- How to Set Up SSH on CentOS & RHEL
- Installing OpenSSH Packages
- Configuring SSH Server
- Installing and Configuring Firewalld
- Conclusion
- How to Enable SSH on CentOS 8
- Installing SSH Server Software:
- Managing OpenSSH Server Service:
- Connecting to the SSH Server:
- SSH Configuration Files:
- Configuring SSH Server:
- Changing SSH Server Port:
- Changing Listening Address:
- Disable root Login:
- Configuring Max Session and Max Password Tries:
- About the author
- Shahriar Shovon
How to Set Up SSH on CentOS & RHEL
Learn to enable SSH on CentOS Linux systems. Also learn to configure it to follow the best practices.
SSH (Secure Shell) is a secure network protocol based on the client-server architecture that allows you to securely access remote computers/servers over the network.
SSH is widely used by system administrators for connecting to remote servers. This makes administrators easily manage servers and applications remotely and securely from anywhere at any time.
In this guide, I’ll show you how to set up and enable SSH on CentOS/RHEL systems. With the SSH enabled on this CentOS system, you should be able to access this system from other computers using its IP address.
This tutorial also includes the steps to change the default SSH port, disable SSH login for the root user, and set up firewalld to secure your SSH server.
To complete this guide, ensure you have got the following requirements:
- A CentOS/RHEL Linux system. You can install it on your physical machine/real hardware, or using the virtual machine through KVM/VirtualBox, or using third-party cloud providers like Linode (but they usually already have SSH enabled).
- A non-root user with sudo/root privileges. This user will be used for modifying your system. And in the end, this user can be used to log in to your server.
Installing OpenSSH Packages
OpenSSH is one of the most popular software implementations of SSH protocol. It is used by millions of Linux servers, and become a critical part of the server environment. By default, OpenSSH is available on most Linux distribution repositories, including CentOS and RHEL systems.
Before you get started, refresh your package index using the DNF package manager as below.
Next, install OpenSSH packages on the CentOS/RHEL systems using the following command. This command will install OpenSSH server packages, as well as OpenSSH client software.
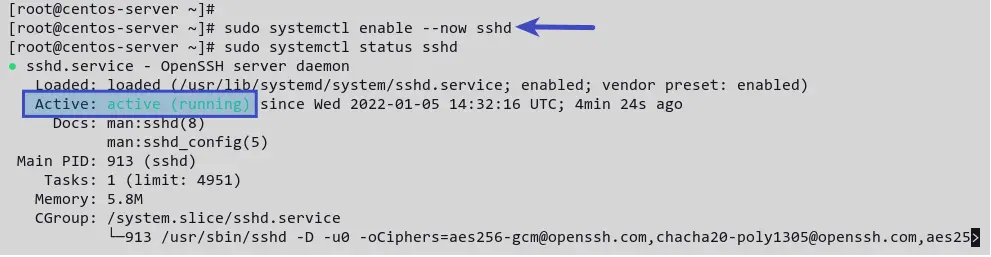
sudo dnf install openssh-server openssh-clients -y After OpenSSH installation is complete, execute the following command to start the sshd service and enable it to start automatically at the system boot.
sudo systemctl enable --now sshd Now, verify the sshd service status by running the following command.
sudo systemctl status sshd You’ll receive output like the following screenshot. The sshd service is active (running) .
Configuring SSH Server
By default, the SSH configuration is available at the /etc/ssh directory, and the main configuration file is sshd_config . This file contains some basic SSH configuration, such as ListenAddress that determines the IP address of running SSH service, Port for setting up SSH service port, authentication methods, and many more.
In this section, you’ll modify the configuration sshd_config , then change the default SSH port and disable login for the root user.
This setting is recommended for security reasons, it is to increase server security and reduce the brute force attack against your server.
Now, open the file sshd_config using vi editor or your preferred editor.
sudo vi /etc/ssh/sshd_config Before you start editing the file, you must know that lines beginning with # and empty lines are interpreted as comments.
At the top of the line, change the default SSH port from 22 to your preferred port. This tutorial uses the non-standard port 2028 for SSH.
Please make sure that you have a non-root user with sudo access already enabled on this system. Otherwise, if you disable root login, you may not be able to log in to your server remotely.
Next, change the option of PermitRootLogin yes to PermitRootLogin no . This will disable SSH login for the user root user. Optionally, you can add # at the beginning of the line PermitRootLogin .
After making changes, verify the SSH configuration, then restart the sshd service.
sshd -t sudo systemctl restart sshd Now, you can connect to your SSH server by running the ssh command below.
The -p option is used to specify the port of your SSH server.
In this section, you have completed the basic configuration for securing the SSH server by changing the default SSH port and disabling login for the root user. Moreover, you’ve learned to connect to the SSH server with a non-standard port. Next, you’ll install and configure firewalld.
Installing and Configuring Firewalld
If you are using the CentOS/RHEL server on the public internet, such as a cloud server, then you may need to enable the firewall. This will increase your server security, by limiting access only to specific services such as SSH, HTTP, and HTTPS. On CentOS/RHEL-based distribution, firewalld is the default firewall package that you can install on your system.
In this section, you’ll install firewalld and set up its open ports for your SSH server.
To install firewalld, run the dnf command below.
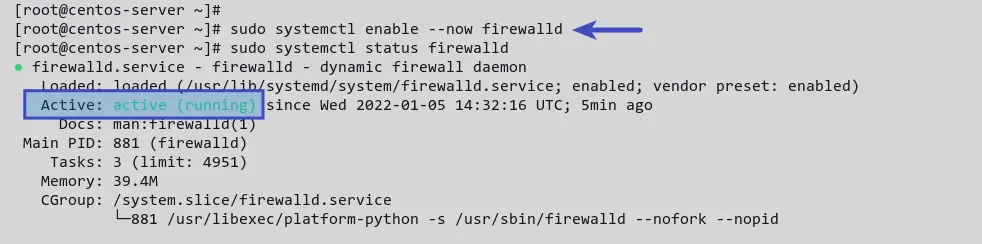
sudo dnf install firewalld -y After firewalld installation is completed, start and enable the firewalld service. Then verify its status by running the following command.
sudo systemctl enable --now firewalld sudo systemctl status firewalld You’ll receive a similar output like the screenshot below. The firewalld service is active (running) .
For interacting with firewalld, you can use the command firewall-cmd . It is the command-line interface for managing firewalld rules. You can use firewall-cmd to add, remove, and modify firewalld rules. And there are many more that you can do with using the firewall-cmd .
Now, to add the custom SSH port to your system, run the firewall-cmd command below.
sudo firewall-cmd --add-port=2028/tcp --permanent You’ll receive the output success , which means the operation success and completed.
This example uses the port 2028 as the custom SSH port. and the SSH service is running on the TCP port, so you need to specify the port and protocol such as 2028/tcp . The option —permanent makes this rule permanently.
Next, reload firewalld rules to apply a new configuration using the following command.
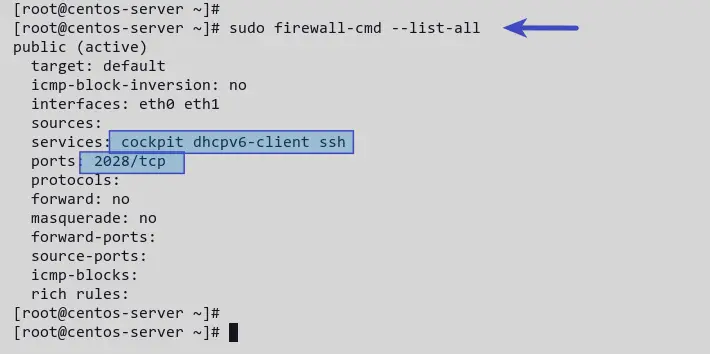
You have added the SSH custom port to the firewalld. Execute the command below to list all enabled rules.
Now you’ll see a list of enabled rules in firewalld. The services SSH, Cockpit, and dhcp are enabled by default.
To remove the default SSH rule, run the firewall-cmd command below. Then reload again firewalld rules.
sudo firewall-cmd --permanent --remove-service=ssh sudo firewall-cmd --reload Now, you have completed the installation and configuration of firewalld to secure your SSH server.
Conclusion
In this guide, you have completed the installation and configuration of SSH on the CentOS/RHEL system. You have secured your SSH server by changing the default port and disabling the login for the root user. Additionally, you’ve completed the firewalld installation and configuration on the CentOS/RHEL system for securing the SSH server.
Let us know if you have questions.
How to Enable SSH on CentOS 8
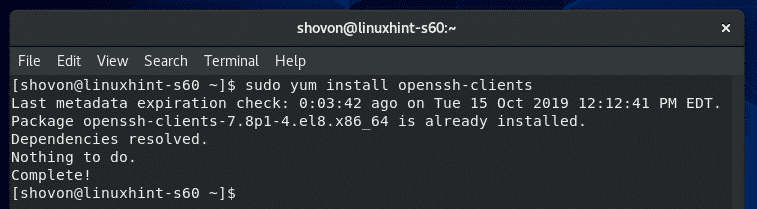
In order to connect to a SSH server, you must have OpenSSH client programs installed on your client machine.
In a CentOS or RHEL machine, you can install OpenSSH client programs with the following command:
The SSH client programs should be installed. In my case, it’s already installed.
Installing SSH Server Software:
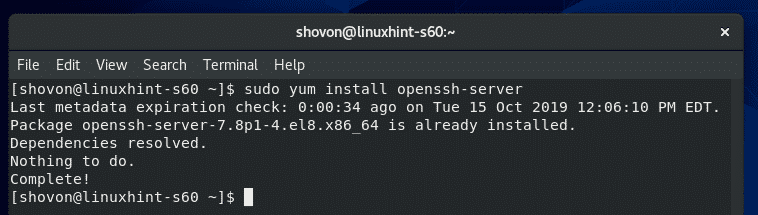
If you want to connect to your CentOS 8 server using SSH, then, you must have SSH server software installed on your CentOS 8 machine.
To install SSH server softwares on your CentOS 8 machine, run the following command:
OpenSSH server package should be installed. In my case, it is already installed.
Managing OpenSSH Server Service:
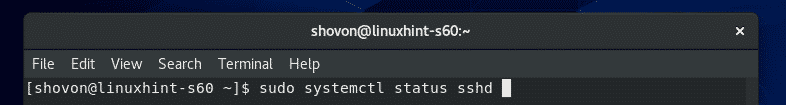
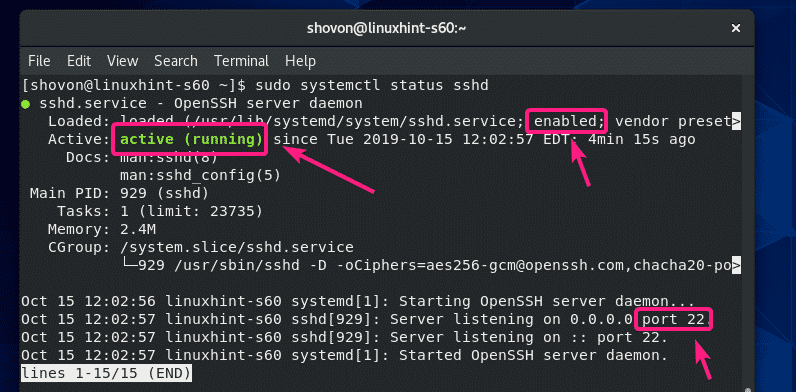
Once you have OpenSSH server software installed on your CentOS 8 machine, check whether the sshd service is running with the following command:
As you can see, the sshd service is active/running. It is also enabled to start automatically on system boot.
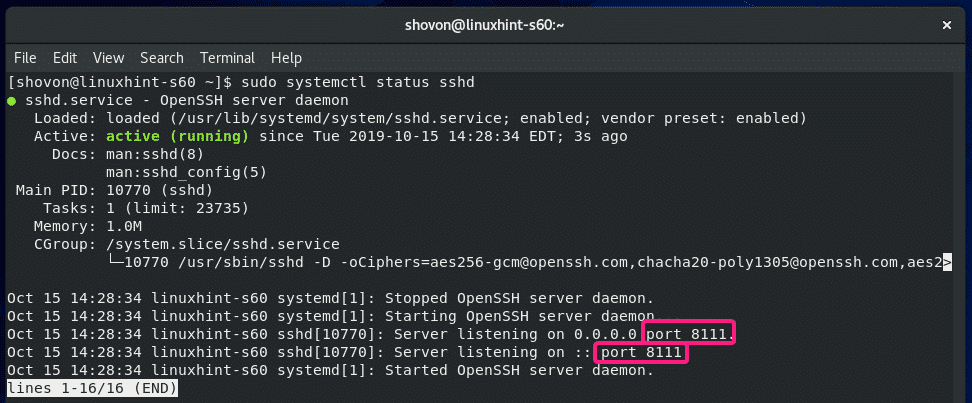
The SSH server is listening on all network interfaces (0.0.0.0) on port 22 by default.
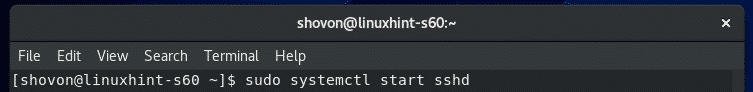
If the sshd service is not running on your CentOS 8 machine for some reason, you can manually start is with the following command:
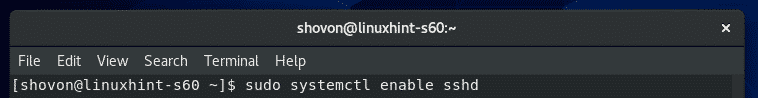
If the sshd service is not enabled to start automatically on system boot, then you can add it to the system startup as follows:
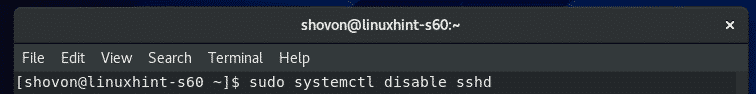
The same way, if you don’t want the SSH service to automatically start on system boot (for security reasons), then remove sshd service from the system startup as follows:
If you want to stop sshd service once you’ve configured your CentOS 8 server machine, then you can do so as follows:
If you change the SSH server configuration files, then for the changes to take effect, you will have to restart the sshd service. You can restart the sshd service as follows:
Connecting to the SSH Server:
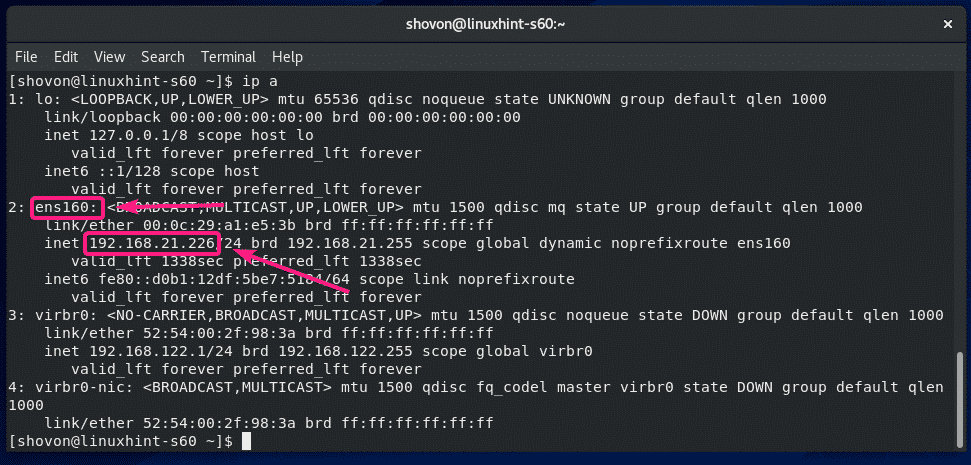
In order to connect to the SSH server, you need to know the IP address of your CentOS 8 server when you’ve SSH server software installed.
To find the IP address, run the following command on your CentOS 8 machine.
As you can see, the IP address of my CentOS 8 machine is 192.168.21.226. It will be different for you. So, make sure to replace it with yours from now on.
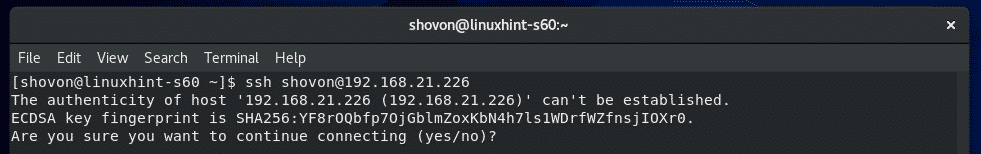
Now, from a client computer (must have SSH client programs installed), run the following command to connect to the CentOS 8 server using SSH:
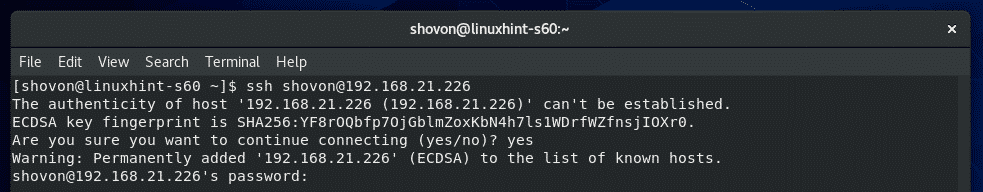
Now, type in yes and press .
Now, type in the password of your login_username and press .
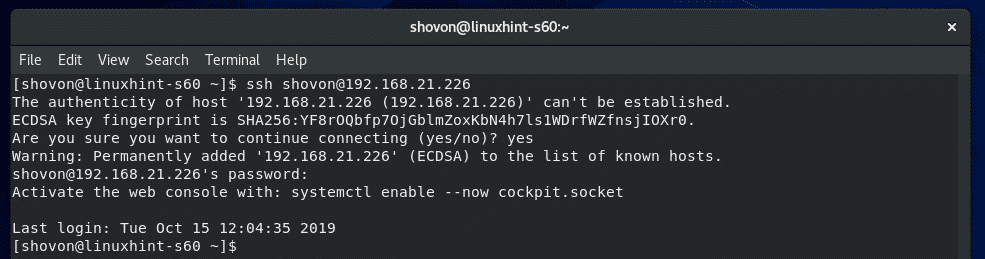
You should be logged in to the CentOS 8 machine via SSH.
Now, you can run any command on your CentOS 8 server from the client.
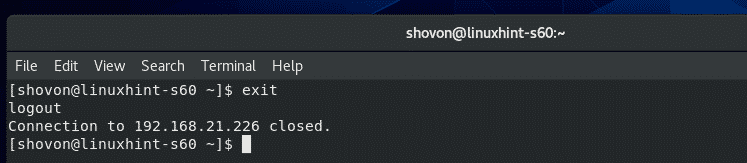
Once you’re done, close the SSH session as follows:
The SSH session should be closed.
SSH Configuration Files:
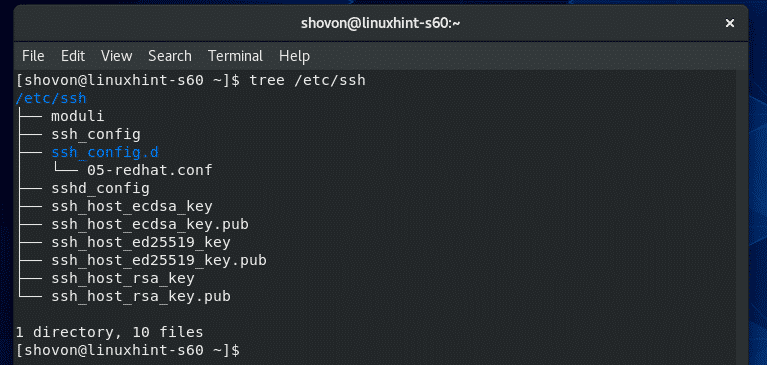
On CentOS 8, the SSH server and client configuration files are in the /etc/ssh directory.
The contents of the /etc/ssh directory are shown in the screenshot below.
Here, ssh_config and ssh_config.d/05-redhat.conf are the SSH client configuration files.
sshd_config is the SSH server configuration file. sshd_config file is our main focus in this article.
Configuring SSH Server:
To edit the sshd_config file, you can use the CentOS 8’s default text editor vi.
To open /etc/ssh/sshd_config configuration file in vi text editor, run the following command:
The configuration file should be opened. To modify the file, press i to go to insert mode.
Once you’re done editing the configuration file, press to go back to command mode.
If you want to save the file and close vi text editor, type in :wq! and press .
If you want to discard the changes and close vi text editor, type in :q! and press .
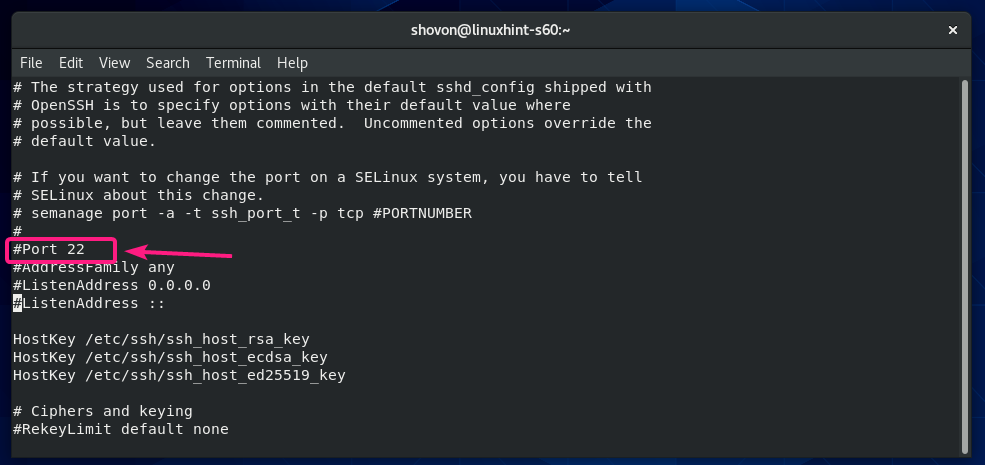
Changing SSH Server Port:
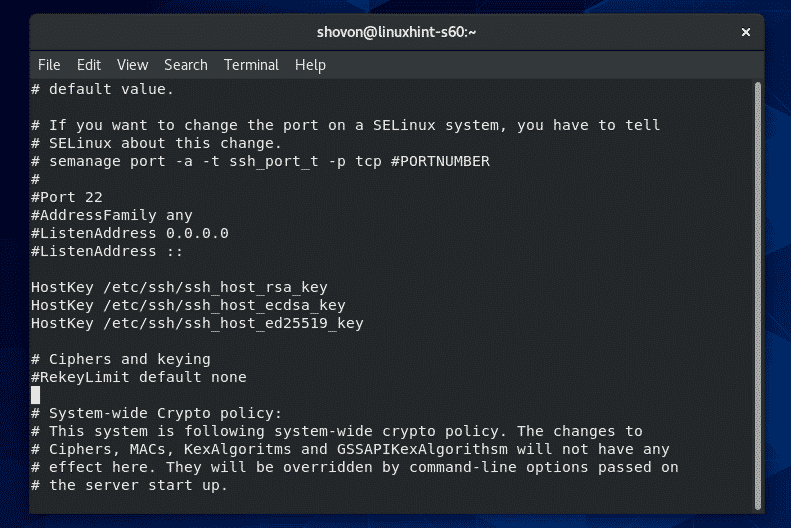
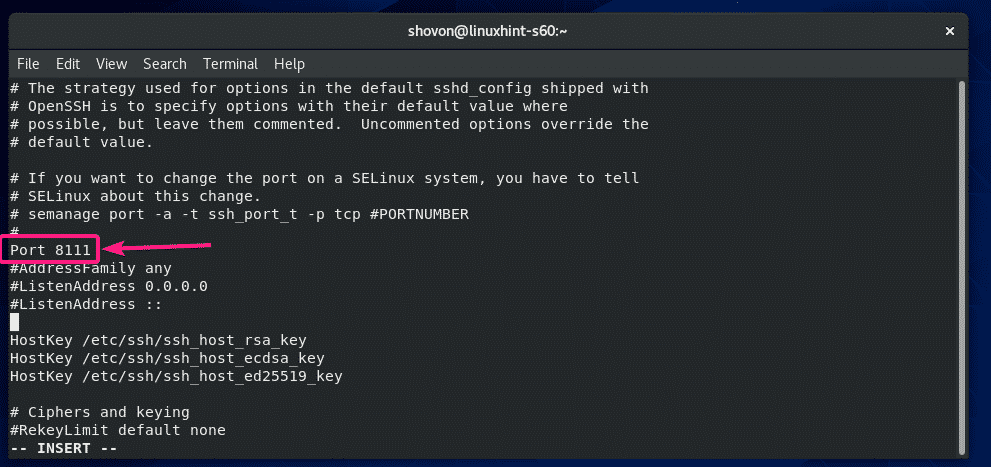
If you want to change the SSH server port from the default port 22 to something else (let’s say 8111) for security reasons, then uncomment the line as marked in the screenshot below from the sshd_config configuration file.
The configuration file should look as follows once Port is set. When you’re done, save the file.
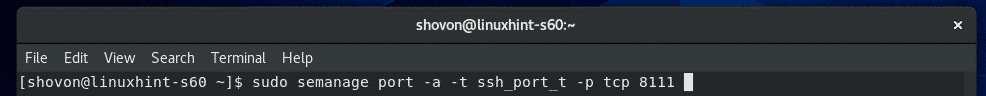
Now, configure SELinux to allow the port 8111 for SSH with the following command:
Before finishing the port change be sure to allow traffic to the new port through the firewall if it is running. For example the following command sequence:
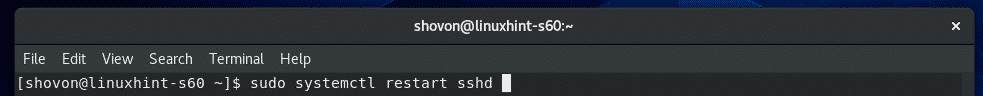
Now, restart the sshd service as follows:
SSH server should run on port 8111 from now on.
Changing Listening Address:
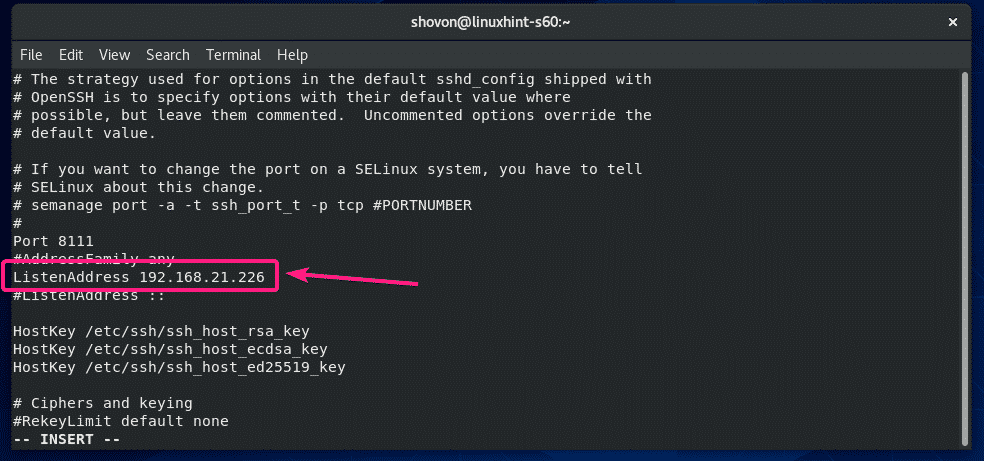
If you want the SSH server to listen to only a single network interface, then add the following line in the sshd_config file.
ListenAddress IP_ADDRESS_OF_INTERFACE
The configuration file should look as follows once ListenAddress is set.
Disable root Login:
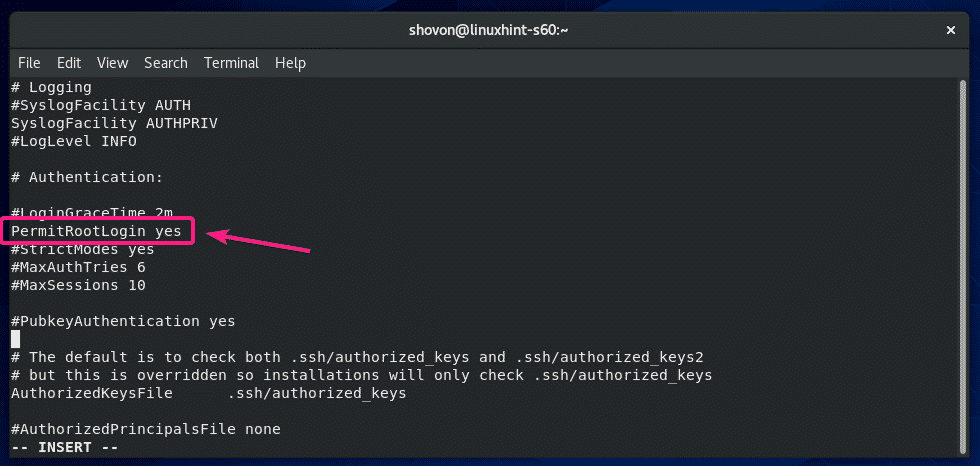
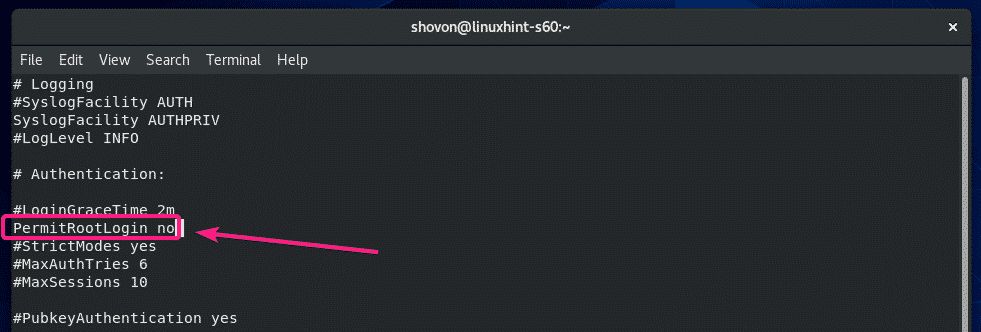
By default, CentOS 8 allows root user login over SSH. If you don’t want that, then change PermitRootLogin yes to PermitRootLogin no in the sshd_config configuration file.
The configuration file should look as follows once PermisRootLogin is set to no.
Configuring Max Session and Max Password Tries:
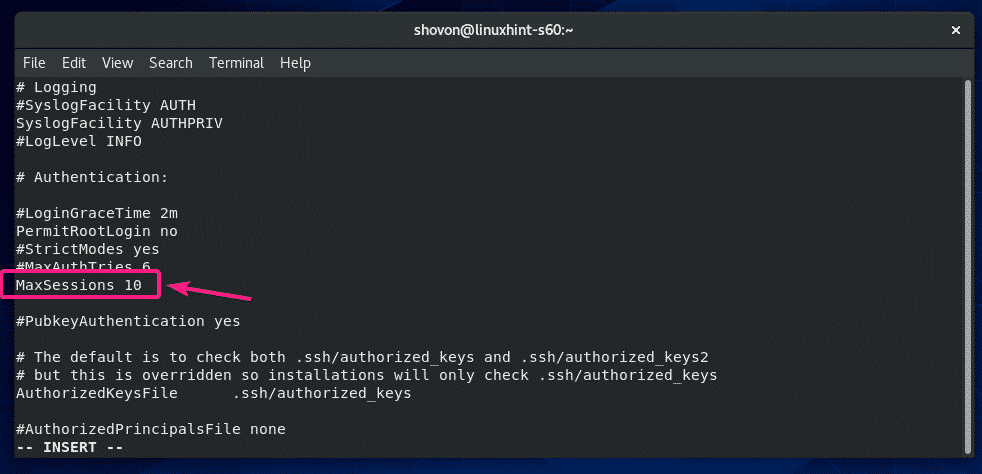
If you want to limit how many users can stay logged in to your CentOS 8 server via SSH, then uncomment MaxSessions in the sshd_config file and set your desired session number (default 10).
The configuration file should look as follows once MaxSessions is set to 10.
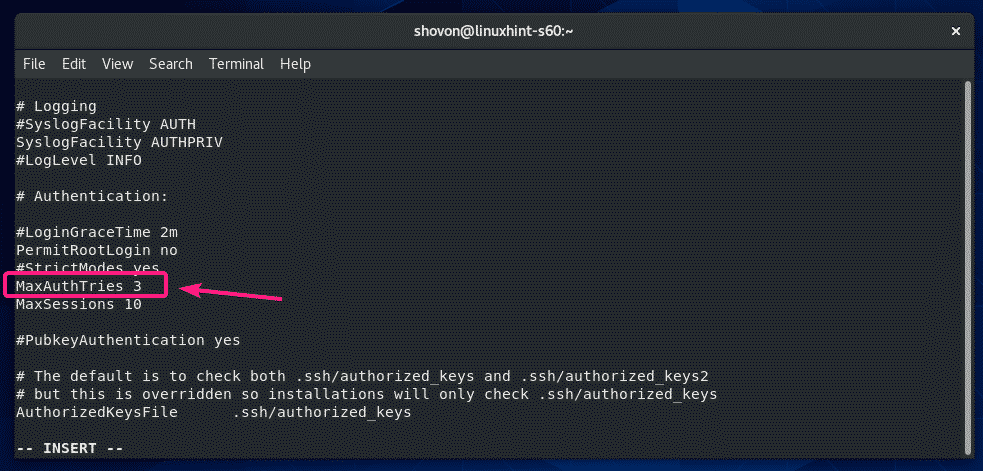
The same way, you can set a limit for failed login attempts. Just uncomment MaxAuthTries and set how many failed login attempts you want to allow before closing the connection.
The configuration file should look as follows once MaxAuthTries is set to 3.
So, that’s how you install and configure SSH server on CentOS 8. Thanks for reading this article.
About the author
Shahriar Shovon
Freelancer & Linux System Administrator. Also loves Web API development with Node.js and JavaScript. I was born in Bangladesh. I am currently studying Electronics and Communication Engineering at Khulna University of Engineering & Technology (KUET), one of the demanding public engineering universities of Bangladesh.