- How to find out where a program is looking for libraries
- 3 Answers 3
- How to check which libraries are used by a program or process on Linux ?
- Check shared library dependencies of a running process
- How to check what libraries are used by a program or process on Linux
- Check Shared Library Dependencies of a Program Executable
- Check Shared Library Dependencies of a Running Process
- Support Xmodulo
- Get list of static libraries used in an executable
- 5 Answers 5
- Linked
- Related
- Hot Network Questions
- Subscribe to RSS
How to find out where a program is looking for libraries
The other day I came across a linux command that let me see where a program is expecting to find its libraries. It is very useful to solve library dependency problems for not so popular or proprietary software. I used ldd , it was very informative, but missed one crucial piece of information for me: ldd -v ./my_executable gave good information for libraries that my_executable can link to. But for those it can not link/find, ldd only gave information like:
3 Answers 3
on linux you can use the LD_DEBUG. This link is helpful.
Probably you need the strace command Take a look here http://www.thegeekstuff.com/2011/11/strace-examples/
strace -e open ./my_executable shows pretty much what I want to see. I had the impression that the command I was looking for gives more concise output though. I accept this as the answer anyway.
The information about library paths is stored in /etc/ld.so.conf :
/usr/local/lib64 /usr/local/lib include /etc/ld.so.conf.d/*.conf # /lib64, /lib, /usr/lib64 and /usr/lib gets added # automatically by ldconfig after parsing this file. # So, they do not need to be listed. See man ldconfig for more information.
I am aware of this. However, some programs will look for library from /path/to/installation/dir/libraries . What worse, this path can be hard-coded, and it is different from the actual installation path.
But why should ldd list all directories where it is looking? You can get this info from /etc/ld.so.conf and you can also look if LD_LIBRARY_PATH is set. See this documentation.
How to check which libraries are used by a program or process on Linux ?
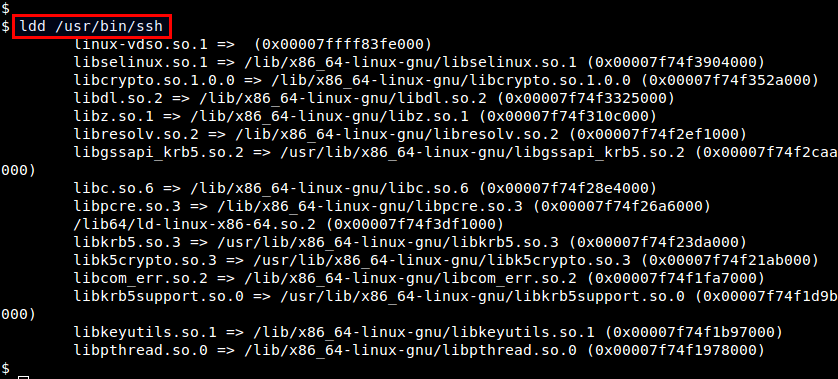
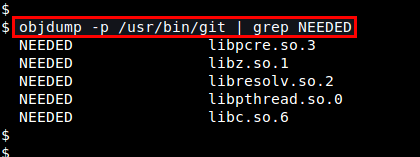
To find out what libraries a particular executable depends on, you can use ldd command. This command invokes dynamic linker to find out library dependencies of an executable.[ram@linuxforfreshers.com]$ldd /usr/bin/ssh linux-vdso.so.1 => (0x00007ffe099dc000) libselinux.so.1 => /lib/x86_64-linux-gnu/libselinux.so.1 (0x00007f578f64a000) libcrypto.so.1.0.0 => /lib/x86_64-linux-gnu/libcrypto.so.1.0.0 (0x00007f578f26e000) libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007f578f069000) libz.so.1 => /lib/x86_64-linux-gnu/libz.so.1 (0x00007f578ee50000) libresolv.so.2 => /lib/x86_64-linux-gnu/libresolv.so.2 (0x00007f578ec35000) libgssapi_krb5.so.2 => /usr/lib/x86_64-linux-gnu/libgssapi_krb5.so.2 (0x00007f578e9ed000) libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f578e628000) libpcre.so.3 => /lib/x86_64-linux-gnu/libpcre.so.3 (0x00007f578e3ea000) /lib64/ld-linux-x86-64.so.2 (0x000055f5ccd53000) libkrb5.so.3 => /usr/lib/x86_64-linux-gnu/libkrb5.so.3 (0x00007f578e11e000) libk5crypto.so.3 => /usr/lib/x86_64-linux-gnu/libk5crypto.so.3 (0x00007f578deef000) libcom_err.so.2 => /lib/x86_64-linux-gnu/libcom_err.so.2 (0x00007f578dceb000) libkrb5support.so.0 => /usr/lib/x86_64-linux-gnu/libkrb5support.so.0 (0x00007f578dadf000) libkeyutils.so.1 => /lib/x86_64-linux-gnu/libkeyutils.so.1 (0x00007f578d8db000) libpthread.so.0 => /lib/x86_64-linux-gnu/libpthread.so.0 (0x00007f578d6bc000)Note that it is NOT recommended to run ldd with any untrusted third-party executable because some versions of ldd may directly invoke the executable to identify its library dependencies, which can be security risk.Instead, a safer way to show library dependencies of an unknown application binary is to use the following command.objdump -p /path/to/program [ram@linuxforfreshers.com]$objdump -p /usr/bin/ssh | grep NEEDED NEEDED libselinux.so.1 NEEDED libcrypto.so.1.0.0 NEEDED libdl.so.2 NEEDED libz.so.1 NEEDED libresolv.so.2 NEEDED libgssapi_krb5.so.2 NEEDED libc.so.6
Check shared library dependencies of a running process
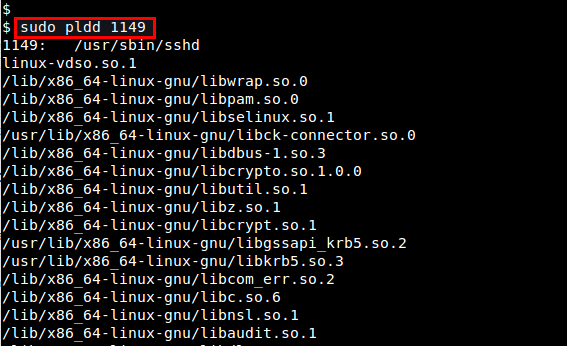
If you want to find out what shared libraries are loaded by a running process, you can use pldd command, which shows all shared objects loaded into a process at run-time. lsof -P -T -p Application_PID
How to check what libraries are used by a program or process on Linux
Question: I would like to know which shared libraries are loaded at run-time when I invoke a particular executable. Is there any way to identify shared library dependencies of a program executable or a running process on Linux?
You can use the following methods to identiy which shared librariies a given program executable (e.g., /path/to/program ) or a given running process (e.g., PID 1149 ) depends on.
Check Shared Library Dependencies of a Program Executable
To find out what libraries a particular executable depends on, you can use ldd command. This command invokes dynamic linker to find out library dependencies of an executable.
Note that it is not recommended to run ldd with any untrusted third-party executable because some versions of ldd may directly invoke the executable to identify its library dependencies, which can be security risk.
Instead, a safer way to show library dependencies of an unknown application binary is to use the following command.
$ objdump -p /path/to/program | grep NEEDED
Check Shared Library Dependencies of a Running Process
If you want to find out what shared libraries are loaded by a running process, you can use pldd command, which shows all shared objects loaded into a process at run-time.
Note that you need root privilege to run pldd command.
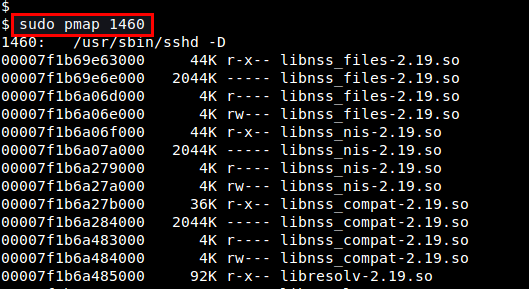
Alternatively, a command line utility called pmap , which reports memory map of a process, can also show shared library dependencies of a running process.
Support Xmodulo
This website is made possible by minimal ads and your gracious donation via PayPal or credit card
Please note that this article is published by Xmodulo.com under a Creative Commons Attribution-ShareAlike 3.0 Unported License. If you would like to use the whole or any part of this article, you need to cite this web page at Xmodulo.com as the original source.
Get list of static libraries used in an executable
Since ldd lists only the dynamic libraries, is there a way to extract the information about the static libraries used to create the executable?
5 Answers 5
ldd shows dynamically linked libraries
nm shows the symbols in the file.
To see which symbols come from static libraries requires running nm against those libraries to get a list of the symbols (functions, etc.) in them, then comparing them to what your list of symbols from nm .
You compare lists with the comm command. See man comm for details.
This was taken from this forum here.
As @Goz and anon point out, this only works if the binary hasn’t been stripped / contains debugging information. Names are not necessary (and are not even used) after a static library has been linked into an application — the calls are all by address.
This does not answer the question. «running nm against those libraries» is not possible if you do not know the libraries; and there are libraries used implicitly in linking.
If its an unknown binary, we don’t know what libraries are present. So «running nm against those libraries » sounds self defeating.
No, the names of the libraries are discarded during the linking process. However, if your executable contains debug information (i.e. it was compiled with the -g flag), you may be able to get information from that.
If you have the source code and don’t want to go through all the code for this, you can generate map file while compiling to know which static libraries are linked.
For example g++ -Xlinker -Map=a.map main.c , check the map file for linked static library information.
There is no way to get the list of static libraries inside some ELF executable.
Because for the linker, a static library is just used as a «lazy» set of members. So the resulting ELF executable would only contain the members needed to link it. So members like foo2.o of libfoo.a are linked as if object file foo2.o was linked into the executable (provided some symbol defined in foo2 is needed, i.e. is referenced somewhere).
Of course, using nm , or objdump , or readelf , or strings on some ELF executable may give some hints about what object files (including those coming from static libraries) are inside it, because you’ll see symbols defined in (members of) those static libraries (or literal strings used inside them).
what kind hints do you mean? Can you give examples? Can you point me to source where I can find more of these hints?
Using readelf for example will show you functions, objects, symbols that are used in the binary. These can serve as hints to find the libraries that were used.For example you may see the Curl_http function in there and know that libcurl is most likely used by the binary and if it is not dynamically linked it has to be linked statically.
Unless a given compiler stores some sort of meta data inside the binary then, no. A static library is code that is directly compiled into the binary.
Linked
Related
Hot Network Questions
Subscribe to RSS
To subscribe to this RSS feed, copy and paste this URL into your RSS reader.
Site design / logo © 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA . rev 2023.7.13.43531
By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy.