- How to automate SSH login with password?
- 9 Answers 9
- sshpass
- Anonymous pipe (recommended by sshpass)
- Environment variable
- Command-line argument (least secure)
- Side note
- SSH public key authentication
- Setup the SSH authentication agent
- How to Pass Password to SSH Command in Linux
- Connecting to Linux Server Using SSH
- Install SSHPass in Linux – A SSH Password Provider
- How to Add Password to SSH Command in Linux
- How to specify password in ssh command
- 2 Answers 2
How to automate SSH login with password?
This doesn’t work. I remember I did this with some tricks somebody guided me, but I can’t remember now the trick I used.
FreeBSD did not accept password-less keys. Don’t be tempted. However some Linux servers accepted it. I believe the Linux server was misconfigured.
This is a valid question. For example, I want to allow a user to enter a password, then login in to another machine using it. I can’t assume that there will be ssh keys distributed across all our machines. The answers below so far do not help this situation.
Very important question. I need an answer too, my webspace provider blocks to put keyfiles on the server, so I must pass the passwort without keyfiles.
Here is a purely bash answer, — file starts — #!/bin/bash [[ $1 =~ password: ]] && cat || SSH_ASKPASS=»$0″ DISPLAY=nothing:0 exec setsid «$@» — file ends— Save it as pass, do a chmod +x pass and then use it like this: $ echo mypass | ./pass ssh user@host
9 Answers 9
Don’t use a password. Generate a passphrase-less SSH key and push it to your VM.
If you already have an SSH key, you can skip this step… Just hit Enter for the key and both passphrases:
$ ssh-keygen -t rsa -b 2048 Generating public/private rsa key pair. Enter file in which to save the key (/home/username/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/username/.ssh/id_rsa. Your public key has been saved in /home/username/.ssh/id_rsa.pub. Copy your keys to the target server:
$ ssh-copy-id id@server id@server's password: Now try logging into the machine, with ssh ‘id@server’ , and check-in:
Note: If you don’t have .ssh dir and authorized_keys file, you need to create it first
to make sure we haven’t added extra keys that you weren’t expecting.
You may also want to look into using ssh-agent if you want to try keeping your keys protected with a passphrase.
These kinds of answers really, really annoy me. That wasn’t the question. Nobody asked how to use key pairs.
This does not answer the question. It is a good answer for a completely different question, but it is terrible for the one asked.
$ sudo apt-get install sshpass $ sshpass -p your_password ssh user@hostname Yup, sometimes you can’t use key based auth for various reasons.. for example right now I can’t use keyauth on a plesk server because out the box it’s not enabled and I don’t have root.
+1! As a side note, you need to run plain ssh once before using sshpass , in order to confirm the RSA fingerprint
-1 for having to use the password in the command. This logs the password at .bash_history in plain text on your machine.
Pro tip: If you don’t want to have a specific command show up in .bash_history, prefix the command with a space. It just works. However, users of this command should be more concerned that non-privileged users on the system can see the full command-line with ps, which, of course, includes the password. Since ssh sessions tend to be long-lived, this is a security issue.
While the correct answer for your question is sshpass (see other answer for details), there is a more secure way — SSH keys. You are just three easy steps away from the solution:
All the following commands are being run on the client side, i.e. your machine
Enter the following command to start generating a rsa keypair:
When the message ‘Enter file in which to save the key’ appears, just leave the filename blank by pressing Enter.
When the terminal asks you to enter a passphrase, just leave this blank (Warning: read below) too and press Enter.
Then copy the keypair onto the server with one simple command:
you can now log in without a password:
WARNING: Leaving SSH keys exposed without encrypting them is a not good practice even if you encrypt your whole drive. What is much safer is to actually enter a passphrase when generating keys and then use Keychain (MacOS, Linux) or SSH agent to remember the passphrase until you signout or suspend or timeout, depending on what you prefer.
Works fine with the default values. Using ~/rsa4live.pub didn’t work for me when attempting ssh-copy-id .
If you want this steps to work for different user, 1. ssh-keygen 2. ssh-copy-id nazir@hostname 3. ssh nazir@hostname
#!/usr/bin/expect -f # ./ssh.exp password 192.168.1.11 id set pass [lrange $argv 0 0] set server [lrange $argv 1 1] set name [lrange $argv 2 2] spawn ssh $name@$server match_max 100000 expect "*?assword:*" send -- "$pass\r" send -- "\r" interact # ./1.ex password localhost ooshro spawn ssh ooshro@localhost ooshro@localhost's password: Linux ubuntu-1010-server-01 2.6.35-25-generic-pae #44-Ubuntu SMP Fri Jan 21 19:01:46 UTC 2011 i686 GNU/Linux Ubuntu 10.10 Welcome to Ubuntu! * Documentation: https://help.ubuntu.com/ Last login: Tue Mar 1 12:41:12 2011 from localhost it will be good to add -oStrictHostKeyChecking=no -oUserKnownHostsFile=/dev/null for ssh command as well to avoid accept the machine into known_hosts
More detailed example of this script you can find at: linuxaria.com/howto/… This examples here should work with remote commands too
SSH single sign-on is usually achieved with public key authentication and an authentication agent. You could easily add your test VM key to an existing auth agent (see example below). Other methods such as gssapi/kerberos exist but are more complex.
sshpass
In situations where password is the only authentication method available, sshpass can be used to automatically enter the password. Please pay particular attention to the SECURITY CONSIDERATIONS section of the man page. In all three options, the password is visible or stored in plaintext at some point:
Anonymous pipe (recommended by sshpass)
# Create a pipe PIPE=$(mktemp -u) mkfifo -m 600 $PIPE # Attach it to file descriptior 3 exec 3<>$PIPE # Delete the directory entry rm $PIPE # Write your password in the pipe echo 'my_secret_password' >&3 # Connect with sshpass -d sshpass -d3 ssh user@host # Close the pipe when done exec 3>&- It is quite cumbersome in bash, arguably easier with programming languages. Another process could attach to your pipe/fd before the password is written. The window of opportunity is quite short and limited to your processes or root.
Environment variable
# Set your password in an environment variable export SSHPASS='my_secret_password' # Connect with sshpass -e sshpass -e ssh user@host You and root can read your process’ environment variables (i.e. your password) while sshpass is running ( cat /proc//environ | tr ‘\0’ ‘\n’ | grep ^SSHPASS= ). The window of opportunity is much longer but still limited to your own processes or root, not other users.
Command-line argument (least secure)
sshpass -p my_secret_password ssh user@host This is convenient but less secure as described in the man page. Command line arguments are visible to all users (e.g. ps -ef | grep sshpass ). sshpass attempts to hide the argument, but there is still a window during which all users can see your password passed by argument.
Side note
Set your bash HISTCONTROL variable to ignorespace or ignoreboth and prefix your sensitive commands with a space. They won’t be saved in history.
SSH public key authentication
# Generate a key pair # Do NOT leave the passphrase empty ssh-keygen # Copy it to the remote host (added to .ssh/authorized_keys) ssh-copy-id user@host The passphrase is very important. Anyone somehow obtaining the private key file won’t be able to use it without the passphrase.
Setup the SSH authentication agent
# Start the agent eval `ssh-agent` # Add the identity (private key) to the agent ssh-add /path/to/private-key # Enter key passphrase (one time only, while the agent is running) The advantage is that your private key is encrypted and you only need to enter its passphrase once (via a safer input method too).
How to Pass Password to SSH Command in Linux
The only way a user can accomplish a complete Linux operating system experience is if this user has had a partial or full glimpse of both sides of the Linux environment. Linux operating system exists both as a desktop environment and as a server environment.
For the desktop environment, users have the advantage of using GUI icons and applications to fulfill their operating system objectives. As for the server environment, an OS user needs some level of authentic familiarity with the Linux terminal commands to achieve an OS goal.
Most users stick to the desktop environment and others to the server environment. However, a multidimensional user will want to experience both sides of these environments. In this case, a Linux desktop user will need to flexibly access a Linux server environment and a Linux server user might also want to access other Linux server environments, routers, and firewalls.
Connecting to Linux Server Using SSH
There is no better-known tool for accessing Linux routers, firewalls, and servers than through the SSH cryptographic network protocol. The traditional approach of using the SSH protocol is summarized in by the following syntax:
$ ssh [email protected]_domain_name_or_server_ip_address
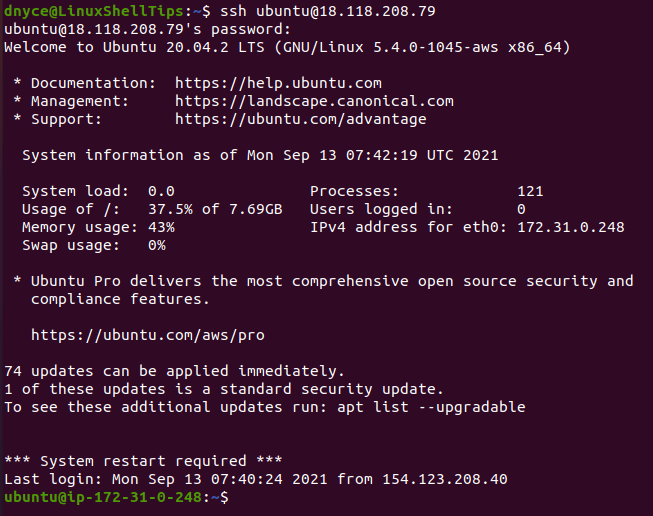
For example, I could access one of my servers in the following manner:
As per the above screen capture, the first access attempt to the Linux server was initiated by the command:
The execution of the above SSH command then later led to the prompt:
It is at this point that I keyed in the user-related (ubuntu) password and was successfully able to gain access to the Linux server.
For a novice Linux user or learner, this server-access approach is exciting and worth the pursuit. However, as you become an elite Linux user, you do not want to repeat yourself with a two-liner Linux command when you could only use one.
This article is here to fix this two-liner server access issue and provide an effective one-liner SSH access command for all your future Linux servers, routers, and firewalls access.
Install SSHPass in Linux – A SSH Password Provider
sshpass command-line tool will do the job for us. It facilitates a simplified approach to non-interactive ssh sign-in and supports one-liner ssh password input.
Firstly, you need to install the sshpass tool on your Linux operating system. Before the installation, ensure that you either have Sudo privileges or you are a Sudoer user of the Linux system.
$ sudo apt-get install sshpass [On Debian, Ubuntu and Mint] $ sudo yum install sshpass [On RHEL/CentOS/Fedora and Rocky Linux/AlmaLinux] $ sudo emerge -a sys-apps/sshpass [On Gentoo Linux] $ sudo pacman -S sshpass [On Arch Linux] $ sudo zypper install sshpass [On OpenSUSE]
How to Add Password to SSH Command in Linux
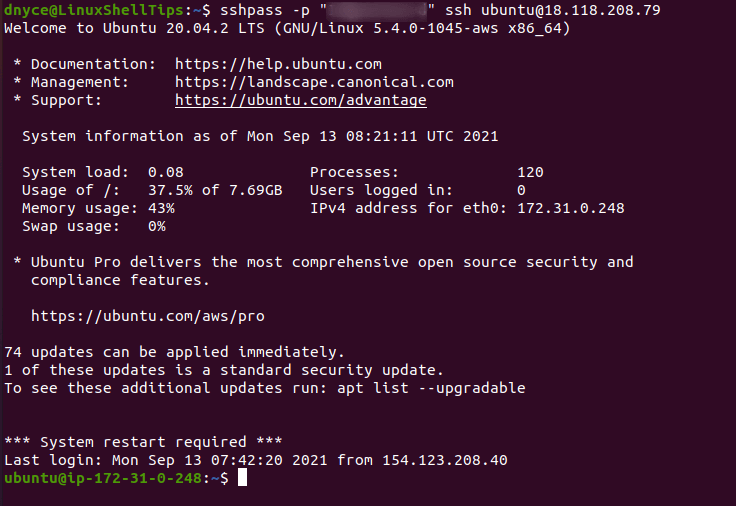
With the successful installation of SSHPASS, the one-liner SSH command syntax for accessing a remote Linux server, router, or firewall will look like the following:
In my case, I would implement SSHPASS usage in the following manner:
As expected, I have successfully accessed my Linux server with a one-liner command.
Combining the use of SSHPASS and SSH to access a remote server, router, or firewall gets rid of unnecessary two-liner commands that lead to an additional password entry prompt. It makes your remote access to other Linux environments faster and efficient.
How to specify password in ssh command
From the terminal I type: ssh user@ip and then it prompts for a password.
Is there a way to specify the password in the ssh command itself?
2 Answers 2
sshpass -ffilename ssh user@ip # prefer this sshpass -pPa5sw0rd ssh user@ip # avoid this where your password is in the first line of the file filename or it is literally Pa5sw0rd . Notes:
- In the manual there is no space after -p or -f , but at least sshpass 1.06 in my Debian 10 allows it; your sshpass may or may not.
- If your password contains characters your shell will interpret (like $ , ‘ or ; ) then you should quote it properly in the command line (but not in the file).
- Avoid -p . Use chmod 600 filename to make the file private (root will still be able to access it though). Read about security considerations in the manual.
Any solution for macOS? sshpass isn’t part of the default OS, and doesn’t seem to be available in Homebrew either.
The correct way to do this, is to switch from password authentication to a public/private key pair. This typically needs no reconfiguration at all and is quite easy.
Step 1: If you do not have a key, create one: ssh-keygen will do that for you
Step 2: Authorize this key on the remote host: Run ssh-copy-id user@ip once, using your password
Step 3: From now on ssh user@ip will no longer ask for your password
Thats correct. But the servers that i am working with are currently having password based authentication. And its really irritating to type password each time they prompt
from a security perspective this is the correct way to do it. but the OP asked «How to specify password in ssh command».
Nearly ALL servers allow key authentication in addition to password authentication — so you use the password authentication (via ssh-copy-id ) to enable the key.