- How to pass the password to su/sudo/ssh without overriding the tty in Linux?
- Method 1: Using Expect
- Method 2: Using ssh-keygen
- Method 3: Using sshpass
- Method 4: Using a configuration file
- Conclusion
- How to Pass Password to SSH Command in Linux
- Connecting to Linux Server Using SSH
- Install SSHPass in Linux – A SSH Password Provider
- How to Add Password to SSH Command in Linux
- Sudo password when authenticating via passwordless SSH
How to pass the password to su/sudo/ssh without overriding the tty in Linux?
Linux: how to pass the password to su/sudo/ssh without overriding the TTY?
There are a few different methods for passing a password to su, sudo, or ssh without overriding the TTY. Each method has its own advantages and disadvantages, and the best method to use will depend on your specific use case. Below are a few examples of how to pass a password to these commands without overriding the TTY.
Method 1: Using Expect
Expect is a scripting language that can be used to automate interactions with interactive programs such as su, sudo, and ssh. It allows you to script the interactions, including sending the password to the program, without requiring any user input.
- Step 1 — Install Expect by running the command sudo apt-get install expect
- Step 2 — Create a script that uses Expect to automate the interaction with the program
For example, the following script can be used to run the command su — user and pass the password «password»:
#!/usr/bin/expect -f spawn su - user expect "Password:" send "password\r" interact- Step 3 — Make the script executable by running the command chmod +x script.sh
- Step 4 — Run the script by running the command ./script.sh
Method 2: Using ssh-keygen
Another way to pass a password to ssh without overriding the TTY is to use ssh-keygen to create a public and private key pair. The public key is then added to the remote server, and the private key is stored on the local machine. When you connect to the remote server using ssh, the private key is used to authenticate you instead of a password.
- Step 1 — Generate a key pair by running the command ssh-keygen -t rsa
- Step 2 — Copy the public key to the remote server by running the command ssh-copy-id user@remote_server
- Step 3 — Connect to the remote server using ssh without a password by running the command ssh user@remote_server
Method 3: Using sshpass
sshpass is a command line utility that allows you to pass a password to ssh without overriding the TTY. This tool can be used to automate ssh connections and can be used in scripts.
- Step 1 — Install sshpass by running the command sudo apt-get install sshpass
- Step 2 — Connect to a remote server using sshpass by running the command sshpass -p ‘password’ ssh user@remote_server
Method 4: Using a configuration file
Another way to pass a password to su, sudo, or ssh without overriding the TTY is to use a configuration file. This method can be used to store the password and other information required to connect to a remote server or run a command as a different user.
For example, create a file named «config» in your home directory and add the following lines:
user=yourusername password=yourpasswordFor example, the following script can be used to run the command su — $(cat config | grep user | cut -d «=» -f2) and pass the password $(cat config | grep password | cut -d «=» -f2):
-
Step 1 — Install a password manager that has a command line interface, such as
pass,bitwarden-cli, orkeepassxc-cli -
Step 2 — Add your password to the password manager.
-
Step 3 — Use the command line interface to retrieve the password and provide it to the command
Conclusion
In conclusion, there are several ways to pass a password to su, sudo, or ssh without overriding the TTY. Each method has its own advantages and disadvantages, and the best method to use will depend on your specific use case. Some of the methods include using Expect, ssh-keygen, sshpass, a configuration file and a password manager. Expect and ssh-keygen are both good choices for automating interactions with these commands, while sshpass is a good choice for automating ssh connections in scripts. Using a configuration file or a password manager can be a good choice for storing and organizing the password securely, and using them in a script can be a good choice for automating tasks. It is important to keep in mind the security risks of storing the passwords in plain text or hardcoded in the script and use the appropriate method that fits the security requirements of your organization.
How to Pass Password to SSH Command in Linux
The only way a user can accomplish a complete Linux operating system experience is if this user has had a partial or full glimpse of both sides of the Linux environment. Linux operating system exists both as a desktop environment and as a server environment.
For the desktop environment, users have the advantage of using GUI icons and applications to fulfill their operating system objectives. As for the server environment, an OS user needs some level of authentic familiarity with the Linux terminal commands to achieve an OS goal.
Most users stick to the desktop environment and others to the server environment. However, a multidimensional user will want to experience both sides of these environments. In this case, a Linux desktop user will need to flexibly access a Linux server environment and a Linux server user might also want to access other Linux server environments, routers, and firewalls.
Connecting to Linux Server Using SSH
There is no better-known tool for accessing Linux routers, firewalls, and servers than through the SSH cryptographic network protocol. The traditional approach of using the SSH protocol is summarized in by the following syntax:
$ ssh [email protected]_domain_name_or_server_ip_address
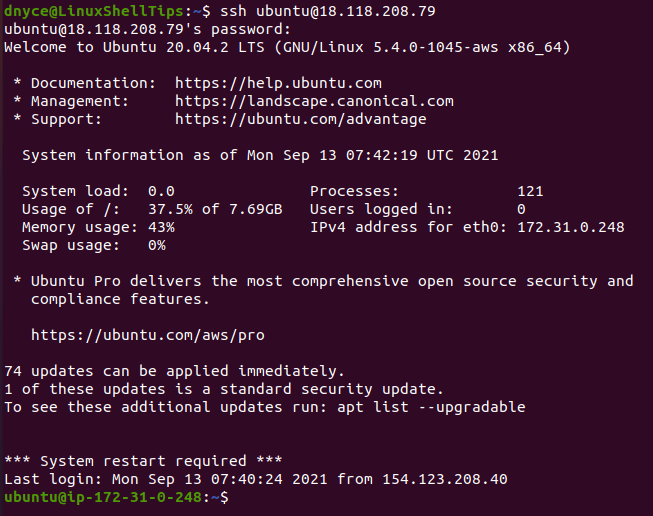
For example, I could access one of my servers in the following manner:
As per the above screen capture, the first access attempt to the Linux server was initiated by the command:
The execution of the above SSH command then later led to the prompt:
It is at this point that I keyed in the user-related (ubuntu) password and was successfully able to gain access to the Linux server.
For a novice Linux user or learner, this server-access approach is exciting and worth the pursuit. However, as you become an elite Linux user, you do not want to repeat yourself with a two-liner Linux command when you could only use one.
This article is here to fix this two-liner server access issue and provide an effective one-liner SSH access command for all your future Linux servers, routers, and firewalls access.
Install SSHPass in Linux – A SSH Password Provider
sshpass command-line tool will do the job for us. It facilitates a simplified approach to non-interactive ssh sign-in and supports one-liner ssh password input.
Firstly, you need to install the sshpass tool on your Linux operating system. Before the installation, ensure that you either have Sudo privileges or you are a Sudoer user of the Linux system.
$ sudo apt-get install sshpass [On Debian, Ubuntu and Mint] $ sudo yum install sshpass [On RHEL/CentOS/Fedora and Rocky Linux/AlmaLinux] $ sudo emerge -a sys-apps/sshpass [On Gentoo Linux] $ sudo pacman -S sshpass [On Arch Linux] $ sudo zypper install sshpass [On OpenSUSE]
How to Add Password to SSH Command in Linux
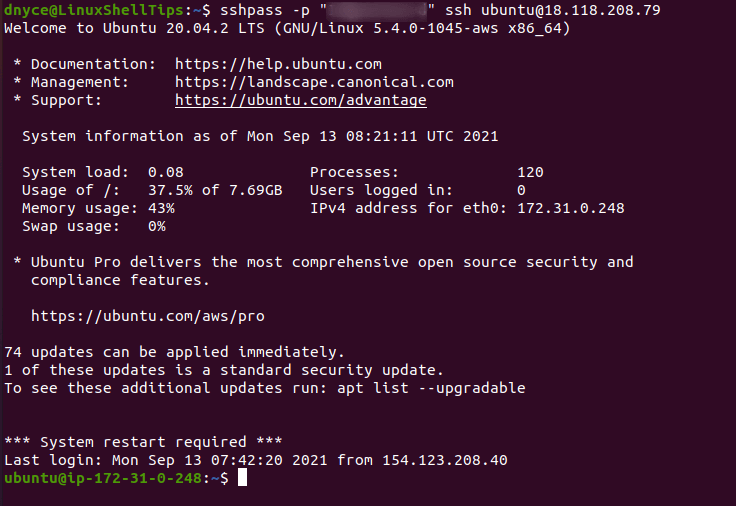
With the successful installation of SSHPASS, the one-liner SSH command syntax for accessing a remote Linux server, router, or firewall will look like the following:
In my case, I would implement SSHPASS usage in the following manner:
As expected, I have successfully accessed my Linux server with a one-liner command.
Combining the use of SSHPASS and SSH to access a remote server, router, or firewall gets rid of unnecessary two-liner commands that lead to an additional password entry prompt. It makes your remote access to other Linux environments faster and efficient.
Sudo password when authenticating via passwordless SSH
Several of these boxes are web servers, and are hosting web applications of what I fear to be dubious quality. (I didn’t write them, so they’re dubious!) I’ve got Apache and the permissions on the servers configured such that a very unprivileged user (www-data) is serving the files, but my fear is that — somehow — an attacker could compromise a web application, escalate privileges to a more privileged user, and then simply sudo -i to root.
I’m not aware of a vulnerability in my software that would allow www-data to escalate its privileges, but I would prefer having a password in place to use sudo were that somehow to happen.
Also, for the record: I did try to set a password by logging in via SSH and then running passwd , but it threw an error. I don’t remember the exact phrasing, but it was something about a «token». Either way, the password didn’t stick, which makes me think I’m misunderstanding something at a fundamental level here.
Any illumination on the subject would be very much appreciated. Thanks.
Thanks for the thoughtful explanations, all. It does in fact seem like the issue lies in /etc/sudoers . Thanks for pointing me in that direction.
I figured I’d document this for the sake of completing the discussion. When I looked into /etc/sudoers , I encountered the following lines:
# ubuntu user is default user in ec2-images. # It needs passwordless sudo functionality. ubuntu ALL=(ALL) NOPASSWD:ALL I am, in fact, using the ubuntu user for my privileged operations (though, again, the webserver is only running as www-data ), so I guess that explains the issue I was having.
If anyone wants to follow up with a guess why the ubuntu user needs passwordless sudo functionality, I’d love to hear it. Otherwise, at least for the time being, I think I’ll let good enough alone and leave the configuration as-is. I don’t want to break a working system while trying to preemptively solve a non-existent problem.
Thanks again for lending your time and expertise.