- What is a sticky Bit and how to set it in Linux?
- What is Sticky Bit?
- Learn Sticky Bit with examples:
- Some FAQ’s related to Sticky Bit:
- Surendra Anne
- Latest posts by Surendra Anne (see all)
- Linux permissions: SUID, SGID, and sticky bit
- Career advice
- Symbolic method
- Numeric method
- Special permission explained
- user + s (pecial)
- group + s (pecial)
- Great Linux resources
- other + t (sticky)
- Setting special permissions
- Summary
What is a sticky Bit and how to set it in Linux?
Today we will see how to set Sticky Bit in Linux. This is next to SGID in our ongoing File and Folder permissions series in Linux. We already discussed about CHMOD, UMASK, CHOWN, CHGRP, SGID and SUID file and folder permissions etc in our the previous posts. In this post we will see
- What is Sticky Bit?
- Why we require Sticky Bit?
- Where we are going to implement Sticky Bit?
- How to implement Sticky Bit in Linux?
What is Sticky Bit?
Sticky Bit is mainly used on folders in order to avoid deletion of a folder and it’s content by other users though they having write permissions on the folder contents. If Sticky bit is enabled on a folder, the folder contents are deleted by only owner who created them and the root user. No one else can delete other users data in this folder(Where sticky bit is set). This is a security measure to avoid deletion of critical folders and their content(sub-folders and files), though other users have full permissions.
Learn Sticky Bit with examples:
Example: Create a project(A folder) where people will try to dump files for sharing, but they should not delete the files created by other users.
How can I setup Sticky Bit for a Folder?
Sticky Bit can be set in two ways
- Symbolic way (t,represents sticky bit)
- Numerical/octal way (1, Sticky Bit bit as value 1)
Use chmod command to set Sticky Bit on Folder: /opt/dump/
Symbolic way:
chmod o+t /opt/dump/ or chmod +t /opt/dump/
Let me explain above command, We are setting Sticky Bit(+t) to folder /opt/dump by using chmod command.
Numerical way:
chmod 1757 /opt/dump/
Here in 1757, 1 indicates Sticky Bit set, 7 for full permissions for owner, 5 for read and execute permissions for group, and full permissions for others.
Checking if a folder is set with Sticky Bit or not?
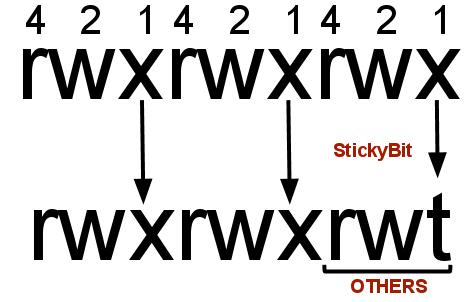
Use ls -l to check if the x in others permissions field is replaced by t or T
For example: /opt/dump/ listing before and after Sticky Bit set
Before Sticky Bit set:
-rwxr-xrwx 1 xyz xyzgroup 148 Dec 22 03:46 /opt/dump/
After Sticky Bit set:
ls -l total 8 -rwxr-xrwt 1 xyz xyzgroup 148 Dec 22 03:46 /opt/dump/
Some FAQ’s related to Sticky Bit:
Now sticky bit is set, let us check if user “temp” can delete this folder which is created xyz user.
$ rm -rf /opt/dump rm: cannot remove `/opt/dump': Operation not permitted $ ls -l /opt total 8 drwxrwxrwt 4 xyz xyzgroup 4096 2012-01-01 17:37 dump $
if you observe other user is unable to delete the folder /opt/dump. And now content in this folder such as files and folders can be deleted by their respective owners who created them. No one can delete other users data in this folder though they have full permissions.
I am seeing “T” ie Capital s in the file permissions, what’s that?
After setting Sticky Bit to a file/folder, if you see ‘T’ in the file permission area that indicates the file/folder does not have executable permissions for all users on that particular file/folder.
Sticky bit without Executable permissions:
so if you want executable permissions, Apply executable permissions to the file.
chmod o+x /opt/dump/
ls -l
command output:
-rwxr-xrwt 1 xyz xyzgroup 0 Dec 5 11:24 /opt/dump/
Sticky bit with Executable permissions:
you should see a smaller ‘t’ in the executable permission position.
How can I find all the Sticky Bit set files in Linux/Unix.
find / -perm +1000
The above find command will check all the files which is set with Sticky Bit bit(1000).
Can I set Sticky Bit for files?
Yes, but most of the time it’s not required.
How can I remove Sticky Bit bit on a file/folder?
chmod o-t /opt/dump/
Post your thoughts on this.
Surendra Anne
Mr Surendra Anne is from Vijayawada, Andhra Pradesh, India. He is a Linux/Open source supporter who believes in Hard work, A down to earth person, Likes to share knowledge with others, Loves dogs, Likes photography. He works as Devops Engineer with Taggle systems, an IOT automatic water metering company, Sydney . You can contact him at surendra (@) linuxnix dot com.
Latest posts by Surendra Anne (see all)
- Docker: How to copy files to/from docker container — June 30, 2020
- Anisble: ERROR! unexpected parameter type in action: Fix — June 29, 2020
- FREE: JOIN OUR DEVOPS TELEGRAM GROUPS — August 2, 2019
- Review: Whizlabs Practice Tests for AWS Certified Solutions Architect Professional (CSAP) — August 27, 2018
- How to use ohai/chef-shell to get node attributes — July 19, 2018
Linux permissions: SUID, SGID, and sticky bit
Getting permissions in Linux can sometimes be a ‘sticky’ situation. Learn how to set the appropriate permissions, even in special circumstances.
Linux permissions are a concept that every user becomes intimately familiar with early on in their development. We need to execute scripts, modify files, and run processes in order to administer systems effectively, but what happens when we see Permission denied? Do you know why we see this message? If you know the cause of the problem, do you know how to implement the solution?
Career advice
I will give a quick explanation of the various ways to calculate permissions, and then we will focus on the special permissions within Linux. If you want an in-depth look at the chmod command, check out this article from Sudoer Shashank Hegde, Linux permissions: An introduction to chmod.
The TL;DR is that there are two main ways of assigning permissions.
Symbolic method
The symbolic method uses the following syntax:
[tcarrigan@server ~]$ chmod WhoWhatWhich file | directory- Who — represents identities: u,g,o,a (user, group, other, all)
- What — represents actions: +, -, = (add, remove, set exact)
- Which — represents access levels: r, w, x (read, write, execute)
An example of this is if I want to add the read and write permissions to a file named test.txt for user and group, I use the following command:
[tcarrigan@server ~]$ chmod ug+rw test.txtFull disclosure, this is not my preferred method of assigning permissions, and if you would like more information around this method, I recommend your nearest search engine.
Numeric method
The numeric method is, in my experience, the best way to learn and practice permissions. It is based on the following syntax:
[tcarrigan@server ~]$ chmod ### file | directoryHere, from left to right, the character # represents an access level. There are three access levels—user, group, and others. To determine what each digit is, we use the following:
- Start at 0
- If the read permission should be set, add 4
- If the write permission should be set, add 2
- If the execute permission should be set, add 1
This is calculated on a per access level basis. Let’s interpret this permissions example:
The permissions are represented as 650. How did I arrive at those numbers?
To put this into the command syntax, it looks like this:
[tcarrigan@server ~]$ chmod 650 test.txtNow that you understand the basics of permission calculation in Linux, let’s look at the special permissions included in the OS.
Special permission explained
Special permissions make up a fourth access level in addition to user, group, and other. Special permissions allow for additional privileges over the standard permission sets (as the name suggests). There is a special permission option for each access level discussed previously. Let’s take a look at each one individually, beginning with Set UID:
user + s (pecial)
Commonly noted as SUID, the special permission for the user access level has a single function: A file with SUID always executes as the user who owns the file, regardless of the user passing the command. If the file owner doesn’t have execute permissions, then use an uppercase S here.
Now, to see this in a practical light, let’s look at the /usr/bin/passwd command. This command, by default, has the SUID permission set:
[tcarrigan@server ~]$ ls -l /usr/bin/passwd -rwsr-xr-x. 1 root root 33544 Dec 13 2019 /usr/bin/passwdNote the s where x would usually indicate execute permissions for the user.
group + s (pecial)
Commonly noted as SGID, this special permission has a couple of functions:
- If set on a file, it allows the file to be executed as the group that owns the file (similar to SUID)
- If set on a directory, any files created in the directory will have their group ownership set to that of the directory owner
[tcarrigan@server article_submissions]$ ls -l total 0 drwxrws---. 2 tcarrigan tcarrigan 69 Apr 7 11:31 my_articlesGreat Linux resources
This permission set is noted by a lowercase s where the x would normally indicate execute privileges for the group. It is also especially useful for directories that are often used in collaborative efforts between members of a group. Any member of the group can access any new file. This applies to the execution of files, as well. SGID is very powerful when utilized properly.
As noted previously for SUID, if the owning group does not have execute permissions, then an uppercase S is used.
other + t (sticky)
The last special permission has been dubbed the «sticky bit.» This permission does not affect individual files. However, at the directory level, it restricts file deletion. Only the owner (and root) of a file can remove the file within that directory. A common example of this is the /tmp directory:
[tcarrigan@server article_submissions]$ ls -ld /tmp/ drwxrwxrwt. 15 root root 4096 Sep 22 15:28 /tmp/The permission set is noted by the lowercase t, where the x would normally indicate the execute privilege.
Setting special permissions
To set special permissions on a file or directory, you can utilize either of the two methods outlined for standard permissions above: Symbolic or numerical.
Let’s assume that we want to set SGID on the directory community_content .
To do this using the symbolic method, we do the following:
[tcarrigan@server article_submissions]$ chmod g+s community_content/Using the numerical method, we need to pass a fourth, preceding digit in our chmod command. The digit used is calculated similarly to the standard permission digits:
[tcarrigan@server ~]$ chmod X### file | directoryWhere X is the special permissions digit.
Here is the command to set SGID on community_content using the numerical method:
[tcarrigan@server article_submissions]$ chmod 2770 community_content/ [tcarrigan@server article_submissions]$ ls -ld community_content/ drwxrws---. 2 tcarrigan tcarrigan 113 Apr 7 11:32 community_content/Summary
In closing, permissions are fundamentally important to being an effective Linux administrator. There are two defined ways to set permissions using the chmod command: Symbolic and numerical. We examined the syntax and calculations required for both methods. We also considered the special permissions and their role in the system. Now that you understand permissions and the underlying concepts, you can solve the ever-annoying Permission denied error when it tries to impede your work.