- fswatch – Monitors Files and Directory Changes or Modifications in Linux
- Features of fswatch
- How To Install fswatch in Linux Systems
- How do I use fswatch on Linux?
- Track file changes using auditd
- Install and start Linux Auditing System
- Make auditd to log all file changes
- Track file changes using auditd
- Install and start Linux Auditing System
- Make auditd to log all file changes
fswatch – Monitors Files and Directory Changes or Modifications in Linux
fswatch is a cross-platform, file change monitor that gets notification alerts when the contents of the specified files or directories are altered or modified.
It executes four types of monitors on different operating systems such as:
- A monitor build on the File System Events API of Apple OS X.
- A monitor based on kqueue, a notification interface present in FreeBSD 4.1 also supported on many *BSD systems, OS X inclusive.
- A monitor based on File Events Notification API of the Solaris kernel plus its spin-offs.
- A monitor based on inotify, a kernel subsystem that shows file system modifications to apps.
- A monitor based on ReadDirectoryChangesW, a Windows API that records alters to a directory.
- A monitor that regularly check that status of file system, keeps file modification times in memory, and manually determine file system changes (which works anywhere, where stat can be used).
Features of fswatch
- Supports several OS-specific APIs
- Allows recursive directory monitoring
- Performs path filtering using including and excluding regular expressions
- Supports customizable record format
- Additionally, it supports periodic idle events
How To Install fswatch in Linux Systems
Unfortunately, fswatch package is not available to install from the default system repositories in any Linux distributions. The only way to install the latest version of fswatch is to build from source tarball as show in the following installation instructions.
First grab the latest fswatch tarball using following wget command and install it as shown:
$ wget https://github.com/emcrisostomo/fswatch/releases/download/1.9.3/fswatch-1.9.3.tar.gz $ tar -xvzf fswatch-1.9.3.tar.gz $ cd fswatch-1.9.3 $ ./configure $ make $ sudo make install
Important: Make sure you’ve GNU GCC (C and C++ Compiler) and Development Tools (build-essential on Debian/Ubuntu) installed on the system, before you compile fswatch from source. If not, install it using following command on your respective Linux distributions..
# yum group install 'Development Tools' [On CentOS/RHEL] # dnf group install 'Development Tools' [On Fedora 22+ Versions] $ sudo apt-get install build-essential [On Debian/Ubuntu Versions]
On Debian/Ubuntu distributions, you might get following error while executing fswatch command..
fswatch: error while loading shared libraries: libfswatch.so.6: cannot open shared object file: No such file or directory
To fix it, you need to execute the command below, this will help refresh the links and cache to the dynamic libraries before you can start using fswatch.
How do I use fswatch on Linux?
The general syntax for running fswatch is:
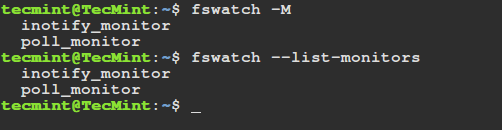
On Linux, it is recommended that you use the default inotify monitor, you can list available monitors by employing the -M or — list-monitors option:
$ fswatch -M $ fswatch --list-monitors
The command below enables you to watch the changes in the current directory ( /home/tecmint ), with events being delivered to standard output every 4 seconds.
The -l or – -latency option allows you to set the latency in seconds, the default being 1 second.
The next command monitors changes to the /var/log/auth.log file every 5 seconds:
$ fswatch -l 5 /var/log/auth.log
Using -t or —timestamp option prints the time stamp for every event, to print the time in UTC format, employ -u or —utf-time option. You can as well format time using -f or —format-time format option:
$ fswatch --timestamp /var/log/auth.log
Next, -x or —event-flags tells fswatch to print the event flags along side the event path. You can use –event-field-seperator option to print events using the particular separator.
$ fswatch --events-flags ~ /var/log/auth.log
To print the numeric value of an event indicating changes in your home directory and /var/log/auth.log file, use -n or —numeric option as below:
$ fswatch --numeric ~ /var/log/auth.log
Perhaps you can look through the fswatch man page for detailed usage options and information:
For more information and usage, visit fswatch Github repository: https://github.com/emcrisostomo/fswatch
In this post, we covered a simple command line utility to help Linux users get notified when the contents of specified files or directory hierarchies are modified.
I hope all went well with the installation, if that is not the case for you, make an effort to reach us via the feedback form below. In addition, in case you have used it before, you may want to offer us some thoughts about your experience with fswatch.
Track file changes using auditd
Most of Linux distributions comes with Linux Auditing System that makes it possible to track file changes, file accesses as well as system calls. It’s pretty useful functionality for sysadmins who wish to know who and when accessed and/or changed sensitive files like /etc/passwd, /etc/sudoers or others.
Daemon auditd that usually runs in background and starts after reboot by default logs those events into /var/log/audit.log file (or into other file if different syslog facility is specified). The common usage is to list all files which should be watched and search auditd’s logs from time to time. For example, I prefer to track any file changes into /etc/passwd, reading/writing of /etc/sudoers, executing of /bin/some/binary or just everything (read, write, attributes changes, executing) for my /very/important/file.
In order to configure that you’ll need two commands: auditctl and ausearch. First one is for configuring auditd daemon (e.g. setting a watch on a file), second one is for searching auditd logs (it’s possible to use grep against /var/log/audit.log too but ausearch command makes this task easier).
Install and start Linux Auditing System
If it happened that auditd daemon isn’t installed in your system then you can fix this by one of below commands:
| sudo apt-get install audit |
| sudo yum install audit |
The next step is to make sure that auditd is running, if command ps ax | grep [a]udit shows nothing then start auditd using command:
| /etc/init.d/auditd start |
As soon as auditd daemon is started we can start configuring it for tracking file changes using auditctl command.
Make auditd to log all file changes
This command will add a rule for auditd daemon to monitor file /etc/passwd file (see option -w /etc/passwd) for reading or changing the atributes (see option -p ra, where r is for read, a is for attribute). Also this command specifies filter key (-k passwd-ra) that will uniquely identify auditd records in its logs files.
Now let’s test this rule: optput the last 20 lines of /etc/passwd file and then search audit log for corresponding records
| tail /etc/passwd |
| [root@test root]# ausearch -k passwd-ra —- time->Wed Jul 4 15:17:14 2012 type=CONFIG_CHANGE msg=audit(1341407834.821:207310): auid=500 ses=23783 op=”add rule” key=”passwd-ra” list=4 res=1 —- time->Wed Jul 4 15:17:20 2012 type=PATH msg=audit(1341407840.181:207311): item=0 name=”/etc/passwd” inode=31982841 dev=09:02 mode=0100644 ouid=0 ogid=0 rdev=00:00 type=CWD msg=audit(1341407840.181:207311): cwd=”/home/artemn” type=SYSCALL msg=audit(1341407840.181:207311): arch=c000003e syscall=2 success=yes exit=3 a0=7fffecd41817 a1=0 a2=0 a3=7fffecd40b40 items=1 ppid=642502 pid=521288 auid=500 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=pts0 ses=23783 comm=”tail” exe=”/usr/bin/tail” key=”passwd-ra” |
As you can see the output of second command shows that auditd has one record for filter key ‘passwd-ra’, it shows that root user (uid=0 gid=0) has read file /etc/passwd using command tail (comm=”tail” exe=”/usr/bin/tail”) at July 4, 2012 (time->Wed Jul 4 15:17:20 2012).
Utility ausearch is pretty powerful so I recommend to read output of man ausearch, in the meantime here are some useful examples:
| ausearch -x /bin/grep ausearch -x rm |
This approach allows to scan auditd records for certain executable, e.g. if you’d like to see if any of watched files was deleted (or not) using command rm then you should use second command of above two.
This one will show you all records for certain UID (username).
Track file changes using auditd
Most of Linux distributions comes with Linux Auditing System that makes it possible to track file changes, file accesses as well as system calls. It’s pretty useful functionality for sysadmins who wish to know who and when accessed and/or changed sensitive files like /etc/passwd, /etc/sudoers or others.
Daemon auditd that usually runs in background and starts after reboot by default logs those events into /var/log/audit.log file (or into other file if different syslog facility is specified). The common usage is to list all files which should be watched and search auditd’s logs from time to time. For example, I prefer to track any file changes into /etc/passwd, reading/writing of /etc/sudoers, executing of /bin/some/binary or just everything (read, write, attributes changes, executing) for my /very/important/file.
In order to configure that you’ll need two commands: auditctl and ausearch. First one is for configuring auditd daemon (e.g. setting a watch on a file), second one is for searching auditd logs (it’s possible to use grep against /var/log/audit.log too but ausearch command makes this task easier).
Install and start Linux Auditing System
If it happened that auditd daemon isn’t installed in your system then you can fix this by one of below commands:
sudo apt-get install audit
The next step is to make sure that auditd is running, if command ps ax | grep [a]udit shows nothing then start auditd using command:
As soon as auditd daemon is started we can start configuring it for tracking file changes using auditctl command.
Make auditd to log all file changes
auditctl -w /etc/passwd -k passwd-ra -p ra
This command will add a rule for auditd daemon to monitor file /etc/passwd file (see option -w /etc/passwd) for reading or changing the atributes (see option -p ra, where r is for read, a is for attribute). Also this command specifies filter key (-k passwd-ra) that will uniquely identify auditd records in its logs files.
Now let’s test this rule: optput the last 20 lines of /etc/passwd file and then search audit log for corresponding records
[[email protected] artemn]# ausearch -k passwd-ra ---- time->Wed Jul 4 15:17:14 2012 type=CONFIG_CHANGE msg=audit(1341407834.821:207310): auid=500 ses=23783 op="add rule" key="passwd-ra" list=4 res=1 ---- time->Wed Jul 4 15:17:20 2012 type=PATH msg=audit(1341407840.181:207311): item=0 name="/etc/passwd" inode=31982841 dev=09:02 mode=0100644 ouid=0 ogid=0 rdev=00:00 type=CWD msg=audit(1341407840.181:207311): cwd="/home/artemn" type=SYSCALL msg=audit(1341407840.181:207311): arch=c000003e syscall=2 success=yes exit=3 a0=7fffecd41817 a1=0 a2=0 a3=7fffecd40b40 items=1 ppid=642502 pid=521288 auid=500 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=pts0 ses=23783 comm="tail" exe="/usr/bin/tail" key="passwd-ra"
As you can see the output of second command shows that auditd has one record for filter key ‘passwd-ra’, it shows that root user (uid=0 gid=0) has read file /etc/passwd using command tail (comm=”tail” exe=”/usr/bin/tail”) at July 4, 2012 (time->Wed Jul 4 15:17:20 2012).
Utility ausearch is pretty powerful so I recommend to read output of man ausearch , in the meantime here are some useful examples:
ausearch -x /bin/grep ausearch -x rm
This approach allows to scan auditd records for certain executable, e.g. if you’d like to see if any of watched files was deleted (or not) using command rm then you should use second command of above two.
This one will show you all records for certain UID (username).