- How to set password policy on Linux
- Preparation
- On Ubuntu, Debian or Linux Mint:
- On CentOS, Fedora or RHEL:
- Prevent Reusing Old Passwords
- On Debian, Ubuntu or Linux Mint:
- On Fedora, CentOS or RHEL:
- Set Minimum Password Length
- On Ubuntu, Debian or Linux Mint:
- On Fedora, CentOS or RHEL:
- Set Password Complexity
- On Ubuntu, Debian or Linux Mint:
- On Fedora, CentOS or RHEL:
- Set Password Expiration Period
- Support Xmodulo
- How to enable and enforce secure password policies on Ubuntu
- Test the secure password policy
- Configure password expiration period
- About the author
- Karim Buzdar
- How do I enforce a password complexity policy?
- 2 Answers 2
How to set password policy on Linux
User account management is one of the most critical jobs of system admins. In particular, password security should be considered the top concern for any secure Linux system. In this tutorial, I will describe how to set password policy on Linux.
I assume that you are using PAM (Pluggable Authentication Modules) on your Linux system, which is the case on all recent Linux distros.
Preparation
Install a PAM module to enable cracklib support, which can provide additional password checking capabilities.
On Ubuntu, Debian or Linux Mint:
$ sudo apt-get install libpam-cracklib
On CentOS, Fedora or RHEL:
The cracklib PAM module is installed by default on CentOS, Fedora, or RHEL. So no further installation is necessary on those systems.
To enforce password policy, we need to modify an authentication-related PAM configuration file located at /etc/pam.d . Policy change will take effect immediately after change.
Note that the password rules presented in this tutorial will be enforced only when non-root users change their passwords. The root password is not governed by the rules.
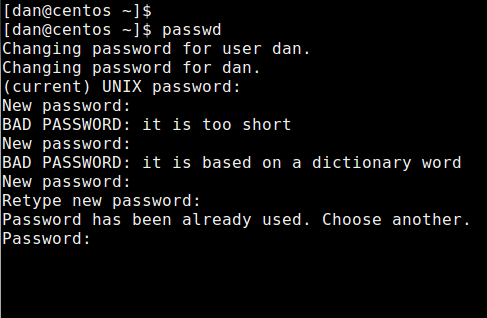
Prevent Reusing Old Passwords
Look for a line that contains both password and pam_unix.so , and append remember=5 to that line. It will prevent five most recently used passwords (by storing them in /etc/security/opasswd ).
On Debian, Ubuntu or Linux Mint:
$ sudo vi /etc/pam.d/common-password
password [success=1 default=ignore] pam_unix.so obscure sha512 remember=5
On Fedora, CentOS or RHEL:
$ sudo vi /etc/pam.d/system-auth
password sufficient pam_unix.so sha512 shadow nullok try_first_pass use_authtok remember=5
Set Minimum Password Length
Look for a line that contains both password and pam_cracklib.so , and append minlen=10 to that line. This will enforce a password of length (10 – ), where indicates how many different types of characters are used in the password. There are four types (upper-case, lower-case, numeric, and symbol) of characters. So if you use a combination of all four types, and minlen is set to 10, the shorted password allowed would be 6.
On Ubuntu, Debian or Linux Mint:
$ sudo vi /etc/pam.d/common-password
password requisite pam_cracklib.so retry=3 minlen=10 difok=3
On Fedora, CentOS or RHEL:
$ sudo vi /etc/pam.d/system-auth
password requisite pam_cracklib.so retry=3 difok=3 minlen=10
Set Password Complexity
Look for a line that contains password and pam_cracklib.so , and append ucredit=-1 lcredit=-2 dcredit=-1 ocredit=-1 to that line. This will force you to include at least one upper-case letter ( ucredit ), two lower-case letters ( lcredit ), one digit ( dcredit ) and one symbol ( ocredit ).
On Ubuntu, Debian or Linux Mint:
$ sudo vi /etc/pam.d/common-password
password requisite pam_cracklib.so retry=3 minlen=10 difok=3 ucredit=-1 lcredit=-2 dcredit=-1 ocredit=-1
On Fedora, CentOS or RHEL:
$ sudo vi /etc/pam.d/system-auth
password requisite pam_cracklib.so retry=3 difok=3 minlen=10 ucredit=-1 lcredit=-2 dcredit=-1 ocredit=-1
Set Password Expiration Period
To set the maximum period of time the current password is valid, edit the following variables in /etc/login.defs .
PASS_MAX_DAYS 150 PASS_MIN_DAYS 0 PASS_WARN_AGE 7
This will force every user to change their password once every six months, and send out a warning message seven days prior to password expiration.
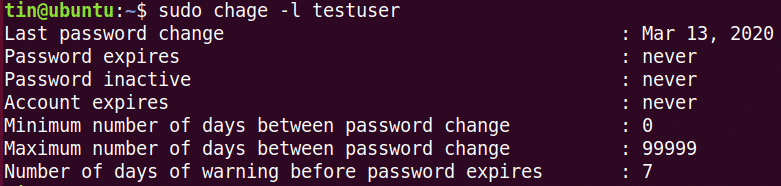
If you want to set password expiration on per-user basis (e.g., to force password reset for user alice on her next login), use chage command instead. To view password expiration policy for a specific user:
Last password change : Dec 30, 2013 Password expires : never Password inactive : never Account expires : never Minimum number of days between password change : 0 Maximum number of days between password change : 99999 Number of days of warning before password expires : 7
By default, a user’s password is set to never expire.
To change the password expiration period for user xmodulo :
$ sudo chage -E 6/30/2014 -m 5 -M 90 -I 30 -W 14 xmodulo
The above command will set the password to expire on 6/30/2014. In addition, the minimum/maximum number of days between password changes is set to 5 and 90 respectively. The account will be locked 30 days after a password expires, and a warning message will be sent out 14 days before password expiration.
This tutorial describes password policy configuration for system administrators. While enforcing complex password policies can help reduce the possibility of unauthorized system breaches, thus making system admin’s life easier, it means that end users have to remember complex passwords. This is when password management tools like pass , KeePassX come in handy. Check them out if you need one.
Support Xmodulo
This website is made possible by minimal ads and your gracious donation via PayPal or credit card
Please note that this article is published by Xmodulo.com under a Creative Commons Attribution-ShareAlike 3.0 Unported License. If you would like to use the whole or any part of this article, you need to cite this web page at Xmodulo.com as the original source.
How to enable and enforce secure password policies on Ubuntu
Secure passwords are the first line of defense against unauthorized access whether it is your personal computer or the server in your organization. However, some employees do not take it seriously and keep using insecure and easy to guess passwords which make their systems compromised. Therefore, it becomes critical for system administrators to enforce a secure password policy for users. In addition, it’s important to change the password after a certain period of time.
In this article, we will learn how to enable and enforce secure password policies on Ubuntu. Also we will discuss how to set a policy that enforce users to change their password at regular interval.
Note that we have explained the procedure on Ubuntu 18.04 LTS system.
A strong password should contain:
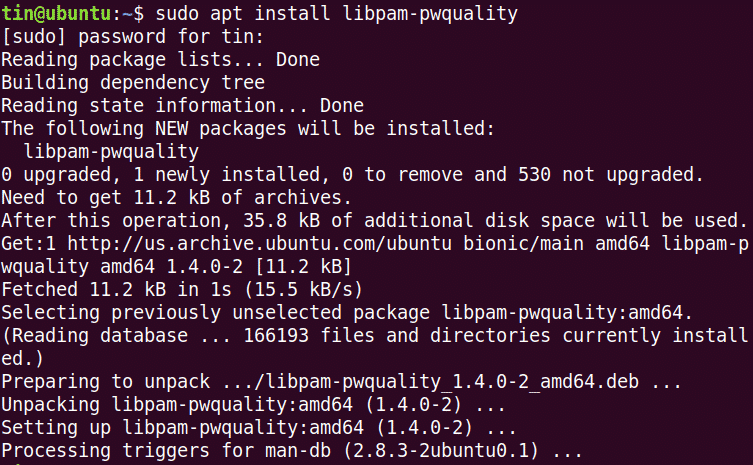
To enforce a secure password policy in Ubuntu, we will use the pwquality module of PAM. To install this module, launch the Terminal by using Ctrl+Alt+T shortcut. Then run this command in Terminal:
When prompted for the password, enter the sudo password.
Now first copy “/etc/pam.d/common-password” file before configuring any changes.
And then edit it for configuring password policies:
Look for the following line:
And replace it with the following:
password requisite
pam_pwquality.so retry = 4 minlen = 9 difok = 4 lcredit =- 2 ucredit =- 2 dcredit =
-1 ocredit =- 1 reject_username enforce_for_root
Let’s see what the parameters in above command mean:
- retry: No. of consecutive times a user can enter an incorrect password.
- minlen: Minimum length of password
- difok: No. of character that can be similar to the old password
- lcredit: Min No. of lowercase letters
- ucredit: Min No. of uppercase letters
- dcredit: Min No. of digits
- ocredit: Min No. of symbols
- reject_username: Rejects the password containing the user name
- enforce_for_root: Also enforce the policy for the root user
Now reboot the system to apply the changes in the password policy.
Test the secure password policy
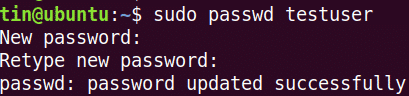
After configuring the secure password policy, it’s better to verify whether it is working or not. To verify it, set a simple password that does not fulfill the above configured secure password policy requirements. We will check it on a test user.
Run this command to add a user:
Now try to enter a password that does not include:·
You can see none of the above-tried passwords has accepted, as they do not meet the minimum criteria defined by the password policy.
Now try adding a complex password that meets the criteria defined by the password policy (Total length: 8 with Minimum:1 uppercase letter, 1 lowercase letter, 1 digit and 1 symbol). Let’s say: Abc.89*jpl.
You can see that the password has now accepted.
Configure password expiration period
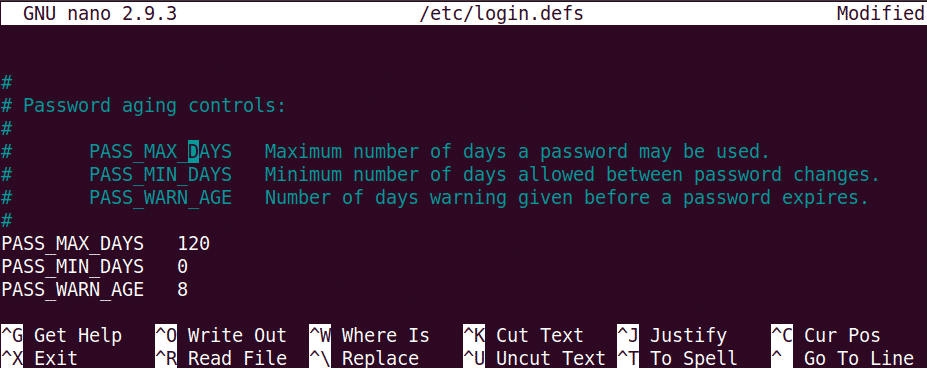
Changing the password at regular interval helps limits the period of unauthorized use of passwords. Password expiration policy can be configured through “/etc/login.defs” file.Run this command to edit this file:
Add the following lines with values as per your requirements.
Note that the above-configured policy will only apply on the newly created users. To apply this policy to an existing user, use “chage” command.
To use chage command, syntax is:
Note: To execute the chage command, you must be the owner of the account or have root privilege otherwise, you will not be able to view or modify the expiry policy.
To view the current password expiry/aging details, the command is:
To configure the maximum No. of days after which a user should change the password.
To configure the minimum No. of days required between the change of password.
To configure warning prior to password expiration:
That is all there is to it! Having a policy that enforces users to use secure passwords and change them regularly after some interval is necessary to ensure system safety and security. For more information regarding the tools discussed in this article, such as pam_pwquality and Chage, see their man pages.
About the author
Karim Buzdar
Karim Buzdar holds a degree in telecommunication engineering and holds several sysadmin certifications. As an IT engineer and technical author, he writes for various web sites. He blogs at LinuxWays.
How do I enforce a password complexity policy?
I’ve had a look around and all I have found is the instructions for specifying the password length; but, I have yet to find something that relates to specifying the content of the password regarding the above points.
Any help would be appreciated.
2 Answers 2
Update January 2023: the library pam_pwquality.so has in many/most cases superceded the use of pam_cracklib.so . pam_pwquality.so should be backwards compatible with pam_cracklib . See pam_pwquality.so man pages for usage details & examples.
Password complexity is enforced by the pam_cracklib module.
In order to modify the password policy for your local machine, you will need to modify your /etc/pam.d/common-password file.
From a terminal window ( Ctrl + Alt + T ), enter the following command:
sudo vi /etc/pam.d/common-password Add the following line to the file (before pam_unix.so or whichever PAM module is used primarily for authentication, as can be seen from examples in the manpage) and save the file:
password requisite pam_cracklib.so ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1 This statement implements the following password requirements:
- dcredit == digit
- ucredit == upper-case character
- lcredit ==lower-case character
- ocredit == other character (special characters, including ! , @ # $ % )
This should satisfy your requirements.
You could also use the variables minlength and retries to further restrict the password requirements.
Here is another good example of modifying a password policy in this manner would be placing the following line in the /etc/pam.d/common-password file:
password requisite pam_cracklib.so retry=3 minlen=10 difok=3 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1 This entry will set a maximum of three attempts at getting an acceptable password with a 10-character minimum length.
This sets the requirement for users to have a minimum of three characters different from the last password.
This will also fulfill the requirement of having the password contain at least one each of digit, lower-case character, and upper-case characters.