How to Disable SSH Root Login in Linux
The root account is often the most targeted account by crackers via SSH under Linux. An enabled SSH root account on a Linux server exposed to a network or, worse, exposed in Internet can pose a high degree of security concern by system administrators.
The SSH root account should be disabled in all cases in Linux in order to harden your server security. You should login via SSH on a remote server only with a normal user account and, then, change privileges to root account via sudo or su command.
In order to disable SSH root account, first log in to your server console with a normal account with root privileges by issuing the below commands.
$ su tecmint $ sudo su - # Drop privileges to root account
After you’ve logged in to console, open the main SSH configuration file for editing with your favorite text editor by issuing the below command. The SSH main configuration file is usually located in /etc/ssh/ directory in most of Linux distributions.
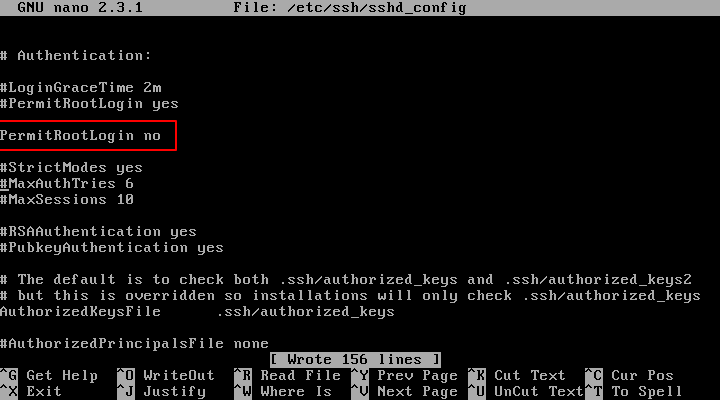
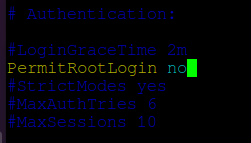
In this file, search for the line “PermitRootLogin” and update the line to look like in the below file excerpt. On some Linux distributions, the “PermitRootLogin” line is preceded by the hashtag sign (#) meaning that the line is commented. In this case uncomment the line by removing the hashtag sign and set the line to no.
After you’ve made the above changes, save and close the file and restart the SSH daemon to apply changes by issuing one of the below commands, specific to your Linux distribution.
# systemctl restart sshd # service sshd restart # /etc/init.d/ssh restart
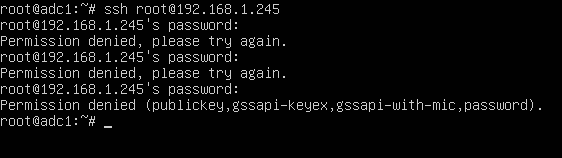
In order to test if the new configuration has been successfully applied, try to login with root account to the server via SSH from a remote system by issuing the below command.
The remote SSH login process for root account should be automatically denied by our SSH server, as illustrated in the below screenshot.
That’s all! You shouldn’t be able remotely login to SSH server with root account via password or via public key authentication mechanisms.
Как разрешить пользователю root заходить по SSH в системах Linux Ubuntu
Обновлено: 04.03.2023 Опубликовано: 07.01.2017
По умолчанию, в некоторых системах Linux (например, Ubuntu) для суперпользователя root вход по SSH с использованием пароля не работает. При попытке подключиться можно увидеть сообщение «access denied» или «permission denied». Такая настройка необходима для обеспечения большей безопасности системе. Однако, если требуется предоставить возможность подключаться по SSH от пользователя root, необходимо выполнить нижеописанное.
* Инструкция подойдет для большинства UNIX-систем.
С использованием сертификата
Система настроена таким образом, чтобы можно было подключиться под пользователем root с использованием сертификата. Рассмотрим, как это сделать.
На любом компьютере с Linux сгенерируем пару ключей командой:
. будет создано 2 файла id_ed25519.pub и id_ed25519. Содержимое файла id_ed25519.pub фиксируем.
Идем на наш целевой компьютер Ubuntu. Создаем каталог:
Вставляем в него содержимое файла id_ed25519.pub.
Теперь с компьютера, где были созданы сертификаты можно зайти на компьютер с Ubuntu:
Теперь с использованием ключа из файла id_ed25519 можно подключиться к нашему компьютеру Ubuntu без пароля.
По паролю
Для начала, необходимо создать пароль пользователю root следующей командой:
После нажатия Enter вводим дважды пароль.
Теперь открываем настройки SSH:
и редактируем параметр PermitRootLogin — задаем значение yes:
* если параметр закомментирован, снимаем комментарий.
** по умолчанию, значение может быть without-password или prohibit-password — оно разрешает вход для root средствами GSSAPI (не парольной аутентификации), например, смарт-карты или отпечатка пальца.
systemctl restart ssh || systemctl restart sshd
или в старых версиях без systemd:
service ssh restart || service sshd restart
How to Disable SSH Login to Specific User in Linux
As you might already know, SSH (Secure Shell) is a network protocol for securely accessing a computer remotely. The server and client software in Linux are thereby known as SSH Server and SSH Client respectively and have many implementations.
By default, SSH allows you to log in to any user of the computer, as long as you have the password for the user. However, this comes with the same problem which is faced by any software using password-based authentication: an invitation for an attacker to exploit and gain admin access.
Today, we will see how to disable SSH login to a specific user, and more importantly, to the root user.
Disable SSH Access to User
You can log in to a system using SSH with any user, using the following syntax:
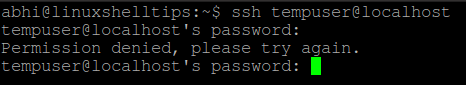
Right now, SSH access is allowed on my machine for all users. Let us now deny access to a particular user called ‘tempuser‘.
Open file ‘/etc/ssh/sshd_config’ in any text editor.
$ sudo vim /etc/ssh/sshd_config
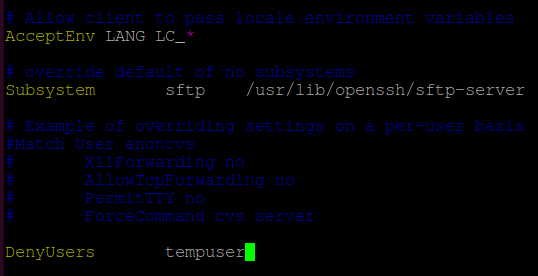
Add the following line at the end of the file:
Important: There is a ‘Tab‘ between ‘DenyUsers‘ and ‘tempuser‘ and not space. It won’t recognize the directive if you add a space.
Restart SSH server with the following command:
$ sudo systemctl restart sshd
If you are using a system that does not have SystemD, run:
$ sudo service sshd restart
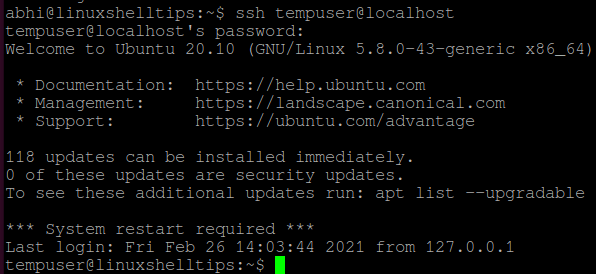
Now, try logging in to localhost with user ‘tempuser’ using SSH. It should show the error ‘Permission denied’, as displayed below:
Disable SSH Root Access
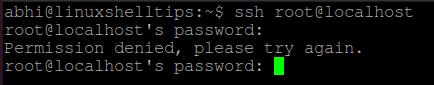
The same way described above can be used to disable login to a root user. However to disable complete root access, i.e., to disable access to all root users, follow the steps given below.
Open the file ‘/etc/ssh/sshd_config’ in any text editor and search for the string ‘PermitRootLogin’. Uncomment the line and if it has any other value, set the value to ‘no’.
Save and exit the file. Restart SSH with:
$ sudo systemctl restart sshd
Or if you are not having SystemD:
$ sudo service sshd restart
Now try logging in to localhost with user ‘root’. It will also show the error ‘Permission Denied’.
Conclusion
In this article, we learned how to disable SSH login access to a specific user. Restricting access to a Non-root user depends on individual scenarios, however, access to Root must be always restricted.
If there is a need for remote Root access, you should set up SSH with RSA authentication, which is more secure than password authentication. Read the man page of SSH (‘man ssh’) for more details.
Thanks for reading and let us know your thoughts in the comments section below!