- How to Fix Connection Refused by Port 22 Debian/Ubuntu
- Verify OpenSSH Installation on Your Linux System
- Check SSH Service
- Allow SSH in Firewall
- Resolve Duplicate IP Address Conflict
- Conclusion
- About the author
- Karim Buzdar
- Installing the OpenSSH Server
- Configuration
- Suggested OpenSSH Server Settings
- Start sshd on a Different Listening Port
- Logging
- Testing the server
How to Fix Connection Refused by Port 22 Debian/Ubuntu
SSH provides a secure channel to access Linux servers. Sometimes we come across the error Connection refused while connecting to SSH servers. There could be several reasons behind the error like the SSH service is inactive, the port is blocked by UFW firewall, the server is using a different port, or because of some IP conflict. Today, we will explore different ways we can resolve the Connection Refused issue on an Ubuntu/Debian system.
Verify OpenSSH Installation on Your Linux System
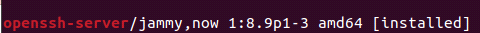
First, check if OpenSSH is installed on your system or not. The command mentioned below will verify it.
If OpenSSH is installed, you will see the following output on the terminal.
In case OpenSSH is not installed, we will install it by executing the following command:
Check SSH Service
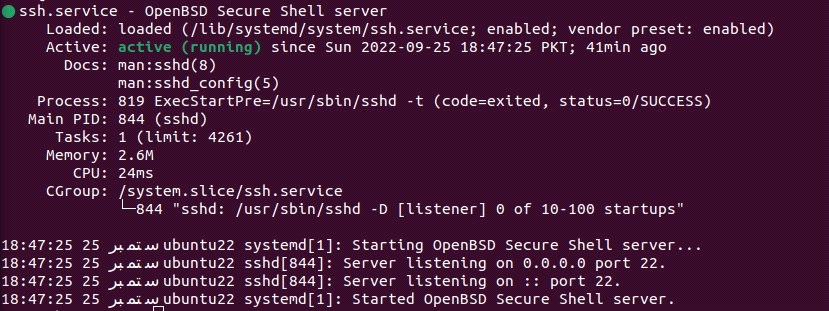
Let’s now check what’s the status of the SSH service on our system. It should be active or in the running state. The reason why you are getting a connection refused error could be the inactive state of SSH on your system. Run the following command to check the status:
The output tells us it is in the active (running state).
If your SSH service is inactive, you can start it by executing the following commands:
Check SSH Server Listening Port
Perhaps, you are connecting to the wrong port which is why you are getting a connection refused error. For example, the server is listening for a connection on port 1068 but you are trying to connect to port 22.
Before trying to connect, first, verify which port is being used by the SSH server to listen to new connections. If the server is listening on default port 22, then you can use the following command syntax to make a connection:
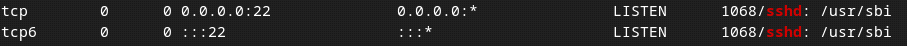
Issue the following command to check on which port the OpenSSH server is listening:
As we can see 22 port is in use by OpenSSH to listen to connections.
In case, some other port is being used in place of 22, you will issue the command like this:
Allow SSH in Firewall
A connection refused message could also be because the firewall on your system is blocking the SSH port. To allow the port through firewall, execute this command:
If a port other than 22 is being used, you will issue the command like this:
Once the rules are updated, you will get this output on the terminal:
Reload the firewall with this command to update the rules:
Now check the status of firewall to verify if the SSH port has been allowed or not.
You will see the following message if you are using port 2244 for SSH:
Resolve Duplicate IP Address Conflict
Another reason that may be causing this issue is a duplicate IP address. So, we need to verify if the system has a duplicate address or not. To do that, we need arping utility on our system. Install it using the following command:
Now, ping the server IP address using the command syntax below:
If you receive a reply from more than one MAC address, that means a duplicate IP address is running on the system. To resolve this issue, change the IP of the SSH server.
Conclusion
In today’s guide, we discussed several reasons that could be causing the Connection refused error and several ways to resolve this issue. This article will surely help you in troubleshooting the error.
About the author
Karim Buzdar
Karim Buzdar holds a degree in telecommunication engineering and holds several sysadmin certifications. As an IT engineer and technical author, he writes for various web sites. He blogs at LinuxWays.
Installing the OpenSSH Server
If you want to securely connect to your machine from a remote computer, even a computer running another operating system like Mac OS or Windows, then you need to install the following package: openssh-server.
Configuration
Once you have installed the SSH server, you will need to configure it by editing the sshd_config file in the /etc/ssh directory.
First, make a backup of your sshd_config file by copying it to your home directory, or by making a read-only copy in /etc/ssh by doing:
sudo cp /etc/ssh/sshd_config /etc/ssh/sshd_config.factory-defaults sudo chmod a-w /etc/ssh/sshd_config.factory-defaults
Creating a read-only backup in /etc/ssh means you’ll always be able to find a known-good configuration when you need it.
Once you’ve backed up your sshd_config file, you can make changes with any text editor (sudo gedit /etc/ssh/sshd_config runs the standard text editor). Once you’ve made your changes, you can apply them by saving the file then doing:
Suggested OpenSSH Server Settings
The default /etc/ssh/sshd_config which is used with Ubuntu’s OpenSSH implementation is more secure than that found in many other distributions of GNU/Linux, but there are changes which can enhance this level of security even further, and those changes are suggested here. Some of these changes may not be suitable to your particular situation. Use the settings which offer the best trade-off between security, and usability for your situation.
Start sshd on a Different Listening Port
Because a lot of people with SSH servers use weak passwords, many online attackers will look for an SSH server, then start guessing passwords at random. An attacker can try thousands of passwords in an hour, and the recommended long-term solution is to disable passwords altogether. However, you can get a limited amount of security by using strong passwords, and listening for connections on a non-standard port.
Most SSH servers listen on port number 22, so most scanners only look on that port. By using a different port, you can hide your SSH server from most scanners. This is a type of «security by obscurity» — a trick that can improve your security a little bit for a little while, but which shouldn’t be relied upon as your primary security system.
Using a non-standard port has another problem: you always need to tell your SSH client which non-standard port to use. See below for details on how to do this for the OpenSSH client.
To change the port that your SSH server listens on, first pick a number between 1,024 and 49,152 (Wikipedia explains why those numbers are special). Then add that port to your sshd_config file. For example, to listen to port number 2,222:
You can have as many Port lines as you like, but it’s considered good practice to keep them all together. You should make sure to comment out (or delete) the Port line that was originally in the file, to make your server stops listening on that port. So to listen on port 2,222 only, the relevant part of your sshd_config file should look like this:
Don’t forget you need to save the file, then restart your sshd, before your changes will take effect.
Logging
By default, the OpenSSH server logs to the AUTH facility of syslog, at the INFO level. It can be very informative to increase the logging level to VERBOSE for a week, then see how many spurious attempts have been made to access your computer. To increase the level, find the following line:
Now all the details of ssh login attempts will be saved in your /var/log/auth.log file.
If you have started using a different port, or if you think your server is well-enough hidden not to need much security, it’s recommended to increase your logging level, then examine your auth.log file every so often. If you find a significant number of spurious login attempts, then your computer is under attack, and you need more security.
Testing the server
Once you have configured the server, save your changes and restart it, then do:
You should be prompted to type your password, and you should get another command-line when you type your password in. If this works, then your SSH server is listening on the standard SSH port. If you have set your computer to listen on a non-standard port, then you will need to go back and comment out (or delete) a line in your configuration that reads Port 22. Otherwise, your SSH server has been configured correctly.
To leave the SSH command-line, type:
If you have set your computer to listen on a non-standard port, connect to it by doing:
Remember to replace with the port number you chose earlier on. If you are asked for a password, and get another command-line when you type it, then your SSH server has been configured correctly.
If you have a local network (such as a home or office network), try logging in from one of the other computers on your network. If nothing happens, you might need to tell your computer’s firewall to allow connections on port 22 (or from the non-standard port of you chose earlier).
Finally, try logging in from another computer elsewhere on the Internet — perhaps from work (if your computer is at home) or from home (if your computer is at your work). If you can’t access your computer this way, you might need to tell your router’s firewall to allow connections from port 22, and might also need to configure Network Address Translation.
SSH/OpenSSH/InstallingConfiguringTesting (последним исправлял пользователь knome 2013-12-13 18:43:05)
The material on this wiki is available under a free license, see Copyright / License for details
You can contribute to this wiki, see Wiki Guide for details