- Welcome to the MIT Kerberos Distribution Page!
- Contents
- About the Distributions
- Kerberos V5 Release 1.21.1 — current release (2023-07-10)
- Kerberos V5 Release 1.20.2 — maintenance release (2023-07-06)
- MIT Kerberos for Windows 4.1
- MIT Kerberos for Windows 3.2.2
- Kerberos Installation
- Step By Step Guide For Installing Kerberos on Linux
- Step 1: Ensure Your Devices Meet the Kerberos Protocol Installation
- Step 2: Run the Command apt-get install kbr5-user.
- Step 3: Enter a Local Account Password
- Step 4: Input the Default Kerberos 5.
- Step 5: Install Kerberos KDC Server
- Step 6: Install the Kerberos KDC Client
- Step 7: Configure Kerberos by Modifying Files
- Step 8: Create KDC Databases
- Step 9- ACL Changes:
- Step 10: Add Admin Name for KDC
- Step 11: Restart the Kerberos Admin and KDC Server
- Conclusion
- About the author
- Kennedy Brian
Welcome to the MIT Kerberos Distribution Page!
Downloading of this software may constitute an export of cryptographic software from the United States of America that is subject to the United States Export Administration Regulations (EAR), 15 CFR 730-774. Additional laws or regulations may apply. It is the responsibility of the person or entity contemplating export to comply with all applicable export laws and regulations, including obtaining any required license from the U.S. government.
Contents
About the Distributions
Current releases are signed with one of the following PGP keys:
C449 3CB7 39F4 A89F 9852 CBC2 0CBA 0857 5F83 72DF (ghudson@mit.edu) C1BD 1C74 4EA6 6EA2 DDF1 1B43 CFE2 8FC7 253A AB87 (ghudson@mit.edu) 2C73 2B1C 0DBE F678 AB3A F606 A32F 17FD 0055 C305 (tlyu@mit.edu)
Each distribution that is distributed as a tar file contains one or more files and their detached PGP signature files.
Kerberos V5 Release 1.21.1 — current release (2023-07-10)
Kerberos V5 Release 1.20.2 — maintenance release (2023-07-06)
MIT Kerberos for Windows 4.1
- 64-bit MSI Installer kfw-4.1-amd64.msi, 10812k.
- 32-bit MSI Installer kfw-4.1-i386.msi, 5836k.
- Sources kfw-4.1-src.zip, 7981k, detached signature kfw-4.1-src.zip.asc, 1k. kfw-4.1-amd64-mit.msi, 10808k.
- 32-bit MSI Installer with MIT-specific krb5.ini kfw-4.1-i386-mit.msi, 5836k. —>
MIT Kerberos for Windows 3.2.2
- Installer kfw-3-2-2.exe, 6425k.
- MSI Installer kfw-3-2-2.msi, 8967k.
- Core Binaries, kfw-3-2-2.zip, 8218k.
- SDK, kfw-3-2-2-sdk.zip, 559k.
- Sources, kfw-3-2-2-src.zip, 13814k.
$Id: index.html,v 1.334 2023/07/11 22:52:39 ghudson Exp $
MIT Kerberos [ home ] [ contact ]
Kerberos Installation
Kerberos is an Open Authentication System created by MIT. Numerous big data systems use Kerberos for the server-to-server correspondences in network security. The Kerberos protocol has strong cryptographic authentication over devices, allowing clients and servers to develop trusted communication. The protocol aims to address common network security issues.
It deals with a ticket-based framework to prevent intrusion from external attackers. Thus, it prevents any possibilities of secret phrase sniffing or secret password thefts.
This step-by-step guide illustrates the how to install Kerberos on Linux in the following ways;
- Kerberos installation prerequisites and an explanation of how to set up and design Kerberos in a Cluster
- How to install Kerberos KDC Server in one machine
- How to install Kerberos client in the rest of the machines
Step By Step Guide For Installing Kerberos on Linux
The Kerberos authenticating protocol is available for downloading from the official MIT repository. You can also find it at the Ubuntu store. Thus, you can install it on Ubuntu 22.04 or any Linux OS version using the following steps:
Step 1: Ensure Your Devices Meet the Kerberos Protocol Installation
Notably, Kerberos will only install if your devices meet all the necessary prerequisites. These prerequisites include;
- The same time frame between your host and client/user devices since a time difference of more than 5 minutes will lead to failure.
- Both devices have the same operating system.
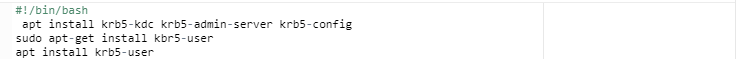
Step 2: Run the Command apt-get install kbr5-user.
First, start up your computer and open the terminal window. Then, run the command
Step 3: Enter a Local Account Password
Enter the local account password for your system. Press Y and then the ENTER key once prompted to continue.
Step 4: Input the Default Kerberos 5.
In the next step, the user will be requested to input a default Kerberos 5. Input the following text in capital letters LinHint@UBUNTUBOX.COM:
These first three steps come in handy in setting up the installation files. Once these installation files are ready, press the ENTER key, and Kerberos will execute automatically until the process is complete.
Step 5: Install Kerberos KDC Server
Kerberos KDC Server can be introduced in the Master workstation. Yet, that is certainly not a strict rule, making it possible to be introduced in any server inside the Cluster.
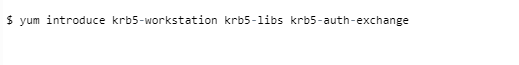
Step 6: Install the Kerberos KDC Client
Introduce Kerberos KDC client on every one of the nodes or machines in the cluster using the yum command.
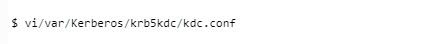
Step 7: Configure Kerberos by Modifying Files
As a component of the setup, we should make changes to two records:
kdc.conf Changes
In the example, utilize a unique Realm name. For this demonstration, we will pick Realm’s name as LinHint@UBUNTUBOX.COM.
1, 2 are pretty straightforward, while 3 and 4 tell which machines are important for our Realm. Any machine with hostname abc.testdomain.local, g1.testdomain.local , gk.testdomain.local and testdomain.local is planned to LinHint@UBUNTUBOX.COM
Step 8: Create KDC Databases
It is time to create KDC (Key Distribution Center) data sets that the Kerberos server will use. This is our installation process:
Setting up a Master Password becomes mandatory after this step. Follow the commands as prompted and copy the password. This password will come in handy for any KDC dataset-related exercises like restarting your system or database changes later on.
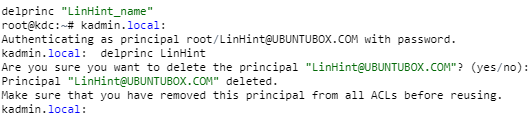
Step 9- ACL Changes:
Follow the command to make ACL changes
Change it appropriately with your Realm name. We will use */LinHint@UBUNTUBOX.COM * in this demonstration.
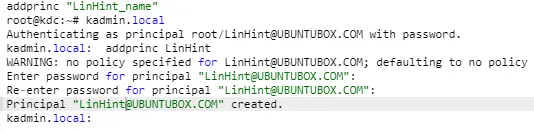
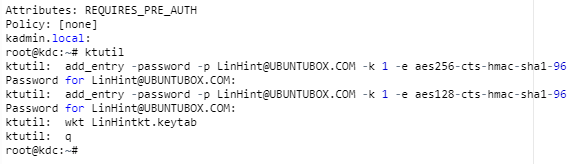
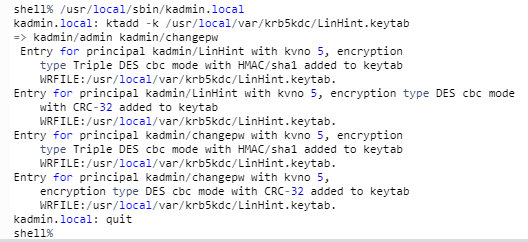
Step 10: Add Admin Name for KDC
It is vital to ensure that you can only add an admin for KDC in the machine with the KDC server. Adding it to any of the Kerberos client machines will not yield the desired results.
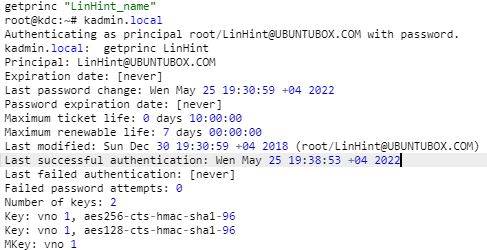
This command will bring you to the kadmin.local brief. You can then use the command below with your Realm name see all the principles created during your installation.
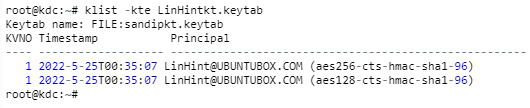
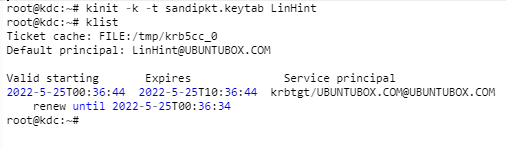
Step 11: Restart the Kerberos Admin and KDC Server
Again, these commands MUST only be done in the KDC Server machine. This step is a confirmation of full installation:
Restart KDC Server
Restart KADMIN Server
Conclusion
It is a relatively easier procedure for installing the latest Kerberos version, popularly known as KRB5, on Linux. Administrators can therefore grant permission to users to securely sign on to systems and programs without the keying in passwords every time.
About the author
Kennedy Brian
Brian is a computer scientist with a bias for software development, programming, and technical content development. He has been in the profession since 2015. He reads novels, jogs, or plays table tennis whenever not on gadgets. He is an expert in Python, SQL, Java, and data and network security.