- Login as non-root user in terminal
- 2 Answers 2
- How to Add a non-Root User to Kali Linux
- Adding a Non-Root User
- Installing Google Chrome
- Installing other Non-Root Softwares
- Conclusion
- About the author
- Usama Azad
- How to Create Sudo User in RHEL, CentOS, Rocky & AlmaLinux
- Creating a New Sudo/Sudoer User in Linux
- Option 1: Add User to Sudo Wheel Group
- Option 2: Editing /etc/sudoers File
- Testing Sudoer User Access in Linux
- Create new linux account as a user without root access
- 5 Answers 5
Login as non-root user in terminal
This is a question that I would expect to quickly get an answer from google. However somehow google is failing me. Let’s assume I’m logged in to a terminal session and I would like temporarily work as another non-root user whose password I know without leaving my session. When logged as this user I want the home directory, etc, for this user set up correctly until I log out. How do I do that? I tried
and then keying in the password, it did not produce any error but I saw no visible changes of the command prompt it would still say myname@myhost. The home directory also was that of myname and not the new login I tried to login as. I’m — as it’s apparent now — quite inexperienced in linux/Ubuntu, so any info is welcome.
2 Answers 2
To which user you want to change to?
The problem is that you are trying to «su» into a user that does not have a shell assigned to it. Most of the users such as mysql, pulse, etc, created by the system or by some packages when you install software does not have a shell assigned.
You can check if a user has a shell assigned by looking into the /etc/passwd file, just look at the end of the line of each user, if it says /bin/false it means that it does not have a shell assigned, if it has something like /bin/bash or any other shell, then you should be able to «su» into that user.
When i say «shell assigned» it basically means that it has «shell access»
still if the user does not have shell access, you can always execute commands as that user with
How to Add a non-Root User to Kali Linux
Generally, Most Linux distros ask their users to use lower user privileges while using the Operating System. That is a great advice for Operating System’s security, because this non-Root (Non-Administrative) environment maintains an extra layer of security between the normal user and the Operating System. This user environment is useful where multiple users and separate privileges in a system are required. Also this non-root environment is good for security because a software crash running with user privileges won’t blow up the whole operating system or a new software vulnerability won’t give entire Root access to the hacker.
Kali Linux is mainly used for Penetration testing and Security Auditing, where most of the tools need to be run with administrative (Root) privileges by a single user so to avoid running every tool with “sudo” every time, it’s better to have default Root environment . Also it’s unlikely that a Kali’s system is used by multiple users and hence by default Kali has a single user “root” with Administrative privileges. Also due to its default root privileged environment, Kali Linux isn’t recommended for absolute beginners.
This root environment limits many user applications to operate because many application like Google Chrome, TOR Browser, VLC Media Player only operate in sandboxed user environment for security reasons.
Perks of having a normal user account in Kali Linux
- You can install and use many non-root softwares including Google Chrome, TOR Browser, VLC Media Player and many other softwares.
- It’s safe not to use Operating system as Root because any mistake done by root user or root application can be destructive.
- You can install GNOME management tools and customize your desktop environment
Adding a Non-Root User
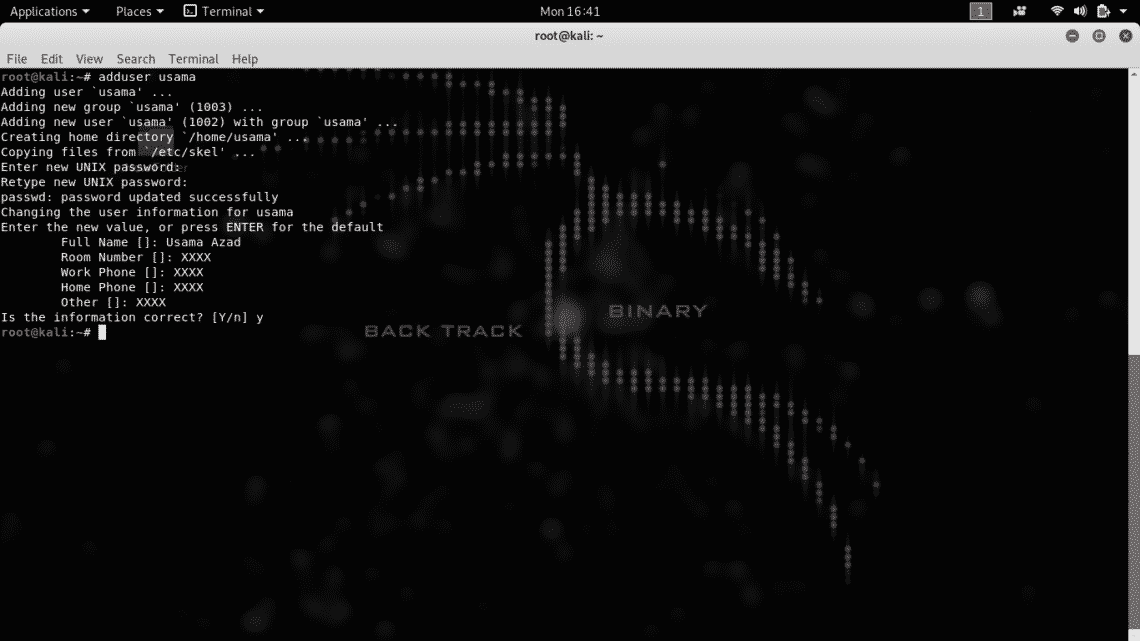
First of all register a normal user account using “adduser” command, it’ll ask you for password confirmation and other user details
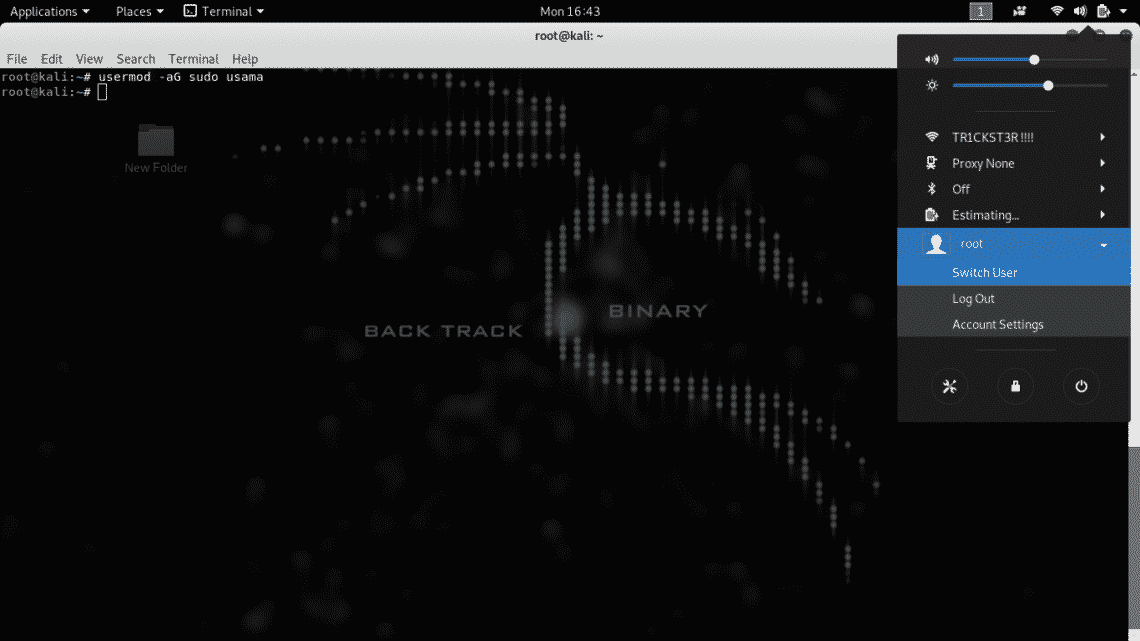
Now, change the user mode to perform administrative (sudoer) tasks, so you can run sudo command later.
A normal user is created which can run root tasks by using “sudo” command. Now logout from your root user and login again with your newly created account.
Installing Google Chrome
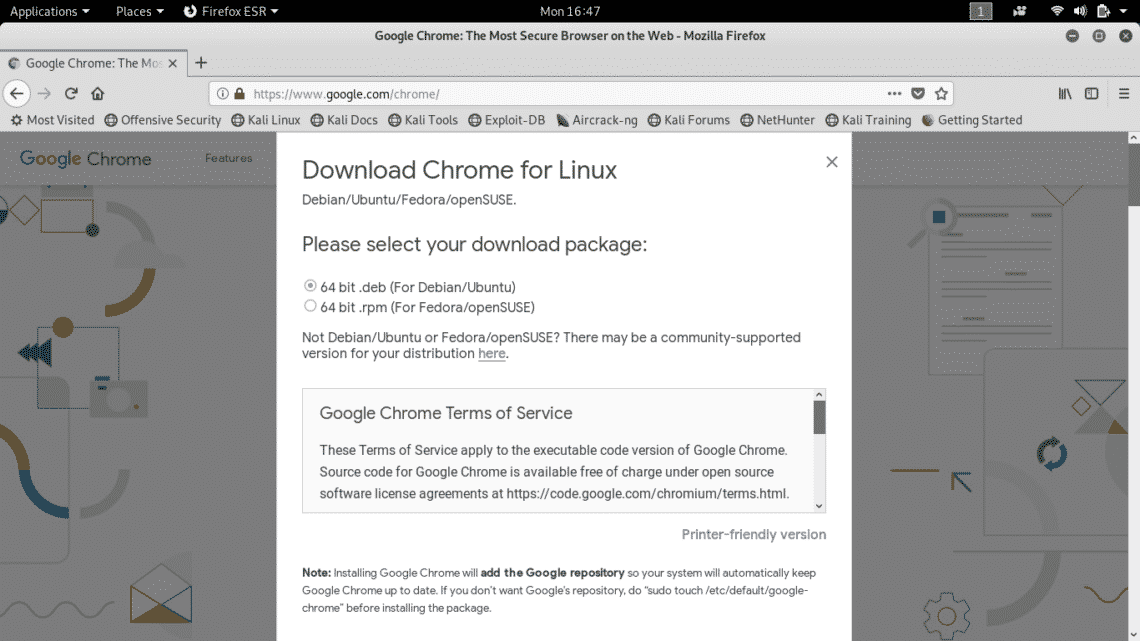
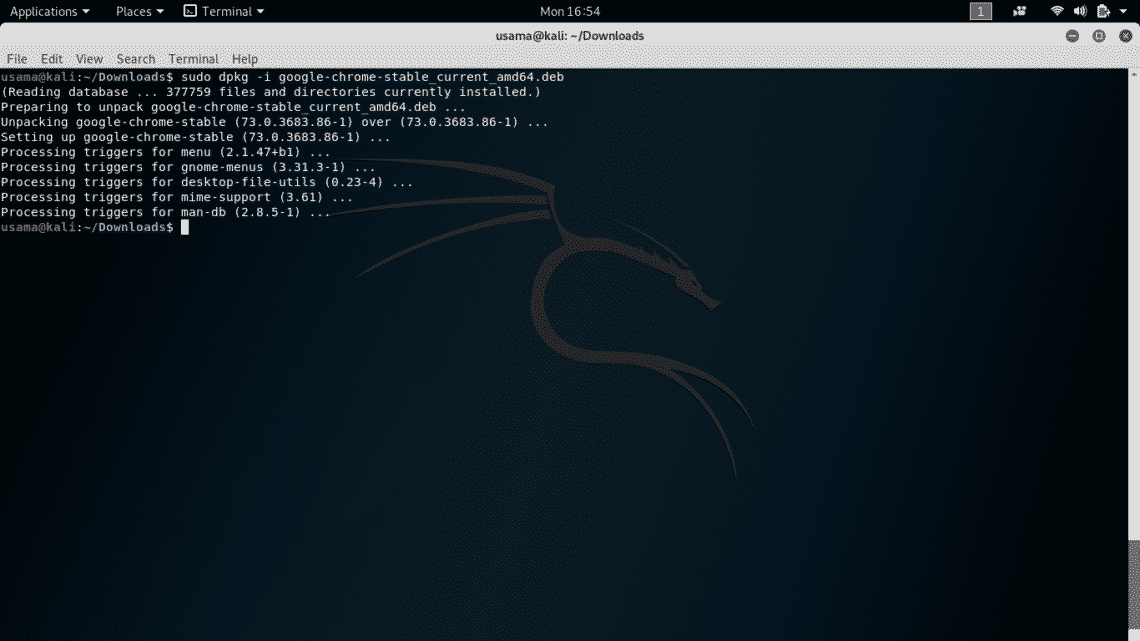
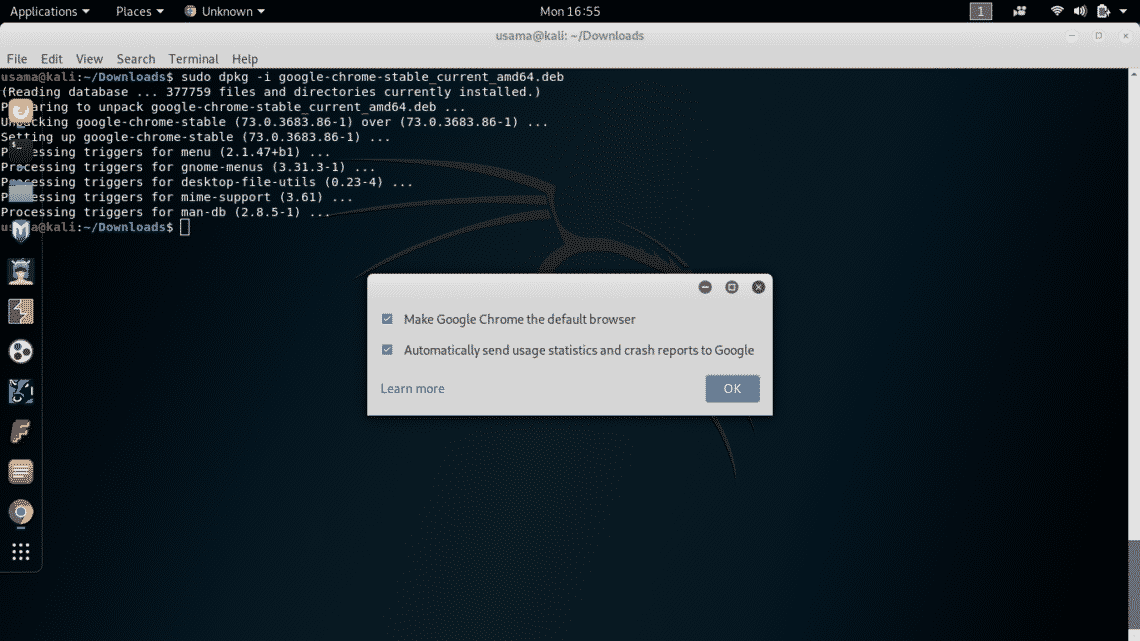
You can install Google Chrome in this non-root user. Go to Chrome’s official website and download the debian installer package “.deb” for Kali Linux and install it using package installer.
If you get any errors, please type the following
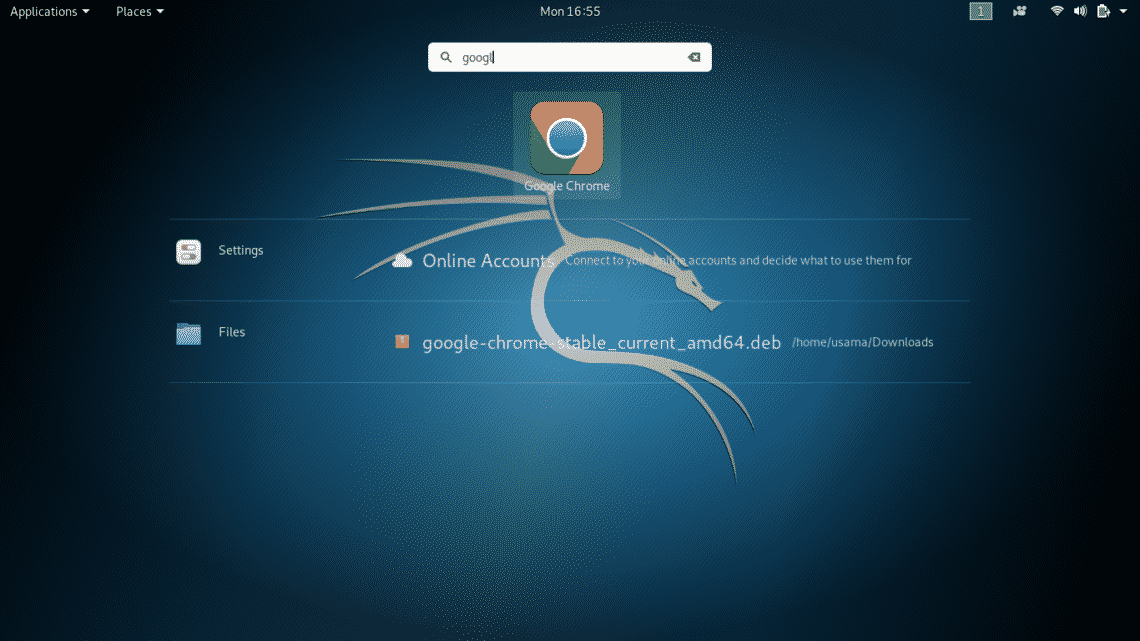
Now, you can run Google Chrome from the GNOME Menu
Installing other Non-Root Softwares
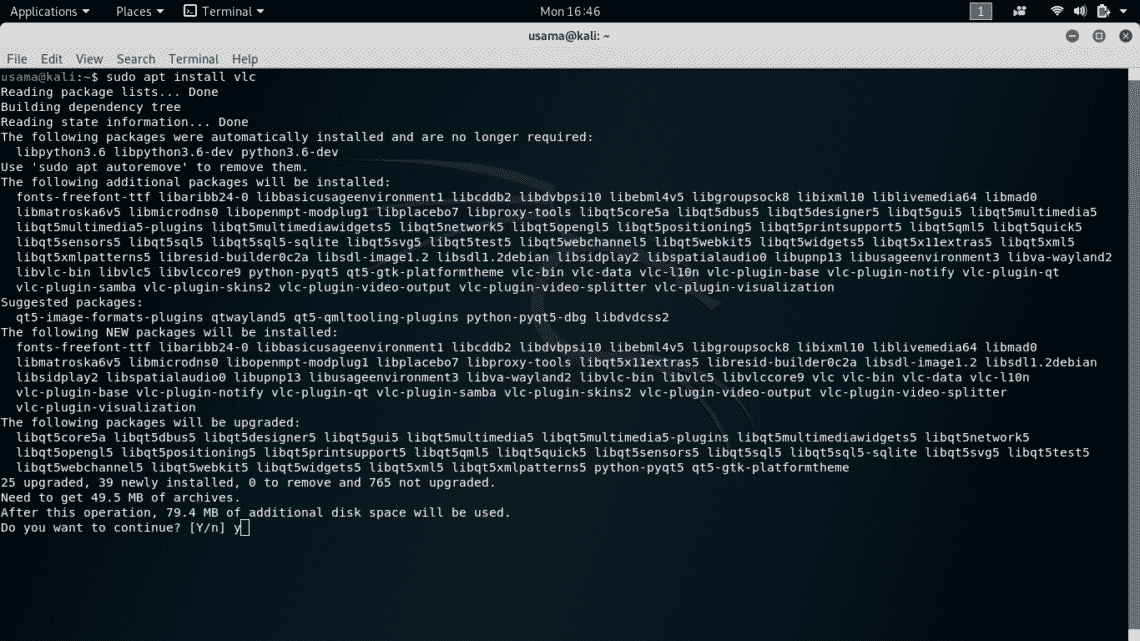
You can also install other softwares like VLC Media Player, TOR Browser by adding their repositories, using apt-get or by manually downloading their “.deb” and then installing it. For example, you can install VLC using apt-get with sudo.
To install TOR Browser, type
usama@kali:~$ sudo add-apt-repository ppa:webupd8team / tor-browser
usama@kali:~$ sudo apt-get update
usama@kali:~$ sudo apt-get install tor-browser torbrowser-launcher -y
Conclusion
Because of user requirements, Kali comes with default Root environment and it’s intended for power user. But in some circumstances, one may need non-root environment. That you can do by adding a sudoer non-root user to the users list. There’s also an “Expert Mode” in Kali Linux’s installation menu where you can choose not to add default root mode.
About the author
Usama Azad
A security enthusiast who loves Terminal and Open Source. My area of expertise is Python, Linux (Debian), Bash, Penetration testing, and Firewalls. I’m born and raised in Wazirabad, Pakistan and currently doing Undergraduation from National University of Science and Technology (NUST). On Twitter i go by @UsamaAzad14
How to Create Sudo User in RHEL, CentOS, Rocky & AlmaLinux
The Redhat Enterprise Linux (RHEL) ecosystem hosts several interesting Linux-based OS distributions. The OS pair AlmaLinux and Rocky Linux are exciting replacements for the discontinued CentOS distribution.
RHEL 8, AlmaLinux, and Rocky Linux systems are increasingly being sorted after by many Linux users due to the performance footprints they offer.
The main users of an operating system environment can be categorized into the root (Sudoer) users and non-root users. Root users have full control of the operating system environment and can create other users in addition to managing the OS’s applications, processes, and configurations. The non-root users have limited interactions with an operating system environment.
As the root user of your Linux system, you will at one point need to give other non-root users more OS privileges and execution power. For this step to happen, these normal OS users will need to be graduated to Sudo users.
Make sure you have Sudoer/root user access privileges on your system before proceeding with the article guide.
Creating a New Sudo/Sudoer User in Linux
The term Sudo is an abbreviation for the superuser do or substitute user do. The directory path /etc/sudoers hosts existing Sudoer users’ security policy associated with their warranted privileges.
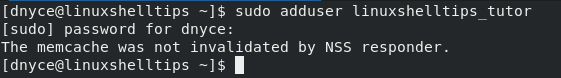
To create a new user from scratch, execute the following command.
$ sudo adduser linuxshelltips_tutor
The above command will create a non-root user called linuxshelltips_tutor.
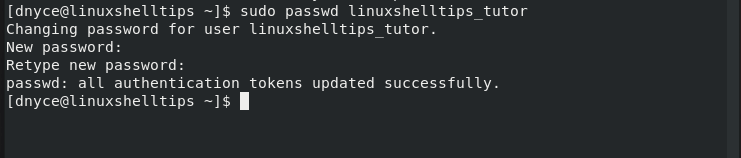
Next, we need to assign this new user a login password.
$ sudo passwd linuxshelltips_tutor
We now have two options of making your exiting/created Linux user a Sudoer-privileged user.
Option 1: Add User to Sudo Wheel Group
Only wheel group members are granted Sudo access and privileges. To make user linuxshelltips_tutor a member of this wheel group, we will implement the usermod command in the following manner.
$ sudo usermod -aG wheel linuxshelltips_tutor
With the above command execution, we have made linuxshelltips_tutor a Sudoer user.
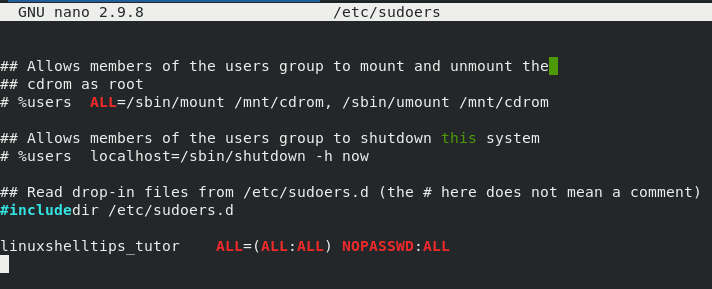
Option 2: Editing /etc/sudoers File
This file lists all the users on your system and their customizable access and privileges. We can modify this file to make our newly created user a Sudoer user in the following manner.
First, open the file with your preferred command-line editor.
$ sudo nano /etc/sudoers file
At the bottom of this file, we will modify it in the following manner in order to make linuxshhelltips_tutor a Sudoer user.
linuxshelltips_tutor ALL=(ALL:ALL) NOPASSWD:ALL
The NOPASSWD portion of the above entry will not require the linuxshelltips_tutor user to adhere to any password authentication protocol when executing sudo-associated terminal commands.
Testing Sudoer User Access in Linux
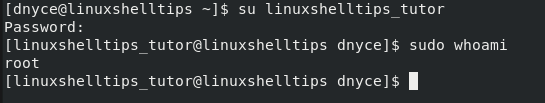
We need to confirm that we indeed created a Sudoer user. The first Sudoer user test can be performed with the following commands.
$ su linuxshelltips_tutor $ sudo whoami
You can even switch to the new user’s home directory before executing the whoami command.
As the command output suggests, we are dealing with a root user.
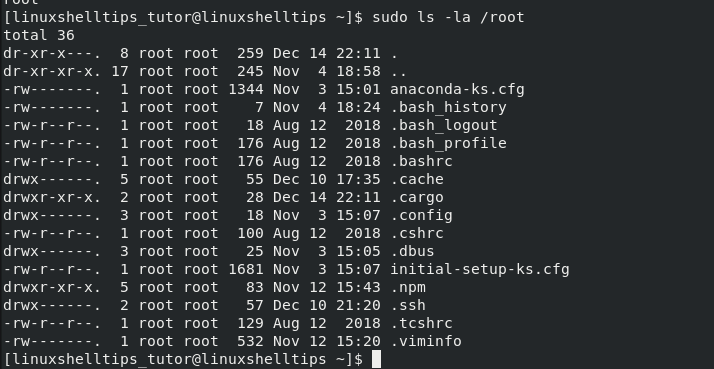
Alternatively, listing the contents under /root should also confirm that we are dealing with a root/sudo user. The content of the /root path cannot be displayed under a non-root user profile.
A Sudo/Sudoer user has exclusive Linux OS privileges which are not availed for a non-Sudo user. This user has more control in their assigned OS role.
Create new linux account as a user without root access
Is it possible to create a non-root Linux user account without being logged in as a root user and without using sudo ?
5 Answers 5
Boot up into a system rescue CD. Or, if your root account is locked, boot to single-user mode (add 1 to the end of the boot command). Other than that, no. Could you imagine how insecure that would make a system?
I don’t see any security threat in that. I just want to create an user account with the same privilege I have in my account while I’m logged with my account
@Simone You could make dozens of accounts so it’s hard for the admin to kick you off the system. Or make a second account and store all your illegal files there. Or just make new accounts to get around per-user restrictions like disk quotas
@Simone A comment like this is likely to get you fired in any shop that actually has computer systems helping you make money.
@Kevin well even the way you describe it you will be creating accounts as user root. Not all systems allow login without root-password in runlevel 1. And the boot-process as well as the boot menu should be password protected on any halfway secure system.
@Nils Yes, but not the root of his system. My understanding of runlevel 1 is that it requires a password if and only if root has one, but it’s possible I’m mistaken. And yes, the boot menu should be protected, but we all know that’s not always going to be the case.
It requires writing in some files. Which happen to be writable only by root. So use a setuid root binary like sudo or be root.
If the system is not being used, just mount the hard driver and edit manually the files you need, there should be binaries on the system to edit the password file/groups and such. I’m more a BSD user so I don’t know the names but look for vipw/adduser/useradd/usermgmt/etc.
Are you sure you really need to do that? Managing user is part of the administrator’s tasks, so root is the way to go. If someone else can modify system files, there’s a security problem.