- Saved searches
- Use saved searches to filter your results more quickly
- License
- The-Cracker-Technology/Empire
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- PowerShell-Empire
- Starting PowerShell-Empire with Starkiller on Kali Linux
- Adding a Listener through Starkiller
- Adding a Stager through Starkiller
- Interacting with Agents through Starkiller
- PowerShell-Empire Modules
- Discovery Modules
- Credential Access Modules
- Packages and Binaries:
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
License
The-Cracker-Technology/Empire
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
Empire 3 is a post-exploitation framework that includes a pure-PowerShell Windows agent, and compatibility with Python 3.x Linux/OS X agents. It is the merger of the previous PowerShell Empire and Python EmPyre projects. The framework offers cryptologically-secure communications and flexible architecture.
On the PowerShell side, Empire implements the ability to run PowerShell agents without needing powershell.exe, rapidly deployable post-exploitation modules ranging from key loggers to Mimikatz, and adaptable communications to evade network detection, all wrapped up in a usability-focused framework. PowerShell Empire premiered at BSidesLV in 2015 and Python EmPyre premiered at HackMiami 2016. BC Security presented updates to further evade Microsoft Antimalware Scan Interface (AMSI) and JA3/S signatures at DEF CON 27.
Empire relies heavily on the work from several other projects for its underlying functionality. We have tried to call out a few of those people we’ve interacted with heavily here and have included author/reference link information in the source of each Empire module as appropriate. If we have failed to properly cite existing or prior work, please let us know at Empire@BC-Security.org.
Empire is currently being developed and maintained by @Cx01N, @Hubbl3, & @Vinnybod. While the main Empire project is no longer maintained, this fork is maintained by @bcsecurity1. Please reach out to us on our Discord if you have any questions or talk about offensive security.
As of Empire 3.1, we will no longer be actively supporting the Python 2.7 base code. If you wish to continue to leverage Python 2.7 then please use the 3.0.x Releases, since they were built to ensure backward compatibility.
Please see our Releases or Changelog page for detailed release notes.
We recommend the use of Kali, Poetry, or our Docker images to run Empire. Kali Linux users and Direct Sponsors will receive 30-day early access to new Empire and Starkiller features.
The following operating systems have been tested for Empire compatibility. We will be unable to provide support for other OSs at this time. Consider using our Prebuilt Docker containers which can run on any system.
You can install the latest version of Empire by running the following:
sudo apt install powershell-empire sudo powershell-empire
Note: Newer versions of Kali require you to run sudo before starting Empire.
Poetry is a dependency and virtual environment management tool. This is highly recommended if using the SocketIO notification feature introduced in 3.5.0. To install Poetry, please follow the installation guide in the documentation or run sudo pip3 install poetry .
git clone --recursive https://github.com/BC-SECURITY/Empire.git cd Empire sudo ./setup/install.sh sudo poetry install sudo poetry run python empire If you want to run Empire using a pre-built docker container:
docker pull bcsecurity/empire: docker run -it -p 1337:1337 -p 5000:5000 bcsecurity/empire: # with persistent storage docker pull bcsecurity/empire: docker create -v /empire --name data bcsecurity/empire: docker run -it -p 1337:1337 -p 5000:5000 --volumes-from data bcsecurity/empire: # if you prefer to be dropped into bash instead of directly into empire docker run -it -p 1337:1337 -p 5000:5000 --volumes-from data bcsecurity/empire: /bin/bash
- The last commit from master will be deployed to the latest tag
- The last commit from the dev branch will be deployed to the dev tag
- All github tagged releases will be deployed using their version numbers (v3.0.0, v3.1.0, etc)
Check out the Empire wiki for instructions on getting started with Empire.
Plugins are an extension of Empire that allow for custom scripts to be loaded. This allows anyone to easily build or add community projects to extend Empire functionality. Plugins can be accessed from the Empire CLI or the API as long as the plugin follows the template example. A list of Empire Plugins is located here.
Contributions are more than welcome! The more people who contribute to the project the better Empire will be for everyone. Below are a few guidelines for submitting contributions.
- As of Empire 3.1.0, Empire only officially supports Python 3. If you still need Python 2 support, please use the 3.0.x branch or releases.
- Submit pull requests to the dev branch. After testing, changes will be merged to master.
- Depending on what you’re working on, base your module on ./lib/modules/powershell_template.py or ./lib/modules/python_template.py. Note that for some modules you may need to massage the output to get it into a nicely displayable text format with Out-String.
- Cite previous work in the ‘Comments’ module section.
- If your script.ps1 logic is large, may be reused by multiple modules, or is updated often, consider implementing the logic in the appropriate data/module_source/* directory and pulling the script contents into the module on tasking.
- Use approved PowerShell verbs for any functions.
- PowerShell Version 2 compatibility is STRONGLY preferred.
- TEST YOUR MODULE! Be sure to run it from an Empire agent and test Python 3.x functionality before submitting a pull to ensure everything is working correctly.
- For additional guidelines for your PowerShell code itself, check out the PowerSploit style guide.
PowerShell-Empire
PowerShell-Empire is a post-exploitation framework that is built upon a large collection of PowerShell modules and scripts. It also contains various scripts written in C# and Python that can be used against a target OS. The PowerShell-Empire framework currently has hundreds of modules that can aid in almost all penetration testing tactics and techniques.
PowerShell-Empire have also developed a front-end GUI called Starkiller for the framework which makes configuration and activities that little bit easier to manage, especially when dealing with multiple targets. However, there is still the CLI available, with the framework running a server/client model.
Kali Linux comes with PowerShell-Empire and Starkiller pre-installed. 1
Starting PowerShell-Empire with Starkiller on Kali Linux
Start the PowerShell-Empire Server and Client in separate terminal windows. Ensure that the server is operational prior to starting the client to ensure that they can communicate.
sudo powershell-empire server sudo powershell-empire client
Create a new user on the PowerShell-Empire Client. Once the new user has been created, the PowerShell-Empire Client terminal can be closed if using the Starkiller GUI, otherwise the client is the interface to be used for configuring and interacting with agents.
(Empire) > admin (Empire) > create_user %USERNAME% %PASSWORD%
Open Starkiller and logon using the credentials set in the previous section. The URL by default is set to https://localhost:1337 .
Adding a Listener through Starkiller
- Navigate to the Listener window
- Press the create button on the top right to enter the New Listener prompt and select the type of listener using the drop-down menu.
For this example, the HTTP Listener is selected. Configure the Listener as below:
Name: darkcybeHttp Host: 172.16.2.2 Port: 1335
- KillDate: An expiration date that sets agent autocleanup
- DefaultProfile: Sets the URL GET request parameters to blend into normal traffic
- UserAgent: Set the UA string, useful to masquerade traffic
- ServerVersion: Set to a common Server Header to masquerade traffic
Adding a Stager through Starkiller
- Navigate to the Stager window
- Press the create button on the top right to enter the New Stager prompt and select the type of stager using the drop-down menu.
For this example, the windows/reverseshell is selected. Configure the Stager as below:
Listener: darkcybeHttp LocalHost: 172.16.2.2
Payloads can be created for Windows, MacOs, and Linux.
Interacting with Agents through Starkiller
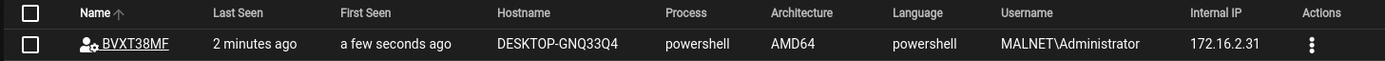
When a target executes the stager, the agent will connect to the Listener and be displayed on the Agents window, as per the image below:
Selecting the agent will open an agent specific window containing a number of different options:
- Interact: Allows for shell commands and PowerShell-Empire Modules to be executed on the agent.
- File Browser: Directory traversal including file upload and download functionality.
- Tasks: A history of actions carried out on the host
- View: Agent specific configuration
PowerShell-Empire Modules
Discovery Modules
When executing the Bloodhound modules, the Sharphound archive defaults to C:\Users\%USERNAME%\ on the target agent. The download directory on the attacking Kali host is /var/lib/powershell-empire/server/downloads/%AGENT%/ .
Credential Access Modules
Using the Mimkatz LogonPasswords modules automatically adds collected credentials to the credentials window within PowerShell-Empire.
Packages and Binaries:
This package contains a post-exploitation framework that includes a pure-PowerShell2.0 Windows agent, and a pure Python Linux/OS X agent. It is the merge of the previous PowerShell Empire and Python EmPyre projects. The framework offers cryptologically-secure communications and a flexible architecture. On the PowerShell side, Empire implements the ability to run PowerShell agents without needing powershell.exe, rapidly deployable post-exploitation modules ranging from key loggers to Mimikatz, and adaptable communications to evade network detection, all wrapped up in a usability-focused framework.
Installed size: 168.60 MB
How to install: sudo apt install powershell-empire
- default-mysql-server
- python3
- python3-aiofiles
- python3-bcrypt
- python3-cryptography
- python3-docopt
- python3-donut
- python3-dropbox
- python3-fastapi
- python3-flask
- python3-flask-socketio
- python3-humanize
- python3-jinja2
- python3-jose
- python3-jq
- python3-macholib
- python3-multipart
- python3-netifaces
- python3-openssl
- python3-passlib
- python3-prompt-toolkit
- python3-pycryptodome
- python3-pydantic
- python3-pydispatch
- python3-pyinstaller
- python3-pyminifier
- python3-pymysql
- python3-pyparsing
- python3-pyperclip
- python3-pyvnc
- python3-requests
- python3-secretsocks
- python3-setuptools
- python3-simplejson
- python3-socketio
- python3-sqlalchemy
- python3-sqlalchemy-utc
- python3-terminaltables
- python3-tk
- python3-urllib3
- python3-uvicorn
- python3-websocket
- python3-websockets
- python3-websockify
- python3-xlrd
- python3-xlutils
- python3-yaml
- python3-zlib-wrapper
powershell-empire
[email protected]:~# powershell-empire -h usage: empire.py [-h] . positional arguments: server Launch Empire Server client Launch Empire CLI options: -h, --help show this help message and exit