- How To Control Privileged User on Linux
- Types of Linux accounts
- Privileged Account Security
- Built-in Linux Monitoring Tools
- Creating a new user and modifying its privileges in Linux
- Simple way to create a new user in Linux.
- Universal way to create a new user in Linux.
- New user’s system privileges
- Setting password and account expiration
- How to delete a user
- Summary
How To Control Privileged User on Linux
Despite the rising number of cybercrimes, many companies who are willing to invest in proper security measures are much better protected today, than they were in the past. Security solution and practices are advancing rapidly in order to accommodate new threats and help companies stay ahead of the curve.
However, not all companies are willing to make the necessary investments, and definitely, not all threats are viewed as equal. While company will most definitely employ basic security solutions, such as firewalls and anti-viruses, not everybody is makes the necessary investment into privileged account security and user action monitoring, with many opting for standard built-in measure that their software and systems provide.
Linux in particular has the reputation for being less vulnerable to malware, but its privileged accounts are in fact very prone to both hacker attacks and misuse by malicious insiders. Let us look in more detail at how to control privileged user on Linux and what security measures Linux provides out of the box in order to help protect privileged accounts, and how effective they really are.
Types of Linux accounts
Same as Windows, Linux features several types of accounts:
- Super user or root – this is a default administrative account that allows for a full control of the system akin to Windows Administrator account. Linux root privileges allow user to execute any commands and control any services and any other accounts, change user permissions, add user to group, etc.
- Normal user – this is a regular account with restricted set of Linux user privileges. It can’t access any critical system resources or services and needs permission from root user to run certain commands.
- System user – a user account with the same level of privilege as the normal user, reserved for the use by various applications. Such accounts are employed in order to give applications certain permissions, or to isolate them for security purposes.
Linux allows for great flexibility with its accounts. You can create multiple root Linux accounts if needed, and also assigned different permissions to accounts or groups of accounts. You can also directly change permissions for reading, writing and execution of certain files or directories, as well as their ownership, which directly dictates user’s authority over said files. All of this flexibility, however, is a double edged sword, making it easy for perpetrator or tech-savvy malicious insider to misuse or steal protected data.
Ultimately, the root account is the most vulnerable point of the system as it is necessary for access to protected files and settings, and Linux has a couple of built-in ways to protect such an account.
Privileged Account Security
Any active root account should always be protected with a password, and Linux will ask you to set one during the installation or when you first decide to use root account. However, directly using root account is not the most secure course of actions for an organization, especially if you have several system administrators.
Much better way is to use a regular account and temporarily enable root privileges, by using su or sudo commands. Both of these commands perform a similar task – allow to delegate administrative privilege to regular account, but they function slightly differently. In order to use su, your administrator needs to know both password from their own account and from the root. While this may provide additional layer of protection when their account is compromised, it is not ideal from the insider threat standpoint.
Sudo command allows to get root privilege level without the need to know root password. Permission to access sudo command for other users is decided directly by the root. Sudo disables any additional privileges when the user stays inactive for more than five minutes, requiring password the next time, which helps to protect the console when administrator leaves without disabling privileged access.
Overall, this basic security measures allow to limit the extent of power that administrator has over the system and allow to better track the usage of administrative accounts. For example, if the administrator has logged in at an unusual time, it may be a cause for concern over breach or insider attack. However, without the proper insight into user actions, reliable protection from insider attacks cannot be guaranteed. Let us look at what tools Linux provides in user monitoring department.
Built-in Linux Monitoring Tools
Linux has a number of commands that allow privileged users to access logs and monitor the use of various system resources. The most basic of them is the top tool that provides a dynamic overview of all currently running processes. You can not only check system resource utilization, but also see all executed commands and other useful information that can give you some insight into what your users are doing.
Linux is also famous for its built-in network sniffer. Unlike the similar Windows tool, it allows not only to view network traffic in real time, but also capture it for later analysis, which provides a good amount of visibility into network usage.
Overall, Linux has fairly robust built-in monitoring functionality, but it is designed mainly for technical maintenance and troubleshooting. It does not present data in a convenient manner, and does not allow to easily get an overview of user actions, which makes its usefulness for insider threat detection fairly limited.
While Linux has a number of built-in tools for controlling and protecting privileged accounts, in a modern cybersecurity environment this level of protection is not nearly enough. New threats and vulnerabilities emerge very time, and Linux is not immune from them. If you wish to truly protect your Linux system, you need to employ a professional privileged access management and privileged user monitoring solutions that will give you a full visibility into who logged in with a privileged account and what they are doing.
Creating a new user and modifying its privileges in Linux
If you use Linux with a graphical desktop environment like Ubuntu, for example, you can add or remove new users through its Settings. But this is simplified and I have to say a limited way to do that. The right way is to use the command line. And it is the only way if you work with a server Linux system. Below, you will learn all you need to know about how to create, delete, and modify users in the Linux command line.

Simple way to create a new user in Linux.
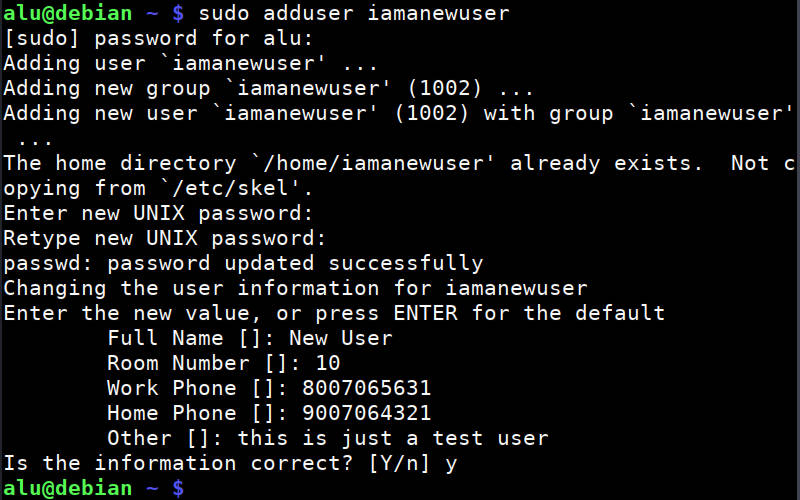
Many Linux systems have a user-friendly command to add a new user. The command is adduser. You type this command and the username of a new user.
The command will prompt you to create a user password, full name, and some additional information which can be skipped if you want.
And that’s it. The new user is created. This command also creates a home directory for new user ( /home/username )
However, if you also need to grant this user the administrative privileges, you need to add it to the sudo group:
sudo adduser username sudo Now, this new user will be able to execute the administrative commands with sudo .
This was the simplest way to create a new user in Linux. The adduser command is available in many Linux ditros, but in fact, it is a more user-friendly type of the command useradd , which is more advanced. Below, I would like to show you how to use this more advanced command too.
Universal way to create a new user in Linux.
If adduser is not available in your distro or you want to have little more control over the new user. You need to use the command useradd . I know the names are similar and easy to mix. But try to remember that useradd is a more important command. Basically, adduser just points to useradd .
To create a new user with the default options, run:
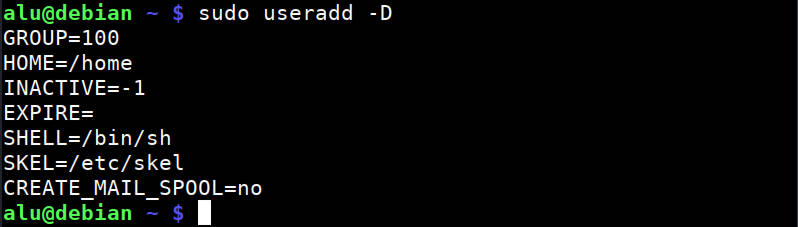
To check what default options were used to create a user, run:
These are the default rules on my Debian VPS (they may differ for your system. ):
You can change these options and use some more. To see all available options of the useradd command, check its help:
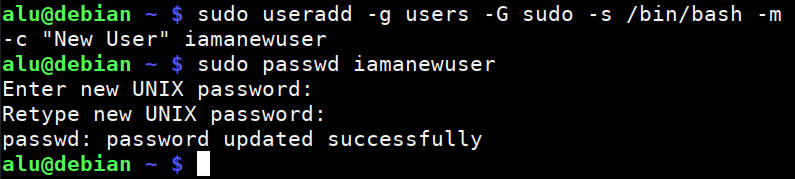
Based on these options, a more complete command would be:
sudo useradd -g users -G sudo -s /bin/bash -m -c "Full name" username Finally, you need to set a password for this user with passwd.
New user’s system privileges
As you have seen I added a new user to the sudo group and granted it administrative privileges. This is what I did on my server and this what you would want to do if you are an admin of the system. But if you create a user on your Linux system for someone else, you probably do not want them to have administrative privileges. So, do not add them to the sudo group.
Setting password and account expiration
If you are a system administrator and you have many uses in your system, besides not including them in the sudo group, you may also want to enhance the security of your system by the expiration time on the passwords and accounts of these new users.
You can do this with the command chage . Note, it is without n . The command is short of change age.
You can see all the available options of this command:
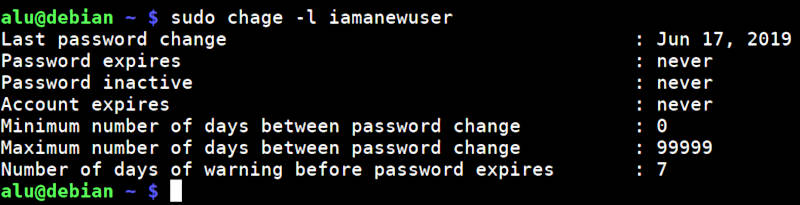
To check if there are any limitations set on a user, run:
Usually, there are no expiration dates by default. But you can set some limits with the command chage :
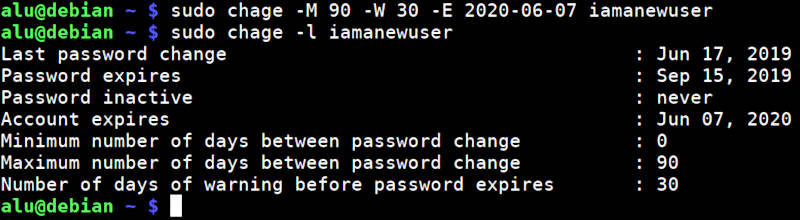
sudo chage -M 90 -W 30 -E 2020-06-07 username The above command will set a password expiration date to 90 days and warning about the need to update the password to 30 days before the expiration. And the account will expire on June 6, 2020.
You can see that if you check the status of the user:
You can also do some manipulation with users using the command usermod . But I have to skip it because this post will be too long.
How to delete a user
Finally, to delete a user, run this command:
If you also want to remove the home directory of this user, add option -r. But be careful, because it will remove all the data of this user:
Summary
- To create a new user in Linux, you can use the user-friendly command adduser or the universal command useradd . The latter is available in all Linux distros.
- New users do not have administrative privileges by default, to grant them such privileges, add them to the sudo group.
- To set time limits on password and account of a user, use the command chage .
- To delete a user, use the command userdel
Average Linux UserFollow I am the founder of the Average Linux User project, which is a hobby I work on at night. During the day I am a scientist who uses computers to analyze genetic data.