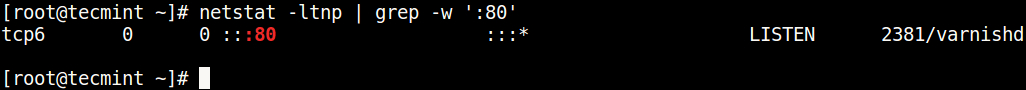Finding the PID of the process using a specific port?
I am installing hadoop on my Ubuntu system. When I start it, it reports that port 9000 is busy. I used:
tcp 0 0 127.0.0.1:9000 0.0.0.0:* LISTEN netstat command might work in many operations systems to allow you get that, you just have to find the arguments that will ensure it will show pids along each known opened port.
7 Answers 7
Your existing command doesn’t work because Linux requires you to either be root or the owner of the process to get the information you desire.
On modern systems, ss is the appropriate tool to use to get this information:
$ sudo ss -lptn 'sport = :80' State Local Address:Port Peer Address:Port LISTEN 127.0.0.1:80 *:* users:(("nginx",pid=125004,fd=12)) LISTEN ::1:80 . * users:(("nginx",pid=125004,fd=11)) You can also use the same invocation you’re currently using, but you must first elevate with sudo :
$ sudo netstat -nlp | grep :80 tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 125004/nginx $ sudo lsof -n -i :80 | grep LISTEN nginx 125004 nginx 3u IPv4 6645 0t0 TCP 0.0.0.0:80 (LISTEN) @AdamB Unless a Mac user arrived here searching for Finding the PID of the process using a specific port
Also you can use lsof utility. Need to be root.
# lsof -i :25 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME exim4 2799 Debian-exim 3u IPv4 6645 0t0 TCP localhost:smtp (LISTEN) exim4 2799 Debian-exim 4u IPv6 6646 0t0 TCP localhost:smtp (LISTEN) This command will also give you processes with established connections, not just processes that are listening .
Not necessarily to be root. And, for those who want to get PID only, you can lsof -i :25 -Fp , which produces output like p1234 .
Important to note that you may need to run as sudo as some processes may be inaccessible to the user.
I am using «CentOS 7 minimal» which has nor netstat neither lsof . But a lot of linux distributions have the socket statistics command (i.e. ss ).
Here is an example of execution:
# ss -tanp | grep 6379 LISTEN 0 128 127.0.0.1:6379 *:* users:(("redis-server",pid=2531,fd=4)) USER PID ACCESS COMMAND 22/tcp: root 598 F. sshd This is a good thing to remember generally. Commands in Linux generally won’t give information on processes started by root/sudo unless the command is run with Sudo. This is true even when the command does not normally need sudo to run correctly.
Running the command with sudo would give you the PID . On my development machine I get:
$ netstat -nlp | grep 8080 tcp6 0 0 . 8080 . * LISTEN - $ sudo netstat -nlp | grep 8080 tcp6 0 0 . 8080 . * LISTEN 16449/java And as mentioned in other answers you can also use the ss or the lsof commands.
I’m working on a Yocto Linux system that has a limited set of available Linux tools. I managed to find the process of a running port using the following commands (where I find the process using port 1883):
root@root:~# netstat -lt Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 0.0.0.0:hostmon 0.0.0.0:* LISTEN tcp 0 0 localhost.localdomain:domain 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:9080 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:1883 0.0.0.0:* LISTEN tcp 0 0 . hostmon . * LISTEN tcp 0 0 localhost:domain . * LISTEN tcp 0 0 . ssh . * LISTEN tcp 0 0 . 1883 . * LISTEN root@root:~# fuser 1883/tcp 290 root@root:~# ps | grep 290 290 mosquitt 25508 S /usr/sbin/mosquitto -c /etc/mosquitto/mosquitto.conf 12141 root 8444 S grep 290 As we can see above, it’s the program /usr/sbin/mosquitto that’s using port 1883.
Proto Recv-Q Send-Q Local Address Foreign Address State Benutzer Inode PID/Program name tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 0 55233 - tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN 1000 3166326 364815/node tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN 127 36032 - tcp 0 0 127.0.0.1:587 0.0.0.0:* LISTEN 0 55234 - tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 0 2927660 - tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN 127 36034 - tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 0 30995 - tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN 101 26903 - tcp 0 0 127.0.0.1:6379 0.0.0.0:* LISTEN 132 32262 - tcp6 0 0 127.0.0.1:9300 . * LISTEN 129 40952 - tcp6 0 0 . 35729 . * LISTEN 1000 3088940 355480/grunt tcp6 0 0 ::1:9300 . * LISTEN 129 40945 - tcp6 0 0 ::1:9200 . * LISTEN 129 41261 - tcp6 0 0 ::1:631 . * LISTEN 0 2927659 - tcp6 0 0 127.0.0.1:9200 . * LISTEN 129 41262 - tcp6 0 0 . 9003 . * LISTEN 1000 3234646 373445/code tcp6 0 0 . 22 . * LISTEN 0 31006 - tcp6 0 0 . 80 . * LISTEN 0 940224 - tcp6 0 0 ::1:6379 . * LISTEN 132 32263 - udp 0 0 127.0.0.53:53 0.0.0.0:* 101 26902 - udp 0 0 0.0.0.0:631 0.0.0.0:* 0 2927684 - udp 0 0 0.0.0.0:5353 0.0.0.0:* 115 29345 - udp 0 0 0.0.0.0:42443 0.0.0.0:* 115 29347 - udp6 0 0 . 5353 . * 115 29346 - udp6 0 0 . 34477 . * 115 29348 - 3 Ways to Find Out Which Process Listening on a Particular Port
A port is a logical entity that represents an endpoint of communication and is associated with a given process or service in an operating system. In previous articles, we explained how to find out the list of all open ports in Linux and how to check if remote ports are reachable using the Netcat command.
In this short guide, we will show different ways of finding the process/service listening on a particular port in Linux.
1. Using netstat Command
netstat (network statistics) command is used to display information concerning network connections, routing tables, interface stats, and beyond. It is available on all Unix-like operating systems including Linux and also on Windows OS.
In case you do not have it installed by default, use the following command to install it.
$ sudo apt-get install net-tools [On Debian/Ubuntu & Mint] $ sudo dnf install net-tools [On CentOS/RHEL/Fedora and Rocky Linux/AlmaLinux] $ pacman -S netstat-nat [On Arch Linux] $ emerge sys-apps/net-tools [On Gentoo] $ sudo dnf install net-tools [On Fedora] $ sudo zypper install net-tools [On openSUSE]
Once installed, you can use it with the grep command to find the process or service listening on a particular port in Linux as follows (specify the port).
In the above command, the flags.
- l – tells netstat to only show listening sockets.
- t – tells it to display tcp connections.
- n – instructs it to show numerical addresses.
- p – enables showing of the process ID and the process name.
- grep -w – shows matching of exact string (:80).
Note: The netstat command is deprecated and replaced by the modern ss command in Linux.
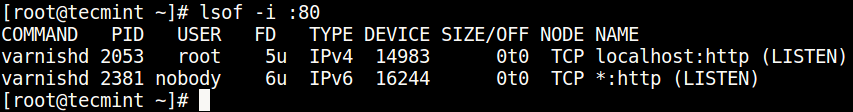
2. Using lsof Command
lsof command (List Open Files) is used to list all open files on a Linux system.
To install it on your system, type the command below.
$ sudo apt-get install lsof [On Debian, Ubuntu and Mint] $ sudo yum install lsof [On RHEL/CentOS/Fedora and Rocky Linux/AlmaLinux] $ sudo emerge -a sys-apps/lsof [On Gentoo Linux] $ sudo pacman -S lsof [On Arch Linux] $ sudo zypper install lsof [On OpenSUSE]
To find the process/service listening on a particular port, type (specify the port).
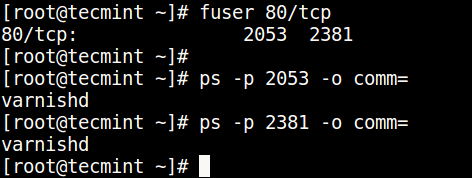
3. Using fuser Command
fuser command shows the PIDs of processes using the specified files or file systems in Linux.
You can install it as follows:
$ sudo apt-get install psmisc [On Debian, Ubuntu and Mint] $ sudo yum install psmisc [On RHEL/CentOS/Fedora and Rocky Linux/AlmaLinux] $ sudo emerge -a sys-apps/psmisc [On Gentoo Linux] $ sudo pacman -S psmisc [On Arch Linux] $ sudo zypper install psmisc [On OpenSUSE]
You can find the process/service listening on a particular port by running the command below (specify the port).
Then find the process name using PID number with the ps command like so.
$ ps -p 2053 -o comm= $ ps -p 2381 -o comm=
You can also check out these useful guides about processes in Linux.
You might also like:
That’s all! Do you know of any other ways of finding the process/service listening on a particular port in Linux, let us know via the comment form below.
How to find ports opened by process ID in Linux?
Hmm..I don’t seem to have the —all and —program options. I’m using OSX. Brew doesn’t seem to have a formula for it either.
-n will dramatically speed things up by not resolving hostnames. netsta -tupan is a good default command all and easy to remember.
You can use the command below:
As a side note, netstat -ao will read the /proc/PID/tcp etc to see the ports opened by the process. This means that its reading information supplied by the system (the linux KERNEL), and is in no way directly looking on the network interface or other means. Same goes for lsof.
If you are doing this as a security measure, you failed. You should never (NEVER EVER) trust the output of netstat, even if you are 100% sure you are in fact running a real netstat program (as opposed to a trojaned version) or any other program that reads the /proc filesystem. Some people seem to think that netstat, ls, ps or any other of the standard unix tools do some sort of magic and poll information from the sources, the truth is all of them rely on the /proc filesystem to get all of their data, which can be easily subverted by a rootkit or hypervisor.
If you’re dealing with a rootkitted system or a compromised hypervisor, you can’t trust anything, including something that purports to look directly at the network interface.
You can use the netstat command line tool with the -p command line argument:
-p (Linux):
Process: Show which processes are using which sockets (similar to -b under Windows). You must be root to do this.
To display all ports open by a process with id $PID :
In some embedded devices or with old version of Linux, the problem is netstat do not have —process or -p options available.
The following script shows process with its IP and port, you must be root.
#!/bin/bash for protocol in tcp udp ; do #echo "protocol $protocol" ; for ipportinode in `cat /proc/net/$ | awk '/.*:.*:.*/'` ; do #echo "#ipportinode=$ipportinode" inode=`echo "$ipportinode" | cut -d"|" -f3` ; if [ "#$inode" = "#" ] ; then continue ; fi lspid=`ls -l /proc/*/fd/* 2>/dev/null | grep "socket:\[$inode\]" 2>/dev/null` ; pid=`echo "lspid=$lspid" | awk 'BEGIN /socket/'` ; if [ "#$pid" = "#" ] ; then continue ; fi exefile=`ls -l /proc/$pid/exe | awk 'BEGIN ">/->/'` #echo "$protocol|$pid|$ipportinode" echo "$protocol|$pid|$ipportinode|$exefile" | awk ' BEGIN function iphex2dec(ipport) < ret=sprintf("%d.%d.%d.%d: %d","0x"substr(ipport,1,2),"0x"substr(ipport,3,2), "0x"substr(ipport,5,2),"0x"substr(ipport,7,2),"0x"substr(ipport,10,4)) ; if( ret == "0.0.0.0:0" ) #compatibility others awk versions < ret= strtonum("0x"substr(ipport,1,2)) ; ret=ret "." strtonum("0x"substr(ipport,3,2)) ; ret=ret "." strtonum("0x"substr(ipport,5,2)) ; ret=ret "." strtonum("0x"substr(ipport,7,2)) ; ret=ret ":" strtonum("0x"substr(ipport,10)) ; >return ret ; > < print $1" pid:"$2" local="iphex2dec($3)" remote="iphex2dec($4)" inode:"$5" exe=" $6 ; >' ; #ls -l /proc/$pid/exe ; done ; done tcp pid:1454 local=1.0.0.127:5939 remote=0.0.0.0:0 inode:13955 exe=/opt/teamviewer/tv_bin/teamviewerd tcp pid:1468 local=1.1.0.127:53 remote=0.0.0.0:0 inode:12757 exe=/usr/sbin/dnsmasq tcp pid:1292 local=0.0.0.0:22 remote=0.0.0.0:0 inode:12599 exe=/usr/sbin/sshd tcp pid:4361 local=1.0.0.127:631 remote=0.0.0.0:0 inode:30576 exe=/usr/sbin/cupsd tcp pid:1375 local=1.0.0.127:5432 remote=0.0.0.0:0 inode:12650 exe=/usr/lib/postgresql/9.3/bin/postgres With ls you can know the process route.
The fuser command says that the process is: 2054
I’ve added IPv6 support and made a few fixes. Additionally on my system the octets of the IP address are reversed. Dependencies are only to posix shell, awk and cut.
My Version can be found on Github
#!/bin/sh # prints all open ports from /proc/net/* # # for pretty output (if available) start with # ./linux-get-programm-to-port.sh | column -t -s $'\t' #set -x ip4hex2dec () < local ip4_1octet="0x$" local ip4_2octet="$" ip4_2octet="0x$" local ip4_3octet="$" ip4_3octet="0x$" local ip4_4octet="$" ip4_4octet="0x$" local ip4_port="0x$" # if not used inverse #printf "%d.%d.%d.%d:%d" "$ip4_1octet" "$ip4_2octet" "$ip4_3octet" "$ip4_4octet" "$ip4_port" printf "%d.%d.%d.%d:%d" "$ip4_4octet" "$ip4_3octet" "$ip4_2octet" "$ip4_1octet" "$ip4_port" > # reoder bytes, byte4 is byte1 byte2 is byte3 . reorderByte() < if [ $-ne 8 ]; then echo "missuse of function reorderByte"; exit; fi local byte1="$" local byte2="$" byte2="$" local byte3="$" byte3="$" local byte4="$" echo "$byte4$byte3:$byte2$byte1" > # on normal intel platform the byte order of the ipv6 address in /proc/net/*6 has to be reordered. ip6hex2dec()< local ip_str="$" local ip6_port="0x$" local ipv6="$(reorderByte $)" local shiftmask="$" ipv6="$ipv6:$(reorderByte $)" shiftmask="$" ipv6="$ipv6:$(reorderByte $)" ipv6="$ipv6:$(reorderByte $)" ipv6=$(echo $ipv6 | awk '< gsub(/(:0|^0)/, ":"); sub(/(:0)+:/, "::");print>') printf "%s:%d" "$ipv6" "$ip6_port" > for protocol in tcp tcp6 udp udp6 raw raw6; do #echo "protocol $protocol" ; for ipportinode in `cat /proc/net/$protocol | awk '/.*:.*:.*/'` ; do #echo "#ipportinode=$ipportinode" inode=$ if [ "#$inode" = "#" ] ; then continue ; fi lspid=`ls -l /proc/*/fd/* 2>/dev/null | grep "socket:\[$inode\]" 2>/dev/null` ; pids=`echo "$lspid" | awk 'BEGIN /socket/ END>'` ; # removes duplicats for this pid #echo "#lspid:$lspid #pids:$pids" for pid in $pids; do if [ "#$pid" = "#" ] ; then continue ; fi exefile=`ls -l /proc/$pid/exe | awk 'BEGIN ">/->/'`; cmdline=`cat /proc/$pid/cmdline` local_adr_hex=$ remote_adr_hex=$ remote_adr_hex=$ if [ "#$" = "#6" ]; then local_adr=$(ip6hex2dec $local_adr_hex) remote_adr=$(ip6hex2dec $remote_adr_hex) else local_adr=$(ip4hex2dec $local_adr_hex) remote_adr=$(ip4hex2dec $remote_adr_hex) fi echo "$protocol pid:$pid \t$local_adr \t$remote_adr \tinode:$inode \t$exefile $cmdline" done done done