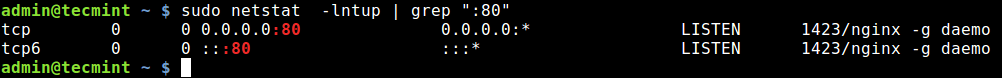- 4 Ways to Find Out What Ports Are Listening in Linux
- Using netstat Command
- Using lsof Command
- Using ss Command
- Using nmap Command
- Using the fuser Command
- Using the lshw Command
- Using the iptables Command
- Conclusion
- 4 Ways to Find Out What Ports Are Listening in Linux
- 1. Using Netstat Command
- 2. Using ss Command
- 3. Using Nmap Command
- 4. Using lsof Command
- How to find ports opened by process ID in Linux?
- -p (Linux):
4 Ways to Find Out What Ports Are Listening in Linux
Linux is a popular operating system that is widely used by system administrators, developers, and other tech enthusiasts. One of important tasks in managing a Linux system is to identify which ports are being used and which ones are available. In this article, we will discuss 4 ways to find out what ports are listening in Linux.
Using netstat Command
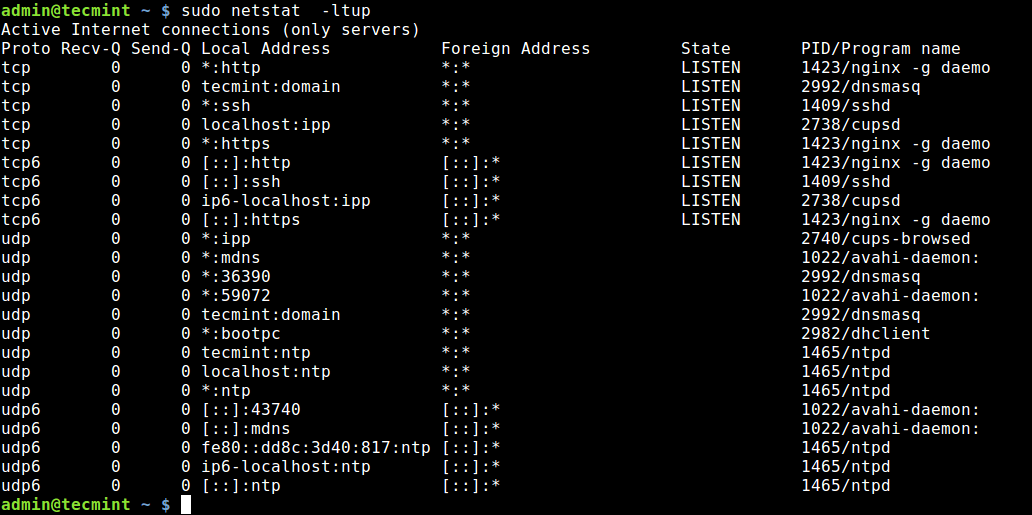
The netstat command is a powerful tool that provides detailed information about network connections, routing tables, and other related statistics. To check which ports are listening, you can use following command −
This command will display a list of all ports that are currently listening on system. «-l» option tells netstat to only show listening sockets, «-t» specifies TCP connections, and «-n» displays port numbers instead of resolving them to names.
Here is an example output −
Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN
The output shows that SSH daemon is listening on port 22 and CUPS printing service is listening on port 631.
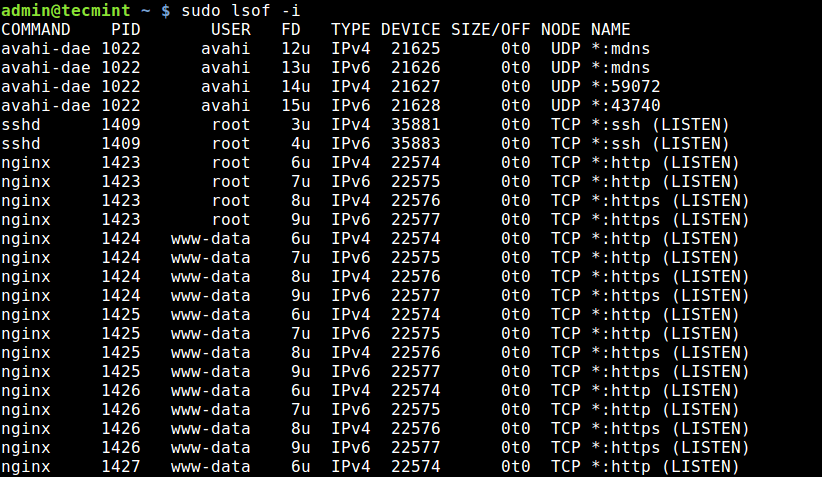
Using lsof Command
The lsof command (short for «list open files») is a powerful tool that can be used to list all open files and network connections on a Linux system. To find out which ports are listening, you can use following command −
$ sudo lsof -i -P -n | grep LISTEN
This command will display a list of all open network connections on system that are in a listening state. «-i» option specifies that we are interested in network connections, «-P» tells lsof to use port numbers instead of service names, and «-n» disables hostname resolution.
Here is an example output −
sshd 2269 root 3u IPv4 11758 0t0 TCP *:22 (LISTEN) cupsd 2889 root 7u IPv4 16314 0t0 TCP 127.0.0.1:631 (LISTEN)
The output shows that SSH daemon is listening on port 22 and CUPS printing service is listening on port 631.
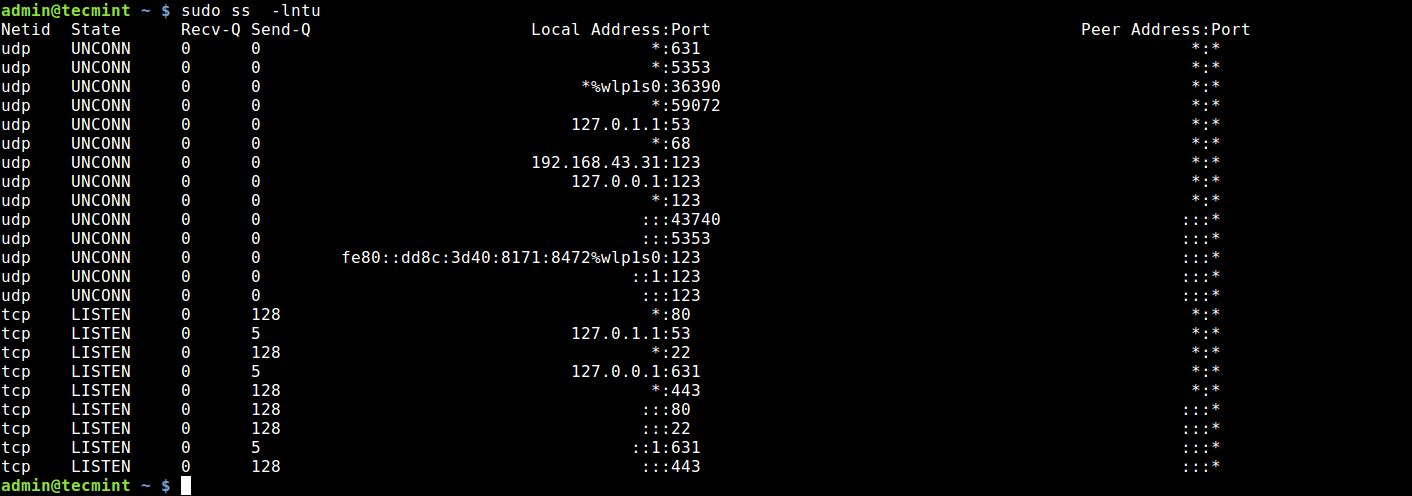
Using ss Command
The ss command is a modern replacement for netstat command and provides similar functionality. To check which ports are listening, you can use following command −
This command will display a list of all TCP ports that are currently listening on system. «-l» option tells ss to only show listening sockets, «-t» specifies TCP connections, and «-n» displays port numbers instead of resolving them to names.
Here is an example output −
State Recv-Q Send-Q Local Address:Port Peer Address:Port LISTEN 0 128 *:22 *:* LISTEN 0 5 127.0.0.1:631 *:*
The output shows that SSH daemon is listening on port 22 and CUPS printing service is listening on port 631.
Using nmap Command
The nmap command is a powerful tool that can be used for network exploration, security scanning, and port scanning. To check which ports are listening on a remote system, you can use following command −
This command will perform a TCP SYN scan on all ports on remote system and report which ports are open and listening. «-sS» option tells nmap to use a SYN scan, which is a stealthy scanning technique that can evade some network intrusion detection systems. «-p-» option tells nmap to scan all 65535 ports on system.
Here is an example output −
Starting Nmap 7.60 ( https://nmap.org ) at 2023-03-23 10:00 PDT Nmap scan report for Host is up (0.035s latency). Not shown: 65534 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 443/tcp open https
The output shows that remote system has ports 22, 80, and 443 open and listening.
Using the fuser Command
The fuser command is a simple utility that identifies processes using a particular file, directory, or socket. To check which ports are listening using the fuser command, use the following command −
$ sudo fuser -n tcp -v 1-65535
This command will display all processes using TCP ports 1 to 65535. Let’s break down the options used in the command −
-n tcp tells fuser to only display TCP connections
-v tells fuser to display more verbose output
The output of the fuser command will display a list of processes using TCP ports, along with their respective PIDs.
Using the lshw Command
The lshw command is a hardware information utility that can also be used to display network information, including open ports. To check which ports are listening using the lshw command, use the following command −
$ sudo lshw -class network -short
This command will display a list of network devices on your system, along with their respective drivers and open ports.
Using the iptables Command
The iptables command is a powerful firewall utility that can be used to display and manipulate firewall rules, including open ports. To check which ports are listening using the iptables command, use the following command −
This command will display the current firewall rules on your system, including any open ports that are allowed through the firewall.
Conclusion
Identifying which ports are listening on a Linux system is an important task for system administrators, developers, and security professionals. In this article, we discussed 4 ways to find out what ports are listening in Linux: using netstat command, using lsof command, using ss command, and using nmap command. Each of these methods has its own strengths and weaknesses, and you should choose one that best fits your needs. With these tools in your arsenal, you can better manage your Linux system and keep it secure.
4 Ways to Find Out What Ports Are Listening in Linux
The state of a port is either open, filtered, closed, or unfiltered. A port is said to be open if an application on the target machine is listening for connections/packets on that port.
In this article, we will explain four ways to check open ports and also will show you how to find which application is listening on what port in Linux.
1. Using Netstat Command
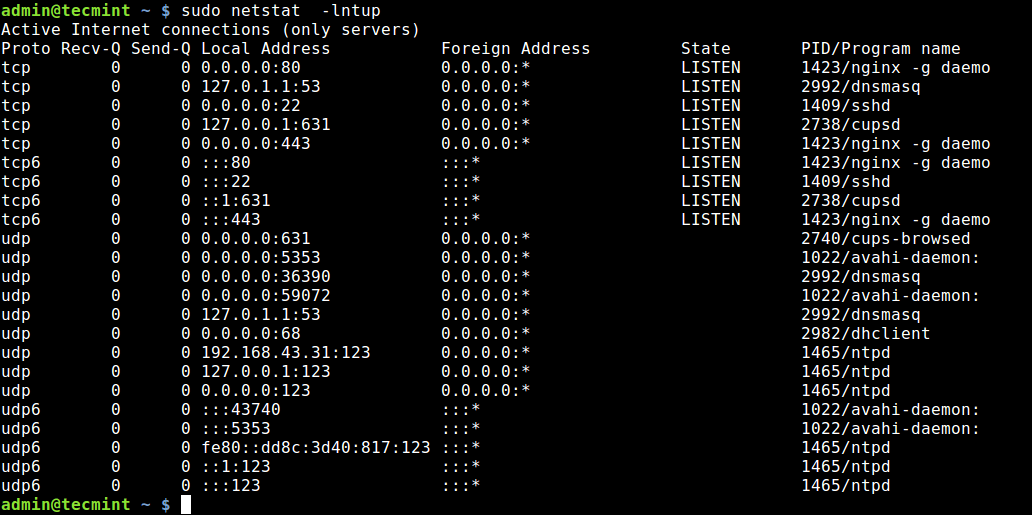
Netstat is a widely used tool for querying information about the Linux networking subsystem. You can use it to print all open ports like this:
The flag -l tells netstat to print all listening sockets, -t shows all TCP connections, -u displays all UDP connections and -p enables printing of application/program name listening on the port.
To print numeric values rather than service names, add the -n flag.
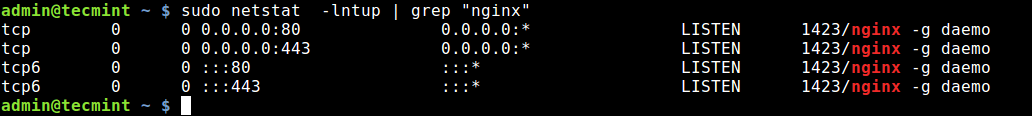
You can also use grep command to find out which application is listening on a particular port, for example.
$ sudo netstat -lntup | grep "nginx"
Alternatively, you can specify the port and find the application bound to, as shown.
$ sudo netstat -lntup | grep ":80"
2. Using ss Command
ss command is another useful tool for displaying information about sockets. It’s output looks similar to that of netstat. The following command will show all listening ports for TCP and UDP connections in numeric value.
3. Using Nmap Command
Nmap is a powerful and popular network exploration tool and port scanner. To install nmap on your system, use your default package manager as shown.
$ sudo apt install nmap [On Debian/Ubuntu] $ sudo yum install nmap [On CentOS/RHEL] $ sudo dnf install nmap [On Fedora 22+]
To scan all open/listening ports in your Linux system, run the following command (which should take a long time to complete).
$ sudo nmap -n -PN -sT -sU -p- localhost
4. Using lsof Command
The final tool we will cover for querying open ports is lsof command, which is used to list open files in Linux. Since everything is a file in Unix/Linux, an open file may be a stream or a network file.
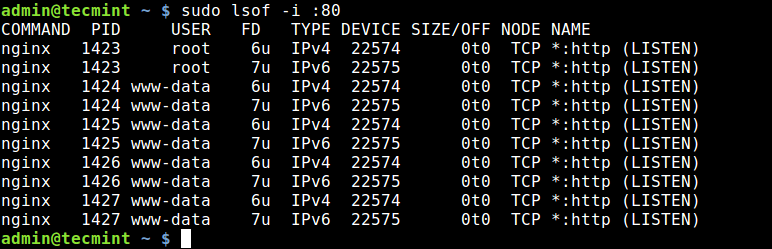
To list all Internet and network files, use the -i option. Note that this command shows a mix of service names and numeric ports.
To find which application is listening on a particular port, run lsof in this form.
That’s all! In this article, we have explained four ways to check open ports in Linux. We also showed how to check which processes are bound upon particular ports. You can share your thoughts or ask any questions via the feedback form below.
How to find ports opened by process ID in Linux?
Hmm..I don’t seem to have the —all and —program options. I’m using OSX. Brew doesn’t seem to have a formula for it either.
-n will dramatically speed things up by not resolving hostnames. netsta -tupan is a good default command all and easy to remember.
You can use the command below:
As a side note, netstat -ao will read the /proc/PID/tcp etc to see the ports opened by the process. This means that its reading information supplied by the system (the linux KERNEL), and is in no way directly looking on the network interface or other means. Same goes for lsof.
If you are doing this as a security measure, you failed. You should never (NEVER EVER) trust the output of netstat, even if you are 100% sure you are in fact running a real netstat program (as opposed to a trojaned version) or any other program that reads the /proc filesystem. Some people seem to think that netstat, ls, ps or any other of the standard unix tools do some sort of magic and poll information from the sources, the truth is all of them rely on the /proc filesystem to get all of their data, which can be easily subverted by a rootkit or hypervisor.
If you’re dealing with a rootkitted system or a compromised hypervisor, you can’t trust anything, including something that purports to look directly at the network interface.
You can use the netstat command line tool with the -p command line argument:
-p (Linux):
Process: Show which processes are using which sockets (similar to -b under Windows). You must be root to do this.
To display all ports open by a process with id $PID :
In some embedded devices or with old version of Linux, the problem is netstat do not have —process or -p options available.
The following script shows process with its IP and port, you must be root.
#!/bin/bash for protocol in tcp udp ; do #echo "protocol $protocol" ; for ipportinode in `cat /proc/net/$ | awk '/.*:.*:.*/'` ; do #echo "#ipportinode=$ipportinode" inode=`echo "$ipportinode" | cut -d"|" -f3` ; if [ "#$inode" = "#" ] ; then continue ; fi lspid=`ls -l /proc/*/fd/* 2>/dev/null | grep "socket:\[$inode\]" 2>/dev/null` ; pid=`echo "lspid=$lspid" | awk 'BEGIN /socket/'` ; if [ "#$pid" = "#" ] ; then continue ; fi exefile=`ls -l /proc/$pid/exe | awk 'BEGIN ">/->/'` #echo "$protocol|$pid|$ipportinode" echo "$protocol|$pid|$ipportinode|$exefile" | awk ' BEGIN function iphex2dec(ipport) < ret=sprintf("%d.%d.%d.%d: %d","0x"substr(ipport,1,2),"0x"substr(ipport,3,2), "0x"substr(ipport,5,2),"0x"substr(ipport,7,2),"0x"substr(ipport,10,4)) ; if( ret == "0.0.0.0:0" ) #compatibility others awk versions < ret= strtonum("0x"substr(ipport,1,2)) ; ret=ret "." strtonum("0x"substr(ipport,3,2)) ; ret=ret "." strtonum("0x"substr(ipport,5,2)) ; ret=ret "." strtonum("0x"substr(ipport,7,2)) ; ret=ret ":" strtonum("0x"substr(ipport,10)) ; >return ret ; > < print $1" pid:"$2" local="iphex2dec($3)" remote="iphex2dec($4)" inode:"$5" exe=" $6 ; >' ; #ls -l /proc/$pid/exe ; done ; done tcp pid:1454 local=1.0.0.127:5939 remote=0.0.0.0:0 inode:13955 exe=/opt/teamviewer/tv_bin/teamviewerd tcp pid:1468 local=1.1.0.127:53 remote=0.0.0.0:0 inode:12757 exe=/usr/sbin/dnsmasq tcp pid:1292 local=0.0.0.0:22 remote=0.0.0.0:0 inode:12599 exe=/usr/sbin/sshd tcp pid:4361 local=1.0.0.127:631 remote=0.0.0.0:0 inode:30576 exe=/usr/sbin/cupsd tcp pid:1375 local=1.0.0.127:5432 remote=0.0.0.0:0 inode:12650 exe=/usr/lib/postgresql/9.3/bin/postgres With ls you can know the process route.
The fuser command says that the process is: 2054
I’ve added IPv6 support and made a few fixes. Additionally on my system the octets of the IP address are reversed. Dependencies are only to posix shell, awk and cut.
My Version can be found on Github
#!/bin/sh # prints all open ports from /proc/net/* # # for pretty output (if available) start with # ./linux-get-programm-to-port.sh | column -t -s $'\t' #set -x ip4hex2dec () < local ip4_1octet="0x$" local ip4_2octet="$" ip4_2octet="0x$" local ip4_3octet="$" ip4_3octet="0x$" local ip4_4octet="$" ip4_4octet="0x$" local ip4_port="0x$" # if not used inverse #printf "%d.%d.%d.%d:%d" "$ip4_1octet" "$ip4_2octet" "$ip4_3octet" "$ip4_4octet" "$ip4_port" printf "%d.%d.%d.%d:%d" "$ip4_4octet" "$ip4_3octet" "$ip4_2octet" "$ip4_1octet" "$ip4_port" > # reoder bytes, byte4 is byte1 byte2 is byte3 . reorderByte() < if [ $-ne 8 ]; then echo "missuse of function reorderByte"; exit; fi local byte1="$" local byte2="$" byte2="$" local byte3="$" byte3="$" local byte4="$" echo "$byte4$byte3:$byte2$byte1" > # on normal intel platform the byte order of the ipv6 address in /proc/net/*6 has to be reordered. ip6hex2dec()< local ip_str="$" local ip6_port="0x$" local ipv6="$(reorderByte $)" local shiftmask="$" ipv6="$ipv6:$(reorderByte $)" shiftmask="$" ipv6="$ipv6:$(reorderByte $)" ipv6="$ipv6:$(reorderByte $)" ipv6=$(echo $ipv6 | awk '< gsub(/(:0|^0)/, ":"); sub(/(:0)+:/, "::");print>') printf "%s:%d" "$ipv6" "$ip6_port" > for protocol in tcp tcp6 udp udp6 raw raw6; do #echo "protocol $protocol" ; for ipportinode in `cat /proc/net/$protocol | awk '/.*:.*:.*/'` ; do #echo "#ipportinode=$ipportinode" inode=$ if [ "#$inode" = "#" ] ; then continue ; fi lspid=`ls -l /proc/*/fd/* 2>/dev/null | grep "socket:\[$inode\]" 2>/dev/null` ; pids=`echo "$lspid" | awk 'BEGIN /socket/ END>'` ; # removes duplicats for this pid #echo "#lspid:$lspid #pids:$pids" for pid in $pids; do if [ "#$pid" = "#" ] ; then continue ; fi exefile=`ls -l /proc/$pid/exe | awk 'BEGIN ">/->/'`; cmdline=`cat /proc/$pid/cmdline` local_adr_hex=$ remote_adr_hex=$ remote_adr_hex=$ if [ "#$" = "#6" ]; then local_adr=$(ip6hex2dec $local_adr_hex) remote_adr=$(ip6hex2dec $remote_adr_hex) else local_adr=$(ip4hex2dec $local_adr_hex) remote_adr=$(ip4hex2dec $remote_adr_hex) fi echo "$protocol pid:$pid \t$local_adr \t$remote_adr \tinode:$inode \t$exefile $cmdline" done done done