Linux «show mac-address-table» analogue
Few days ago I could see a user question about Linux analogue for Cisco «show mac-address-table» command. He wo'nt use the «arp»or «arp -a» command for some hidden reasons. And I think it may be interesting for other users.
The «arp» or «arp -a» command shows you mac-address table (MAC-interface maping) and ARP table (MAC-IP mapping) all-in-one. Cisco IOS devices, as networking equipment, show some more information and it contains VLAN id and entry type (static or dynamic).
Cisco output are below:
#sh mac address-table
Mac Address Table
——————————————-
Vlan Mac Address Type Ports
—- ———— ——— ——
All 0100.0ccc.cccc STATIC CPU
All 0100.0ccc.cccd STATIC CPU
All ffff.ffff.ffff STATIC CPU
10 0000.0c07.abcd DYNAMIC Gi0/1
20 000b.be68.bcde DYNAMIC Gi0/2
30 0013.6016.cdef DYNAMIC Gi0/3
Total Mac Addresses for this criterion: 67
#sh ip arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 10.100.10.11 0 3c4a.92b2.abcd ARPA Vlan10
Internet 10.100.20.28 162 b4b5.2fab.bcde ARPA Vlan20
But Linux «arp» and «arp -a» commands show us some another information:
# arp
Address HWtype HWaddress Flags Mask Iface
192.168.10.1 ether 00:50:56:c0:00:08 C eth0
192.168.10.2 ether 00:50:56:f2:83:0a C eth0
# arp -a
? (192.168.10.1) at 00:50:56:c0:00:08 [ether] on eth0
? (192.168.10.2) at 00:50:56:f2:83:0a [ether] on eth0
So you can see both ARP and MAC-address table in one output. It is not so rich as Cisco output but it is good enough.
But if you think that the «arp» output contains a lot of extra information you may parse it with «awk» command:
# arp | grep -v Address | awk ' < print $3,$5 >'
00:50:56:c0:00:08 eth0
00:50:56:f2:83:0a eth0
- install bridge-utils,
- set the bridge,
- add interfaces to the bridge
- use «brctl showmacs» command
# brctl addbr 1
# brctl addif 1 eth0
# brctl showmacs 1
port no mac addr is local? ageing timer
1 00:0c:29:1f:cf:5a yes 0.00
1 00:50:56:c0:00:08 no 0.00
So I hope this information may be interesting and useful.
Как удалить свой ЦИФРОВОЙ СЛЕД в интернете? Подпишитесь на наш ТГ канал и обретите свою цифровую свободу.
Using MAC table – Linux Bridge – WILT
In an earlier blog, I have talked about Linux bridge based virtual networking. Recently as part of a comment on my blog, I learnt how to view and interpret the MAC table of Linux bridge. In this installment of WILT (What I Learnt Today) series, I will share how MAC Table can be used for troubleshooting Linux bridges.
MAC Table — Background
Bridges and Switches forward packets by examining and learning MAC address from incoming packets. Linux bridges are no different from their hardware counterparts. And looking at the MAC table learnt by Linux bridges can provide useful insight into the flow of packets.
In cloud platforms like OpenStack, virtual machines (VMs) started by different tenants may get scheduled on the same hardware server. It follows that these VMs will share the resources on that server including the network ports. Let us consider a scenario where Linux bridge is used for virtual networking (as Mechanism driver in OpenStack). Now if there was a problem with one of the network ports on a server, it will be good to know which VMs are impacted by it.
Since multiple Linux bridges may be present, one of the best ways to find out the affected VMs for a given physical network port, is by looking at the MAC table of the Linux bridge that is bound to the failed network port.
Interpreting MAC Table — Step-by-Step guide
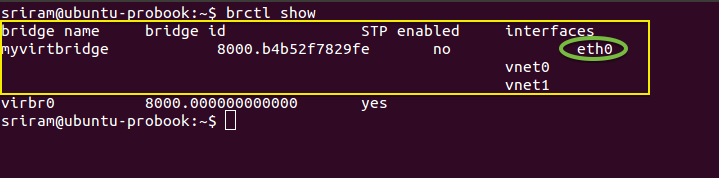
Step 1: If you have detected that eth0 interface is having a problem, then using brctl show command you can list all the bridges and identify the Linux bridge bound to eth0.
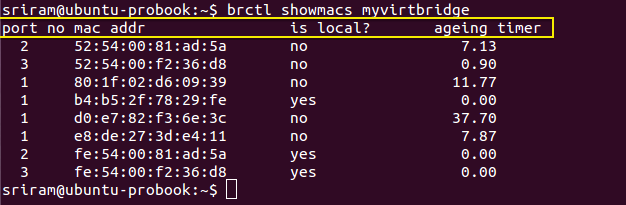
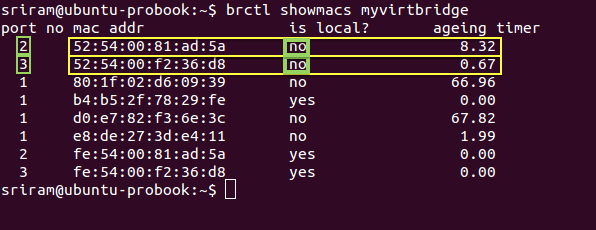
Step 2: Next execute the command brctl showmacs with the bridge you identified in Step 1 to view the MAC table. In the output, each row represents MAC address learnt at each port of the Linux bridge. The important columns in the output are ‘is local?’, ‘port no’ and ‘mac addr’.
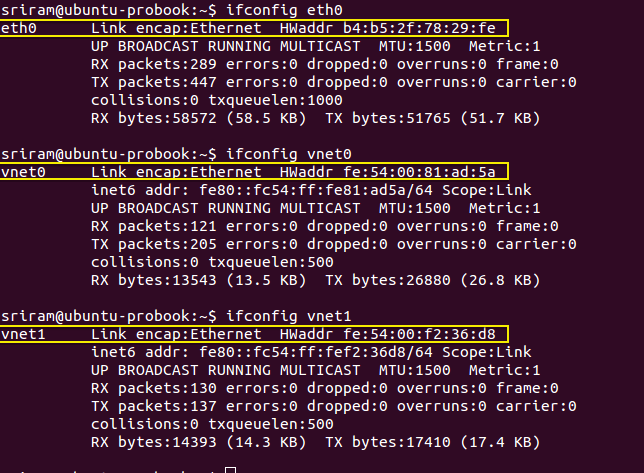
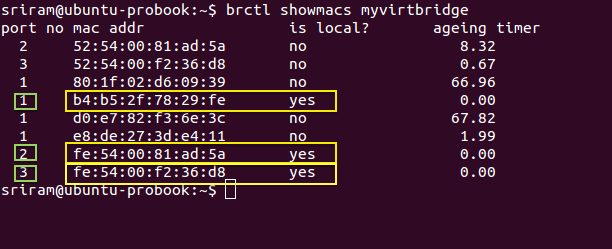
Step 3: When a row (or MAC address) has ‘is local’ as Y (means Yes), then it represents the MAC address of an interface directly on the Linux Bridge**. **You can confirm this with the MAC address of _eth0 _which is bound to the Linux bridge (myvirtbridge in the screenshot below). The other interfaces with ‘is local’ as Yes are the tap interfaces directly on the Linux bridge. Make a note of the ‘port no’ for these tap interface MAC addresses (where ‘is local’ is Yes).
In this example, Port Number 1 belongs to the eth0 interface. And Ports 2 and 3 represent the Tap interfaces on the Linux bridge (myvirtbridge).
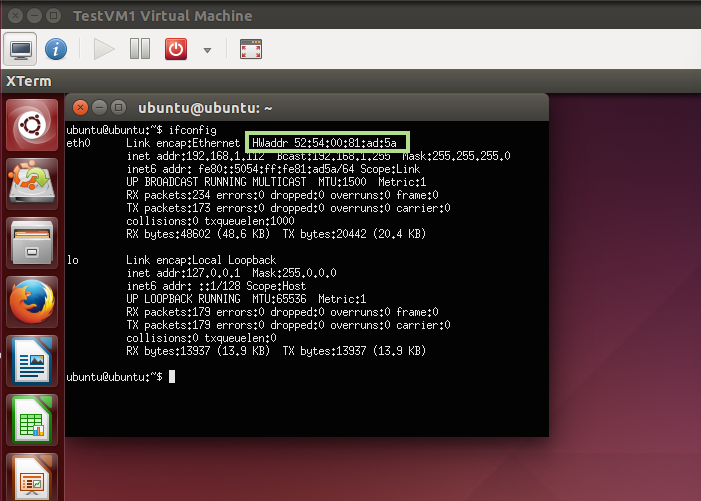
Step 4: For each port number with a ‘is local’ as Yes, you will find another entry in the MAC table with the same port number but with ‘is local’ as No. These entries with ‘is local’ as No represents the MAC address _learnt _from the incoming packets. Since we are looking at Port number for tap interfaces, the remote entities that are sending these packets are basically the virtual interfaces inside virtual machines. In the picture below, for Local port 2, the non-local (remote) MAC address is ‘52:54:00:81:ad:5a’. This will be the MAC address of a virtual NIC of a VM. Similarly for local port 3.
Step 5: There are two ways to confirm that the remote MAC addresses belong to VMs.
- You can use the _ps -ef _ command and grep for these remote MAC addresses.
- Or you can login into the VMs and try the ifconfig command _inside _the VM.
Conclusion: As seen in the step by step guide, understanding MAC table output provides useful insights into the flow of packets in a Linux bridge. It can be a useful tool in troubleshooting networking problems (in addition to other tools).
Andrey Dugin @blog
Пару дней назад я увидел в Интернете вопрос о том, какой в Linux существует аналог команды Cisco IOS «show mac-address-table». При этом пользователь категорически не хотел пользоваться командой «arp» либо «arp -a». То ли с целью парсинга и вывода на третьи системы, то ли еще из каких побуждений. Естестенно, мне стало интересно, и свой вариант я опишу в этой, так сказать, «статье».
Команда Linux CLI «arp» либо «arp -a» показывает по принципу «два в одном»: и ARP-таблицу (соответствие MAC и IP-адресов), так и часть таблицы MAC-адресов (соответствие MAC-адреса интерфейсу, на котором он виден). Естественно, Cisco, как сетевое устройство, имеет чуть больше функций и содержит тип записи в таблице MAC-адресов (static, dynamic) и номер VLAN.
Vlan Mac Address Type Ports
—- ———— ——— ——
All 0100.0ccc.cccc STATIC CPU
All 0100.0ccc.cccd STATIC CPU
All ffff.ffff.ffff STATIC CPU
10 0000.0c07.abcd DYNAMIC Gi0/1
20 000b.be68.bcde DYNAMIC Gi0/2
30 0013.6016.cdef DYNAMIC Gi0/3
Total Mac Addresses for this criterion: 67
#sh ip arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 10.100.10.11 0 3c4a.92b2.abcd ARPA Vlan10
Internet 10.100.20.28 162 b4b5.2fab.bcde ARPA Vlan20
Вот таким образом выглядит вывод команд «arp» и ‘arp -a» в Linux:
# arp
Address HWtype HWaddress Flags Mask Iface
192.168.10.1 ether 00:50:56:c0:00:08 C eth0
192.168.10.2 ether 00:50:56:f2:83:0a C eth0
# arp -a
? (192.168.10.1) at 00:50:56:c0:00:08 [ether] on eth0
? (192.168.10.2) at 00:50:56:f2:83:0a [ether] on eth0
То есть, как бы и ARP-таблица, и таблица MAC-адресов одновременно. Не столь богато, как в Cisco, но все же.
Если же подобный вывод является избыточным, можно довольно просто распарсить его, оставив только интерфейс и MAC, перенаправив вывод в awk:
# arp | grep -v Address | awk ‘ < print $3,$5 >‘
00:50:56:c0:00:08 eth0
00:50:56:f2:83:0a eth0
В случае ненависти или индивидуальной непереносимости команд «arp» и/или «awk», можно пойти другим путем:
- установить bridge-utils;
- создать бридж;
- добавить на бридж интерфейс;
- использовать команду » brctl showmacs «
Полагаю, таким образом ответ на вопрос можно считать если не исчерпывающим, то, как минимум, содержащим приемлемые варианты.
Andrey Dugin @blog
Few days ago I could see a user question about Linux analogue for Cisco «show mac-address-table» command. He wo’nt use the «arp»or «arp -a» command for some hidden reasons. And I think it may be interesting for other users.
The «arp» or «arp -a» command shows you mac-address table (MAC-interface maping) and ARP table (MAC-IP mapping) all-in-one. Cisco IOS devices, as networking equipment, show some more information and it contains VLAN id and entry type (static or dynamic).
Cisco output are below:
#sh mac address-table
Mac Address Table
——————————————-
Vlan Mac Address Type Ports
—- ———— ——— ——
All 0100.0ccc.cccc STATIC CPU
All 0100.0ccc.cccd STATIC CPU
All ffff.ffff.ffff STATIC CPU
10 0000.0c07.abcd DYNAMIC Gi0/1
20 000b.be68.bcde DYNAMIC Gi0/2
30 0013.6016.cdef DYNAMIC Gi0/3
Total Mac Addresses for this criterion: 67
#sh ip arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 10.100.10.11 0 3c4a.92b2.abcd ARPA Vlan10
Internet 10.100.20.28 162 b4b5.2fab.bcde ARPA Vlan20
But Linux «arp» and «arp -a» commands show us some another information:
# arp
Address HWtype HWaddress Flags Mask Iface
192.168.10.1 ether 00:50:56:c0:00:08 C eth0
192.168.10.2 ether 00:50:56:f2:83:0a C eth0
# arp -a
? (192.168.10.1) at 00:50:56:c0:00:08 [ether] on eth0
? (192.168.10.2) at 00:50:56:f2:83:0a [ether] on eth0
So you can see both ARP and MAC-address table in one output. It is not so rich as Cisco output but it is good enough.
But if you think that the «arp» output contains a lot of extra information you may parse it with «awk» command:
# arp | grep -v Address | awk ‘ < print $3,$5 >‘
00:50:56:c0:00:08 eth0
00:50:56:f2:83:0a eth0
- install bridge-utils,
- set the bridge,
- add interfaces to the bridge
- use «brctl showmacs» command
# brctl addbr 1
# brctl addif 1 eth0
# brctl showmacs 1
port no mac addr is local? ageing timer
1 00:0c:29:1f:cf:5a yes 0.00
1 00:50:56:c0:00:08 no 0.00
So I hope this information may be interesting and useful.