- Allowing remote tomcat debugging on 8000 port in Ubuntu
- Ubuntu Firewall (UFW) – How to Configure, Check Status, Open/Close Ports & Enable/Disable
- Requirements
- Install UFW
- Configure UFW Default Policies
- Allow incoming Connections
- Allow Specific Port
- Allow Specific Port Range
- Allow Specific IP Address
- Allow Specific Subnet
- Allow Specific Network Interface
- Deny incoming Connections
- List Application Profile
- Delete UFW Rules
- Enable UFW Logging
- Reset & Disable UFW
- Conclusion
- Recent Posts
- How to open a port?
Allowing remote tomcat debugging on 8000 port in Ubuntu
I have an application deployed in tomcat on a google Ubuntu VM. Application is running fine and accessible remotely by domain name and IP address.
I want to debug this application remotely using Eclipse from another Ubuntu system. On google VM I am starting the tomcat with command,
Listening for transport dt_socket at address: 8000 I guess that means remote debugging is enabled on 8000 port. But when I try to connect to application from Eclipse for remote debugging it gives ‘connection refused’ error.
When I try telnet remotely it gives,
ivish@ivish:~$ telnet host_ip 8000 Trying host_ip . telnet: Unable to connect to remote host: Connection timed out google@vm:/opt/tomcat8$ nmap localhost Starting Nmap 5.21 ( http://nmap.org ) at 2016-09-19 05:27 UTC Nmap scan report for localhost (127.0.0.1) Host is up (0.00015s latency). Not shown: 994 closed ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 3306/tcp open mysql 5432/tcp open postgresql 8000/tcp open http-alt 8009/tcp open ajp13 Nmap done: 1 IP address (1 host up) scanned in 0.04 seconds Any idea how can i successfully remote debug the application? Thanks. EDIT:
Output of ‘sudo iptables -L’ command on Google VM.
google@vm:/opt/tomcat8$ sudo iptables -L Chain INPUT (policy ACCEPT) target prot opt source destination sshguard all -- anywhere anywhere Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination Chain sshguard (1 references) target prot opt source destination ivish@ivish:~$ sudo iptables -L Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination Ubuntu Firewall (UFW) – How to Configure, Check Status, Open/Close Ports & Enable/Disable
Firewalls are one of the most important (if not the most important) features to install and configure correctly — Lets learn how to do it!
Last Updated: December 2nd, 2019 by Hitesh J in Guides, Linux
UFW stands for “Uncomplicated Firewall” is the default firewall tool for Debian based operating systems. It is an alternative program to iptables that simplifies the process of configuring and managing the firewall.
Generally, iptables is a very advanced tool with powerful functionality, but it’s syntax is very complex and difficult for beginners. While UFW provides user-friendly syntax that makes it easier to manage your firewall. UFW also provides a user-friendly front-end for managing iptables firewall rules.
UFW may be the appropriate solution for you are looking to secure your network easily.
In this tutorial, we will show you how to install and use UFW firewall on Linux.
Requirements
- A server running Ubuntu operating system.
- A root password is configured on your system.
Install UFW
By default, UFW is installed in most Ubuntu operating systems. If not installed, you can install it by running the following command:
Once the installation is completed, you can check the status of UFW firewall with the following command:
You should see the following output:
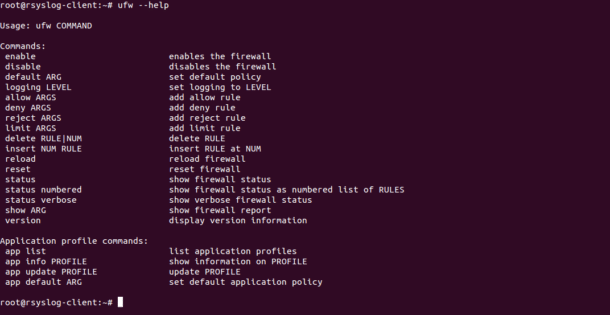
You can check all the options available with UFW using the following command:
You should see the following screen:
Configure UFW Default Policies
By default, UFW is configured to allow all outgoing connections and deny all incoming connections. Before started with your UFW firewall, set your UFW firewall rules back to the defaults. You can set the default policy with the following commands:
ufw default deny incoming
ufw default allow outgoing
Now, anyone trying to access your server can not be able to connect your server.
Next, you will need to activate the UFW firewall to apply the changes. Before activating the UFW firewall, it is recommended to allow incoming SSH connection to access your server from a remote location. You can allow incoming SSH connection with the following command:
If your SSH is configured to listen on a different port (2222 )then run the following command:
Now, you can enable the UFW firewall using the following command:
Allow incoming Connections
There are several ways to allow incoming connections like, allow specific port, allow specific port range, allow specific IP address, allow specific subnet and allow specific network interface.
Allow Specific Port
By default UFW is configured to deny all incoming connections. So you will need to allow specific port as per your need.
For example, to allow incoming HTTP connections run the following command:
You can also specify port number instead service name as shown below:
To allow incoming connection on UDP port 21 run the following command:
You can see a sample output of the above commands in the following screen:
You can also check the status of UFW firewall with the following command:
You should see the following screen:
Allow Specific Port Range
Instead of allowing single ports UFW also allows you to specify multiple port numbers in a single command. For example, you can allow incoming connections from ports 8000 to 9000 with the following command:
To allow UDP port range 8000 to 9000, run the following command:
Allow Specific IP Address
UFW allows you to access all ports from a specific IP address. For example, if you want to allow all incoming connections from the IP address 192.168.0.100 run the following command:
ufw allow from 192.168.0.100
You can also allow access to specific port (8080) from the specific IP address (192.168.0.101).
ufw allow from 192.168.0.101 to any port 8080
Allow Specific Subnet
You can also allow incoming connections from a range of IP addresses. For example, to allow all incoming connections from the IP address 192.168.0.1 to 192.168.0.254 run the following command:
ufw allow from 192.168.0.0/24
You can also specify the destination port 8089 that the subnet 192.168.0.0/24 is allowed to connect to as shown below:
ufw allow from 192.168.0.0/24 to any port 8089
Allow Specific Network Interface
If you want to add firewall rules that only apply to a specific network interface (eth0). For example, allow all incoming connections to the network interface eth0 run the following command:
You can allow access on a specific port 9000 only to specific interface eth0 by running the following command:
ufw allow in on eth0 to any port 9000
Deny incoming Connections
You can deny all incoming connections on port 80, 443 and 25 with the following command:
ufw deny 80/tcp
ufw deny 443/tcp
ufw deny 25/tcp
To deny all incoming connections from specific subnet, run the following command:
To deny all incoming connections from specific IP address, run the following command:
List Application Profile
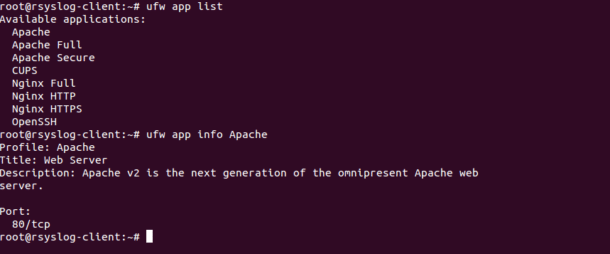
By default, all application profile saved in the /etc/ufw/applications.d directory. You can list all application profile with the following command:
You should see the following output:
Available applications:
Apache
Apache Full
Apache Secure
CUPS
Nginx Full
Nginx HTTP
Nginx HTTPS
OpenSSH
You can also see the information about a specific application with the following command:
You should see the following output:
Profile: Apache
Title: Web Server
Description: Apache v2 is the next generation of the omnipresent Apache web
server.
Port:
80/tcp
You can see a sample output of above commands in the following screen:
Delete UFW Rules
There are two ways you can delete UFW rules, with the actual rule and with rule numbers.
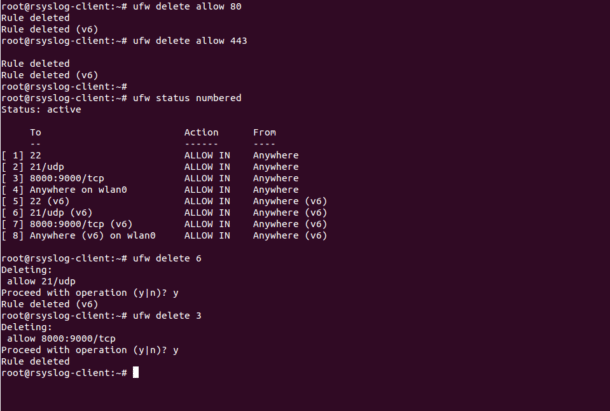
The first method to delete a rule by specifying the actual rule. For example, to delete a rule for port 80 and 443 run the following command:
ufw delete allow 80
ufw delete allow 443
The second method to delete a rule by specifying rule numbers. First, you will need to find the number of the rule you want to delete. You can list all the rules with numbers as shown below:
You should see the following output:
Status: active
To Action From
— —— —-
[ 1] 22 ALLOW IN Anywhere
[ 2] 21/udp ALLOW IN Anywhere
[ 3] 8000:9000/tcp ALLOW IN Anywhere
[ 4] Anywhere on wlan0 ALLOW IN Anywhere
[ 5] 22 (v6) ALLOW IN Anywhere (v6)
[ 6] 21/udp (v6) ALLOW IN Anywhere (v6)
[ 7] 8000:9000/tcp (v6) ALLOW IN Anywhere (v6)
[ 8] Anywhere (v6) on wlan0 ALLOW IN Anywhere (v6)
Now, delete the rule number 6 with the following command:
To delete the rule number 3, run the following command:
You can see the sample output of all commands in the following screen:
Enable UFW Logging
Enabling UFW logging is very useful to troubleshoot your firewall rules.
You can enable logging with the following command:
You can also disable the UFW logging any time with the following command:
By default, UFW logs are stored in the file /var/log/ufw.log. You can see it with the following command:
Reset & Disable UFW
If you want to revert all of your changes that you have made with UFW, run the following command:
The above command will disable UFW and delete all active rules.
In some cases, you want to disable and deactivate all the rules. You can do it with the following command:
Conclusion
In the above tutorial, we learned how to install, configure and working with UFW firewall. I hope you have now enough knowledge to secure your system with the UFW.
Recent Posts
- Forcepoint Next-Gen Firewall Review & Alternatives
- 7 Best JMX Monitoring Tools
- Best PostgreSQL Backup Tools
- Best CSPM Tools
- Best Cloud Workload Security Platforms
- Best Automated Browser Testing Tools
- Event Log Forwarding Guide
- Best LogMeIn Alternatives
- Citrix ShareFile Alternatives
- SQL Server Security Basics
- Cloud Security Posture Management Guide
- Cloud Workload Security Guide
- The Best JBoss Monitoring Tools
- ITL Guide And Tools
- 10 Best Enterprise Password Management Solutions
How to open a port?
I have ubuntu 12.04 and I’m not able to allow certain port in my firewall. So I basically said I will allow everything but it’s still not working. Please help. nmap on this machine from other machine says:
$ nmap host_name Not shown: 996 closed ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 139/tcp open netbios-ssn 445/tcp open microsoft-ds $ nmap localhost Starting Nmap 5.21 ( http://nmap.org ) at 2014-01-21 11:14 PST Nmap scan report for localhost (127.0.0.1) Host is up (0.000080s latency). Not shown: 991 closed ports PORT STATE SERVICE 22/tcp open ssh 25/tcp open smtp 53/tcp open domain 80/tcp open http 139/tcp open netbios-ssn 445/tcp open microsoft-ds 631/tcp open ipp 3306/tcp open mysql 8000/tcp open http-alt Nmap done: 1 IP address (1 host up) scanned in 0.04 seconds # iptables -L -n Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 mmoghimi@titan:~$ sudo netstat -tulpn Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN 14842/mysqld tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN 982/smbd tcp 0 0 127.0.0.1:39346 0.0.0.0:* LISTEN 3405/GoogleTalkPlug tcp 0 0 127.0.0.1:50995 0.0.0.0:* LISTEN 3405/GoogleTalkPlug tcp 0 0 127.0.0.1:5939 0.0.0.0:* LISTEN 2412/teamviewerd tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 2429/dnsmasq tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 985/sshd tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1267/cupsd tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 1748/exim4 tcp 0 0 0.0.0.0:17500 0.0.0.0:* LISTEN 2885/dropbox tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN 982/smbd tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN 4134/python tcp6 0 0 . 139 . * LISTEN 982/smbd tcp6 0 0 . 80 . * LISTEN 1832/apache2 tcp6 0 0 . 22 . * LISTEN 985/sshd tcp6 0 0 ::1:631 . * LISTEN 1267/cupsd tcp6 0 0 ::1:25 . * LISTEN 1748/exim4 tcp6 0 0 . 445 . * LISTEN 982/smbd udp 0 0 127.0.0.1:53 0.0.0.0:* 2429/dnsmasq udp 0 0 0.0.0.0:68 0.0.0.0:* 2403/dhclient udp 0 0 128.54.44.214:123 0.0.0.0:* 3430/ntpd udp 0 0 MYIP:123 0.0.0.0:* 3430/ntpd udp 0 0 127.0.0.1:123 0.0.0.0:* 3430/ntpd udp 0 0 0.0.0.0:123 0.0.0.0:* 3430/ntpd udp 0 0 137.110.255.255:137 0.0.0.0:* 2602/nmbd udp 0 0 MYIP:137 0.0.0.0:* 2602/nmbd udp 0 0 128.54.47.255:137 0.0.0.0:* 2602/nmbd udp 0 0 128.54.44.214:137 0.0.0.0:* 2602/nmbd udp 0 0 0.0.0.0:137 0.0.0.0:* 2602/nmbd udp 0 0 137.110.255.255:138 0.0.0.0:* 2602/nmbd udp 0 0 MYIP:138 0.0.0.0:* 2602/nmbd udp 0 0 128.54.47.255:138 0.0.0.0:* 2602/nmbd udp 0 0 128.54.44.214:138 0.0.0.0:* 2602/nmbd udp 0 0 0.0.0.0:138 0.0.0.0:* 2602/nmbd udp 0 0 0.0.0.0:17500 0.0.0.0:* 2885/dropbox udp 0 0 0.0.0.0:36889 0.0.0.0:* 1356/avahi-daemon: udp 0 0 0.0.0.0:5353 0.0.0.0:* 1356/avahi-daemon: udp6 0 0 ::1:123 . * 3430/ntpd udp6 0 0 fe80::fab1:56ff:fe9:123 . * 3430/ntpd udp6 0 0 fe80::3e77:e6ff:fe6:123 . * 3430/ntpd udp6 0 0 . 123 . * 3430/ntpd udp6 0 0 . 33792 . * 1356/avahi-daemon: udp6 0 0 . 5353 . * 1356/avahi-daemon: