- Нет интернета при подключении vpn микротик
- Re: LT2P/IPSec VPN working no internet access
- Re: LT2P/IPSec VPN working no internet access
- Re: LT2P/IPSec VPN working no internet access
- Re: LT2P/IPSec VPN working no internet access
- Re: LT2P/IPSec VPN working no internet access [SOLVED]
- L2TP -IPSec Mikrotik. Нет доступа к Интернету. Почему?
Нет интернета при подключении vpn микротик
I have an L2TP / IPSec VPN server configured and working (except for internet access) as per these instructions —
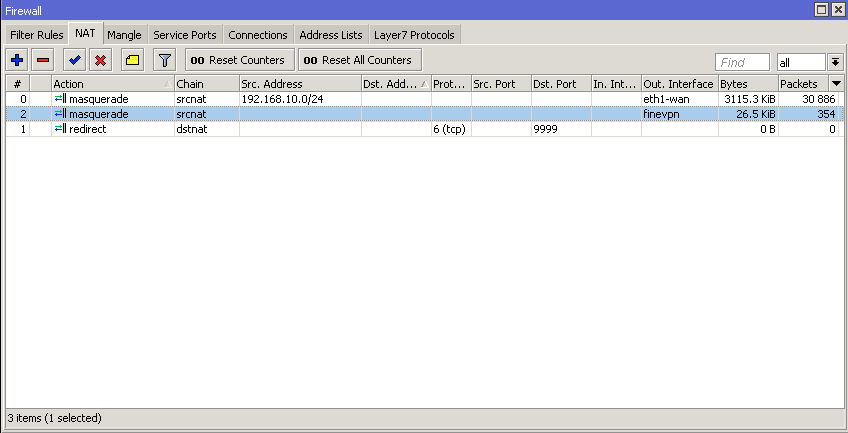
The VPN tunnel works and I can see the assets on the remote networks — as the firewall allows. The VPN network has a nat Masq rule.
Re: LT2P/IPSec VPN working no internet access
I assume you claim the fact that the client cannot access internet via the L2TP tunnel. If the client cannot access internet at all while the L2TP connection is active, the issue is at Mikrotik side; if it can access internet but bypassing the L2TP tunnel, it is the routing setting at client side which differs depending on client type.
The instructions on the Wiki cover the key subject, but cannot cover all individual environments, so the reader always has to implement the key subject into his local context. And referring to the Wiki doesn’t provide any information on how your actual firewall rules and routing look like. Don’t ask what it might be, post the configuration to let someone else find what it really is, as this is a much easier task.
Re: LT2P/IPSec VPN working no internet access
# jun/09/2019 17:49:01 by RouterOS 6.44.3 /interface vlan add interface=main_bridge name=main-v10 vlan-id=10 /interface list add name=WAN add name=LAN /ip pool add name=main ranges=192.168.254.50-192.168.254.199 add name=vpn ranges=192.168.50.50-192.168.50.80 /ip dhcp-server add address-pool=main dhcp-option-set="IP Phones" disabled=no interface=\ main-v10 lease-time=3d name=main_server /ppp profile set *FFFFFFFE dns-server=1.1.1.1,8.8.8.8 idle-timeout=15m local-address=\ 192.168.50.2 remote-address=vpn use-encryption=required /interface bridge port2 add bridge=main_bridge comment="Trunk #1" interface=ether2 add bridge=main_bridge comment="Trunk #2" interface=ether3 /ip settings set rp-filter=strict /interface bridge vlan add bridge=main_bridge comment=main_network tagged=main_bridge,ether2,ether3 \ vlan-ids=10 /interface l2tp-server server set authentication=mschap2 enabled=yes use-ipsec=required /interface list member add interface=ether1 list=WAN add interface=main-v10 list=LAN /ip address add address=192.168.254.1/24 comment="Main Network" interface=main-v10 \ network=192.168.254.0 add address=x.x.x.x comment="Modem" interface=ether1 \ network=x.x.x.x /ip cloud set ddns-enabled=yes /ip dns set allow-remote-requests=yes servers=\ 192.168.254.6,1.1.1.1,8.8.8.8,1.0.0.1,8.8.4.4 /ip firewall address-list add address=192.168.254.0/24 comment=Default list=main add address=192.168.50.0/24 comment=Default list=vpn /ip firewall filter add action=accept chain=input comment="Allow established,related,untracked" \ connection-state=established,related,untracked add action=drop chain=input comment="Drop invalid input" connection-state=\ invalid add action=accept chain=input comment="Allow L2TP/IPSec VPN connection" \ dst-port=500,1701,4500 in-interface-list=WAN protocol=udp add action=accept chain=input comment="Allow L2TP/IPSec VPN connection" \ in-interface-list=WAN protocol=ipsec-esp add action=accept chain=input comment=\ "Allow main list into router" src-address-list=main add action=drop chain=input comment=\ "drop all else" add action=fasttrack-connection chain=forward comment=\ "Allow forward fasttrack" connection-state=established,related add action=accept chain=forward comment=\ "Allow Forward established,related, untracked" connection-state=\ established,related,untracked add action=drop chain=forward comment="Drop invalid forward" \ connection-state=invalid add action=accept chain=forward comment=\ "Alllow LAN interface-list out wan interface-list" in-interface-list=LAN \ out-interface-list=WAN add action=accept chain=forward comment=\ "Allow VPN to main network connections" dst-address-list=main \ src-address-list=vpn add action=accept chain=forward comment="RFC 6092 - accept in ipsec policy" \ ipsec-policy=in,ipsec add action=accept chain=forward comment="RFC 6092 - accept out ipsec policy" \ ipsec-policy=out,ipsec add action=drop chain=forward comment=\ "Drop new connections from internet which are not dst-natted" \ connection-nat-state=!dstnat connection-state=new in-interface-list=WAN add action=drop chain=forward comment="Drop packets from LAN interface-list th\ at do not come from the LAN interface-list" in-interface-list=LAN \ out-interface-list=!LAN add action=drop chain=forward comment="should be out" /ip firewall nat add action=masquerade chain=srcnat comment="Masquerade all LAN traffic" \ ipsec-policy=out,none out-interface-list=WAN /ip route add distance=1 gateway=x.x.x.x /ip service set telnet disabled=yes set ftp disabled=yes set www disabled=yes set ssh disabled=yes set api disabled=yes set api-ssl disabled=yes /ip ssh set strong-crypto=yes /system ntp client set enabled=yes server-dns-names="0.pool.ntp.org,1.pool.ntp.org,2.pool.ntp.org\ ,3.pool.ntp.org,time.google.com" /tool bandwidth-server set enabled=no /tool mac-server set allowed-interface-list=none /tool mac-server ping set enabled=noRe: LT2P/IPSec VPN working no internet access
The only rule in the firewall chain of your «drop-all-but-exceptions» firewall which permits outbound connections through WAN is
action=accept chain=forward comment=»Alllow LAN interface-list out wan interface-list» in-interface-list=LAN out-interface-list=WAN ,
but as the VPN interfaces are not members of interface list LAN, this rule doesn’t allow packets coming from these interfaces to establish new connections to internet.
Another permissive rule is action=accept chain=forward comment=»Allow VPN to main network connections» dst-address-list=main src-address-list=vpn which refers to src-address-list=vpn but only the LAN subnet 192.168.254.0/24 is listed in the dst-address-list=main so this rule also doesn’t match packets from VPN clients to internet.
And that’s it, the two remaining permissive rules which refer to ipsec-policy are irrelevant because IPsec is only used to encrypt the transport packets of the L2TP, so the payload packets coming in via the L2TP tunnel do not match any IPsec policy.
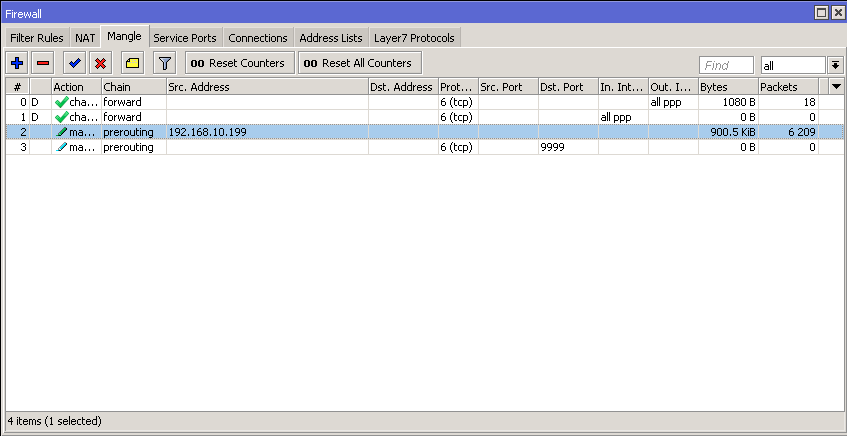
So either add an interface-list=LAN item to the /ppp profile , so that each dynamically created L2TP server interface would be added as a member to the interface list, or add another rule like action=accept chain=forward comment=»Allow VPN to internet» out-interface-list=WAN src-address-list=vpn before the last action=drop rule, and remove the last-but-one and last-but-two action=drop rules because they are useless in the current setup. The first one permits dst-natted packets which came in via WAN to go further through the chain but the next rule ignores them and the last rule drops them; the second one drops anything from LAN to anywhere else but again, what this rule ignores is dropped by the last one.
Re: LT2P/IPSec VPN working no internet access
«So either add an interface-list=LAN item to the /ppp profile»
This looks like a cleaner way to do it. Should I add the interface-list=LAN to both the default and default-encryption profile? To test, I added it to the default-encryption profile and it worked. I did not realize you could dynamically add to an interface list — even thought it was right in front of me. Very neat feature.
«ipsec-policy are irrelevant because IPsec is only used to encrypt the transport packets of the L2TP»
To be honest I left these rules as they came in MTs default firewall rules. I did not have a clear understanding of when they would match. Now I mostly do. .
«remove the last-but-one and last-but-two action=drop rules because they are useless in the current setup.»
The last drop rule needs to stay — it is these two that are useless?
add action=drop chain=forward comment=\ "Drop new connections from internet which are not dst-natted" \ connection-nat-state=!dstnat connection-state=new in-interface-list=WAN add action=drop chain=forward comment="Drop packets from LAN interface-list th\ at do not come from the LAN interface-list" in-interface-list=LAN \ out-interface-list=!LANWould the first rule be more effective (match) earlier in the chain? I assume it simply does not matter as it will hit the last rule and drop anyway. So perhaps there is no advantage to it.
Last Question — Is it a best practice to have one catch all Masq rule, or to use multiple Masq rules for each network? I can be more granular with a rule for each, but is not as clean. What is your preference?
Thank you again for all your help.
Re: LT2P/IPSec VPN working no internet access [SOLVED]
It depends on which profile your /interface l2tp-server server , or your /ppp secret refer (the latter, if set, supersedes the former)
«remove the last-but-one and last-but-two action=drop rules because they are useless in the current setup.»
The last drop rule needs to stay — it is these two that are useless?
Would the first rule be more effective (match) earlier in the chain? I assume it simply does not matter as it will hit the last rule and drop anyway. So perhaps there is no advantage to it.
Exactly. That rule (drop what comes in via WAN unless dst-nated) remained there from the default firewall settings, and its effect in the default firewall settings is «accept any connection initiated from LAN side, accept any connection initiated from WAN side if dst-nated, drop the rest» because what is not dropped by that rule is accepted as it is the last rule in the forward chain and the default handling if no rule matches is hardcoded to «accept» (unlike in naked linux iptables where you can set default handling for each chain).
Is it a best practice to have one catch all Masq rule, or to use multiple Masq rules for each network? I can be more granular with a rule for each, but is not as clean. What is your preference?
First of all, action=masquerade should only be used with interfaces whose address dynamically changes, because each change of address or interface going down causes all masqueraded connections to be dropped. Other than that, there is no actual preference — whereas in the mangle chain every packet is handled so you it is important to make the number of rules a packet has to pass through as low as possible, the nat chains only handle the initial packet of each connection so it is not so critical to have one rule per WAN interface. So after all it is the readability what matters most if you plan to modify your firewall now and then.
L2TP -IPSec Mikrotik. Нет доступа к Интернету. Почему?
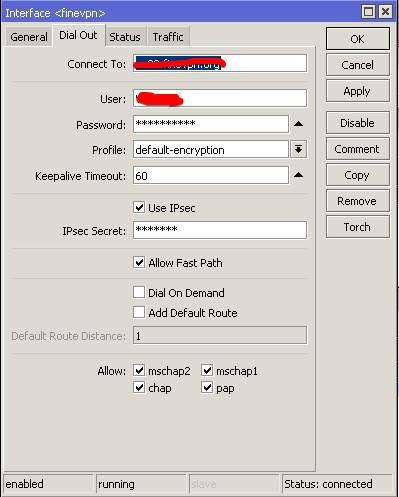
Настроил сеть. Без VPN интернет есть. Необходимо настроить L2TP Client и как видно в статусе соединение с сервером идет. Пробовал в Add Default Route ставить чекбокс Enable (0,1) — пропадает доступ в интернет совсем.
VPN в данном случае делаю к локальному адресу 196.168.10.199. Пробовал и на весь пул DHCP.
Наведите на мысль где нестыковка?
а если снять галку «default route», то интернет есть?
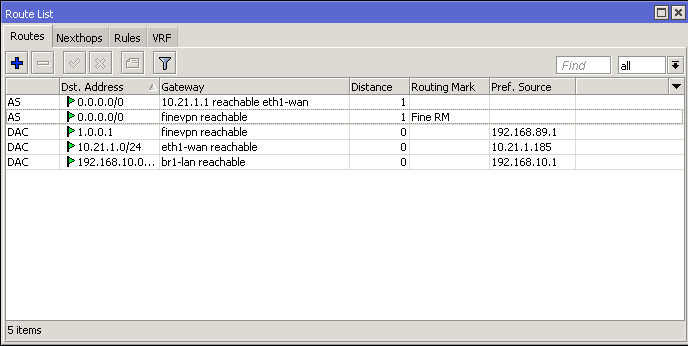
вообще же установка галки «default route» означает, что весь трафик в интернет микротик станет пытаться слать через vpn-соединение, и если vpn-сервер, к которому вы сделали подключение, не настроен на пересылку трафика от вас в интернет, то соединения с интернетом и не будет. вместо default route вам надо добавить в таблицу маршрутизации маршрут, который направлял бы трафик для определённой подсети (той, которая за vpn-сервером) на ip vpn-шлюза (vpn-сервера).