- Network Access Control (NAC) Software for Linux
- Compare the Top Network Access Control (NAC) Software for Linux of 2023
- What is Network Access Control (NAC) Software for Linux?
- Device42
- N‑able N-sight RMM
- Portnox Security
- S3M Security Network Access Control
- Genian NAC
- Cruz Operations Center (CruzOC)
- NordLayer
- Auconet BICS
- How To Control Access Based on Client IP Address in NGINX
- Control Access Based on Client IP Address in NGINX
Network Access Control (NAC) Software for Linux
Compare the Top Network Access Control (NAC) Software for Linux of 2023
What is Network Access Control (NAC) Software for Linux?
Network access control (NAC) software provides companies with a security platform to manage sensitive data access through a network connection. Compare the best Network Access Control (NAC) software for Linux currently available using the table below.
Device42
Device42 is the leading and most comprehensive agentless hybrid IT discovery, inventory and dependency mapping platform available today. It continuously discovers, normalizes, and categorizes the entire IT stack data. Automated dependency mapping and built-in insights enable our customers to optimize the infrastructure and applications, migrate with ease, solve problems fast, pass compliance and audits with flying colors, and run IT with confidence. Thousands of users across 70+ countries, including many government agencies, enterprises and 200+ partners and systems integrators, use these capabilities to manage and modernize IT infrastructure and ensure business and operational continuity. Try it for yourself today, free for 30 days!
N‑able N-sight RMM
N‑able N-sight RMM® is a cloud-based IT solution that makes it easy for MSPs to deliver valuable technology services within hours, not weeks or months. Clear graphical dashboards place alerts front and center so you can focus on what needs you most. Built-in remote access and security features help you support and protect from day one. And when you’re ready, grow your business with additional security layers and add-ons services to expand your offering. N‑able N-sight RMM features include remote access, network path visualization, automated monitoring and maintenance, prescriptive data analytics, data-breach risk intelligence, and more. N‑able N-sight RMM is also available for download as Android and iOS mobile apps to allow users to manage issues anywhere.
Portnox Security
Portnox CLEAR is the only cloud-native network access control (NAC) solution that unifies essential network and endpoint security capabilities: device discovery, network authentication, access control, network hardware administration, risk mitigation and compliance enforcement. As a cloud service, Portnox CLEAR eliminates the need for on-going maintenance such as upgrades and patches and requires no on-site appliances. As such, the platform can be easily deployed, scaled and managed by lean, resource-constrained IT teams across any corporate network — no matter how complex.
S3M Security Network Access Control
S3M Security is a cybersecurity company that focuses on software development and provides value added services in network and information security. Founded by people with more than 20 years of experience in the industry, S3M Security operates in the USA, Europe and EMEA regions. Our team continues to develop new approaches and solutions every day to provide secure environments for organizations against increasing cyber threats and attacks.
Genian NAC
Genians delivers a cybersecurity platform that ensures full network surveillance for all connected devices and provides dynamic access control to maintain compliance with IT security policies. It then leverages automation to orchestrate an organization’s entire security portfolio in concert with Device Platform Intelligence, Network Access Control (NAC), and Endpoint Detection and Response (EDR) to achieve an optimally-secure network edge. Genians Zero Trust Network Access Control (NAC) can secure every single connecting point in various networking environments such as VPN, xDSL, and 5G, while ensuring least-privilege access, multifactor authentication (MFA), and micro-segmentation. It can also enhance any enterprise’s Secure Access Service Edge (SASE) architecture. Genians secures millions of various endpoints in organizations of all sizes and industries, including global Fortune 500 companies, the government, the military, energy, finance, healthcare, education, and more.
Cruz Operations Center (CruzOC)
CruzOC is a scalable multi-vendor network management and IT operations tool for robust yet easy-to-use netops. Key features of CruzOC’s integrated and automated management include performance monitoring, configuration management, and lifecycle management for 1000s of vendors and converging technologies. With CruzOC, administrators have implicit automation to control their data center operations and critical resources, improve network and service quality, accelerate network and service deployments, and lower operating costs. The result is comprehensive and automated problem resolution from a single-pane-of-glass. Cruz Monitoring & Management. NMS, monitoring & analytics — health, NPM, traffic, log, change. Automation & configuration management — compliance, security, orchestration, provisioning, patch, update, configuration, access control. Automated deployment — auto-deploy, ZTP, remote deploy. Deployments available on-premise and from the cloud.
NordLayer
NordLayer is an adaptive network access security solution for modern businesses — from the world’s most trusted cybersecurity brand, Nord Security. We help organizations of all sizes to fulfill scaling and integration challenges when building a modern secure remote access solution within an ever-evolving SASE framework. Quick and easy to integrate with existing infrastructure, hardware-free, and designed with ease of scale in mind, NordLayer meets the varying growth pace and ad-hoc cybersecurity requirements of agile businesses and distributed workforces today
Auconet BICS
Strengthen your existing ITOM solutions with synergistic Auconet BICS capabilities. Auconet provides next-generation IT operations management and security through its BICS (Business Infrastructure Control Solution), on a single pane of glass. BICS continuously discovers, secures, manages, and centrally controls every network device, port, and endpoint, in complex, heterogeneous IT or SCADA infrastructures with up to a million or more endpoints. Auconet BICS enables global enterprises to seamlessly and efficiently solve today’s issues with mobile device utilization and BYOD, and tomorrow’s challenges with Internet of Everything non-traditional endpoints. Designed for the enterprise, and proven by long-term installations, Auconet is trusted by top-tier Global 1000 firms, including BASF, Siemens, and Deutsche Bahn, as well as hundreds of leading financial institutions. Auconet BICS delivers a fresh, efficient approach to control complex networks.
How To Control Access Based on Client IP Address in NGINX
There are several ways of NGINX web server security hardening one of which is access control based on IP address. This guide explains how to secure web applications by controlling access based on a client’s IP address in NGINX.
This guide assumes that you have an NGINX web server installed and running, otherwise check out these guides:
Control Access Based on Client IP Address in NGINX
The ngx_http_access_module module in NGINX enables limiting access to certain client IP addresses. You can activate it with the allow and deny directives.
The allow directive as the name implies allows access for a specific IP address, network, Unix socket, or all (keyword for the previous entities), and the deny directive denies access for a specific IP address, network, Unix socket, or all.
Both directives are valid in the HTTP, server, location as well as limit_except context. Here is an example of using the allow and deny directives within a location context to restrict access to an API service:
upstream app_api < keepalive 100; server 10.1.1.50:5000; server 10.1.1.71:5001; >server < listen 80; server_name _; access_log /var/log/nginx/app_api_access.log main; error_log /var/log/nginx/app_api_error.log debug; root /usr/share/nginx/html/; location / < try_files $uri /api; >location /api < proxy_read_timeout 3600; proxy_connect_timeout 3600s; keepalive_timeout 15; send_timeout 300; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; proxy_set_header Host $http_host; proxy_redirect off; proxy_http_version 1.1; proxy_set_header Connection ""; proxy_pass http://app_api$request_uri; #list of allowed IPs to access API allow 10.10.10.20; allow 10.10.40.29; allow 192.168.2.23; allow 192.168.10.0/24; deny all; >>
In the above example, any request to access any of the proxied API endpoints is allowed only for the 10.10.10.20, 10.10.40.29, 192.168.2.23 IP addresses, and any of the ones in the 192.168.10.0/24 network. Requests from any other IP address or network or UNIX-domain socket will be denied.
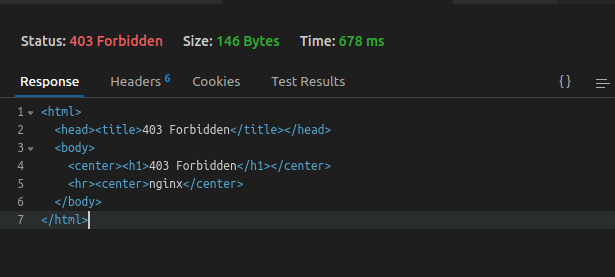
NGINX will respond with a 403 forbidden error to the client as shown.
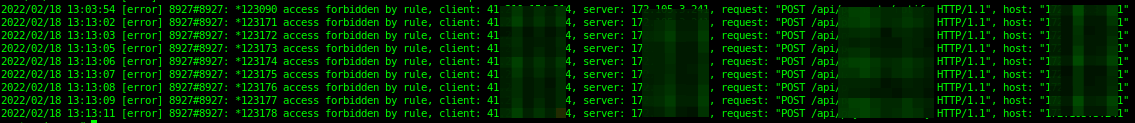
When you check the /var/log/nginx/app_api_error.log error log, you will find entries like the ones shown in the following screenshot:
# cat /var/log/nginx/app_api_error.log debug
For more NGINX web server security hardening tips, check out: The Ultimate Guide to Secure and Harden Nginx Web Server.