffic from the outside network from reaching your system. The firewall rules decide which traffic to allow in or out. In Linux firewalls, there is a concept called zones. Sysadmins can configure each zone with its own firewall rules, which allow or deny incoming traffic into the system. Imagine a home security system that states which person should be allowed to visit which rooms inside your house.
Diagram via: Getting Started with firewalld (Red Hat Customer Portal)
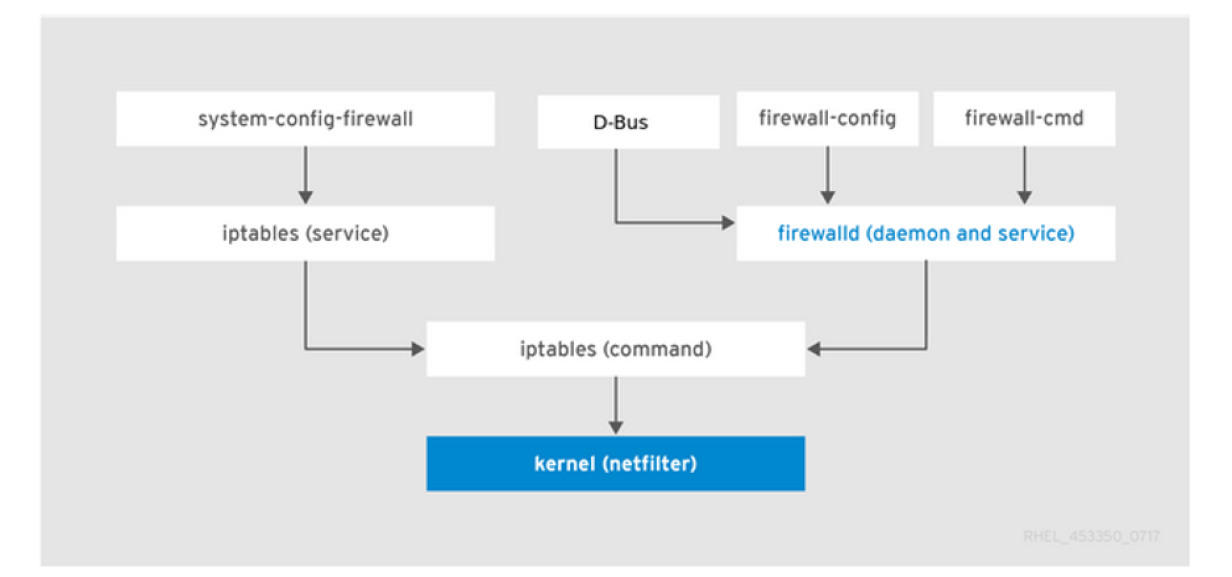
firewalld is a firewall service that provides a host-based customizable firewall via the D-bus interface. As mentioned above, firewalls use zones with a predefined set of rules, and each service uses ports. We can allow/block any incoming traffic to a particular service based on its port. For example, if you don’t want anyone to SSH into your system, you can block port 22, and this makes sure that no one can access your system from outside via SSH.
Linux security
Zones
The firewalld service uses a concept of zones. We can assign network interfaces to these zones and decide which kind of traffic can enter that network. We can use Network Manager to assign interfaces to particular zones using the firewall-cmd command, a widely known command-line tool. The default zones are stored under the /usr/lib/firewalld/zones/ directory. Now let’s learn about some of the pre-defined zones available in firewalld .
- Block: In this zone, any incoming connections are rejected with an icmp-host-prohibited message, and only connections initiated from within the system are allowed.
- DMZ: For systems that need limited internal network connections, it accepts only selected incoming connections. Also known as a demilitarized zone.
- Drop: Connections are dropped without any notifications. Outgoing connections are possible.
- Public: This zone is used for devices on the untrusted public network.
- Trusted: All network connections are accepted.
One of these zones can be set as default per the user’s needs. After the installation, the public zone is set as the default, which you can change later.
Firewall rules in Red Hat Enterprise Linux
Now that we know the basics of firewalld , we can explore how to use the commands to add or remove different services.
To view whether the firewall is running, use the following commands:
# systemctl status firewalld firewalld.service - firewalld - dynamic firewall daemon Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled) Active: active (running) since Fri 2020-11-13 18:19:05 CET; 4 months 4 days ago# firewall-cmd --state runningTo list the information about the default zone:
# firewall-cmd --list-all public (active) target: default icmp-block-inversion: no interfaces: baremetal cni-podman0 eno1 eno2 eno3 provisioning sources: services: cockpit dhcpv6-client http ssh ports: 8080/tcp 80/tcp 80/udp 67/udp 68/udp protocols: masquerade: no forward-ports: source-ports: icmp-blocks: rich rules:As you can see above, the public zone is set as default. The output displays the interfaces assigned to this zone and which services and ports are enabled/allowed.
# firewall-cmd --list-all --zone=home home target: default icmp-block-inversion: no interfaces: sources: services: cockpit dhcpv6-client mdns samba-client sshEnable/start the firewalld service upon system start:
# systemctl enable firewalld # systemctl start firewalldDisable/stop the firewalld service upon system start:
# systemctl disable firewalld # systemctl stop firewalldAdd ports and services to zones and make them permanent
Next, let’s see some of the commands to add new services and ports to a particular zone and make them permanent (remain even after system reboot).
To open up or block ports on firewalld use:
# firewall-cmd --list-ports # firewall-cmd --add-port --permanent # firewall-cmd --reloadPorts are logical devices that enable an operating system to receive incoming traffic and forward it to system services. Usually, those services listen on standard ports. For example, HTTP listens on port 80 and HTTPS listens on port 443.
Usually port-type means tcp , udp or sctp .
Next is an example that adds port 443 on the default zone permanently:
# firewall-cmd --add-port 443/tcp --zone=public --permanent # firewall-cmd --reloadWe can also remove the port by using —remove-port option.
Rich rules in firewalld
We can also use rich rules, which have some advanced filtering capabilities in firewalld . The syntax for these is below. These rich rules are helpful when we want to block or allow a particular IP address or address range.
Use the following command to display the current rich rule settings:
# firewall-cmd --list-rich-rulesWe can control a particular IP of the host and ports using rich rules.
The following rule accepts SSH connections only from the host with IP 10.1.111.21 and drops other connections:
# firewall-cmd --add-rich-rule='rule family=ipv4 source address=10.1.111.21/24 service name=ssh log prefix="SSH Logs" level="notice" accept'This example rejects ping requests from all hosts with an error message:
# firewall-cmd --add-rich-rule='rule protocol value=icmp reject'The following rule rejects requests coming from IP 172.92.10.90/32 port 21 and accepts every other connection:
# firewall-cmd --add-rich-rule='rule family=ipv4 source address=172.92.10.90/32 port port=21 protocol=tcp reject'Wrap up
Enabling firewalld lets the user allow or restrict incoming connections and selectively secure their system from unwanted network traffic. Remember that firewall rules decide which traffic to allow in or out of a system. You can configure a zone with its own firewall rules, which allows or denies incoming traffic into the system. But also remember that allowing any traffic or port access to your system makes it vulnerable to security breaches and potential attacks.
33.7. Настройка межсетевого экрана
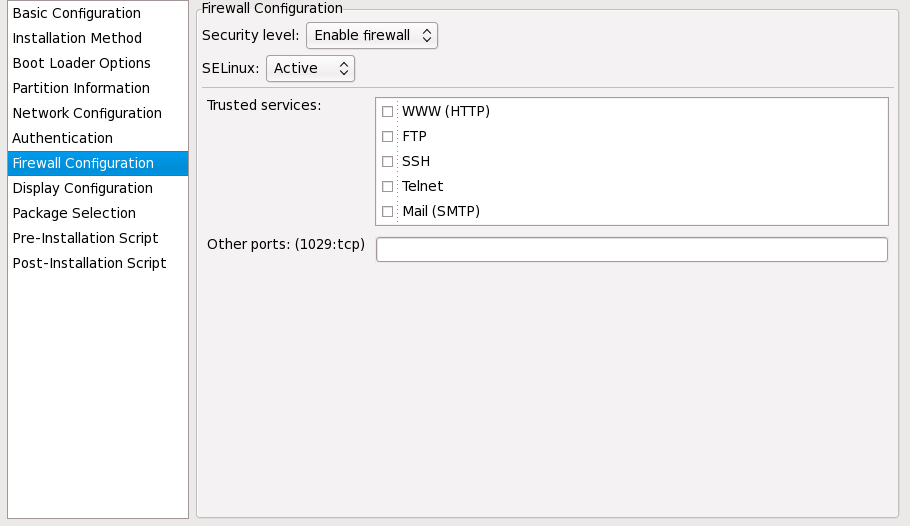
Окно настройки межсетевого экрана аналогично диалогу настройки программы установки и утилиты настройки уровня безопасности .
Рисунок 33.10. Настройка межсетевого экрана
Если межсетевой экран отключен, система открывает доступ к любым активным службам и портам. Внешние подключения к системе не отклоняются и не запрещаются.
Если межсетевой экран включен, система не будет принимать входящие пакеты, явно не определенные вами (за исключением разрешенных по умолчанию). По умолчанию разрешены только пакеты, отвечающие на исходящие запросы, например ответы DNS или DHCP-серверов. Если необходим доступ к службам, запущенным на этом компьютере, вы можете это разрешить.
В списке Доверенные устройства показаны устройства, настроенные в разделе Настройка сети . Система будет принимать соединения с любых устройств в этом списке. Например, если eth1 получает данные только от внутренних компьютеров, возможно, вы захотите разрешить подключения с этого устройства.
Если служба выбрана в списке Доверенные службы , система принимает и обрабатывает подключения к этой службе.
В текстовом поле Другие порты можно перечислить дополнительные порты, которые следует открыть для удаленного доступа. Используйте формат порт:протокол . Например, чтобы разрешить IMAP-доступ через экран, укажите imap:tcp . Также можно явно задать числовой номер порта; например, чтобы пропустить UDP-пакеты в через 1234, введите 1234:udp . Чтобы указать несколько портов, разделите их запятыми.
33.7.1. Настройка SELinux
При кикстарте может быть установлен принудительный (строгий) режим SELinux, режим предупреждений или выключен . Более тонкая конфигурация на данном этапе недоступна.