- Sudoers file, enable NOPASSWD for user, all commands
- Question
- How to Setup Sudo No Password in Linux
- How to Setup Sudo No Password
- Step 1:
- Step 2:
- Example1:
- Example2:
- Conclusion:
- About the author
- Syeda Wardah Batool
- How to run sudo command with no password?
- 6 Answers 6
- Execute sudo without Password?
- 12 Answers 12
Sudoers file, enable NOPASSWD for user, all commands
This is a fairly complex question related to the sudoers file and the sudo command in general. NOTE: I have made these changes on a dedicated machine running Ubuntu Desktop 13.04, that I use purely for learning purposes. I understand it’s a huge security risk to enable NOPASSWD sudo.
Question
Initially, my only change to the sudoers file ( /etc/sudoers ) was one line, a user specification that should have enabled nicholsonjf to run all commands with sudo without having to enter a password (see the line that starts with nicholsonjf):
# This file MUST be edited with the 'visudo' command as root. # # Please consider adding local content in /etc/sudoers.d/ instead of # directly modifying this file. # # See the man page for details on how to write a sudoers file. # Defaults env_reset Defaults mail_badpass Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin" # Host alias specification # User alias specification # Cmnd alias specification # User privilege specification root ALL=(ALL:ALL) ALL nicholsonjf ALL=NOPASSWD: ALL # Members of the admin group may gain root privileges %admin ALL=(ALL) ALL # Allow members of group sudo to execute any command %sudo ALL=(ALL:ALL) ALL # See sudoers(5) for more information on "#include" directives: #includedir /etc/sudoers.d However this did not work, and I was still prompted for my password every time I ran a command as nicholsonjf. I was only able to start running sudo commands as nicholsonjf once I removed nicholsonjf from the sudo and admin groups. Can anyone explain why this worked? Is it because the user nicholsonjf was inheriting sudo rights from the two group specifications of admin and sudo (seen below in the sudoers file), which were overriding the nicholsonjf user specification because they were further down in the config file?
How to Setup Sudo No Password in Linux
When a user executes the command with the sudo privileges, it asks for the password to run it and confirms the user’s request to perform that specific function from the file sudoers.
The Sudoers is the administrator’s file used for system configuration. System administrators can give access to the users to run some specific command or all commands. It keeps all the records in it about what and when things are done by whom.
It is good to set the password when you have multiple users in a single account. But when you’re the only user of a system and use it as a root user, typing the password multiple times for sudo privileges could irritate you. So, instead of entering the password even for a single function, it is better to set sudo without a password.
You can do it using the etc/sudoers file as we will discuss below.
How to Setup Sudo No Password
To set sudo without entering the password is a straightforward way that you don’t need to worry about. Just follow the steps carefully:
Step 1:
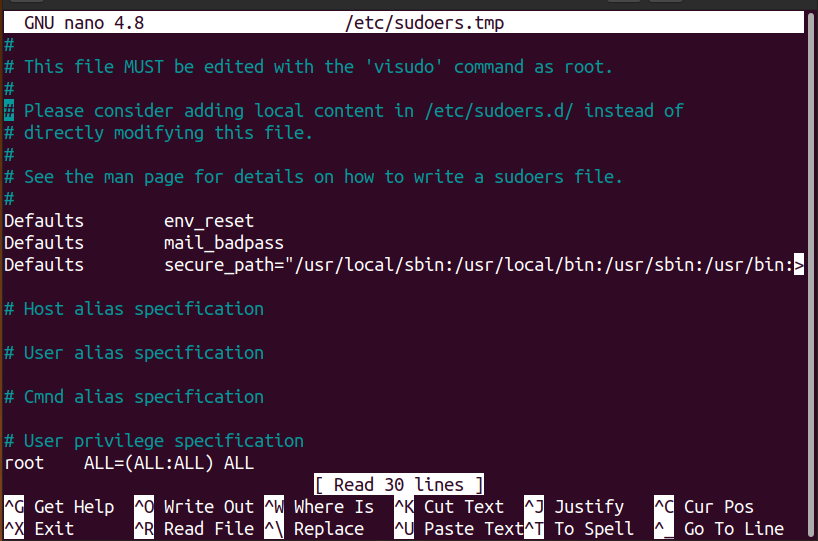
Open the terminal and type the following command to get /etc/sudoers file:
Enter the credential i.e. password to get the file:
Step 2:
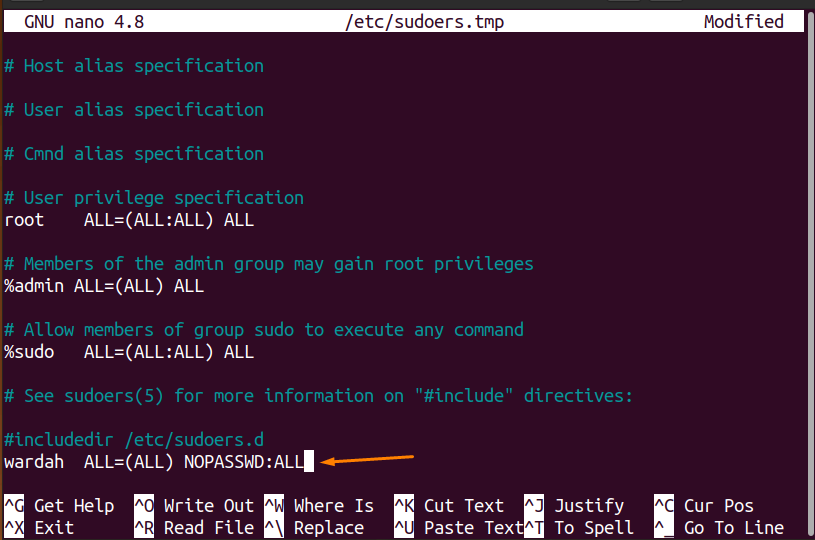
Scroll down till the end of the /etc/sudoers file and append the mentioned below line:
(The mentioned line should be written at the end of the file so the other directives couldn’t be overridden with this)
Note: wardah is the username in my Linux system. You will write your username here.
Press Ctrl+s to save the /etc/sudoers file and then Ctrl+x to exit it.
Let’s run an example that needs Sudo privileges in command.
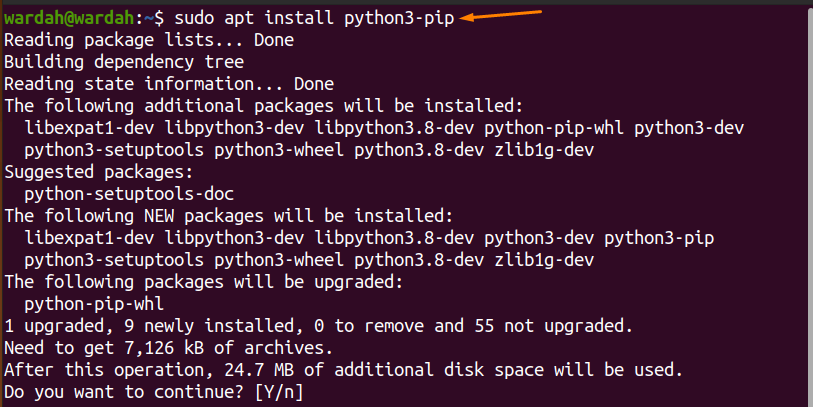
Example1:
Run the given command in terminal to install pip package through python:
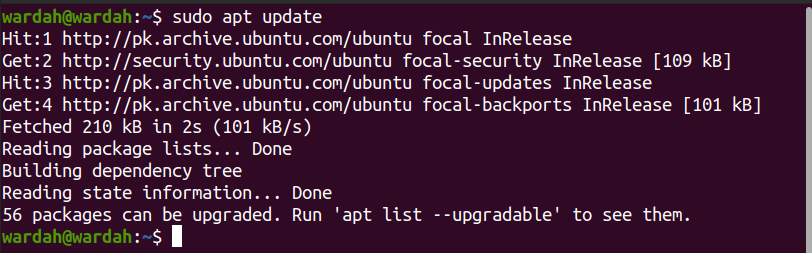
Example2:
Execute the update command to update all packages available in the Linux system:
As you can see in both of the mentioned examples, after setting no password in sudo privileges, it won’t ask you to enter the password again while executing commands.
Conclusion:
Entering a password all the time with the Sudo command is irritating when you’re the only user. We can set the Sudo without a password using the /etc/sudoers file. The sudoers is the system administration configuration file having all the information about the user, what, and when they performed in the system.
About the author
Syeda Wardah Batool
I am a Software Engineer Graduate and Self Motivated Linux writer. I also love to read latest Linux books. Moreover, in my free time, i love to read books on Personal development.
How to run sudo command with no password?
How does the ubuntu user on the AWS images for Ubuntu Server 12.04 have passwordless sudo for all commands when there is no configuration for it in /etc/sudoers ? I’m using Ubuntu server 12.04 on Amazon. I want to add a new user that has the same behavior as the default Ubuntu user. Specifically I want passwordless sudo for this new user. So I’ve added a new user and went to edit /etc/sudoers (using visudo of course). From reading that file it seemed like the default ubuntu user was getting it’s passwordless sudo from being a member of the admin group. So I added my new user to that. Which didn’t work. Then I tried adding the NOPASSWD directive to sudoers . Which also didn’t work. Anyway, now I’m just curious. How does the ubuntu user get passwordless privileges if they aren’t defined in /etc/sudoers . What is the mechanism that allows this?
6 Answers 6
Okay, I have discovered the answer so may as well put it here for completeness. At the end of /etc/sudoers there is what I thought was just a comment:
However this actually includes the contents of that directory. Inside of which is the file /etc/sudoers.d/90-cloudimg-ubuntu . Which has the expected contents
# ubuntu user is default user in cloud-images. # It needs passwordless sudo functionality. ubuntu ALL=(ALL) NOPASSWD:ALL So that is where the sudo configuration for the default ubuntu user lives.
You should edit this file using visudo. The following command will let you edit the correct file with visudo.
sudo visudo -f /etc/sudoers.d/90-cloudimg-ubuntu aychedee ALL=(ALL) NOPASSWD:ALL In later versions (14.04 for example) the included file is /etc/sudoers.d/90-cloud-init-users (so to edit.. sudo visudo -f /etc/sudoers.d/90-cloud-init-users ). Although it’d be cleaner to create additional files than editing the generated one. Note that files containing a . or ending in ~ will not be included.
@Phil_1984_ Most likely, it was added as a comment to allow compatibility with other (standard?) versions of sudo, which don’t allow includes, but wouldn’t be tripped up by a weird comment. (Standards are hard! 😉
I found that the most straight forward thing to do, in order to easily replicate this behavior across multiple servers, was the following:
# Members of the admin group may gain root privileges %admin ALL=(ALL) ALL # Members of the admin group may gain root privileges %admin ALL=(ALL) NOPASSWD:ALL And move it under this line:
# Allow members of group sudo to execute any command %sudo ALL=(ALL:ALL) ALL # This file MUST be edited with the 'visudo' command as root. # # Please consider adding local content in /etc/sudoers.d/ instead of # directly modifying this file. # # See the man page for details on how to write a sudoers file. # Defaults env_reset Defaults mail_badpass Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin" # Host alias specification # User alias specification # Cmnd alias specification # User privilege specification root ALL=(ALL:ALL) ALL # Allow members of group sudo to execute any command %sudo ALL=(ALL:ALL) ALL # Members of the admin group may gain root privileges %admin ALL=(ALL) NOPASSWD:ALL # See sudoers(5) for more information on "#include" directives: #includedir /etc/sudoers.d then for every user that needs sudo access WITH a password:
and for every user that needs sudo access WITH NO password:
(on older versions of ubuntu, you may need to):
sudo service sudo restart Edit: You may have to add the admin group as I don’t think it exists by default.
You can also add the default AWS ubuntu user to the admin group via this command:
sudo usermod ubuntu -g admin Note: As @hata mentioned, you may need to use adm as your admin group name, depending on which version of Ubuntu is being used.
Execute sudo without Password?
Inspired by this question. I am the sole person using my system with 12.04.
Every time I issue a sudo command; the system asks for the user password (which is good in its own way).
However I was thinking; without activating the root account; how can I execute the sudo commands which will not ask for user password to authenticate. NOTE: I want to execute sudo command without authenticating via password; only when they are executed via terminal.
I don’t want to remove this extra layer of security from other functions such a while using ‘Ubuntu software center’ or executing a bash script by drag-drop something.sh file to the terminal.
so you only want to be asked for the password in the terminal and for other things not, or the other way arround?! in both ways, I think its a high security breach
I want that system may not ask password only when in the terminal. for any other purpose the system must ask a password. This requirement is only temporary, and to be used while configuring n installing new servers.. during fresh server installations, it really take hours of configuring with sudo commands.. issuing password every 15 min. is headache. I don’t want to use root account.
For sure you can prolong the timeout. Also, if you’re frequently doing fresh server setups you should think about automating the process. You are not paid to type, you are paid to solve problems and to get sh*t done.
12 Answers 12
You can configure sudo to never ask for your password.
Open a Terminal window and type:
In the bottom of the file, add the following line:
Where $USER is your username on your system. Save and close the sudoers file (if you haven’t changed your default terminal editor (you’ll know if you have), press Ctl + x to exit nano and it’ll prompt you to save).
As of Ubuntu 19.04, the file should now look something like
# # This file MUST be edited with the 'visudo' command as root. # # Please consider adding local content in /etc/sudoers.d/ instead of # directly modifying this file. # # See the man page for details on how to write a sudoers file. # Defaults env_reset Defaults mail_badpass Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin" # Host alias specification # User alias specification # Cmnd alias specification # User privilege specification root ALL=(ALL:ALL) ALL # Members of the admin group may gain root privileges %admin ALL=(ALL) ALL # Allow members of group sudo to execute any command %sudo ALL=(ALL:ALL) ALL # See sudoers(5) for more information on "#include" directives: #includedir /etc/sudoers.d YOUR_USERNAME_HERE ALL=(ALL) NOPASSWD: ALL After this you can type sudo in a Terminal window without being prompted for the password.
This only applies, to using the sudo command in the terminal. You’ll still be prompted for your password if you (for example) try to install a package from the software center