- Linux users and sudo
- Notes for new Debian users
- Why not sudo?
- Why sudo?
- Users and sudo
- Verifying sudo membership
- Add existing user from commandline
- Creating users with sudo
- Creating new user while installing OS
- Creating new user from commandline
- Configuration overview
- Problems and tips
- Sorry, user jdoe is not allowed to execute .
- The include directive
- sudoers is read-only
- Require root password
- No password prompt for sudo user
- Customize credentials cache timeout
- See also
- The Ultimate Guide to Linux - Creating a Sudo User
- How to Create a New User
- Use adduser or useradd to add a new user
- Use passwd to update the new user's password
- Give the New User Sudo Permissions
- On Debian systems (Ubuntu / Linux Mint / ElementryOS), add users to the sudo group
- On RHEL based systems (Fedora / CentOS), add users to the wheel group
- How to Delete a User
- Debian based systems (Ubuntu / Linux Mint / ElementryOS)
- RHEL based systems (Fedora / CentOS)
- How To Add User To Sudoers & Add User To Sudo Group on Ubuntu
- Steps to Add Sudo User on Ubuntu
- Step 1: Create New User
- Step 2: Add User to Sudo Group
- Step 3: Verify User Belongs to Sudo Group
- Step 4: Verify Sudo Access
Linux users and sudo
Sudo (sometimes considered as short for Super-user do) is a program designed to let system administrators allow some users to execute some commands as root (or another user). The basic philosophy is to give as few privileges as possible but still allow people to get their work done. Sudo is also an effective way to log who ran which command and when.
Notes for new Debian users
Some new Debian users, usually coming from Ubuntu, are shocked by problems like «sudo not working in Debian». However, this situation only happens if you have set a root password during your Debian installation.
If you like sudo and you want to install it (even if you skipped it during your Debian installation), you can, but in the way without sudo, so, becoming root with the su command, installing it, and adding yourself in the sudo group and doing a full logout/login.
$ su - Password: (enter here the password of the root user that you specified during your Debian installation, and press Enter) # apt install sudo # adduser jhon-smith sudo
(Obviously just replace «jhon-smith» with your personal username)
Then please do a full logout and login again.
Why not sudo?
Note that, historically, all Unix-like systems worked perfectly even before «sudo» was invented. Moreover, having a system without sudo could still give security benefits, since the sudo package could be affected by security bugs, as any additional part of the system.
Lot of Debian users do not install sudo. Instead, they open a terminal as root (for example with su - from a normal user). So you do not have to put «sudo» in front of any command.
Why sudo?
- Nobody needs to know the root password (sudo prompts for the current user’s password). Extra privileges can be granted to individual users temporarily, and then taken away without the need for a password change.
- It’s easy to run only the commands that require special privileges via sudo; the rest of the time, you work as an unprivileged user, which reduces the damage that mistakes can cause.
- Auditing/logging: when a sudo command is executed, the original username and the command are logged.
For the reasons above, switching to root using sudo -i (or sudo su) is usually deprecated because it cancels most of the above features.
Users and sudo
Debian’s default configuration allows users in the sudo group to run any command via sudo.
Verifying sudo membership
uid=1001(foo) gid=1001(foo) groups=1001(foo),27(sudo)
Add existing user from commandline
# adduser foo # adduser foo sudo
After being added to a new group the user must log out and then log back in again for the new group to take effect. Groups are only assigned to users at login time. A most common source of confusion is that people add themselves to a new group but then do not log out and back in again and then have problems because the group is not assigned; be sure to verify group membership.
Creating users with sudo
You can also create new users with sudo membership:
Creating new user while installing OS
As of DebianSqueeze, if you give root an empty password during installation, sudo will be installed and the first user will be able to use it to gain root access (currently, the user will be added to the sudo group). The system will also configure gksu and aptitude to use sudo. You should still verify group membership after logging in as the installed user.
Creating new user from commandline
(or first get root as in previous section). You should then login as the new user and verify group membership.
Configuration overview
Now, if you want to allow certain users to execute certain programs, here’s a quick example (for more information, read the fine manual), which you can put in a file in /etc/sudoers.d, probably using visudo -f /etc/sudoers.d/myfile.
User_Alias MYADMINS = jdoe Cmnd_Alias SHUTDOWN = /sbin/reboot, /sbin/poweroff Cmnd_Alias PKGMGMT = /usr/bin/dpkg, /usr/bin/apt-get, /usr/bin/aptitude # Users listed above (MYADMINS) can run package managers and reboot the system. MYADMINS ALL = PKGMGMT, SHUTDOWN
Problems and tips
Sorry, user jdoe is not allowed to execute .
$ sudo test We trust you have received the usual lecture from the local System Administrator. It usually boils down to these three things: #1) Respect the privacy of others. #2) Think before you type. #3) With great power comes great responsibility. [sudo] password for jdoe: Sorry, user jdoe is not allowed to execute '/usr/bin/test' as root on localhost.
This message means what it says: the user you’re running as isn’t allowed to execute the given command on the given machine. One confusing possible reason for this is that the administrator has just added user jdoe to a privileged group — but you’re still using the old login, which doesn’t have that new group information, and therefore has no new sudo-ing rights. People in this situation are usually advised to log out completely and back in again, though you can sometimes get away with just performing a «re-login on the spot» with su - $USER or changing group with newgrp sudo.
The include directive
This makes it possible for other packages to provide snippets in /etc/sudoers.d/ which modify the configuration of sudo. It may look as if it needs to be edited to take out the leading numbersign (a.k.a. "hash" or "pound"), but no, the '#' is part of the directive!
It is recommended that you make local changes in a snippet as well.
sudoers is read-only
Yes, the file /etc/sudoers is intentionally set read-only, even for root!
The explanation is that it was set up this way to motivate admins to only ever edit it via the command visudo, which provides additional checking before leaving the new file in place. You might think that the fix for a mangled /etc/sudoers, the fix may be as simple as su -c visudo, but sudo is often used in a place where simply su'ing to root is not possible since you simply don't know the root password.
Beware, most text editors will let you edit the file without complaining about the read-only bit, so you might not automatically get this additional protection.
Require root password
If you want to require the root password for use of sudo, rather than the user password, add the line:
No password prompt for sudo user
If you want sudo group members to execute commands without password, add the line:
Customize credentials cache timeout
As default, after asking a password, your credentials are cached by sudo and last for 15 minutes. You can change this behavior using the command visudo and customizing the timeout for a specific user:
Defaults:foobar timestamp_timeout=30
See also
- Manpages: sudoers(5), sudo(8), visudo(8), sudoedit(8), sudoreplay(8)
- Doas - A lighter and more minimalistic tool for the same purpose, with simpler configuration.
The Ultimate Guide to Linux - Creating a Sudo User
sudo stands for either "superuser do" or "switch user do", and sudo users can execute commands with root/administrative permissions, even malicious ones. Be careful who you grant sudo permissions to – you are quite literally handing them the key your house.
Before creating a new sudo user, you must first create a new user.
How to Create a New User
Use adduser or useradd to add a new user
Be sure to replace username with the user that you want to create. Also, note that to create a new user, you must also be a sudo user yourself.
Use passwd to update the new user's password
A strong password is highly recommended!
Give the New User Sudo Permissions
After creating a new user, add them to the appropriate group using the usermod command.
On Debian systems (Ubuntu / Linux Mint / ElementryOS), add users to the sudo group
sudo usermod -aG sudo usernameOn RHEL based systems (Fedora / CentOS), add users to the wheel group
sudo usermod -aG wheel usernameHow to Delete a User
To delete a user, use the following commands.
Debian based systems (Ubuntu / Linux Mint / ElementryOS)
RHEL based systems (Fedora / CentOS)
That's all you need to know about creating a new sudo user in Linux. And remember, "With great power comes great responsibility."
If this article was helpful, tweet it .
Learn to code for free. freeCodeCamp's open source curriculum has helped more than 40,000 people get jobs as developers. Get started
freeCodeCamp is a donor-supported tax-exempt 501(c)(3) charity organization (United States Federal Tax Identification Number: 82-0779546)
Our mission: to help people learn to code for free. We accomplish this by creating thousands of videos, articles, and interactive coding lessons - all freely available to the public. We also have thousands of freeCodeCamp study groups around the world.
Donations to freeCodeCamp go toward our education initiatives, and help pay for servers, services, and staff.
How To Add User To Sudoers & Add User To Sudo Group on Ubuntu
The sudo command is the preferred means to handle elevated permissions. In supported versions of Ubuntu, using the sudo command will grant elevated permissions for 15 minutes.
Standard user accounts are restricted from performing sensitive tasks, such as viewing the contents of the /root directory. This prevents the accidental use of commands with massive consequences. It also makes it more difficult for intruders to compromise a system. However, sometimes you need to run an administrative command. Sudo – or Super User Do – grants you privileges to run sensitive tasks.
This simple tutorial will show you how to add a new user on Ubuntu and provide sudo access.
- A system running a supported version of Ubuntu
- Access to a root user account or another account with sudo privileges
- Access to a terminal window/command line (Ctrl–Alt–T)
Note: Linux Sudo Command tutorials also available for CentOS and Debian.
Steps to Add Sudo User on Ubuntu
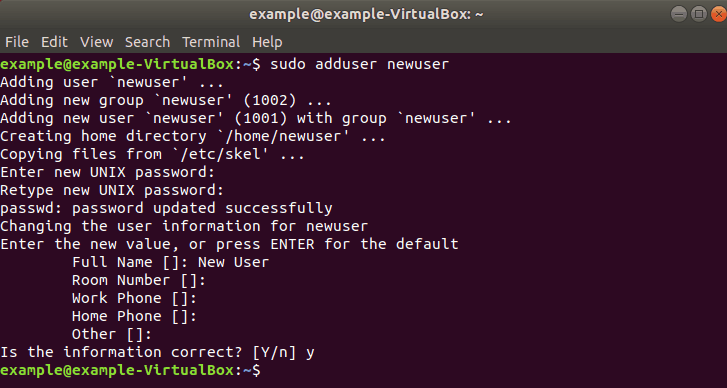
Step 1: Create New User
1. Log into the system with a root user or an account with sudo privileges.
2. Open a terminal window and add a new user with the command:
The adduser command creates a new user, plus a group and home directory for that user.
You may get an error message that you have insufficient privileges. (This typically only happens for non-root users.) Get around it by entering:
3. You can replace newuser with any username you wish. The system will add the new user; then prompt you to enter a password. Enter a great secure password, then retype it to confirm.
4. The system will prompt you to enter additional information about the user. This includes a name, phone numbers, etc. – these fields are optional, and can be skipped by pressing Enter.
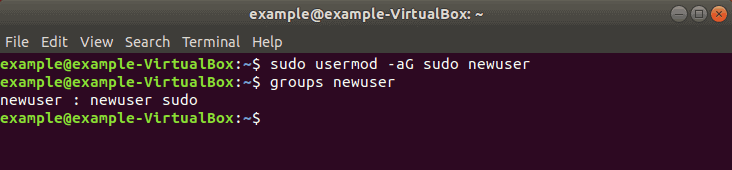
Step 2: Add User to Sudo Group
Most Linux systems, including Ubuntu, have a user group for sudo users. To grant the new user elevated privileges, add them to the sudo group.
In a terminal, enter the command:
Replace newuser with the username that you entered in Step 1.
Again, if you get an error, run the command with sudo as follows:
sudo usermod -aG sudo newuserThe -aG option tells the system to append the user to the specified group. (The -a option is only used with G .)
Note: Usermod command is a useful tool for user management. To learn more about its options, refer to our guide How To Use The Usermod Command In Linux.
Step 3: Verify User Belongs to Sudo Group
Enter the following to view the groups a user belongs to:
The system will respond by listing the username and all groups it belongs to, for example: newuser : newuser sudo
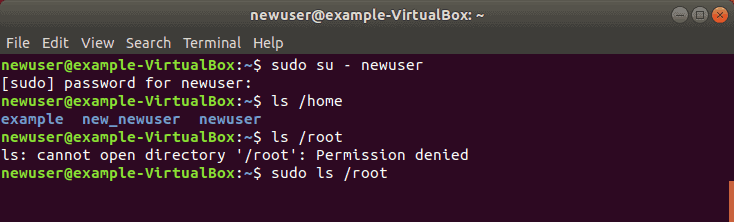
Step 4: Verify Sudo Access
Replace newuser with the username you entered in Step 1. Enter your password when prompted. You can run commands as normal, just by typing them.
However, some commands or locations require elevated privileges. If you try to list the contents of the /root directory, you’ll get an access denied error: ls /root
The command can be executed with:
The system will prompt for your password. Use the same password you set in Step 1. You should now see the contents of the /root directory.
Now you know how to add and create a user with sudo privileges on Ubuntu.
Before sudo, users would log in to their systems with full permissions over the entire system with the su command. This was risky as users could be exploited by tricking them into entering malicious commands. These vulnerabilities were solved by limiting account privileges. However, administrators still had to log out of their account and into an admin account to perform routine tasks.
The sudo command in Ubuntu strikes a balance – protecting user accounts from malicious or inadvertent damage while allowing a privileged user to run administrative tasks. To learn more about the difference between these commands, check out Sudo vs. Su.